Although 45 days have passed since Western Digital was successfully targeted in a cyber attack, the brand has only recently opened up a little further on the nature and impact. Although we covered this in alot of detail back in the middle of April (see link below), WD has only recently publicly shared a little of the data was accessed, as well as contacting potentially affected users. Also, in that time, several other prominent online security sources have added to the discussion, wither independently or after being contacted by the attackers to verify the legitimacy of their claims. For many, the 10-day suspension of the WD My Cloud services might have been the last they have heard about these events, assuming that this had been fully resolved. Sadly that is not the case and whether you are a WD NAS user or not, it might be worth taking a moment to get updated on the ongoing security issues surrounding a big name in NAS and one of the biggest names in storage!
Previous News Port on this HERE – Western Digital Cyber Incident Update- WHAT HAPPENED?
Continued Taunting and Claims By the Hacker Group, BlackCat via ALPHV
Towards the end of April (first on the 18/04 and then later on the 28/04) Dominic Alvieri, a Cybersecurity analyst and security researcher (find his twitter HERE), detailed online information/posts shared by Blackcat on the site Alphv with regard to the data obtained, claims of the WD’s response, lack of security care, information surrounding their intentions and details of the data obtained. While the perpetrators claim not to be part of the ALPHV ransomware group, the posts were shared via their data leak site to highlight the current status quo with Western Digital.
You have to read this final warning.@westerndigital @BleepinComputer https://t.co/P625juLWo1 pic.twitter.com/ohvc2QRP7g
— Dominic Alvieri (@AlvieriD) April 18, 2023
The text in the posted pages is as follows:
Western Intelligence or Western Digital: The Fine Line Between Selling Drives and Espionage 4/18/2023, 12:36:47 AM
Oh Western Digital, The chances we give you, but the continuous egotistical behavior shown indicates you don’t even care about the well being of your company in the slightest. Even the largest companies would want to know every detail they can about what was taken, but Western Digital didn’t even bother to contact us. I am confused by this because we offered to give them file trees of everything, as all groups do when extorting their victims. But as stated they did not even contact. How sad, but I cannot say I’m surprised. At the helm of this company you have a corrupt former Cisco Executive. We thought after our interview with TechCrunch maybe they’d come to do some exploring to find out what data was taken, though. If you are investing in this company– I would advise encouraging the leadership to at least find out what was taken.
Please do not feel sorry for these hounds. I can assure you that they are far more corrupt than you realize, and we have evidence to support our assertions. It’s approaching fast. But, we are not superior to them. We apologize but we won’t divulge if they pay.
Important documents will be released while priceless artifacts will be sold. At this moment, nothing has been sold or leaked. Despite our attempts over the past two weeks, Western Digital has not responded to any of our contact attempts. Even the most naive organizations would want to know precisely what was taken, this situation demonstrates the lack of corporate governance. Have a look at how far we were able to travel through their network, for example. They are corrupt and disregarded everything, thinking nothing would happen. News flash: When they filed Form 8-K with the Securities and Exchange Commission, they misrepresented several details regarding our intrusion, purposefully.
It appears there is additional speculation. No worries everyone we will clean it up. We have their firmware too.
We will fuck you until you cannot stand anymore Western Digital Consider this our final warning.
This was followed up by Dominic by further shared posts by Blackcat:
BlackCat on Western Digital part 2.
“We’ve seen speculation when it comes to customer data. To clarify we obtained a full backup to their SAP back office.”@westerndigital pic.twitter.com/Sm7eg2zmKz
— Dominic Alvieri (@AlvieriD) April 28, 2023
The text in the posted pages is as follows:
Western Digital Chronicles II: The Weekly Descent into Oblivion
4/28/2023, 10:10:40 PM
The last I recall we said something along the lines of “I will fuck you until you cannot stand anymore” I guess they thought we were surely joking.
He didn’t get in touch or glance at the webpage. Don’t be concerned, David. I’ll dismantle your wealth now. You appear so immense and influential.
Beginning next week on an unspecified day, we will share leaks every week until we lose interest. Once that happens, we will put their intellectual property up for sale, including code signing certificates, firmware, personally identifiable information of customers, and more.
