Dirty Pipe Linux Weakness and Why You and your Linux Based NAS Should Care?
For those that might not be aware, a vulnerability in Linux kernel 5.8 and above was disclosed by Max Kellerman last week and publically disclosed (with a proof of concept demonstrating the weakness) and this vulnerability was reported (tracked under CVE-2022-0847) and effectively allows a non-privileged user to inject and overwrite data in read-only files, including SUID processes that run as root. This Linux vulnerability is reported to be comparable to the Dirty CoW vulnerability found in Linux from 7 years ago (CVE-2016-5195) where an exploit was used for pushing malware onto software services. Full details on the public disclosure and demonstration of the vulnerability by Kellerman can be found here, but the larger impact of this is that there are many, MANY different software platforms around the world that utilize Linux as the base of their systems and alongside Android and smart home appliances, one big advocate of Linux kernel-based development is NAS storage providers in their systems and services. Now, on the plus side, Linux was incredibly quick to implement a patch on this and the vulnerability has been closed on Linux kernels 5.16.11, 5.15.25, and 5.10.102, however, most NAS servers use different versions of the Linux kernel, as well as roll out updates to their varied hardware systems in a most bespoke fashion. This leads to them potentially running outdated kernels and leaving a door open to this exploit, posing a significant issue to server administrators. We fully expect NAS brands to roll out updates where appropriate/applicable shortly to close this vulnerability, however, one consistent thread in the past when some NAS brands have been hit by ransomware/malware exploits is when vulnerabilities that are found in older software revisions are left unchecked by the end-user (ignoring brand updates or practising unsafe network security). So today, let’s discuss the dirty pipe vulnerability, how/if it affects Synology, QNAP, Asustor and Terramaster NAS platforms right now and what you should do right now to avoid any exploits being used on your system.
What is Dirty Pipe?
In brief, Dirty Pipe is a vulnerability in Linux Kernel 5.8 onwards that allows local users to inject their own data into sensitive read-only files, removing restrictions or modifying configurations to provide greater access than they usually would have. This was first registered and made publically known by Mark Kellerman and he gives an incredibly concise and detailed breakdown on the vulnerability, how he found it and it’s implications in this article by him.
“It all started a year ago with a support ticket about corrupt files. A customer complained that the access logs they downloaded could not be decompressed. And indeed, there was a corrupt log file on one of the log servers; it could be decompressed, but gzip reported a CRC error. I could not explain why it was corrupt, but I assumed the nightly split process had crashed and left a corrupt file behind. I fixed the file’s CRC manually, closed the ticket, and soon forgot about the problem. “Months later, this happened again and yet again. Every time, the file’s contents looked correct, only the CRC at the end of the file was wrong. Now, with several corrupt files, I was able to dig deeper and found a surprising kind of corruption. A pattern emerged.”” Kellermann said.
A short while afterwards, a security advisor by the name of BLASTY updated this with an increasingly easier method of its execution and also publically disclosed it, highlighting just how much easier it made it to gain root privileges by patching the /usr/bin/su command to drop a root shell at /tmp/sh and then executing the script. This all means that it makes it possible for a user to gain admin authentication and system powers and can then execute malicious commands to the system.
Dirty Pipe PoC (https://t.co/ql5Y8pWDBj) works beautifully. 🤑 pic.twitter.com/OrRYJE5skC
— blasty (@bl4sty) March 7, 2022
These can range from malware to (the increasingly more likely) a ransomware action that would encrypt the contents of the system and demand a fee for it’s decryption. Now, the nature of this exploit at this time (for systems that have not or cannot update to the latest patch Linux kernel 5.16.11, 5.15.25, and 5.10.102 right now) is still limited as it would only be usable in the event of a targetted attack and/or the need for a further utility or application in the system to execute the follow-up command. Now the extent to which this affected NAS Drives from the popular off the shelf private server providers is actually surprisingly diverse and a big part of that comes down to how each NAS brand is utilizing Linux. More precisely, different NAS brands are running their NAS system software on differing kernels of linux that they update over time, as well as individual systems in their respective portfolio (for reasons of hardware and utility) also run slightly different revisions of Linux for their software, eg Synology and DSM, QNAP and QTS, Asustor and ADM, etc. So, how does this affect each NAS brand, if at all?
