Deadbolt Ransomware Attacking NAS Drives Again – This time it is Terramaster
It pains me to make this post, but yes, Deadbolt ransomware has once again attacked NAS drives and this time the target is Terramaster devices. Although exact details on the attack vector of this ransomware are yet to be confirmed (though I will be updating this article as more information arrives), it looks like a very similar attack to those that affected Asustor last week, using very similar display methods of highlighting the means of paying the ransom, as well as similar ways that people have been alerted to it on their individual systems. Likely candidates at the time of writing point to this either being based around a UPnP weakness (similar to a previous ransomware exploit that was used) or weak network management (either in the ports used or in 3rd party applications poking holes in your firewall etc in order to facilitate remote access). As mentioned, the details are still rather murky and the first reported hit by users online was around 10 hours ago, so similarities in how people have arranged their network/system services are slowly getting pieced together. If you DO own a Terramaster NAS drive right now, I would make the following recommendations:
- Run a Backup! But check you have not been already hit by the deadbolt ransomware and inadvertently overwrite your ‘god’ backups. I would STRONGLY recommend where possible (space/budget) running a completely new and independent backup of the whole system or at the very least your irreplaceable/mission-critical data
- Disconnect your system from ANY internet connection unless you are 100% confident that your network security is secure (even a VPN doesn’t avoid the fact some apps and services open router ports as a necessity)
- Check your system logs for any large number of IP login attempts. Not strictly necessary in this case as the attack vector is still unconfirmed at the time of writing, but check nonetheless
- Power Down your device unless you are 100% confident that you are untouchable. Although deadbolt is actioned INITIALLY over the internet to push command to the system to conduct a large scale encryption command, delete the encryption key and amend the login screen to their own payment window and key entry. So, if you are BEING attacked by deadbolt ransomware, disconnecting the system from the network internet is not enough (as from THAT point, all operations are being conducted locally (ie inside the system). So power down your device until Terramaster issue a patch to close whatever this exploit is that deadbolt is utilizing
- At the time of writing, we are still awaiting further information on the deadbolt Active Process (i.e in the task/resource monitor). When that is established, you can use SSH and a suitable command client to patch in and kill the process, HOWEVER, you should disable SSH for now if you HAVE NOT been hit, as this manner of control is how the bulk of ransomware attacks are conducted automatically
