QNAP NAS Security Check List – 23 Vital Steps to Secure Your NAS
It must be frustrating to hear about all ransomware and other kinds of attacks on QNAP. Especially if you plan to buy one or own a NAS already. In simple terms, you need to treat your NAS just like your computer. You would not risk going online without an antivirus installed on your Windows PC. Nowadays, Microsoft has built-in antivirus, but systems like NAS do not follow the same route. This is something you need to do manually just like in the olden days. And there are a lot more risks to consider when exposing your server to the internet. At best few brands like Synology will have built-in security advisor software. This will scan the system and notify you about all weak areas in your setup. But even that is not perfect. In this article, I will try to write from a hacker’s perspective. How would they think and what strategies they will use to attack your home network and your NAS.
Bonus – How to secure your Network?
What are the ways your system can be attacked?
There are dozen of different kinds of methods to attack. But there are only a few that actually can affect a big number of NAS users. The rest of the attacks are very targeted at a single victim. Something for unique personal benefit. So the most popular attacks will be explained later in this article.
How does a hacker know I have a NAS?
They won’t until you tell them you have one. Hackers tell robots to scan every single IP in the world on daily bases. This is a single ping (something like saying Hello to a person). By default, devices are configured to reply with hello if they hear the ping. This is where hackers will initiate an open port scan which we will talk about in the next chapter.
Why do I have open ports?
Ports are like doors to different departments in your office. Something like IT office (NAS control panel), The Office Canteen (NAS multimedia apps), HR (NAS email and databases), the dispatch office (file transfer protocols) and so on. Random people pressing buttons on the control panel could cause the company to collapse. In order to keep people out, we use keycards (NAS user authentication).
Some of the door names (ports) are very specific to a certain NAS. This is how hackers can guess what kind of NAS you own.
A simple scan from online https://pentest-tools.com (check your IP) would check the most common ports and tell you if they are open.
A remote scan from a MAC terminal using the command nmap would show not just a few, but all single ports open.
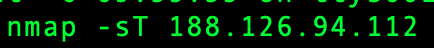
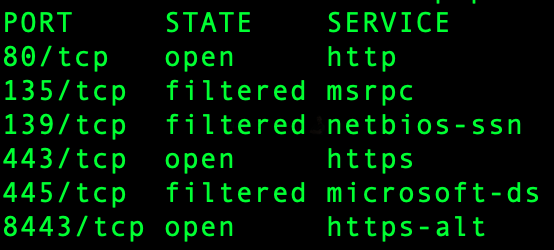
Why open ports are potentially dangerous?
With additional commands like ‘vuln’, and ‘exploit’ hackers will check for software vulnerabilities. All services need regular updates. If not updated specific scripts will detect an outdated service and will allow hackers to abuse it. Similar to having an office key 🔑 that is 100 years old. Even kids could break in.
So your first defence here is your router. If you have not opened any ports since you received your modem/router from your broadband company you should be safe.
But it is worth checking those ports. When you log into your NAS as an admin you can tell your router to open ports. This will be called Port Forwarding. Be careful what you click. There is nothing wrong with open ports if you have security set up. I will talk about security configuration later on.
Here is a list of QNAP default ports link And here is Synology.
Brute force
Now when hackers know you have a NAS with certain ports open, they can start the most basic attack which is guessing your password.
They will try the most common usernames and passwords (such as Admin Password).
Where do hackers find my passwords?
First of all, they will use robots to try every single word inside the dictionary.
There are lists of stolen user names and passwords available on the black market for hackers to buy. You can check if any of your passwords are being sold here https://haveibeenpwned.com or here https://www.avast.com/hackcheck/

When someone is asked to replace or improve the password people so often simply capitalise the first letter, then add the number 1 and ! mark at the end of the password. Of course, hackers will try all stolen passwords with this modified version of it.
![]()
Phishing Attack
This is more popular among targeted attacks where people gain access to your personal data which is priceless. Since this attack is more profitable hackers can spend more time on every person individually. They would normally send you an email that looks very similar to QNAP official emails. They will say something like “your password is compromised, please change it here”. Then they will ask for old password and the new one. This is where they steal your password because you landed on hackers website that looks like QNAP. Always make sure URL is actually QNAP and not something like QNAPpp.com.
MAN in the middle
Another popular phishing method is in places with Public Wifi (coffee shops, trains etc ). Man in the middle can see all data you send and receive if you don’t use HTTPS in URL. Hackers can also direct you to the page that again looks similar to QNAP page where you put your password in. But actually, it’s hackers website. Never access your important stuff or log into anywhere from free wifi EVER!
Zero-Day Exploit
Every piece of software becomes vulnerable with time. Either it is an Operating system or individual apps. Zero-day exploit means that there is a way to break into a system because there is no patch created or the patch has been installed on a particular system. So this makes it a ticking time bomb. They don’t even need your username and password.
It depends on each company how they deal will vulnerabilities. Some companies run Security Bug Bounty Program and some don’t. When a hacker finds a new security hole in the system they have to make a choice. Either they sell this information to a NAS brand or they sell this information to the black market. Or sometimes people simply share vulnerability info for free here https://www.cvedetails.com/vulnerability-list/vendor_id-10080/QNAP.html .
It is up to each brand how quickly they make a patch for each hole. Until there then you either need to disable the service or add another layer of security that doesn’t allow hackers to take advantage of this security hole.
You can scan your network for vulnerabilities and exploits using NMAP command.
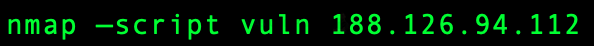
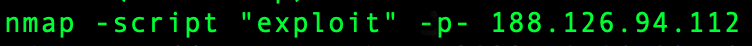
Or for the visual interface, you can use Zenmap.
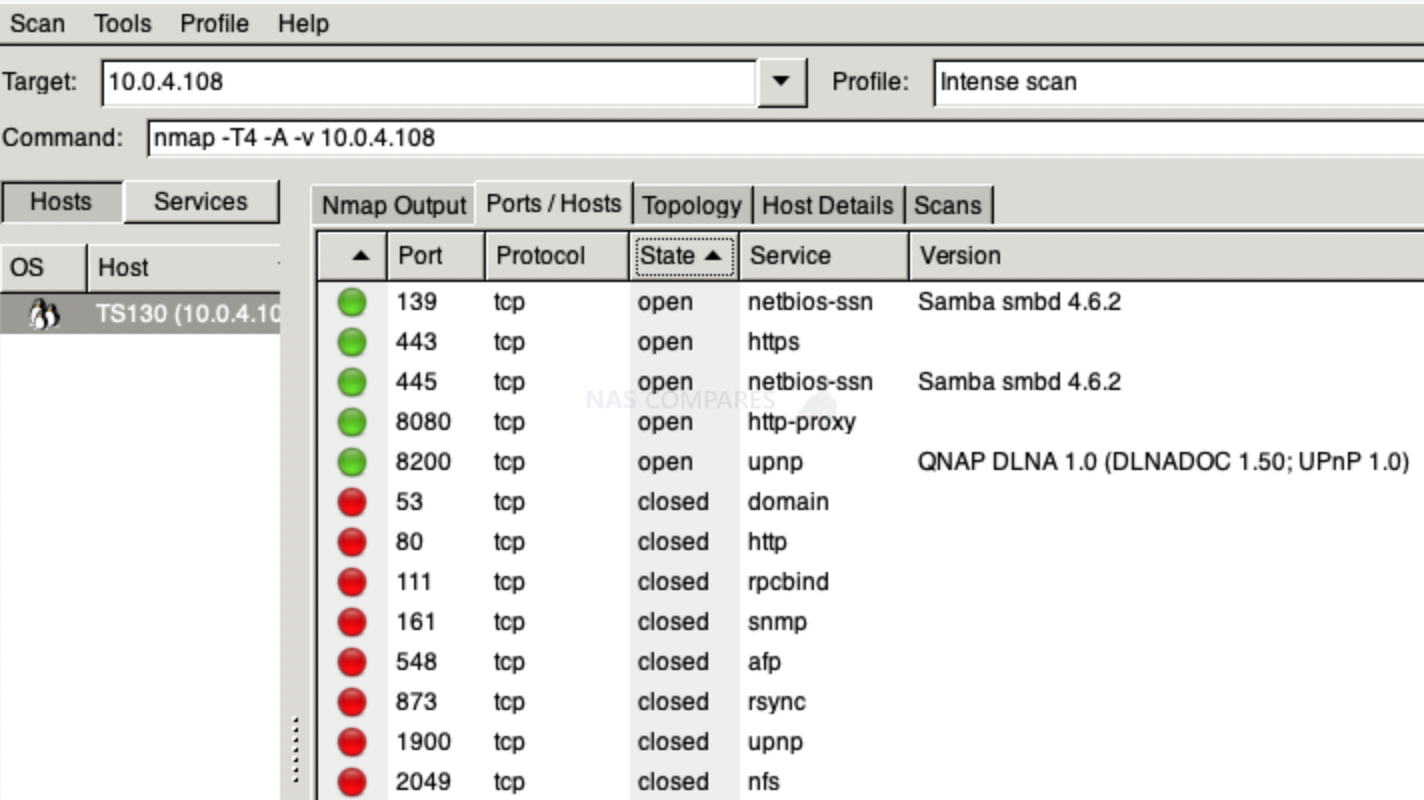
What about other attack types?