What is the Impact of Dirty Pipe on Synology NAS?

By the looks of things, Synology NAS and DSM 7/7.1 are not susceptible to the Dirty Pipe vulnerability. This is largely down to the Diskstation Manager software and services running on Linux kernel 4.4 (this will vary in subversion depending on the Synology NAS solution). The vulnerability that is executed is found in version 5.8 onwards and even if Synology update their platform to this linux revision in the near future, they would also use the patched revisions and therefore avoid the weakness. Indeed, a bold move by the brand themselves on Reddit when an official Synology rep on the /synology sub reddit made it abundantly clear (zero ambiguity) that the Synology NAS platform and DSM7 was not going to be touched by this:
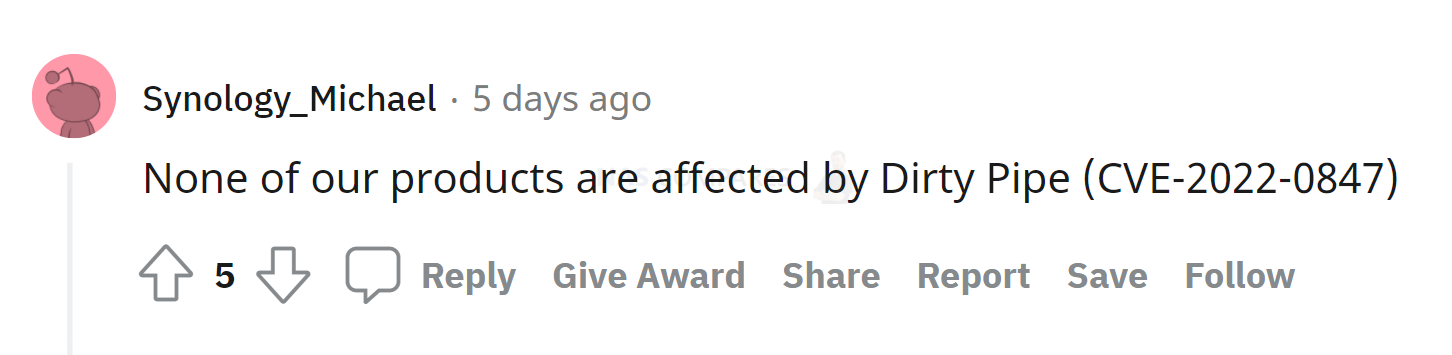
This i further highlighted by the brand’s security advisory not even acknowledging this in any way HERE. Generally, Synology are s#!t hot on updating their advisories, so this is a very good sign and I would believe them on this (as well as the kernel versions backing this up).
What is the Impact of Dirty Pipe on QNAP NAS?

QNAP NAS, QTS and QuTS run a higher revision of the Linux kernel than Synology, which unfortunately means that this vulnerability (although targetted in design and closed in it’s scope). QNAP runs kernal 5.10.60 on it’s Prosumer, business and enterprise systems and kernal 4.2.8 on it’s more affordable/ARM systems. Once again, it is worth remembering that this si a vulnerability that was found in Linux, not QTS/QuTS, so not only is this something that is not QNAP’s fault but also that issuing a patch/firmware update for their software and services will not be immediate (as they run a modified linux platform and any update needs internal implementation and testing before rolling out). QNAP issued details on this remarkably quickly via their Security Advisory pages with an updated line on this and highlighted which systems in their portfolio were unaffected (running Linux Kernel 4.X onward) as well as ones that feature the affected linux revision that an update will be available for shortly. Here is a breakdown of what they said:
-
Release date: March 14, 2022
-
Security ID: QSA-22-05
-
Severity: High
-
CVE identifier: CVE-2022-0847
-
Affected products: All QNAP x86-based NAS and some QNAP ARM-based NAS running QTS 5.0.x and QuTS hero h5.0.x
-
Not affected products: QNAP NAS running QTS 4.x
-
Status: Investigating
A local privilege escalation vulnerability, also known as “dirty pipe”, has been reported to affect the Linux kernel on QNAP NAS running QTS 5.0.x and QuTS hero h5.0.x. If exploited, this vulnerability allows an unprivileged user to gain administrator privileges and inject malicious code. The following versions of QTS and QuTS hero are affected:
- QTS 5.0.x on all QNAP x86-based NAS and certain QNAP ARM-based NAS
- QuTS hero h5.0.x on all QNAP x86-based NAS and certain QNAP ARM-based NAS
For a full list of the affected models, please check “Kernel Version 5.10.60” in the following link: https://www.qnap.com/go/release-notes/kernel. QNAP is thoroughly investigating the vulnerability. We will release security updates and provide further information as soon as possible. Recommendation – Currently there is no mitigation available for this vulnerability. We recommend users to check back and install security updates as soon as they become available.