- Change credentials for the admin account. Although TOS 5 (previewed last month here on YouTube) has the option to disable the admin account (as well as a kill switch for all remote access), the current version of TOS 4 does not have this functionality
- Change your local network and remote access ports from the default 8000, 8080, 8001 etc to something randomized
IF your Terramaster NAS is COMPLETELY isolated from the internet (and you are 100% certain of this, eg you directly PC-to-NAS interface your system OR you run the NAS on an isolated vLAN in your network behind a bunch of layers), then you can largely ignore the above.
UPDATED 02/03 08:00 GMT
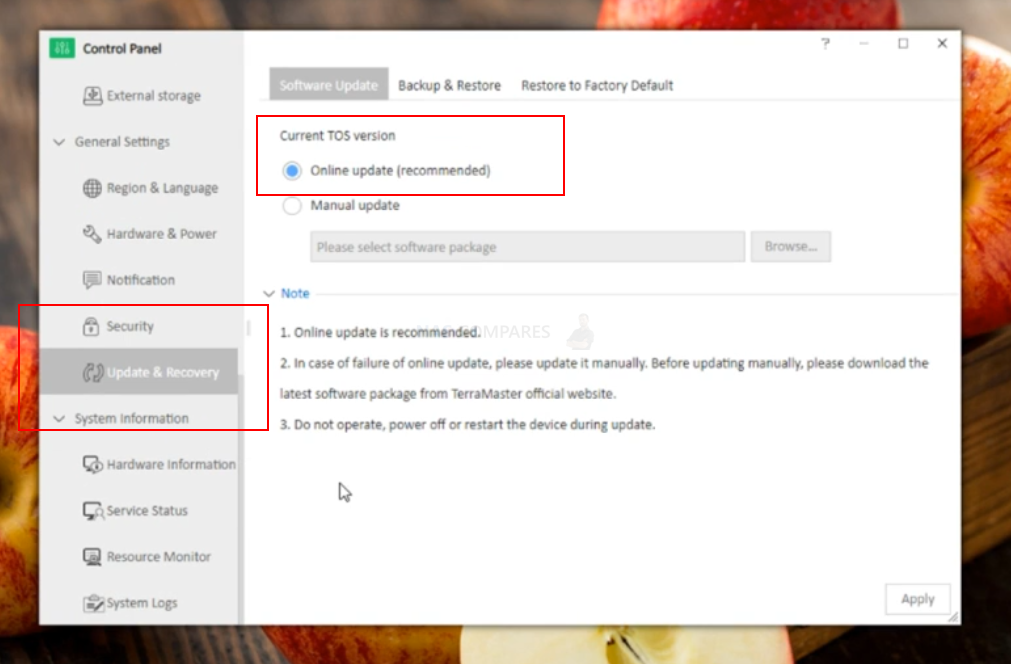
Since the deadbolt ransomware’s first targetted attacks yesterday, Terramaster has rolled out a new firmware update (TOS version 4.2.30) and they strongly recommend users who have not yet been affected to upgrade now. The update will be available from the usual system settings, software update menu from within the TOS web browser GUI in the window below:
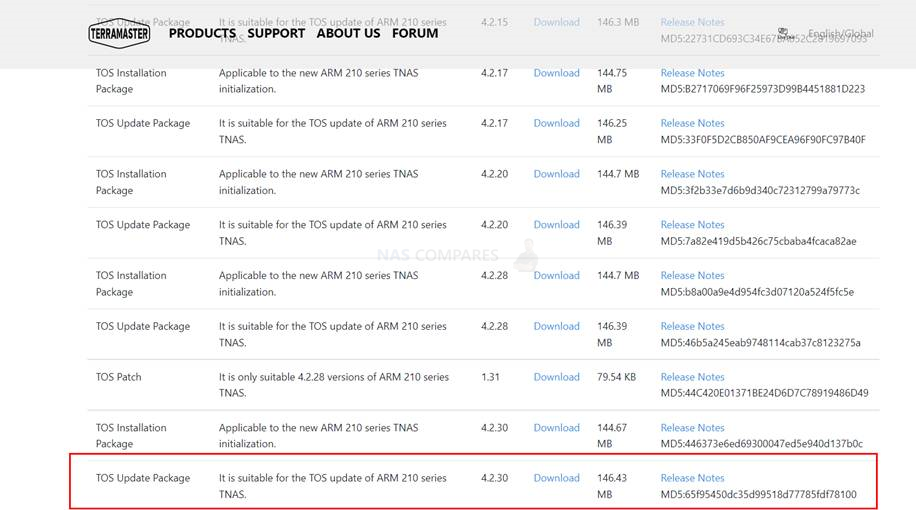
Also, you can choose to manually download the TOS 4.2.30 update directly on TerraMaster official website->SUPPORT->DOWNLOAD page (see image below) here – https://support.terra-master.com/download/
It is VERY IMPORTANT that users understand the following details before they update their Terramaster NAS to this latest firmware updated version:
- If you install this update, it WILL NOT recover/unencrypt files that have been hit by deadbolt (i.e. files that now carry the ‘.deadbolt’ encryption in their name/format. This update closes the vulnerability that allowed the deadbolt group to inject a command towards your terramaster NAS and carry out the attack.
- If you install this update, it will remove the black deadbolt entry screen to your Terramaster NAS when accessing it via the web browser. However, in doing this, you will also lose the (arguably crap) option to recover your files by paying the ransom group, getting an encryption key and decrypting your data. Although unaffected users and those who have zero intention of engaging with the deadbolt group will be happy with this, some users who have lost mission-critical /irreplaceable data that might consider this option might want to think about this update a little further. When Deadbolt hit Asustor NAS devices last week, when Asustor issued a firmware update, they also added a small add on in the app center that allowed the end-user to still access this screen in an isolated fashion to still keep the option of getting an (arguably illegally) paid for solution to recovery.
- Right now, users are attempting to perform recovery with deadbolt files via linux mounted drive setups. It is a painfully slow and low success % operation (as in user base) but if your data is important to you and/or/if you want to resume access to your NAS whilst keeping the encrypted data to one side, I recommend removing the HDD/SSD media (keep track of which drive in which bay) and replace the drives in the Terramaster NAS and re-initialize. Then you can reintroduce those drives to the NAS or to a linux machine in the event of a recovery method becoming possible.
