What are the signs someone is trying to hack into your home network?
There are several signs that someone may be trying to hack into your home network. Some of the most common signs include:
- Unusual network activity: If you notice an increase in network activity, especially at unusual times, it may be a sign that someone is trying to access your network.
- Slow internet speed: If your internet connection becomes slow or intermittent, it may be a sign that someone is using your bandwidth to access the internet or to run a botnet.
- Pop-ups and unwanted ads: If you start seeing pop-ups or unwanted ads while browsing the internet, it may be a sign that your device has been compromised by malware.
- Suspicious IP addresses: If you notice any suspicious IP addresses in your router logs, it may be a sign that someone is trying to access your network from outside.
- Unusual email or social media activity: If you notice any unusual email or social media activity, such as messages from unknown contacts or requests for personal information, it may be a sign that someone has gained access to your accounts.
- Unusual port activity: If you notice any unusual activity on open ports, it may be a sign that someone is trying to access your network through a port forward.
It’s important to be aware of these signs and to take action if you suspect that your network has been compromised. This can include disconnecting from the internet, running a malware scan, and changing your login credentials. Also, if you have any doubt, you should contact a professional for further help.
How do I protect open ports after port forwarding?
There are several ways to protect open ports after port forwarding:
- Use a firewall: Configure your firewall to only allow incoming connections on the ports that are being forwarded. This will block any unauthorized access to the open ports.
- Change the default login credentials: If you are forwarding ports to a device that requires login credentials (such as a router or a web camera), make sure to change the default login credentials to something more secure.
- Use a VPN: Set up a VPN connection to encrypt all of your internet traffic, including the traffic going through the open ports.
- Keep your software updated: Make sure to keep the software and firmware of the devices behind the open ports up-to-date to protect against any known vulnerabilities.
- Monitor your network: Regularly monitor your network for any suspicious activity, such as unusual incoming or outgoing traffic.
- Disable unnecessary ports: Disable any unnecessary ports that are not being used to minimize the attack surface.
It’s important to keep in mind that port forwarding can expose your network to potential security threats, so it’s crucial to take the necessary steps to protect your network.
Let’s expand on the subject of Monitoring your network
Monitoring your network refers to the process of keeping track of the activity on your network in order to detect any unusual or suspicious activity. This can include monitoring traffic patterns, analyzing logs, and using tools to detect and alert on potential security threats.
There are several different methods for monitoring your network, including:
- Network monitoring software: This type of software is used to monitor the activity on your network in real-time. It can alert you to any unusual activity, such as high traffic levels or suspicious IP addresses.
- Log analysis: Reviewing logs of your network activity can help you identify patterns or anomalies that may indicate a security issue.
- Intrusion detection systems (IDS): These systems are designed to detect and alert on potential security threats, such as unauthorized access attempts or suspicious network activity.
- Vulnerability scanning: Regularly scan your network for known vulnerabilities and patch them as soon as possible to prevent potential attacks.
- Penetration testing: This is a type of security testing where a professional simulates a cyber attack on your network to identify vulnerabilities and weaknesses.