Malware Attacks
This will be vare rare occasion to get an actual virus. This usually happens with computers when you try to open a suspicious email attachment file. It could be zip or exe file or similar. On a NAS this could happen when manually installing OS or app. Instead of using AppStore or automated updates.
These viruses include worms, spyware, ransomware, adware, and trojans. This could be done via cheap smart plugs from China or elsewhere if you connect them in the same network (it’s good practice to connect them via guest wifi).
How To Choose The Right Settings to Secure Your NAS?
Now it’s time to go through the checklist and make sure your NAS is safe. You do not need to tick all of the boxes on the checklist. You start with the top and make your way down. The lower you get, the more secure your system gets.
| Security Level | Protects against | |
| BASIC
|
|
Brute Force Attack |
| MEDIUM
|
|
Phishing Attack MAN in the middle Zero-Day Exploit |
| HIGH
|
|
Targeted attack |
1. How to Check and/or Change Your Password
If you use the same password on multiple websites to log in, you risk that your password could be stolen from one of those websites and used to log in to any of your accounts on any other website.
It is humanly impossible to create a strong password that is unique to every account and Still Remember it. So use password generators and save those passwords. One day, when two-step authentication will be required on every system, then weak passwords will not be an issue anymore. And all passwords as you know them will seize to exist.
Protecting ADMIN account with a Very complicated password is the most important thing you have to do. Hackers will be able to access ANYTHING they want on your NAS. If they gained an access to a non-admin user the damage will be very limited.
You can use this random string generated every time you reload this page
Or with Google Chrome browser use an auto generator
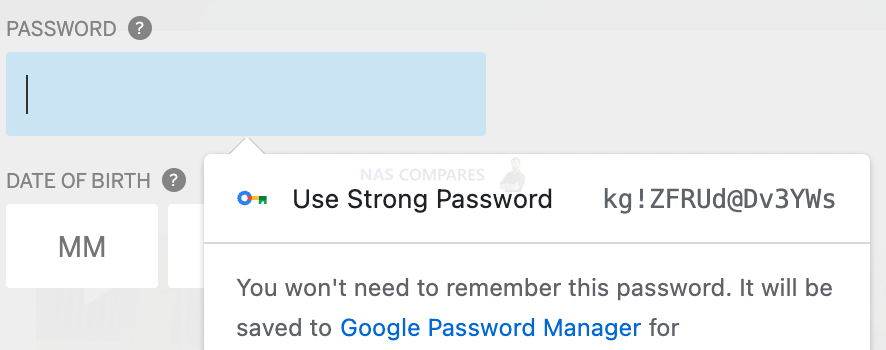
QNAP default Admin password is NIC MAC address, maybe you can use a similar method with a strong password printed on sticker

To change a password, log into your QNAP and click on your user name on the top bar. Then select Options.
Click on the tab ‘Password Settings’
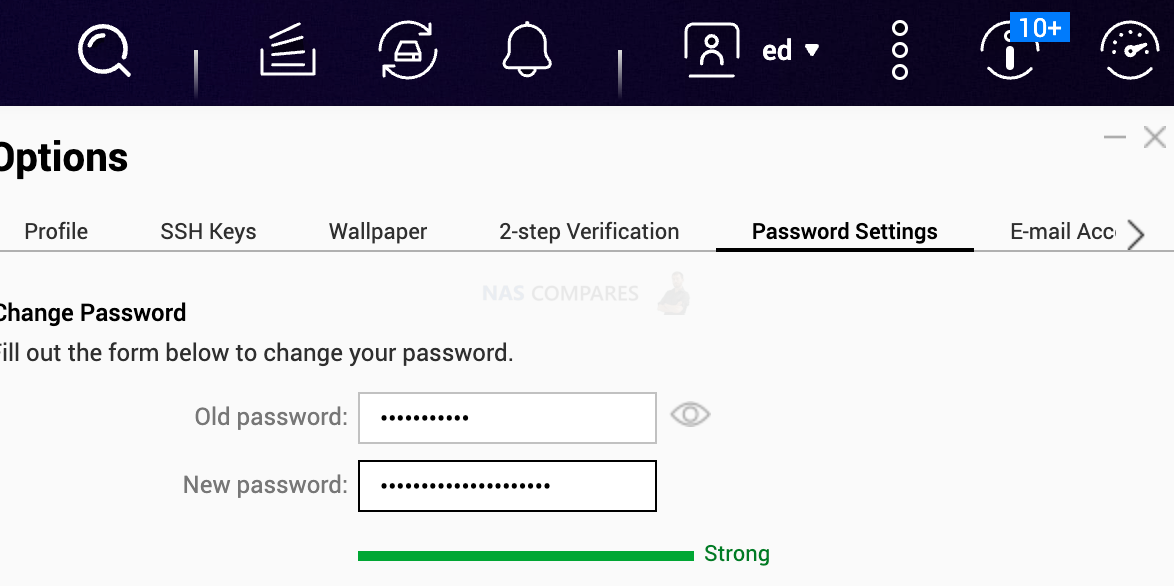
If you do not trust Google password wallet, you can store your passwords on an encrypted SSD like datashur. You will need to physically have this USB stick around and it can be accessed only with a pin code.
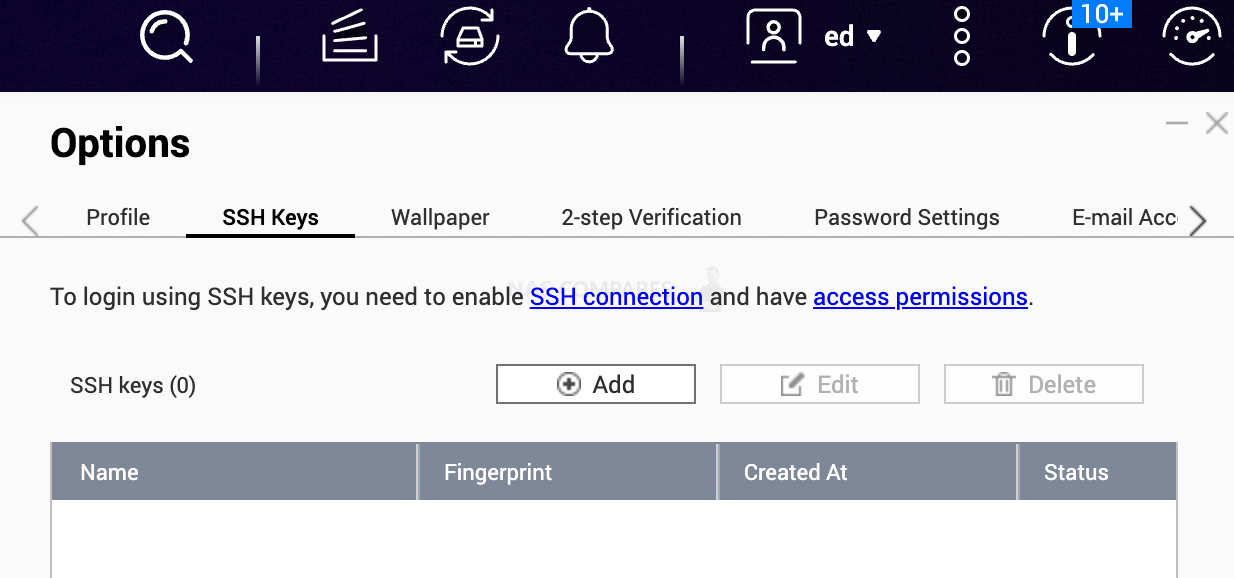
Something similar to a password is a SSH KEY. Instead of having an 8-character string, you can have an entire document filled with random characters. This is called ssh key. You can keep it on a fingerprint-based memory stick. Simple Lexar USB will do the trick.
You can enable SSH Key login option when you open User settings and click on SSH Keys tab.