Back to the Original Article.
What Do We Know About the Terramaster NAS Deadbolt Ransomware Attack?
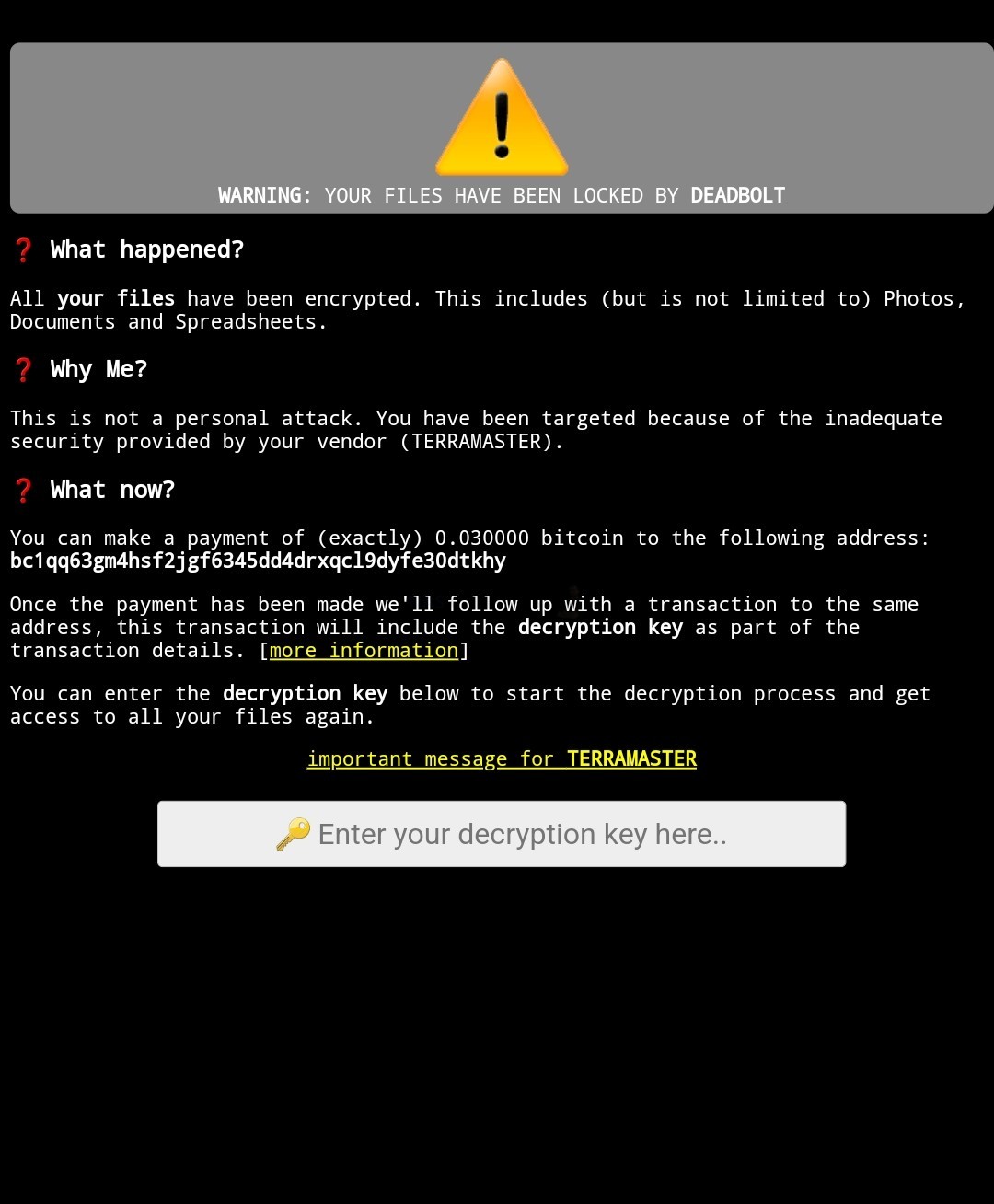
The bulk of the details even at this early stage of the terramaster NAS deadbolt ransomware attack bear alot of similarities to those of the Asustor attack last week (Read the article on that plus all the updates and MOST IMPORTANTLY the comments of that article as there is alot of information on how people have responded/adapted to when this hit them). Most users understood that their Terramaster NAS system was in the process of being hit by deadbolt Ransomware in two very clear ways, one arguably worse than the other. The first was that many of the more value series Terramster NAS systems (2/4 Bay systems at the Dual-Core level) had a sharp and very noticeable rise in system fan activity (and HDD LED lights kicking off incessantly) as the encryption command pushed the system very hard indeed. If you were fortunate enough to spot this early, then there is a reasonable chance that the % of files encrypted would be very low. However, a larger proportion of users found their NAS system was mostly/completely encrypted overnight (or whilst they were out of sight/earshot of the NAS) and their first knowledge of the attack was to be greeted by this (now depressingly familiar in 2022) deadbolt login screen:
Important Message for TERRAMASTER
All your affected customers have been targeted using a zero-day vulnerability in your product. We offer you two options to mitigate this (and future) damage:1) Make a bitcoin payment of 5 BTC to bc1qhkeecsgmzf2965fg57ll3enqyj7y094lxl5nzm:
You will receive all details about this zero-day vulnerability so it can be patched. A detailed report will be sent to support@terra-master.com.
2) Make a bitcoin payment of 15 BTC to bc1qhkeecsgmzf2965fg57ll3enqyj7y094lxl5nzm:
You will receive a universal decryption master key (and instructions) that can be used to unlock all your clients their files. Additionally, we will also send you all details about the zero-day vulnerability to support@terra-master.com.
Upon receipt of payment for either option, all information will be sent to you in a timely fashion.
There is no way to contact us.
These are our only offers.
Thanks for your consideration.Greetings,
DEADBOLT team.
If you are unsure if you have been hit by the deadbolt ransomware attack (i.e. you can still login fine and the login screen has not changed) but want to do a quick checklist on things to monitor. Here is a brief to-do list:
- Your Remote mounted storage is suffering delayed responses/file opening (eg mapped drives, SMB mounts, etc) as this could mean that these are in use by the system and being encrypted. The same goes if you have a recently accessible remote mount that is now inaccessible
- Search for .deadbolt in the file manager search bar. It is not the quickest, but any file hit by this will have the .deadbolt file extension
- Your regular overnight backup(s) failed or took way, WAY too long, as this indicates a large amount of HDD activity taking place at the same time as your regular backups and even 3-4 hard drives in a RAID 5 will struggle to maintain even marginally good input/output actions when these larger volume activities are run simultaneously
- Your system fans are increasing as drive activity has increased notably (encryption is a hefty task for any system to conduct, especially on the entire storage pool/volumes/etc
- Your HDD/SSD LEDs are going NUTS! This also applies if you are using larger than 8TB drives or larger Seagate Ironwolfs NAS drives, Ultrastar, Red Pros, EXOs, etc as these Pro/Ent class drives make some real noise in heavy crunch activity such as large scale encryption
Currently (01/03/22 930AM GMT) Terramaster has yet to issue a formal statement on this or a firmware update, but the attack is around 12 hours old at most. Still, this is now the 3rd Deadbolt attack to hit NAS brands in the last 6 months (Asustor and QNAP previously) and alongside the earlier attack of a vulnerability in TOS at the start of the year. There are hopes that the current TOS 5.0 update (still in Beta) will feature improvements in it’s network security and how much access installed apps have to the core system administration.
What Does Terramaster Advise to Prevent the Deadbolt Ransomware?
Terramaster has responded to this recent Deadbolt ransomware attack of their NAS systems with the following statement:
Recently, we have received reports of some TNAS devices being attacked by Deadbolt Ransomware. Based on the case analysis, we initially concluded that this was an external attack against TNAS devices. To protect your data from Deadbolt, please take action now!
If your NAS works normally, we suggest you take the following countermeasures:
1. Upgrade your TOS to the latest version;
2. Install good anti-virus software on your computer, TNAS device and router to help you detect and resist malicious threats;
3. Disable port forwarding on your router. After disabling this function, you will not be able to access TNAS through the TNAS device bound to the DDNS external network.