It’s important to regularly monitor your network to detect any potential security issues early on, and to take the necessary steps to protect your network from those threats.
What routers or switches can do all this monitoring?
There are several routers and switches available on the market that have built-in monitoring and security features. These can include:
- Cisco Meraki: Cisco Meraki offers a wide range of routers and switches that come with built-in security features, such as firewall, VPN, intrusion detection and prevention, and content filtering. They also offer a cloud-based management platform that allows you to monitor and manage your network remotely.
- Fortinet: Fortinet offers a range of routers and switches that come with built-in security features, such as firewall, VPN, intrusion detection and prevention, and content filtering. They also offer a centralized management platform that allows you to monitor and manage your network remotely.
- Juniper: Juniper offers a range of routers and switches that come with built-in security features, such as firewall, VPN, intrusion detection and prevention, and content filtering. They also offer a centralized management platform that allows you to monitor and manage your network remotely.
- Watchguard: Watchguard offers a range of routers and switches that come with built-in security features, such as firewall, VPN, intrusion detection and prevention, and content filtering. They also offer a centralized management platform that allows you to monitor and manage your network remotely.
- Zyxel: Zyxel offers a range of routers and switches that come with built-in security features, such as firewall, VPN, intrusion detection and prevention, and content filtering. They also offer a centralized management platform that allows you to monitor and manage your network remotely.
It’s important to research and compare different options before purchasing a router or switch to ensure that it meets your specific needs and has all the features you require for monitoring and securing your network.
What about more affordable Synology and Unify DreamMachine routers?
Synology and Unifi routers are also known to have built-in monitoring and security features.
- Synology Router: Synology Router is designed for home and small business use, it offers robust network security features, including a built-in firewall, VPN, and intrusion detection and prevention. The routers also have a web-based management interface that allows you to monitor and manage your network remotely.
- Unifi Dream Machine: Unifi Dream Machine is an all-in-one router that includes a built-in firewall, VPN, and intrusion detection and prevention. It also includes a built-in access point and a web-based management interface that allows you to monitor and manage your network remotely.
Both Synology and Unifi routers are known for their feature-rich software and ease of use. They are great options for home and small business users who want to monitor and secure their networks. It’s important to note that while they have a lot of features, they also have some limitations on the advanced features and scalability when compared with enterprise-grade routers.
Should I create VLAN network infrastructure if I open network ports
Creating a VLAN (Virtual LAN) network infrastructure can be a good way to enhance the security of your network if you have open ports. VLANs allow you to segment your network into different logical segments, which can help to isolate different types of traffic and protect against unauthorized access.
Here are some benefits of using VLANs when you have open ports:
- Segmentation: VLANs can be used to segment the network into different logical segments, such as a guest network and a private network. This can help to isolate different types of traffic and protect against unauthorized access.
- Isolation: By isolating different types of traffic and devices, VLANs can help to limit the spread of malware or other malicious software if a device on your network becomes compromised.