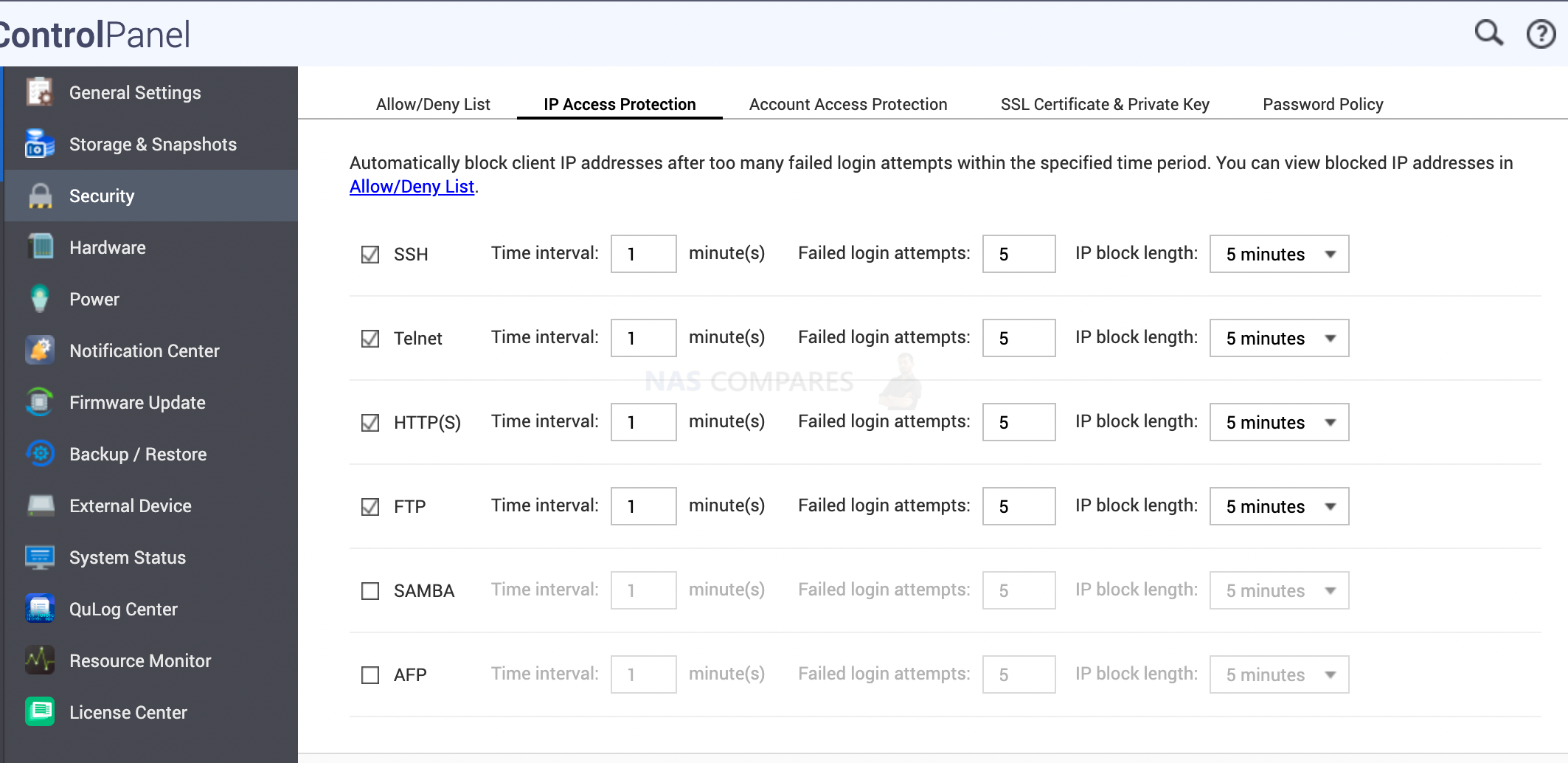
2. How to Enable IP/Account autoblock
Hackers will usually deploy robots to use all possible combinations and stolen password lists to hack your account. If you enable autoblock this will stop the robot after a certain number of attempts. You can block an IP or the user account. You will find respective tabs when you open Control panel/ Security. IP Access Protection is for IP based blocks and Account Access Protection is for locking the account for everyone not just that IP. Some advanced robots will be using various IP addresses from the zombie computers they have gained access to before.
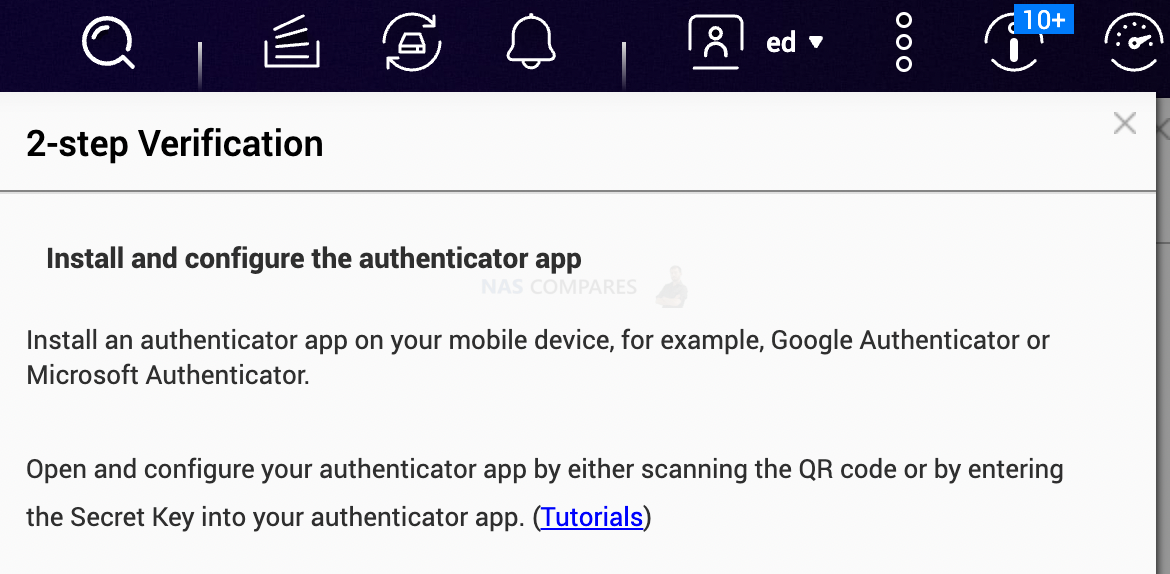
3. How to Enable two-step authentication
Two-step authentication means that you will use a code from another device that only you can have access to. This could be SMS code, email code or Authenticator App code. QNAP only allows Authenticator App that you can install on your Android or iPhone.
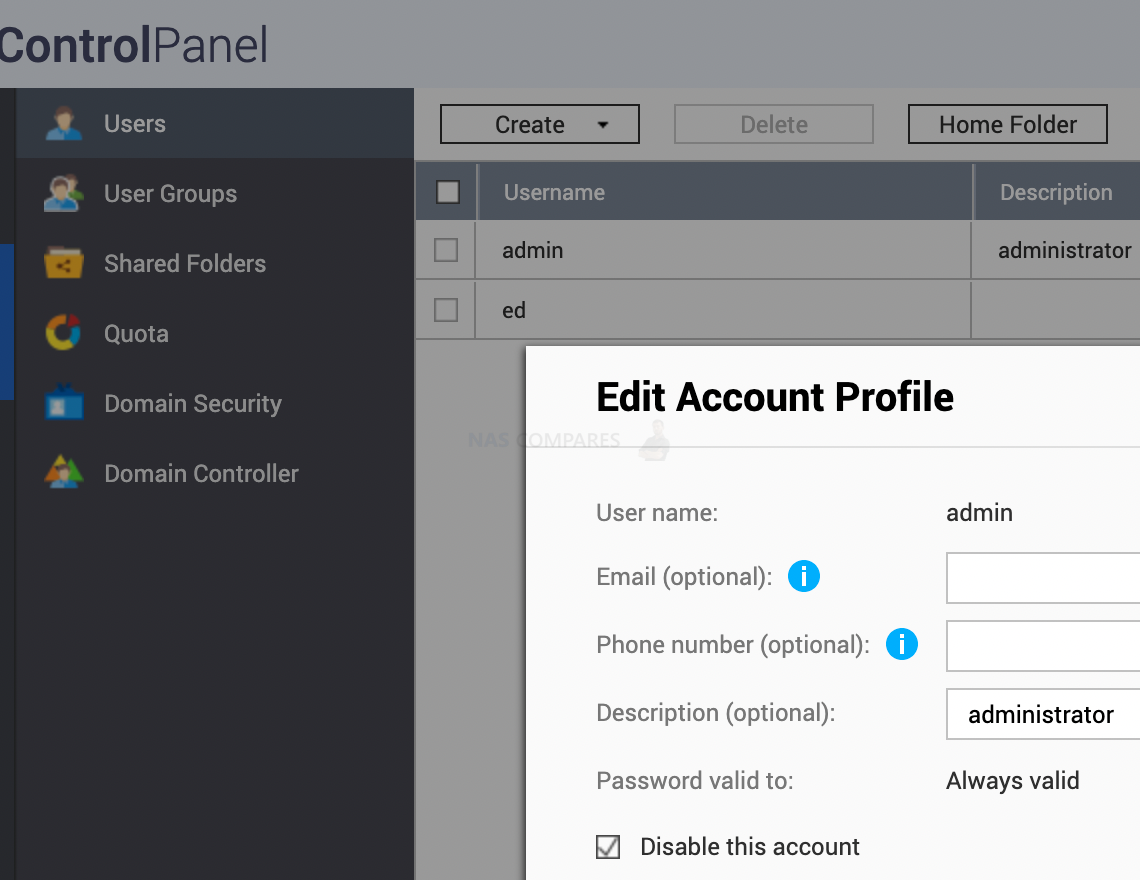
4. How to Disable Admin Account Access
Just like I mention above, ADMIN account has no limits on what it can do. You can create several Admin accounts. All hackers know that the default Admin account is named ‘Admin’, so all they need to do now is try all possible passwords. Simply disabling the main Admin account and creating another one with some unusual name would slow hackers down quite a lot. Slowing down does not mean stopping them. So make sure accessing this account is very difficult, even for you.