4. Disable the UPnP function on your TNAS. After disabling, your PC, multimedia box, TV and other devices may not be able to access TNAS through UPnP protocol, please use DLNA, NFS, SMB protocol to access TNAS instead.
For more detailed measures, please refer to the following link:
https://www.terra-master.com/global/press/index/view/id/1143/
If you find that your NAS has unfortunately been affected by Deadbolt Ransomware, please follow the steps as below:
-
Remove the LAN network cable from your TNAS device immediately.
-
Power off your TNAS; x.86 models: short press the power button; ARM models: long-press the power button 3 seconds.
-
Do not initialize your NAS as this will erase your data.
-
Please contact the online support on our official website or email to support@terra-master.com directly.
Additionally, there is a great deal of activity in the last 12 hours on the official support forums on this, with a Terramaster Customer Representative issuing the following response to an initial enquiry on deadbolt ransomware attacks:
Right now, Asustor has yet to issue further information on recovery on this (unless I have updated this article above with further information), but I would recommend following the steps provided by other NAS brands in the wake of a ransomware attack such as this:
- Change your password.
- Use a strong password.
- Change default HTTP and HTTPS ports. Default ports are 8000 and 8001 respectively.
- Change web server ports. Default ports are 80 and 443.
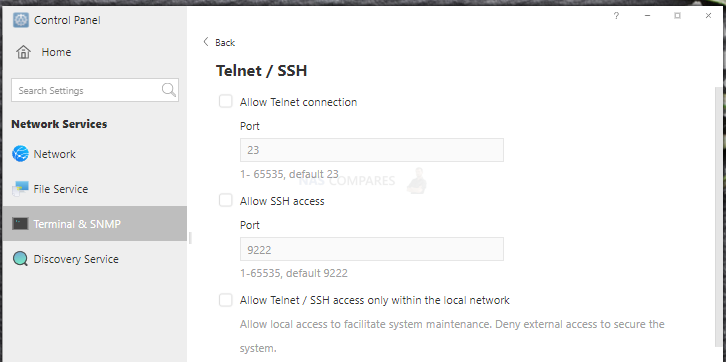
- Turn off Terminal/SSH and SFTP services and other services you do not use.
- Make regular backups and ensure backups are up to date.
Until the attack vector is established, I would recommend going ‘all in’ on updating your security settings. Although a lot of the changes relating to password changes seem unrelated to this, without having a complete throughline on similarities between users, it is best to dot every i and cross every t!
Is There A Solution, Restoration or Recovery Method Currently Available to Deadbolt Affected Terramaster NAS?
As it stands, there is no resolution available from Terramaster NAS if your files have been encrypted by Deadbolt ransomware. other than paying the ransom (which would suck!) many are looking at methods of recovery using linux based mounting of the drives and accessing any snapshots in a BTRFS volume (or using PhotoRec/TeskDisk in the hope of reverting the files), but even then, there is little currently possible to recover affected files. That may not always be the case and I would still recommend keeping the encrypted files (in a 2nd location if you need to format your terramaster for continued use) as recovery methods might become available in weeks/months from now. Terramaster issued an updated press release on this with further instructions on disabling specific services, We suggest you take the following countermeasures:
1. Upgrade your TOS to the latest version;
2. Install good anti-virus software on your computer, TNAS device and router to help you detect and resist malicious threats;
3. Disable port forwarding on your router. After disabling this function, you will not be able to access TNAS through the TNAS device bound to the DDNS external network.
4. Disable the UPnP function on your TNAS. After disabling, your PC, multimedia box, TV and other devices may not be able to access TNAS through UPnP protocol, please use DLNA, NFS, SMB protocol to access TNAS instead.