We’ve seen speculation surrounding customer data. To clarify, we obtained a full backup of their SAP Back Office, which dates back to the last week of March. The backup contains everything (cont)
The page also contains an additional screenshot of a template that presumably was intended for WD users/customers that was to be tailored to impacted users that Blackcat claims to have obtained alongside a plethora of other internal data:
Dear Customer
wanted to notify you that Western Digital recently learned of a network security incident affecting some of our systems. When we become aware of the issue, we quickly launched on investigation with the assistance of leading outside security experts and proactively took some of our systems offline. We are investigating this situation and taking steps to secure our systems. We also are coordinating with law enforcement. Our relationship with you is very important to us and we appreciate your patience while we work through our investigation
SPECIFIC IMPACT TO INDIVIDUAL CUSTOMER IF APPROPRIATE
As a precaution, we have temporarily removed access to our engineering labs and you will not have access to (YOUR SHARED/ lob. We regret any inconvenience to you and your teams and would i ensure you that restoring network access is a top priority (include species of engineering lab acces impact to timeline/deliverables we con
We will keep you informed of our progress as appropriate, and please let me know if you have any questions
Thank you for your ongoing support
Finally, there as details of a shared morning video call with WD Security Threat specialists. All of this in efforts to draw a line through speculation when it comes to customer data and clarify their claims that they have obtained a full backup to WD’s SAP back office
This is a black eye for Western Digital.
BlackCat even posted an early morning video conference “with the finest threat hunters Western Digital has to offer.” https://t.co/QURl2NCScW pic.twitter.com/Y0ElQXHET0
— Dominic Alvieri (@AlvieriD) April 29, 2023
Alongside this, BleepingComputer reports that Western Digital had screenshots of internal emails, files, and video conferences pertaining to its response efforts to a cyberattack in the previously covered March leaked by BlackCat (via Alphv) after the group threatened significant damage to the firm should it refuse to pay the ransom (also first detailed over on TechCrunch).
WD Response and Alerting Its Customers
On the 5th May, Western Digital provided several new updates to the ongoing data security attack, though all of which were a little late out the gate compared with the continued deluge by the attackers themselves and communication with editor platforms (and security experts online up to this point). First, there was an official press release HERE that (focusing on the network security incident) stated the following:
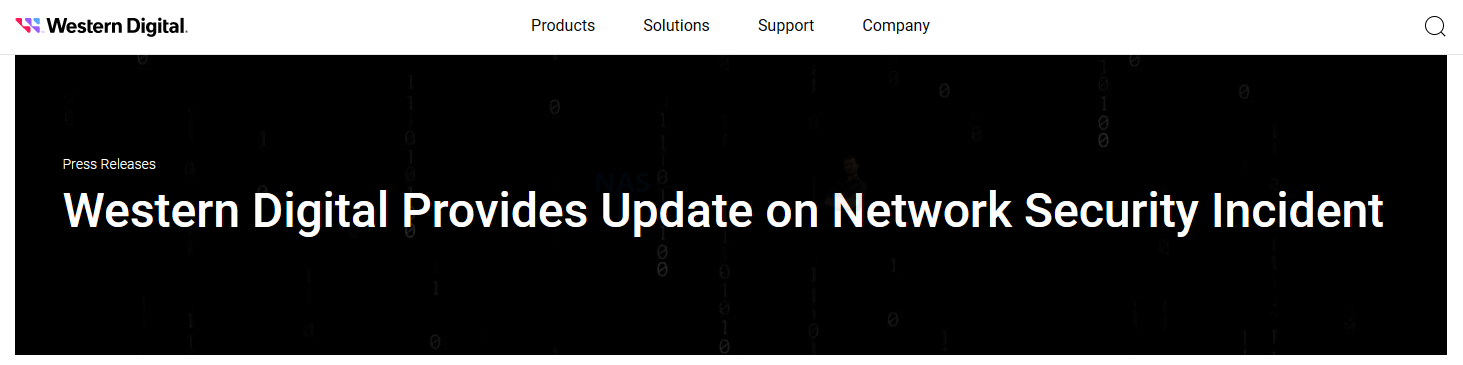
05-05-23 Western Digital Corp. (NASDAQ: WDC) today provided an update on a network security incident involving the Company’s systems.
“On March 26, 2023, we identified a network security incident where an unauthorized third party gained access to a number of the Company’s systems.
On April 2, 2023, we disclosed that upon discovery of this incident, we implemented incident response efforts and initiated an investigation with the assistance of leading security industry experts. This investigation is underway and includes analysis to understand the nature and scope of data obtained by the unauthorized party.