So, if you are curious if your system is running the affected linux kernel, you can find a list of QNAP NAS systems that feature 5.10.60 below:
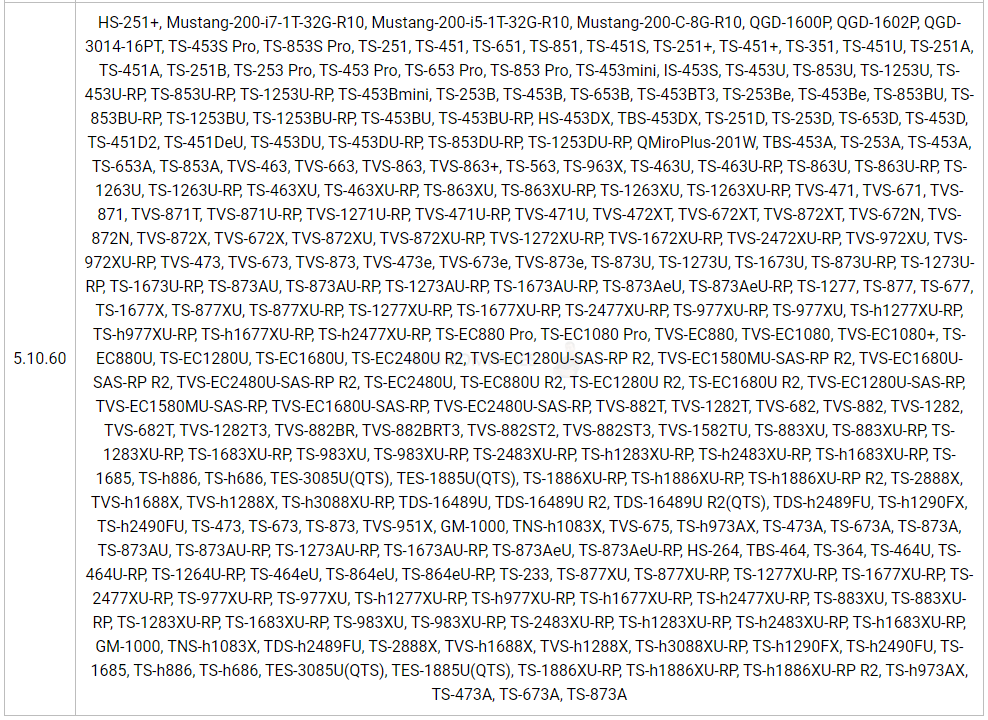
QNAP are working on this right now and although an firmware update should be available quickly, I would recommend heading to the bottom of this article for recommendations on securing your storage and network setup either in the long term OR till an official patch is issued.
What is the Impact of Dirty Pipe on Asustor NAS?

In more positive news, not only is Asustor and ADM 4 not affected by the dirty pipe vulnerability but also the brand has been fantastically loud about this in their security advisory pages. This is one of those rare occasions where a brand has added an entry to their advisory pages for a vulnerability that is NOT impacting their systems. I kind of wish we saw more of this, as even if a brand is NOT affected by a weakness that is being reported on servers, users would rather be abundantly clear. You can find out more from Asustor’s security advisory pages HERE, but the details are available below:
| Severity | Status |
| Not affected | Resolved |
Details – A flaw was found in the way the “flags” member of the new pipe buffer structure was lacking proper initialization in copy_page_to_iter_pipe and push_pipe functions in the Linux kernel and could thus contain stale values. An unprivileged local user could use this flaw to write to pages in the page cache backed by read-only files and as such escalate their privileges on the system.
Statement – None of ASUSTOR’s products are affected by CVE-2022-0847, this vulnerability issue only affects with Linux Kernel 5.8 and above. The Linux Kernel version built in ADM 4.0 is 5.4, and 4.14 in ADM 3.5.