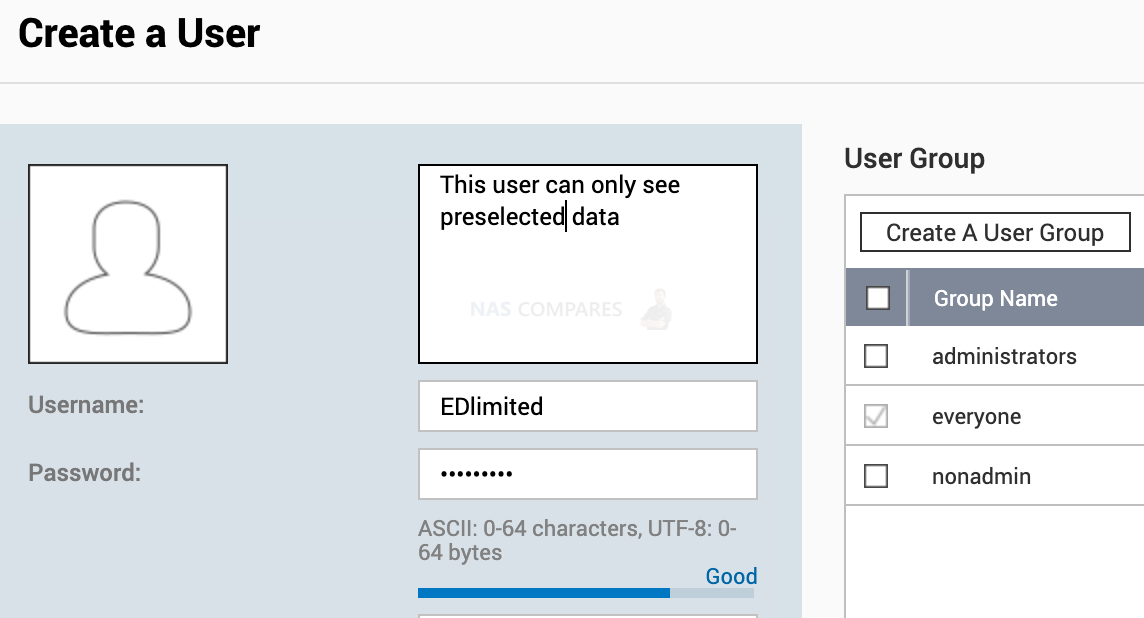
5. How to Create non-Admin users and tailor their Access
When accessing your NAS on daily bases you should use a non-Admin account that has limited functionality and access to the services and files.
6. Remove Apps you don’t use – How to Check and Change Them
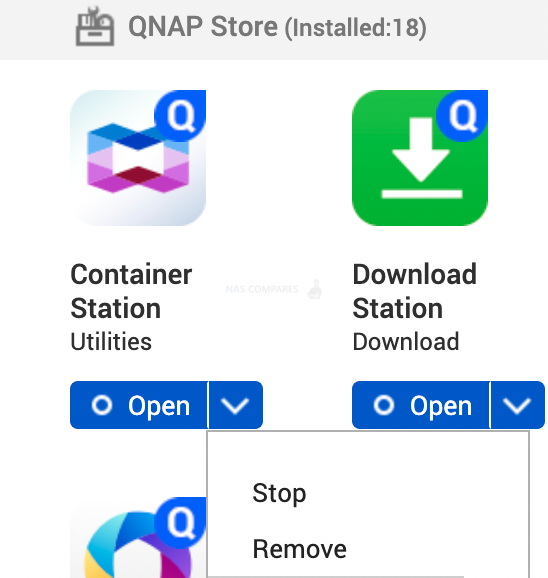
When people get a new NAS they usually are so excited and install every possible app to try it out. But no one removes them nor updates them. More apps you install, more potential attacks you can expect. Each app has its own volnurabilities that gets fixed via regular updates. If you never use half of your apps, why take the risk of potential security holes in any of those apps? Disable or remove apps you don’t use.
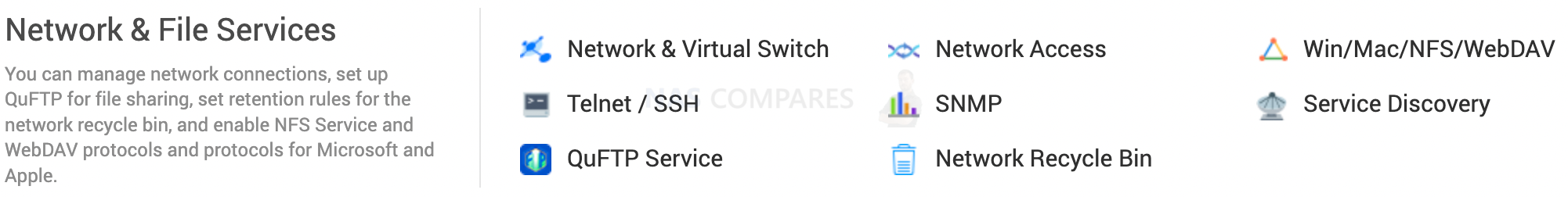
7. How to Disable Services that you don’t use
This could include SSH/Telnet that us used for command line access to your NAS. And UPnP / CloudiD firewall hole punching for remote access.
- Telnet
- SSH
- UPnP
- QNAP CloudiD
You can find all services in QNAP Settings page
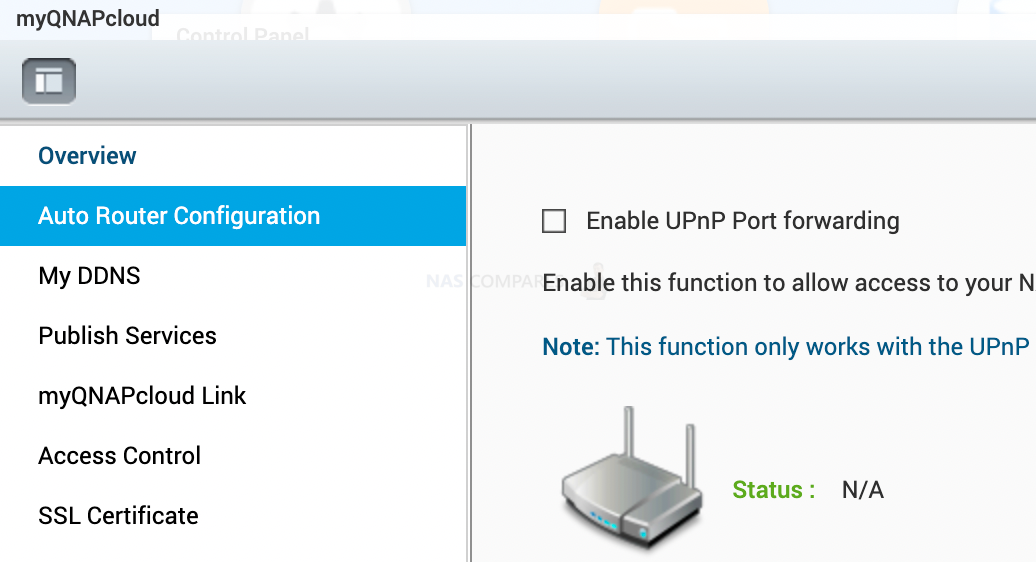
Go to app center/ myQNAPcloud to find UPnP and CloudiD settings
8. How to Close Unused Ports and/or Change ports
Disabling services you don’t use will also close relevant ports. If you do enable services such as SSH, make sure you set a different port. This will confuse and slow hackers down. By default, hackers will test if you have port 22 open before they decide to attack. If ports is changed to 2889, you are less likely to be attacked. The most important ports hackers will use are SSH/Telnet and Ports 80, 443, 8080 and 8443 (HTTP and HTTPS).
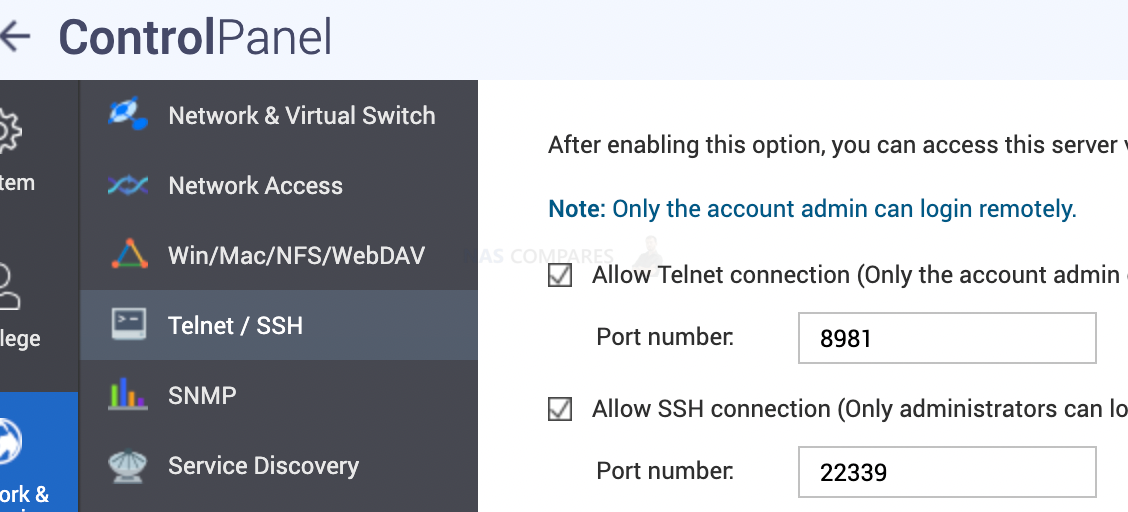
9. How to Enable auto-updates on your NAS
Every time there is a notification about new updates indicates that hackers have found a new hole in the software. Not always hackers can get into your system because of this software bug. But in certain circumstances, they can. The chances to attack increase dramatically when you have open ports on your router and have no firewall or any malicious traffic prevention tools enabled.