As a precautionary measure to secure our business operations, the Company proactively disconnected our systems and services from the public Internet. We are progressing through our restoration process and the majority of our impacted systems and services are now operational. Our factories are and have been operational throughout this incident and we are shipping products to meet our customers’ needs. While initially impacted by our proactive measures, as of April 13, 2023, My Cloud service was restored. Account access to Western Digital’s online store also was impacted and is expected to be restored the week of May 15, 2023.
In collaboration with outside forensic experts, we confirmed that an unauthorized party obtained a copy of a Western Digital database used for our online store that contained some personal information of our online store customers. This information included customer names, billing and shipping addresses, email addresses and telephone numbers. In addition, the database contained, in encrypted format, hashed and salted passwords and partial credit card numbers. We will communicate directly with impacted customers.
We are aware that other alleged Western Digital information has been made public. We are investigating the validity of this data and will continue reporting our findings as appropriate.
Regarding reports of the potential to fraudulently use digital signing technology allegedly attributed to Western Digital in consumer products, we can confirm that we have control over our digital certificate infrastructure. In the event we need to take precautionary measures to protect customers, we are equipped to revoke certificates as needed. We’d like to remind consumers to always use caution when downloading applications from non-reputable sources on the Internet.”
This was also joined by a message that was sent out to WD customers. Detailing a little more on the data that has been obtained. Though it does not detail the extent of the volume of impacted users or if the vulnerability in question that the attackers used has been fully neutralized:
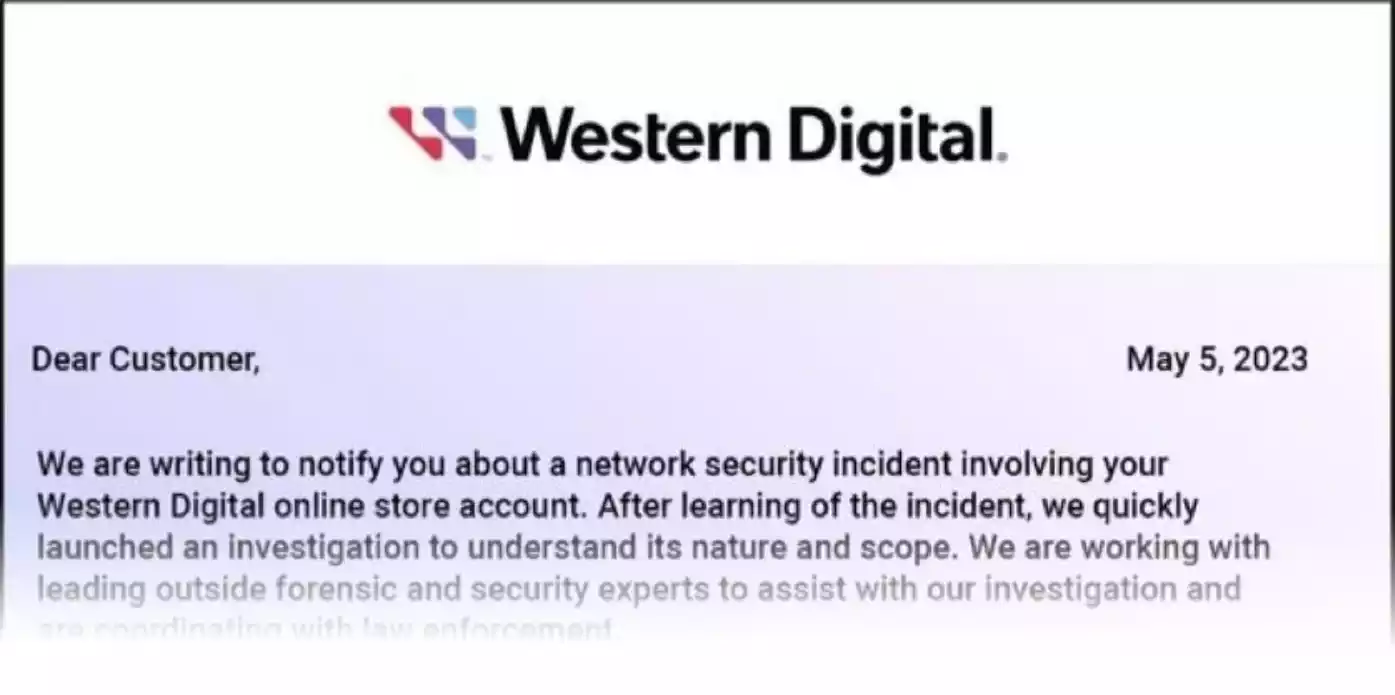
Original text:
Dear Customer,
We are writing to notify you about a network security incident involving your Western Digital online store account. After learning of the incident, we quickly launched an investigation to understand its nature and scope. We are working with leading outside forensic and security experts to assist with our investigation and are coordinating with law enforcement.