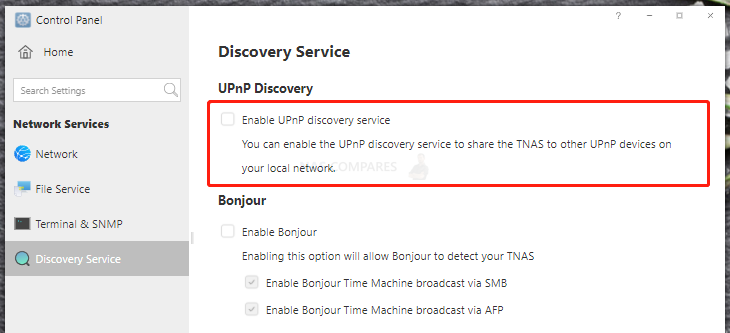
5. Disable RDP, SSH and Telnet when not in use;
Additional Changes Here:
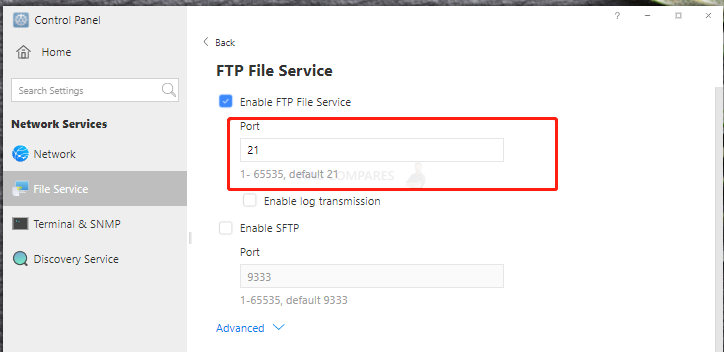
6. Change the default port of FTP. When you use the FTP protocol to access, please pay attention to bringing the port, such as ftp://192.168.0.1:1990.
7. Set a high security level password for all users;
8. Disable the system default admin account, re-create a new admin account, and set an advanced password;
Note: For versions after TOS 4.2.09, you can set the administrator account without using the default admin username when installing the system. If it was upgraded from a version before TOS 4.2.09, you need to reset the system configuration, then you can customize the user name.
9. Enable firewall and only allow trusted IP addresses and ports to access your device;
a. Go to Control Panel > General Settings > Security > Firewall.
b. Create a firewall rule and choose the operation of allow or deny.
c. Fill in the IP range you allow or deny access to. If you fill in the network you want to deny access to, please fill in the subnet address correctly, otherwise it may cause your existing devices to be unable to access TNAS.
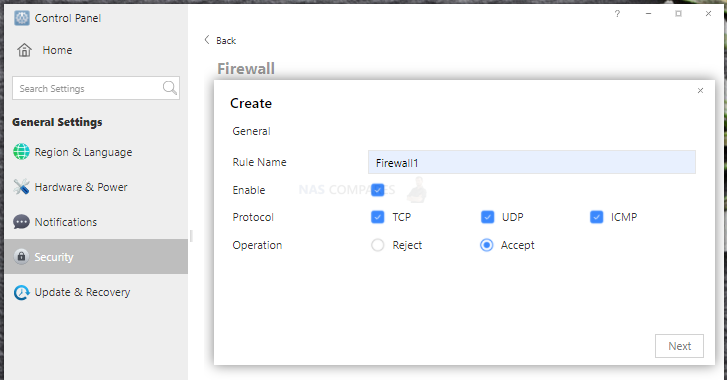
10. Avoid using default port numbers 5443 for https and 8181 for http. After changing, please enter IP:Port in the browser address bar, such as 192.168.0.1:8186.
11. Enable automatic IP block in TOS Control Panel to block IP addresses with too many failed login attempts;
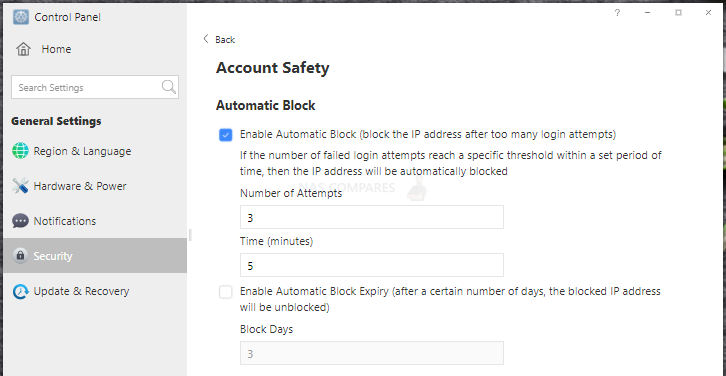
12. Backing up data is the best way to deal with malicious attacks; always back up data, at least one backup to another device. It is strongly recommended to adopt a 3-2-1 backup strategy.