So, they are making things remarkably clear that regardless of the current update/firmware status of your system, you are unaffected.
What is the Impact of Dirty Pipe on Terramaster NAS?

Details on the linux kernel that is utilized by Terramaster in their NAS systems in the current TOS 4 software that is available (As well as the TOS 5 beta) are still being investigated and I will update the article shortly with my findings. Early checks seem to indicate that TOS 4 is running on an earlier version of linux and therefore unaffected. However, I will confirm this and the TOS 5 beta status as soon as possible here in the article.
What Security Measures Should NAS Owners Take to Avoid Dirty Pipe?
Although the circumstances that need to execute this Linux dirty pipe vulnerability towards your NAS are quite restricted (classing this largely as a targetted attack, as a little bit more prior knowledge is needed about the targeted system in order to exploit it and execute code), this should still not leave users to remain complacent. Regardless of whether you are a QNAP, Synology, Asustor or Terramaster user, you should be actioning safe and secure working practices with your data – as well as ensuring that you have sufficient backups in place of your mission-critical and/or irreplaceable data! Here are some recommendations for your NAS setup to reduce the potential for you to be affected by any exploited vulnerability that could well be currently unidentified in your setup:
If you are concerned about being vulnerable to Dirty Pipe and want to ‘shut the doors’ a bit till a firmware update:
- Disable Port Forwarding
- Disable uPnP Auto Configuration Tools
- Disable SSH & Telnet Services
- Change Your Port Numbers
If you want to take a moment to do some security and access house-keeping:
- Disable Admin Accounts
- Enable Auto Updates
- Add 2-Step Verification
- Use Strong Passwords
- Limit App File/Folder Access to applications they do not need them
And finally, most important of all – GET YOUR BACKUPS IN ORDER!
I will repeat this as many times as it takes, but you should NOT be measuring the cost of your backups by the cost of the hardware. You should measure them by the COST to YOU if that data is permanently LOST! Additionally, if all your mission-critical/irreplaceable data is in ONE location (eg on the NAS, sent from your phones and PCs, then deleted from those to make space), then THAT IS NOT A BACKUP! That is the single repository of that data! Get a USB Backup in place, get a Backblaze Subscription HERE affordably or some cloud space in general, get another NAS – whatever it takes! If you need help arranging your NAS backups on your QNAP or Synology NAS, use the video guides below:
Finally, if you want to stay on top of the vulnerabilities that are publically disclosed on Synology, QNAP, Asustor or Terramaster, I STRONGLY recommend following and/or adding your email to the article below. We automatically crawl the security advisory pages from the top NAS brands and have created a single page that automatically lists and updates the status of known NAS vulnerabilities as soon as they are revealed.
Thanks for reading and let’s keep your data safe together!
📧 SUBSCRIBE TO OUR NEWSLETTER 🔔
🔒 Join Inner Circle
Get an alert every time something gets added to this specific article!
This description contains links to Amazon. These links will take you to some of the products mentioned in today's content. As an Amazon Associate, I earn from qualifying purchases. Visit the NASCompares Deal Finder to find the best place to buy this device in your region, based on Service, Support and Reputation - Just Search for your NAS Drive in the Box Below
Need Advice on Data Storage from an Expert?
Finally, for free advice about your setup, just leave a message in the comments below here at NASCompares.com and we will get back to you. Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.
Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.

|
 |
Synology FS200T NAS is STILL COMING... But... WHY?
Gl.iNet vs UniFi Travel Routers - Which Should You Buy?
UnifyDrive UP6 Mobile NAS Review
UniFi Travel Router Tests - Aeroplane Sharing, WiFi Portals, Power Draw, Heat and More
UGREEN iDX6011 Pro NAS Review
Beelink ME PRO NAS Review
Access content via Patreon or KO-FI





Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.







I gotta say, as someone trying to find the videos you reference.. I am lost. Your organization could be improved. Also on the newest QNAP guide tour videos.. you named part 1 as Part 1…and then never again labeled anything else. SIGH.
REPLY ON YOUTUBE
Qnap’s in mo vlog’s house
REPLY ON YOUTUBE
Hello! very good help! thank you! On the other hand, I have connected to OneDrive using HybridMount. I can see this new folder on QFile for Android but not in Qsync for Windows. How could I do that?