Based on the investigation, we recently learned that, on or around March 26, 2023, an unauthorized party obtained a copy of a Western Digital database that contained limited personal information of our online store customers. The information included customer names, billing and shipping addresses, email addresses, and telephone numbers. As a security measure, the relevant database stored, in encrypted format, hashed passwords (which were salted) and partial credit card numbers.
We have temporarily suspended online store account access and the ability to make online purchases. We expect to restore access the week of May 15, 2023. As a precautionary measure, you can take the following steps to help protect your
personal information from potential misuse:
Be cautious of any unsolicited communications that ask for your personal information or refer you to a web page asking for personal information. Avoid clicking on links or downloading attachments from suspicious emails. Check whether your email account has spam settings to help you detect or block suspicious emails.
We hope this information is useful to you. If you have any questions regarding this incident, please call 855-493-7867, Monday-Friday, 8am-5pm PST.
As good as it is that WD are finally sharing more information on the impact of this, since the relative lack of noise they were making on the initial security attack (which led to the WD shop being taken offline and them suspending their WD My Cloud remote services), this is still quite a vague detail on how/if/who has been impacted here. I appreciate that they need to remain guarded (both from a continued security stance and perhaps legally), but given the scale of users that still use their relatively low barrier and affordable NAS solutions, this does seem something of a lacklustre response! Add to that the question marks of if customer data stored in the WD Store and/or the extent of confidential information that is potentially going to be sold to the highest bidder – I think WD needs to be more proactive on this!
The WD Shop is Still Open – Sort of…
The WD Shop has not really been back to 100% since the initial impact of the security attack. Intermittently, we saw the store display this message:
When the store was accessible, the header of the site continues to display the following message:
That said, products and series catalogues can now be accessed. However, you are still not able to make purchases, instead being redirected to resellers in your area:
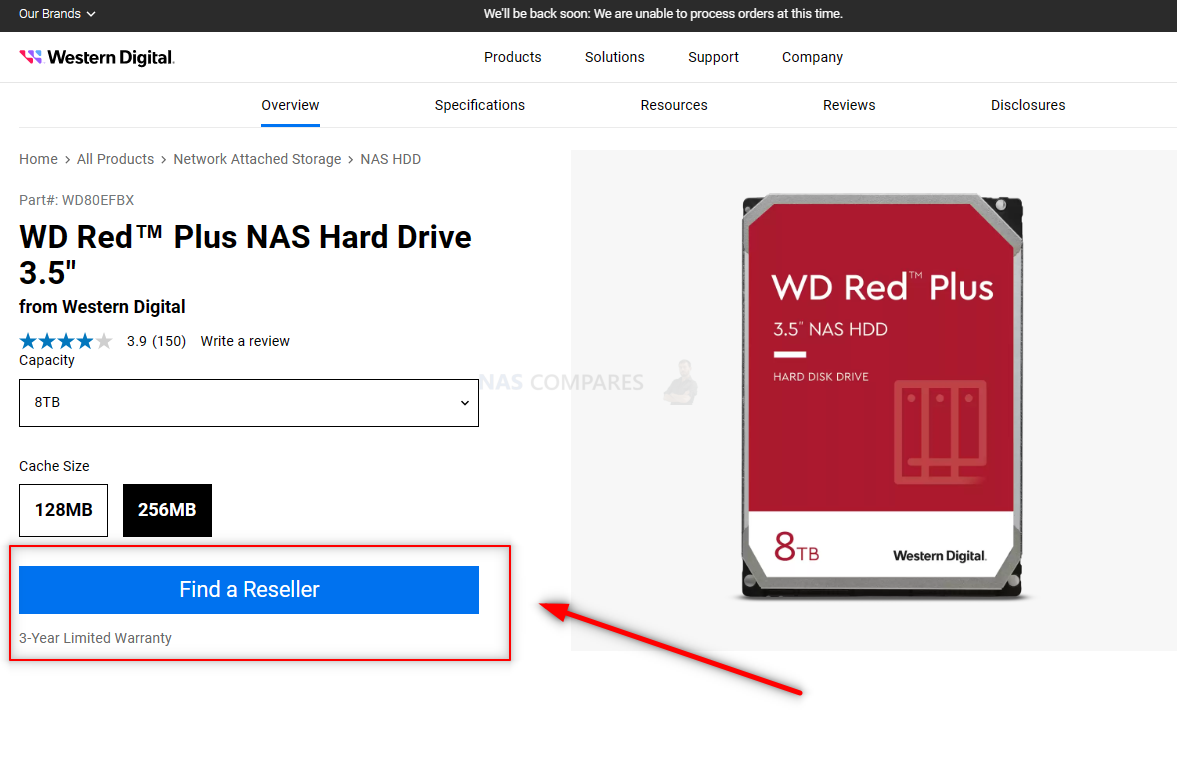
The concern here of course, is whether the vulnerability in question has been blocked and how much of the WD Shop infrastructure is/was/could have been involved in the cyber incident. WD states that they expect to reinstate access to the WD Shop by May 15th, 2023.