Sometimes NAS is configured in a specific way that an update might disable important features. It is OK not to update these NAS ASAP as long as the system is not exposed to the internet thanks to open ports.
You can enable automatic App updates when you open AppCenter/ Settings/ Update.
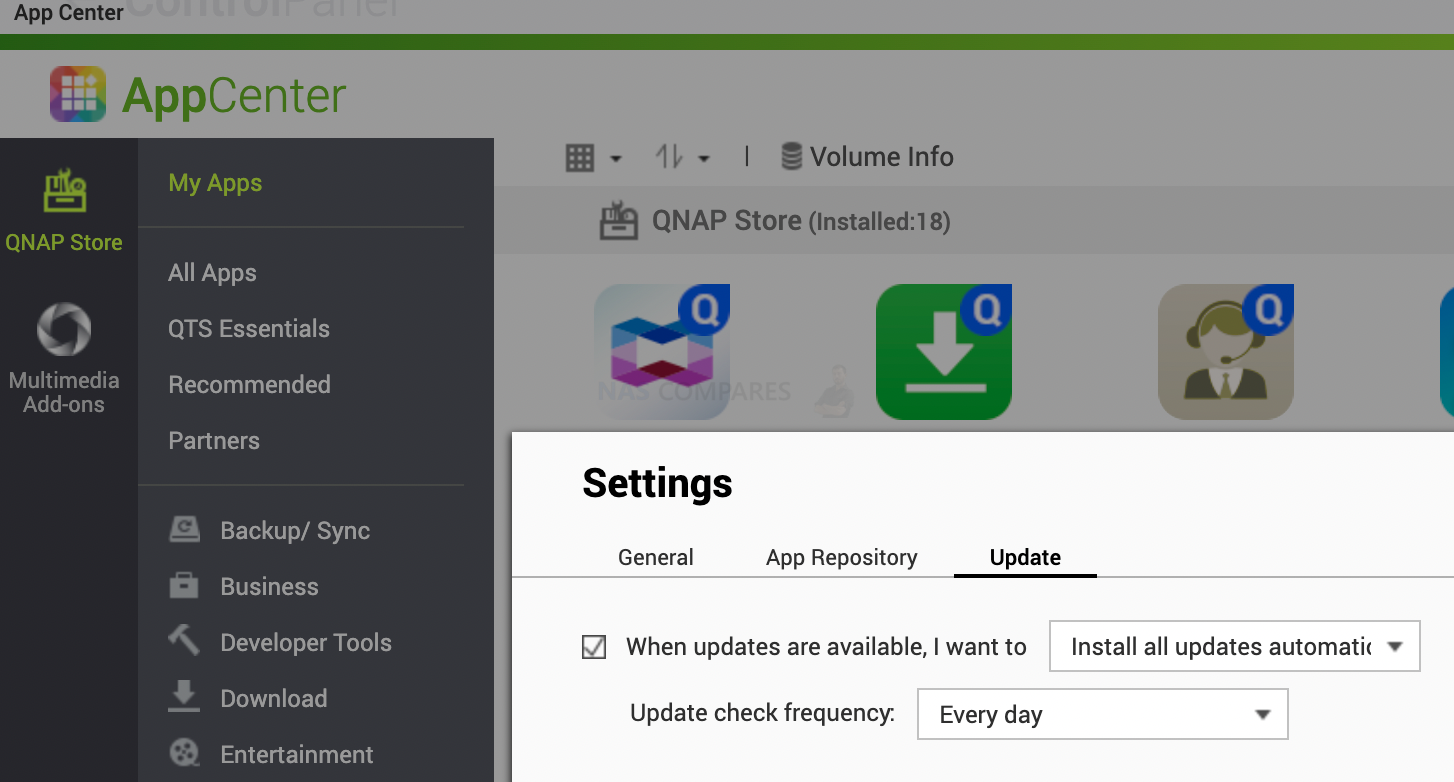
You can also enable automatic operating system updates when you open Control Panel/ Firmware Update/ Auto update
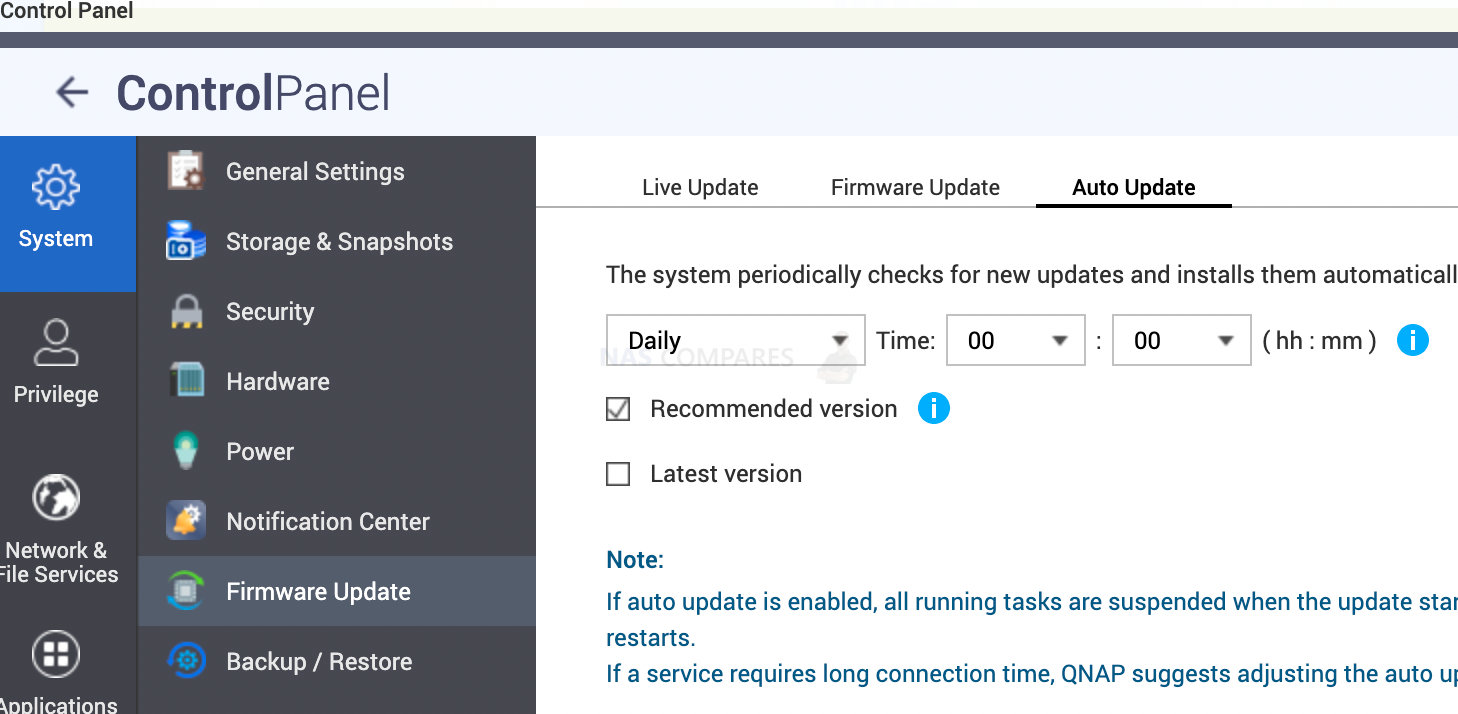
10. Make Sure You Install the Security Advisor and Councilor Application!!!
With so many apps and services, it is hard to know what is going on behind the scenes. Security Advisor will run system checks and will alert you if any apps have open ports or have changed configuration that is not safe. You can install it via AppCenter.