REPLY ON YOUTUBE
1:30 Your right a RAID is not a backup, but due to the functionality of how it’s implemented (ie. a nAS vs two external drives in sync), we call them different names, but the results are the same.
eg.. If you have 2x RAID 1 Hard drives, and one fails, the other still has your data..
If you have two external drives in sync (weather that be via software, or manually kept up to date),, if one of your external drives die, you STILL have your data safe on the other.
So, the way we think of a RAID vs backup depends on the environment itself, but they both keep our data safe if one drive dies.. ie they both serve the same purpose. For eg.. I don’t do raid, because I don’t want to loose storage capacity but I do have external drives synced.. so to me, that is just as good.
REPLY ON YOUTUBE
Your walkthrough videos are incredible provide a plethora of valuable info. It would be super helpful if you could timestamp sections. Understably it’s tricky as many of you video are long form.
REPLY ON YOUTUBE
Cheese ????
REPLY ON YOUTUBE
Is it better to use HBS 3 for time machine versus the build in qnap method by adding a user and a shared folder with smb 3? I think the second method is more flexible since I can add a user per mac and specify quota and stuff like that
REPLY ON YOUTUBE
I can’t find your updated version of QNAP NAS Setup Guide 2021/2022 #1 promised in the current version of #1 (https://youtu.be/_kCS6e1ZoiQ?t=2223). Could you provide that URL? Would be nice to have that link in this video’s description area as well us the #1 video.
REPLY ON YOUTUBE
very informative . i am movig from a drobo 5D to a qnap i wanted to know the best way to safley move 14TB of data tot he new qnap
REPLY ON YOUTUBE
Awesome vids. Thank you, mate! When enterprise versiones release?
REPLY ON YOUTUBE
Hello, I followed you previous video and now I looking at this one. I see that now you have THREE more
folders that where not there before. I see “home” “homes” and “Multimedia” can you explain where they came from? After a Drive failure and a NAS refusing to rebuild, I reset my NAS to default, formatting initializing everything, now I want my system working as it did before…..I am not seeing “default folders”
REPLY ON YOUTUBE
Thanks a lot!
REPLY ON YOUTUBE
The first guide was fantastic. This guide is extremely confusing.
REPLY ON YOUTUBE
Great stuff, I appreciate you sir!
REPLY ON YOUTUBE
FASTASTIC video as always!
If you allow me one question please
In the min 10:54 when you talked about backup the main NAS to a second NAS
using Hyperbackup, you talked about doing it in the morning when the NAS is less use
If i run the backup let say at 3am, my pc will be “sleeping”. Will Hyperbackup work even though the pc is “sleeping”?
Thanks in advance
Have a Productive and Healthy Day!
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now..
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now..
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
*I was hit, so unplugged, shutdown, external USB backs fine. Plex user, was watching at the time no issues, went to update saver denied, then found the splash screen, no on reboot, water gapped on an independent switch no WiFi etc, it instantly goes to initialization. So save to assume the service themselves have been affected. Did safe shutdown. After some time I turn on everything then I found out I’ve been truly hit by deadbolt I did as many research as I could and I found out that scott can actually decrypt the encrypted files. So I paid some money not upto what deadbolt team are asking, then he decrypted my files*
REPLY ON YOUTUBE
Good day all for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
Good day all for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
These methods are great. Was wondering if there is a way to backup files from your PC (documents downloads desktop folders) periodically to the NAS?
REPLY ON YOUTUBE
Let’s see if I have this right: QSync is going to “merge” changes made to a single file by multiple users? So it is a content management app? Just asking…
REPLY ON YOUTUBE
Don’t praise QNAP like they are always on top of stuff. It wasn’t to long ago lots of people lost data because of QNAP’s lack of viligence on security. So one time they are ahead of a vulnerability. Once doesn’t make a company great. Especially when they have a spotty past history like QNAP
REPLY ON YOUTUBE
Jesus Christ QNAP is always in the middle of some drama. I’d never buy that brand.
REPLY ON YOUTUBE
What’s the difference between QSync and regular ‘map network drive’?
REPLY ON YOUTUBE
QNAP is possibly the most vulnerable bit of kit that I’ve ever used. I’m constantly having to update for one vulnerability or another.