If I Use a WD NAS or Have a WD Shop Account – What Should I Do?
![]()
If you are an existing (or even former) WD NAS user, alternatively, you are someone who has shopped at the WD Shop before, then I would certainly recommend that you follow the following guidelines:
- As mentioned in WD’s own messaging, be very mindful and careful with any communication that pertains to be from WD/Western Digital regarding your account. Do NOT provide any further information or account details if prompted (as this might likely allow assisted brute force access hacking). Additionally, check all mail domains of any communication you receive and check any URLs you are directed towards in advance (i.e copy link and paste to view before using) in order to check the destination domain
- If you have not already, change your WD NAS admin/general-user admin login credentials and instate 2-Step Authentication were possible. There is still no confirmation that complete and unencrypted information of user account credentials has been leaked – but why take that chance?
- Ensure your off-site/off-system backups are in order. If an attacker is able to fully access or even partially access your WD NAS system via even moderately powerful user credentials, they are far, FAR more likely to push for ransomware (encrypting your data without leaving a local key) than deletion/destruction, as there is no means of exploiting this for payment. So GET YOUR BACKUPS IN ORDER. Do not rely on a USB backup unless it is only connected during periodic backups and automatically ejected afterwards.
Thinking of leaving WD NAS? Use my Comparison Guide video below to find out which of the other big names in NAS hardware and/or software best suits your needs:
📧 SUBSCRIBE TO OUR NEWSLETTER 🔔
🔒 Join Inner Circle
Get an alert every time something gets added to this specific article!
This description contains links to Amazon. These links will take you to some of the products mentioned in today's content. As an Amazon Associate, I earn from qualifying purchases. Visit the NASCompares Deal Finder to find the best place to buy this device in your region, based on Service, Support and Reputation - Just Search for your NAS Drive in the Box Below
Need Advice on Data Storage from an Expert?
Finally, for free advice about your setup, just leave a message in the comments below here at NASCompares.com and we will get back to you. Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.
Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.

|
 |
The BEST NAS of 2026.... ALREADY??? (UnifyDrive UP6)
How Much RAM Do You Need in Your NAS?
A Buyer's Guide to Travel Routers - GET IT RIGHT, FIRST TIME
Jonsbo N6 DIY NAS Case Review
The Best Bits (and Worst Bits) of NAS of 2025!
Minisforum MS-02 Ultra Review
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.





How come Synology isn’t updating their hardware for the home consumer market? 1gbe is a joke and we should be good ready to use hardware instead of them nickel and diming.
REPLY ON YOUTUBE
How come Synology isn’t updating their hardware for the home consumer market? 1gbe is a joke and we should be good ready to use hardware instead of them nickel and diming.
REPLY ON YOUTUBE
How come Synology isn’t updating their hardware for the home consumer market? 1gbe is a joke and we should be good ready to use hardware instead of them nickel and diming.
REPLY ON YOUTUBE
How come Synology isn’t updating their hardware for the home consumer market? 1gbe is a joke and we should be good ready to use hardware instead of them nickel and diming.
REPLY ON YOUTUBE
Using terra f2-223 for a month 241028. First time seeing a long straight line of single hdd 280 MBps files transfer speed. Currently still running is very old slow wd ex2 clocked 50k+ hrs. Selected terra for its big discount with good specs.
REPLY ON YOUTUBE
You should make a “NAS brand tier list” or “NAS OS tier list.”