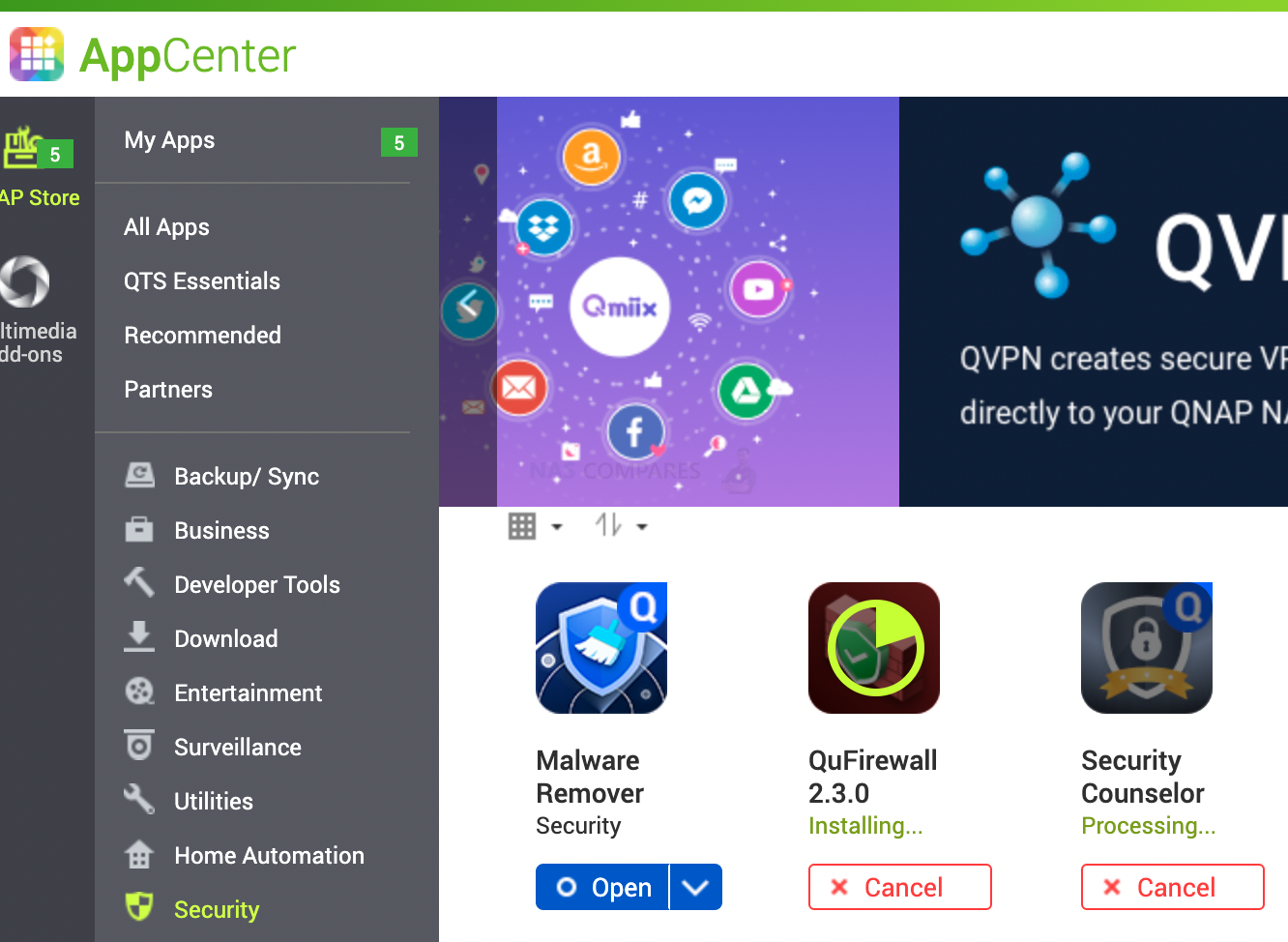
You can then choose the level of security you need. The basic level is often all you need for home use. Businesses might go for the Advanced level. Top-level will suggest disabling a lot of features that is not useful for home use.
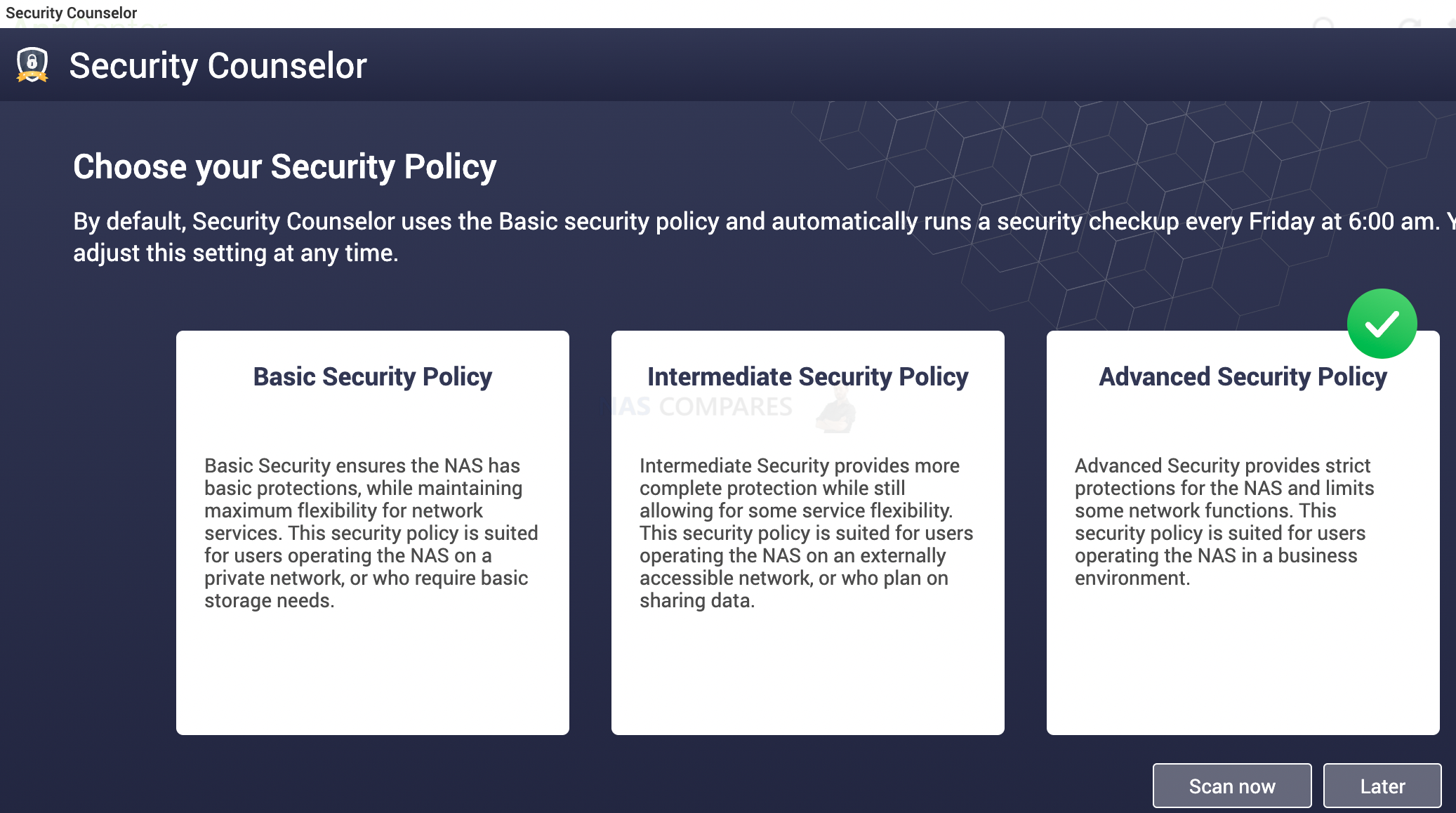
11. Install Antivirus and Set a Scheduled Scan on Day 1
Security counsellor app will allow you to enable 4 crucial parts of your NAS security.