I’m considering just fucking them off, just building my own and using some open source solution instead, as I’m almost certain their turn around for bug/vulnerability updates or fixes will come out way sooner than QNAP manages to push it out
REPLY ON YOUTUBE
I just started researching NAS storage and have come to the conclusion, reading and watching multiple videos on its vulnerabilities, that I’ll stick with DAS.
REPLY ON YOUTUBE
I have my NAS closed off from the Internet completely. I run Plex on a separate PC that reads my media from the NAS. I allowed UPnP to open the necessary ports for my QNAP NAS and was getting brute force attacked with login attempts. That put me off opening it up and sharing data directly off the NAS.
REPLY ON YOUTUBE
Thank you for the heads up!
REPLY ON YOUTUBE
Thank you for early warning!
REPLY ON YOUTUBE
I have one hair follicle left after trying EVERYTHING to get a Qnap TS-212 to backup to a new TS-231P3. The ‘problem’ is that HBS is different on the old NAS and no matter what I do, I cannot get it to allow a backup. So, I worked around the problem by accessing the newer TS-231P3 using HBS 3 and telling that to ‘restore’ the folder of all my work, rather than backup. I’m at 5% and counting. Fingers are crossed.
REPLY ON YOUTUBE
All good tips, very informative and helpful in times when QNAP isn’t releasing any real mitigation for this. I do take issue with “changing your port numbers”, which usually only discourages the beginner ‘hackers’. It’s an example of security through obfuscation and can lead to a false sense of security: this is dangerous..
REPLY ON YOUTUBE
I know on my Synology, it’s a good idea to change the default admin username and use a customized name.
REPLY ON YOUTUBE
Good info mate!
REPLY ON YOUTUBE
This biatch burned my pipe….
REPLY ON YOUTUBE
I’m always afraid that if I mess with port numbers that I will break something. Perhaps a video providing a bit of guidance on port numbers generally, what should be changed, the ranges that they could be changed to, etc.
Thanks for the daily lesson Robbie. Every video is an education.
REPLY ON YOUTUBE
Is there something specific to do to make Qsync works ? I can’t connect to my NAS from windows with it. With the correct IP, login and password
REPLY ON YOUTUBE
If you add a 00:00 time to the chapter list it will add the chapters to the scrubber (video progress bar), you can for example call it: 00:00 Intro
Great videos, love the in depth explanation. It is easy to set up the NAS, but to really use it is hard, so thanks a lot!
REPLY ON YOUTUBE
Thank you very much for these helpful videos. I’ve got a TS-128A and a TS-230 to setup and I’ve only had experience with Synology and WD NASes previously. Seems like QNAP is more complex but more flexible at the same time with generally better hardware for the price.
REPLY ON YOUTUBE
Loving the videos! Thank you 🙂
My QNAP arrives next week. I’m at about 36 mins in this video so far so if my question get’s answered then don’t worry… I’m currently using Dropbox to sync a folder we’re both working in on my computer and a colleague’s computer over the internet. How would I do this with QNAP?
AND I send files to clients by right clicking and hitting “make transfer” with Dropbox. Can I do that with QNAP or do I have to use the web interface?
REPLY ON YOUTUBE
“previous video i did guide You through how to set up a snapshot”…
You mean in video: QNAP NAS Setup Guide 2022 #1 ??
there i didnt found that.. 🙁
REPLY ON YOUTUBE
Your Synology NAS Setup Guide videos are still NOT AVAILABLE (only #1 – #3)
REPLY ON YOUTUBE
This was great. Keep it up with QNAP. Can we explore some of their media Apps? Believe me sir – you do everything right! Happy New Year!
REPLY ON YOUTUBE
HEHEEH, Yes, We absolutely Like chess.
REPLY ON YOUTUBE
When I open Snapshot Replication app on DS7, it warns me that my volume is recording ‘last file access time’, and this may affect snapshot performance. It tells me I can disable this by going into Storage Manager, but that setting is nowhere to be seen. Any ideas?
REPLY ON YOUTUBE
Gouda explanation, very clear and easy to follow, was a bit Cheesy but I’ll take it because there’s stiltonnes of things I have to learn, but with this info my backups will be as robust as a Roquefort ???????? thanks as always
REPLY ON YOUTUBE