REPLY ON YOUTUBE
I’m still disappointed that consumers are still tolerating the planned obsolecence “2.5Gb” ethernet ports. They are deliberately disabling 5G and 10G. There is no 2.5Gb standard; 802.3bz is the multi-gig standard and when properly implemented provides auto-negotiated 1G, 2.5G, 5G, and [802.3an] 10G based on the network nodes and the cable quality.
The main reason I buy these appliance style NAS boxes is the low power consumption compared to what I could build. I prefer those that are relatively closer to a standard vanilla open OS with out of the box defaults and packages that are well coordinated with the hardware. As opposed to proprietary stuff that tells me how I should use my device, or empty hardware with a separate generic OS that I need to fully setup from scratch. I have rarely had good long term experience with proprietary products (In any market not just computing.).
Synology’s primary software advantage came from the Linux base that they built the graphical interface on and that they didn’t try to prevent users from doing command-line linux type management. However, I haven’t been impressed by their slow move away from that to push their proprietary features, and even back in DSM-5 they had some rather strange not-invented-here choices deep in the system like the layout of the virtual filesystem and logical block devices.
REPLY ON YOUTUBE
Yeah, the SMR thing was one of the worst PC news disasters of the last decade
REPLY ON YOUTUBE
Thanks to you I discovered Unraid, now that my 12 yrs old loyal Thecus N4100Pro is doing its job hanging together from hopes, dreams and duct tape, ready for retirement.
REPLY ON YOUTUBE
the critical question that is still unclear to me: do you LIKE seagulls or NOT? ????♂️
REPLY ON YOUTUBE
I bought a My Cloud Mirror EX2 a very long time ago, and although it has almost no use other than back up, I still get regular OS updates from WD. How many of the competitors still provide updates to their systems well after warranty expires? I need to buy a new NAS, and this is an important factor in the decision I make. WD although favourable from that POV – don’t seem to be updating their NAS solutions with any kind of urgency.
REPLY ON YOUTUBE
Excellent comparison, thank u very much!????????
REPLY ON YOUTUBE
Good information. You can improve with shorter to the point video. And improve on pronunciations/enunciation. I mean… @14:20 did u just say I hate seagulls?
REPLY ON YOUTUBE
Which ones are the most reliable?
REPLY ON YOUTUBE
Great video! I currently have FreeNAS running on a Dell T410 server with 6 hard drive bays, and after watching your video, you have convinced me to stick with my current server and upgrade to TrueNAS Core for it’s security and it’s ability to recover from 1-2 failed drives without losing data. Thanks for the great video!
REPLY ON YOUTUBE
as a previous long time user of PLEX and now a 2 year user of Emby, I can say without hesitation that emby appears to be more robust in reliability and maintainability…. by a lot!
REPLY ON YOUTUBE
WD NAS doesn’t last more than 3 yrs. It’s that bad.
REPLY ON YOUTUBE
Do you know about the WD red analytics putting drives into warning after 3years working hours. If not would you be able to investigate. Would you explain what you would recommend doing if they go into warning or recommendations for new drive or don’t buy WD red etc. Thanks
REPLY ON YOUTUBE
I have 2 of the Synology 9 bay (DS18xx) units and want to note that they are far more than NAS. The Synology DS18xx units are complete servers .. capable of not only DHCP and other mundane chores but also are capable of hosting VMs be they Docker containers or VirtualBox etc. Highly recommended.
REPLY ON YOUTUBE
What can we do to protect our personal data taken…e.g. addresses, etc.?
REPLY ON YOUTUBE
The Red Plus hard drives I ordered from WD on March 31 showed up quietly on my doorstep on May 5 (no email stating the package was on its way). So at least they’re shipping existing orders. The next day, I got the notification letter.
REPLY ON YOUTUBE
The store says to buy from resellers and has Amazon listed as a reseller. But they have a long history of not giving warranties when bought off of Amazon. This might be from 3rd party sellers only not sure. A commonly refusal is due to it being a European s/n or some other reasoning. I wanted a 18tb Red Pro but not wishing any warranty issues I ended up purchasing an 18tb Iron Wolf Pro complete with a 5 yr warranty. I got an email as well indicating my information was compromised by using their online store. I know alot of companies get hacked, but they way WD us handling this by keeping info from people for way too long is unacceptable. My business has now shifted to Seagate, sorry WD, but responsibilities to your customers should also be a priority which is clearly not the case.