- Security Checkup (will scan for configuration weaknesses)
- Antivirus (scan files for viruses)
- Malware Remover (Remove any malware found on the system)
- QuFirewall (limit the access your NAS based on IP, GEO and other rules)
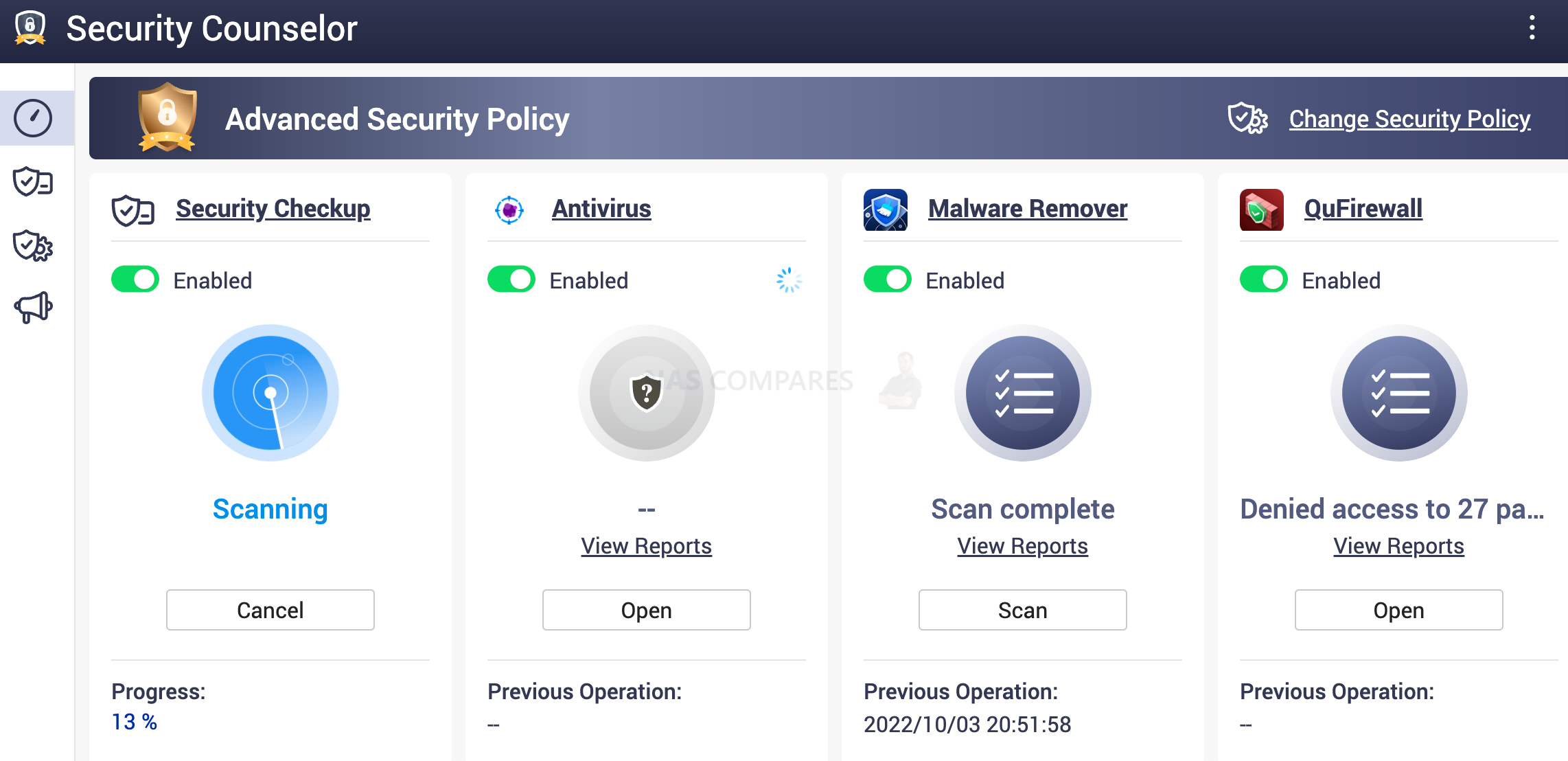
By enabling Antivirus, this actually do not do any scans. You need to manually set the scan schedule. Go to Control panel/ Antivirus/Scan Jobs to set it up.
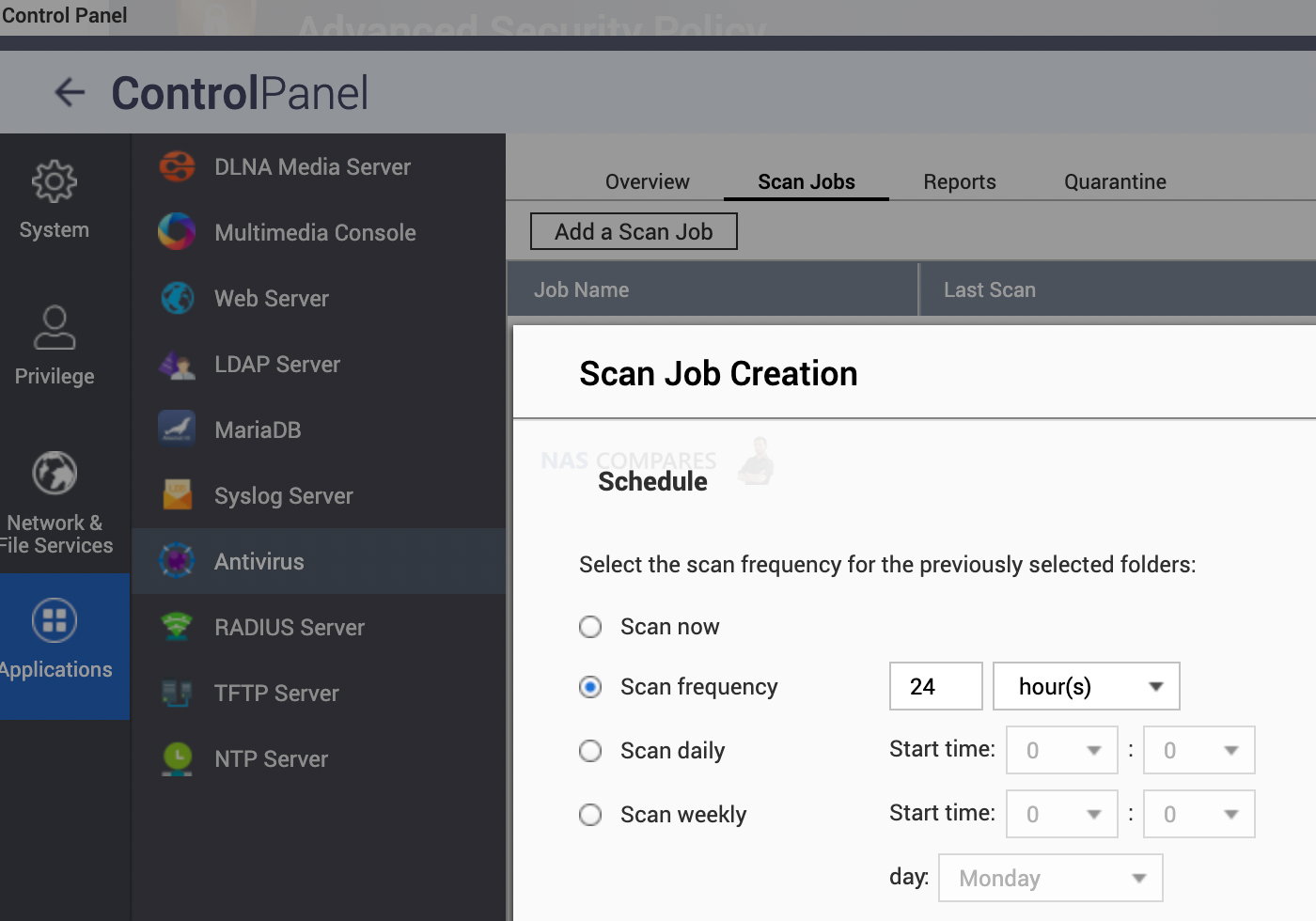
12. How to Enable Firewall protection on Your NAS on Day 1
Having a firewall will automatically block anyone if they do not pass tests like location or IP address. Similar to WD NAS, you can choose to have access to the admin panel ONLY when you are physically present inside your business network. Any access attempts to the control panel over the internet will be blocked. You need to open QuFirewall app and select one of these
- Basic protection (allow your country only to access)
- Subnets Only (allow only your local network to access)
- Restricted security (allow access to popular services only)
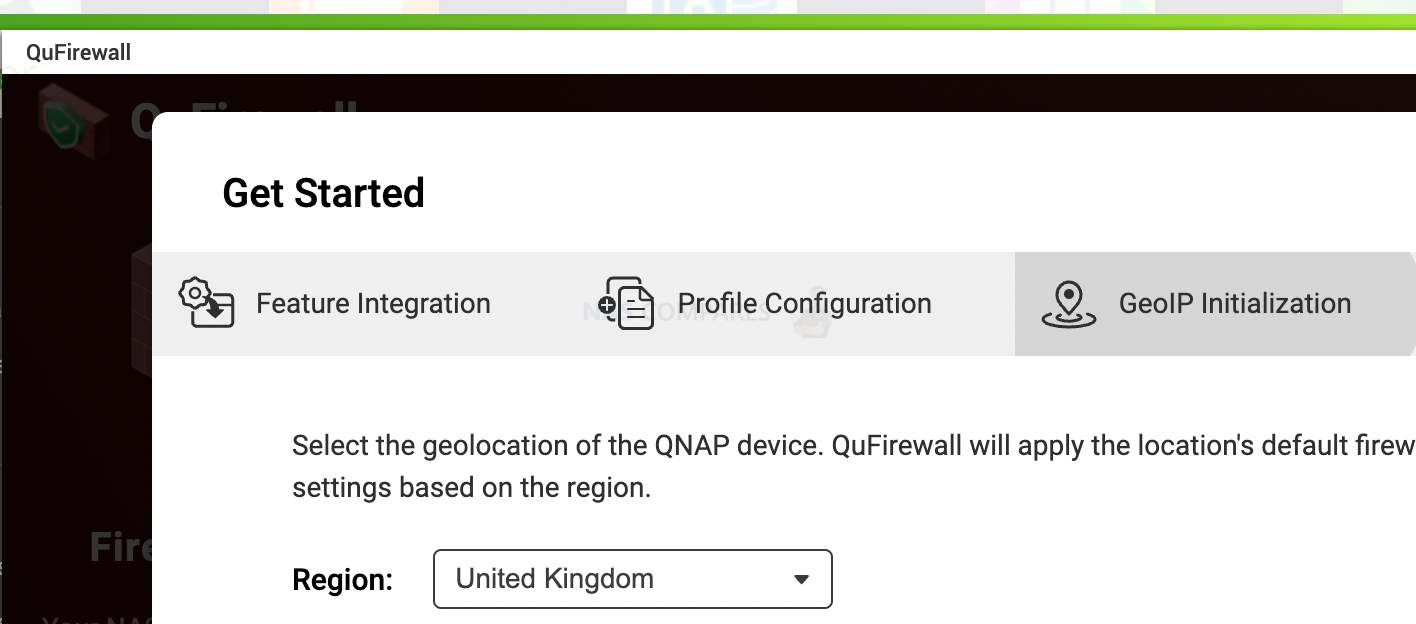
13. How to Set and/or Change User Access Rights
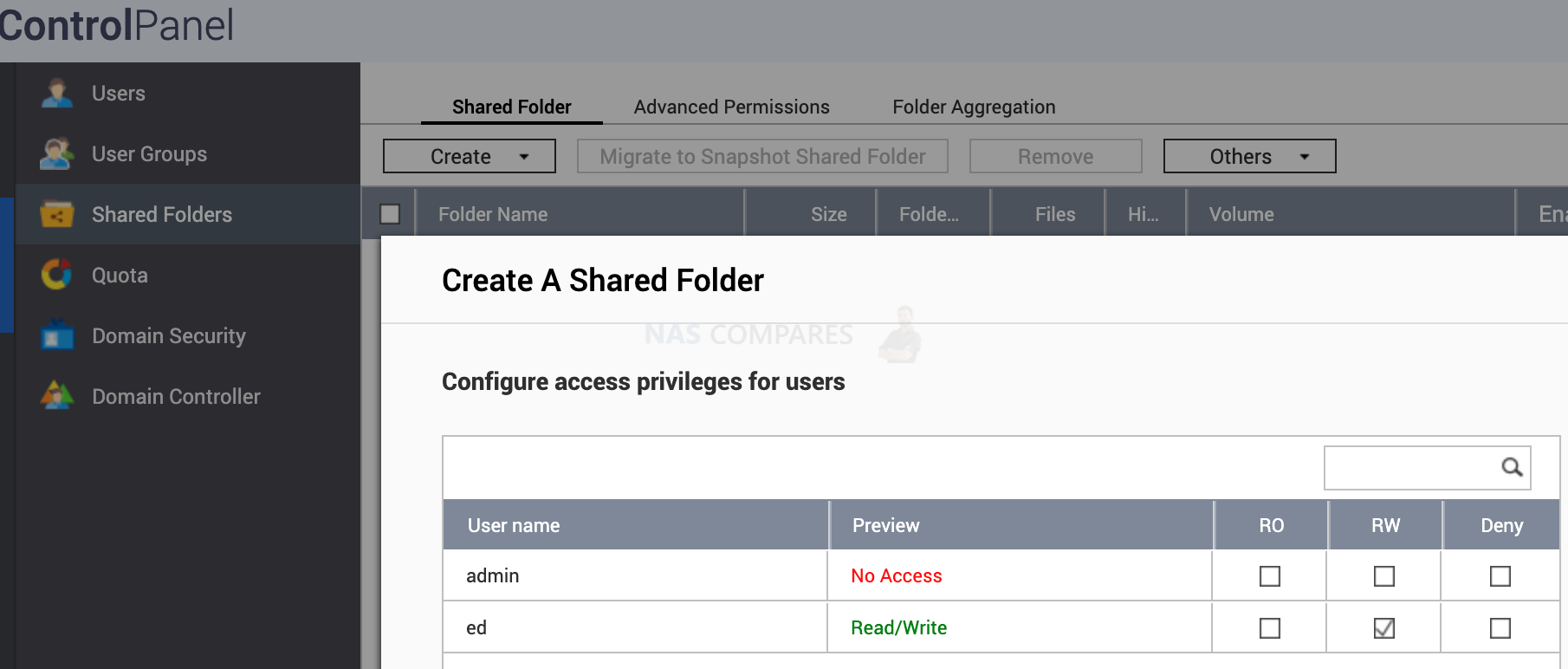