- Access control: VLANs can be used to control access to different parts of your network, allowing you to restrict access to only authorized users and devices.
- Monitoring: By segmenting your network into different VLANs, it’s easier to monitor and detect any unusual activity on specific segments of your network.
It’s important to note that using VLANs alone is not a silver bullet for network security. To secure your network, you need to use a multi-layered approach, which includes a firewall, intrusion detection and prevention, and secure protocols for remote access.
Also, Keep in mind that creating VLANs does increase the complexity of your network, and it may require some knowledge of networking and VLANs to properly set it up. If you’re not confident in your skills, it’s recommended to seek professional help to set it up.
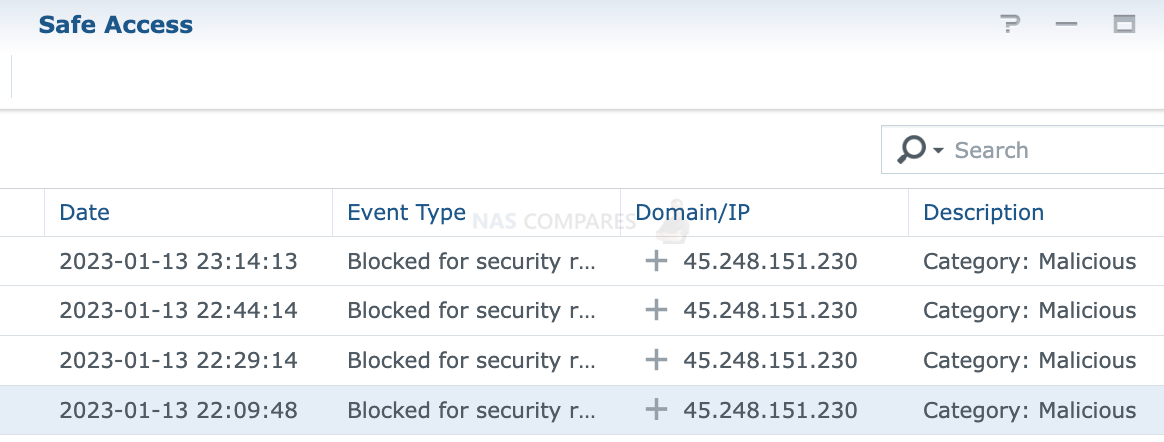
Synology safe access app and activity monitor that blocks malicious activity.
Synology Safe Access is a security app that is available on Synology routers. It is designed to provide advanced security features to protect your network and devices from malicious activity.
Here are some of the features of Synology Safe Access:
- Intrusion Prevention: Safe Access uses deep packet inspection to detect and prevent a wide range of network intrusions, including known and unknown vulnerabilities.
- Parental Controls: Safe Access allows you to set up parental controls to restrict access to inappropriate websites and limit internet access for specific devices during certain hours.
- Content Filtering: Safe Access allows you to filter access to websites based on categories, such as social media, gaming, and adult content.
- VPN: Safe Access includes a VPN server that allows you to access your network remotely and securely over the internet.
- Firewall: Safe Access includes a built-in firewall that can be used to block unauthorized access to your network.
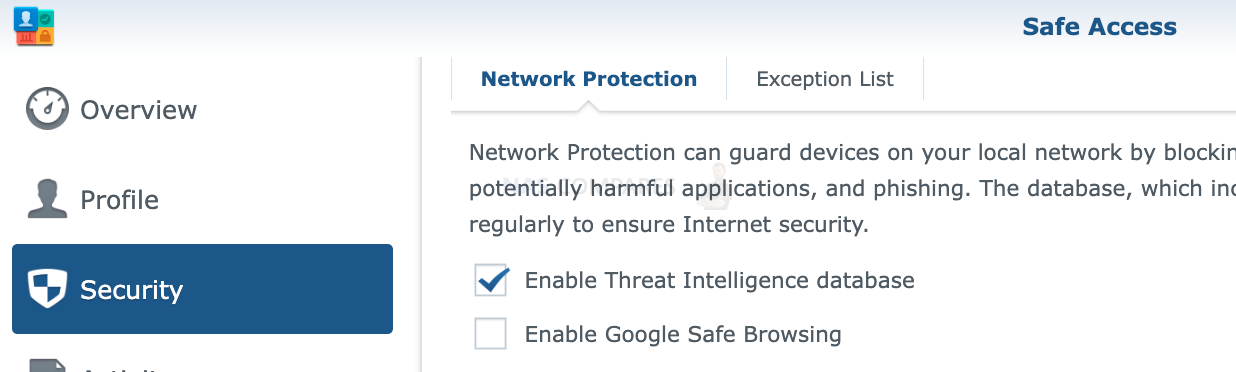
The Activity Monitor is another security feature that is available on Synology routers. It allows you to monitor the network activity in real-time, and view detailed logs of network activity. It can also be used to set up alerts for suspicious activity and analyze data to identify potential security threats.
This feature can help you to identify unusual or malicious activity on your network and take appropriate action to block it. It also allows you to see the top talkers, top protocols, and top blocked IPs.
Overall, Synology Safe Access and the Activity Monitor are useful tools for enhancing the security of your home network and protecting it from malicious activity. It’s important to remember that these security features should be used in conjunction with other security measures, such as regular software updates and a strong password policy.
| Where to Buy a Product | |||
|
|
    
|

|
VISIT RETAILER ➤ |
 |
    
|

|
VISIT RETAILER ➤ |
We use affiliate links on the blog allowing NAScompares information and advice service to be free of charge to you. Anything you purchase on the day you click on our links will generate a small commission which is used to run the website. Here is a link for Amazon and B&H. You can also get me a ☕ Ko-fi or old school Paypal. Thanks! To find out more about how to support this advice service check HERE
UniFi Routers vs OpenWRT DIY Routers - Which Should You Choose?
WHY IS PLEX A BIT S#!t NOW? IS 2026 JELLYFIN TIME? (RAID Room)
Synology FS200T NAS is STILL COMING... But... WHY?
Gl.iNet vs UniFi Travel Routers - Which Should You Buy?
UnifyDrive UP6 Mobile NAS Review
UniFi Travel Router Tests - Aeroplane Sharing, WiFi Portals, Power Draw, Heat and More
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.






DISCUSS with others your opinion about this subject.
ASK questions to NAS community
SHARE more details what you have found on this subject
IMPROVE this niche ecosystem, let us know what to change/fix on this site