REPLY ON YOUTUBE
Well i would like to know what there going to do for comp for people as this has taken over a month to let people no and damage could all ready be done and all the stress of people worrying now.. there is a eu law i think they have to adbied by witch is the gdpr
REPLY ON YOUTUBE
Embarrassing? ????????♂️
REPLY ON YOUTUBE
Update: There is no update. They’re still incompetent.
To not be able to RMA, Return or anything other than speak with people who say their hands are tied is ridiculous. Especially from a company being of this caliber. My support for them is wavering now with this latest situation.
REPLY ON YOUTUBE
I suddenly kept getting loads of spam verification code messages last few weeks. Then I got the email. Now I know why. I’ve not been this annoyed about a hack since dropbox. Tech companies clearly not spending enough to protect themselves. The lastpass situation was unusual.
REPLY ON YOUTUBE
I’ve just replaced mine WD EX2 Ultra for DS920+ with DX517. Just to stay safe in case of problems. Seen you can’t order anything from shop.
REPLY ON YOUTUBE
Love your channel but would also love to see more on long term reliability of units. I have just recently purchased the Qnap TVS-472XT-i3 although I love the unit and have go it fully expanded I hear horror stories of these units failing after Two years. This could in many cases also be caused by recommendations by many YouTube reviewers of putting them away in a cupboard or other enclosed area to avoid hearing noise this certainly would not help longevity and in most cases would cook the units and cause premature failure. I always keep an eye on the temperature of my unit and increase the fan settings when required ie if it is set on quite mode and we have a temperature increase. Keep up the good work.
REPLY ON YOUTUBE
Just stay away from Asustor , Zero support, no spare parts available . over priced Chinese garbage
REPLY ON YOUTUBE
QNAP has had a horrific history of security issues… Security experts advice I’ve heard on QNAP? USE SOMETHING ELSE
REPLY ON YOUTUBE
Okay…. I’m confused. This video says that Synology and QNAP are the way to go for Plex servers, but in previous reviews NASCompares recommends Asustor, especially the Lockerstor Gen 2 because of its processor with embedded graphics, whereas the latest from Synology use older processors or processors without graphics so Plex transcoding is very limited. Am I missing something>?
REPLY ON YOUTUBE
I’ve just ordered dx517 to add to my 920+ to replace my WD EX2 Ultra. Thanks for all the knowledge you are sharing.
REPLY ON YOUTUBE
In my world 27 minutes isn’t a long video especially when its full of useful information. I already have a homebuilt NAS running UnRAID but I’m watching anyway. ????
REPLY ON YOUTUBE
Neat!
REPLY ON YOUTUBE
I had a WD DL4100 which ran fine for 7 years with just a couple of drive failures. However I have been forced down a path of changing it after it completely stopped working. It appears to be “bricked” due to a known fault with the Intel Atom chip. Still, I got 7 years out of it.
REPLY ON YOUTUBE
You’re jibbering and jabbering so mutch so it’s really rubbish to listen to!
REPLY ON YOUTUBE
Robbie, I got a WD Mycloud EX2 Ultra for my first NAS about five years ago. The real problem with the WD products are that they are woefully under powered with 1.3 GHz CPUs and what passes for a Manual or User’s Guide is incomprehensible. It still works and has a job as household’s scratch drive, but my two Synology NASes to all the work.
REPLY ON YOUTUBE
Best channel for NAS related content. I have a raspi w OMV6 and an old PC running truenas scale
REPLY ON YOUTUBE
Discovered your channel a few months ago and I chose the TERRAMASTER F4-423 based on your extensive/exhaustive review..( the look on your face as you tried to put it back together is comedy GOLD.)
Installed TrueNas on 4X WD 12 TB HDD’s , installed 32 GB’s of RAM and 2X 1TB nVME’s as cache and this thing is smooth like ‘buttah’.
BTW , have you ever noticed how few seagull’s there are around Oriental restaurant’s?????
REPLY ON YOUTUBE
I think you missed the boat by a wide margin on this one. The reason many people purchased WD NAS devices was simply because they were the ones available at retail outlets alongside the Seagate – I think it was called the personal cloud server? Anyway, WD and Seagate were what people could find in their local equivalent of BestBuy. They knew the brands because they were who sold them regular hard drives so they were considered safe. The people owning these systems could probably figure out most NAS on the market these days, but probably don’t want to spend a lot of time doing so, so easy of use and simplicity are likely the main selling points. Honestly, the Synology DS423 (not plus) would likely be the easiest transition for WD users. However, the DS423 doesn’t appear to be a global product– it still only appears under the Singapore-only Synology website.