If your Terramaster NAS was NOT affected, I would still recommend disabling remote/internet access., as the act vectors are not clear and there are reports from some users right now that state that they had the latest firmware, they were still hit. Therefore right now there is so much unconfirmed info here to allow remote access (in my opinion) and until further info is made available, I strongly recommend disconnecting your Terramaster NAS from the internet (wire AND via the software settings) and getting your backups in order. I will update this article soon as more information becomes available.
| Where to Buy a Product | |||
|
|
    
|

|
VISIT RETAILER ➤ |
 |
    
|

|
VISIT RETAILER ➤ |
We use affiliate links on the blog allowing NAScompares information and advice service to be free of charge to you. Anything you purchase on the day you click on our links will generate a small commission which is used to run the website. Here is a link for Amazon and B&H. You can also get me a ☕ Ko-fi or old school Paypal. Thanks! To find out more about how to support this advice service check HERE
Gl.iNet vs UniFi Travel Routers - Which Should You Buy?
UnifyDrive UP6 Mobile NAS Review
UniFi Travel Router Tests - Aeroplane Sharing, WiFi Portals, Power Draw, Heat and More
UGREEN iDX6011 Pro NAS Review
Beelink ME PRO NAS Review
UGREEN iDX6011 Pro - TESTING THE AI (What Can it ACTUALLY Do?)
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.





Love how terramaster says go to TOS > Control Panel > General settings > Software update MY NAS IS DEADBOLT LOCKED no way to update it
REPLY ON YOUTUBE
Hello, can TOS 5.0 display videos directly to TV/monitor via hdmi now for f4-421 model? Thanks.
REPLY ON YOUTUBE
My Terramaster F2-220 got hit today – but the encrypted files all have an extension of .iFire – is this a variant of the deadbolt attack?
What can you do if you have been hit?
-you can pay Ransome and hope decryption will work (or use Emisoft)
-you can use PhotoRec or another app that restores freshly deletes files (https://nascompares.com/answer/how-to-recover-data-on-raid-with-photorec-qnap-and-maybe-asustor/)
-you can wait few years until someone creates a key or when computers become fast enough to decrypt AES-128
Maybe someone will find this useful to regain the access to TOS {Asustor Solution}
Regaining Access to the ADM Portal
If you are planning to continue using the existing drives you may regain access to the portal by running these commands below.
First open the Crontab tool to edit what files are being executed on the system.
crontab -e
You will notice a new line entry called cgi_install. Remove the line as found in this image
*/1 * * * * /bin/sh /usr/builtin/etc/cgi_install
https://forum.asustor.com/download/file.php?id=1544
Once that is done commit the changes. Then, remove the offending cgi_install file
rm /usr/builtin/etc/cgi_install
After that is done, navigate to the following to replace the bad cgi index file.
cd /usr/webman/portal
chattr -i index.cgi
rm index.cgi
cp index.cgi.bak index.cgi
This will restore the portal to it’s original state. Once inside the portal, turn off EZ-Connect to prevent future access to the NAS. Remember to block all remote access to the NAS from your firewall if possible.
Resources:
https://thearchitect.wordpress.com/2022/02/21/deadbolt-on-asustor-nas/
https://forum.asustor.com/viewtopic.php?f=45&t=12630
Is there a way for you to check if this allows you to display the new OS through the built in HDMI port that is available on some units like the F4-421? I have watched your earlier videos and I remember you saying that they were hinting at adding that ability sometime down the road. Thanks for the videos, I appreciate them!
REPLY ON YOUTUBE
What do you think of AMBER X Smart Personal Cloud Storage.?
REPLY ON YOUTUBE
Much better that the Qnap OS that is for sure and if Synology don’t pay attention a continues to lunch proprietary crap many this one will start taking some share, well done Terramaster.
REPLY ON YOUTUBE
TOS (same as “TermsOfService”), what a weird name for a OS. I hope you won’t break that TOS by watching movies with your NAS lol
REPLY ON YOUTUBE
Important News for Terramaster NAS users, There are reports of TNAS devices being targetted by Ransomware, learn more here – https://nascompares.com/2022/01/18/terramaster-nas-drives-being-attacked-by-ransomware/
REPLY ON YOUTUBE