REPLY ON YOUTUBE
Thank you for that good video. Greetings from Switzerland!
REPLY ON YOUTUBE
I thought that seagull was my cats lmao.
REPLY ON YOUTUBE
As a Synology DS918+ owner who bought that model based on the raving about Synology’s software and who has used it for 4 years, I don’t see why their software is so raved about, as I feel like it gets in my way and doesn’t have the capabilities I need (their Reverse Proxy GUI for example is no where near as fully featured as proper nginx configs) much of the time… but I’ll freely admit to not giving a single solitary fuck about any of their first party apps either, as I’d rather use Docker Compose, Nextcloud, Jellyfin, Bitwarden, Backblaze B2, etc., and I don’t have surveillance cameras, etc.
REPLY ON YOUTUBE
I’ve always had Synologys (3 DS9XX+ models now, and recommended many to friends/co-workers and family over the 10 years) and have always been really very happy with them, up until recently that is, when I look at the current upgrade/replacement options on offer. It looks like they’ve pretty much cut middle ground “SOHO/Enthusiast” users out of the picture, making us choose between higher priced “business” orientated units, or lower specced “home” use units! Maybe my next NAS will have to be Qnap! I just don’t look forward to all the tinkering and maintenance that Synology save you from so very well and I’ll certainly miss DSM.
REPLY ON YOUTUBE
Just bought my fist My Cloud Home earlier this year and I got slap in the face with WD Discovery will no longer be supported in June 2023.
REPLY ON YOUTUBE
You forgot the most important thing. Company financials. Which of these are financially weak and disappear in 5 years leaving me high and dry without any security updates.
REPLY ON YOUTUBE
Since you are focusing on current WD NAS owners, I would suggest that you must first recognize that these owners are more than likely to be non-tech types. That would completely leave out TrueNAS and UnRAID as alternates. I own QNAP, Synology, and Terramaster NAS and, having spent a lot of type mucking about with them. Synology would be my pick by a wide margin among that group. If you want remote access, Tailscale is free and available in the app store and is dead easy to setup.
REPLY ON YOUTUBE
While not perfect, Synology has a consistently better security track record than QNAP especially in more recent years. I didn’t see that touched upon in this video and was surprised.
REPLY ON YOUTUBE
can you do it less wordy?
REPLY ON YOUTUBE
Thanks for the video. I have an 4th gen i5 as a samba server and it has issues uploading 2.5gb bandwidth. It can receive at 2.5gb and that is my reason for wanting to upgrade.
REPLY ON YOUTUBE
To be honest, I stopped using anything WD even an external USB drive that I bought a WD passport sometimes it loads sometimes it doesn’t load leave it plugged in for ages and when it warms up then it will load I’m just moving away from WD. I just don’t think they’re reliable company for anything.
REPLY ON YOUTUBE
Truenas works great for me !
REPLY ON YOUTUBE
I’m a long term user of XigmaNas. Highly recommended.
REPLY ON YOUTUBE
It just feels like wd is getting left behind for NAS in terms of competitiveness in particular for software. Recently their cloud solution got hacked into.
Synology, QNAP, Asustor, Truenas and Unraid are good picks if you are looking for a nas. Not sure about Terramaster cause i never looked into it.
Truenas has another advantage. It’s free and has zfs. Although for a beginner the initial learning curve to setup and manage it may be a bit higher compared to the other alternatives mentioned. But once you figure it out, it’s not that hard.
One of the important factors for a newbie, they may want a prebuilt NAS because they have no idea what components to get or the skills to assemble it themselves. This is one advantage brands like Synology, QNAP and Asustor have over the others, and also comes with some sort of support. Not to say you can’t get a prebuilt for truenas and unraid, there are those as well if you look around.
I settled with a QNAP since it just works and is prebuilt. When the firmware is end of life, i was able to flash truenas to replace the original QTS OS. So this breathed in extended life with an actively maintained OS. So just because you buy 1 brand, doesn’t necessarily mean you’ll be stuck on that nas OS forever. There may be an option to reflash with an actively maintained os assuming it can be supported, so DYOR.
REPLY ON YOUTUBE
First to arrive – your Seagull buddy????????????????????
REPLY ON YOUTUBE