As suggested before, only use non-admin accounts for daily use. Admin account is only meant to be accessed for configuration changes. Make sure that users have no access to other user data. You can create separate shared folders that can be shared. If hackers will manage to gain access to this user account, they can only destroy this user’s data and not others. If the admin account is hacked then all users will lose the data.
You can create a separate shared folder with unique access rights under Control Panel/ Shared Folders. I would have separate shared folders and user names for Multimedia, surveillance and Backups.
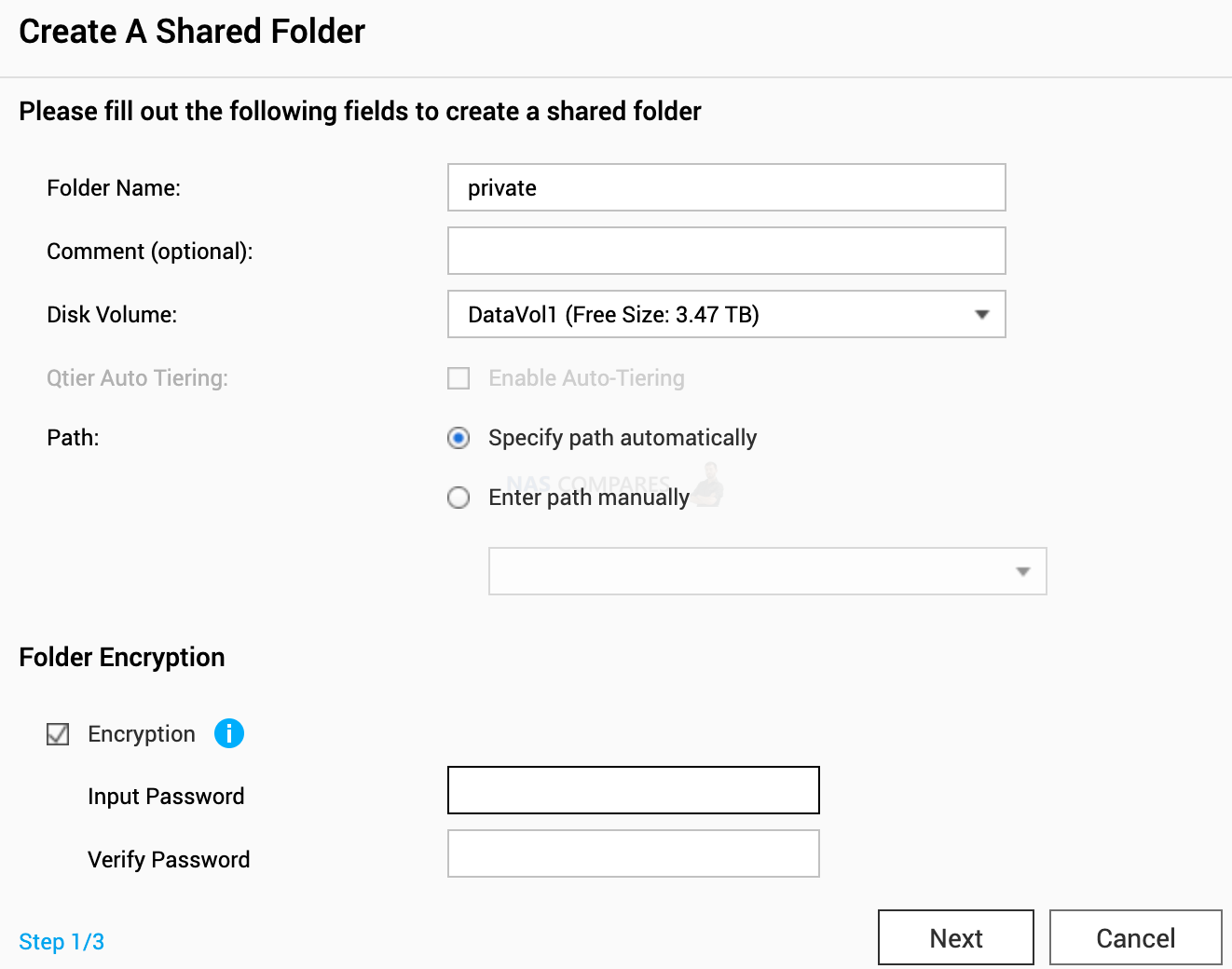
You can also specify different volume for each shared folder. This could also protect your data. Last ransomware attacked only volume1. Those with multiple volumes were not as affected. Especially who use volume one for OS and apps only. You can also encrypt shared folder. If someone steals your NAS, they can not see any data in this folder.
14. Use VPN to connect to your NAS (Norton etc.)
Never connect to your NAS via free WiFi. If you have to, use VON on your phone or computer. This will create a private network between your laptop and VPN server. No one in this free WiFi network will be able to see what you are doing. What data you are sending or receiving.
https://us.norton.com/products/norton-secure-vpn
15. Install an SSL (HTTPS) Certificate for Encrypted Access
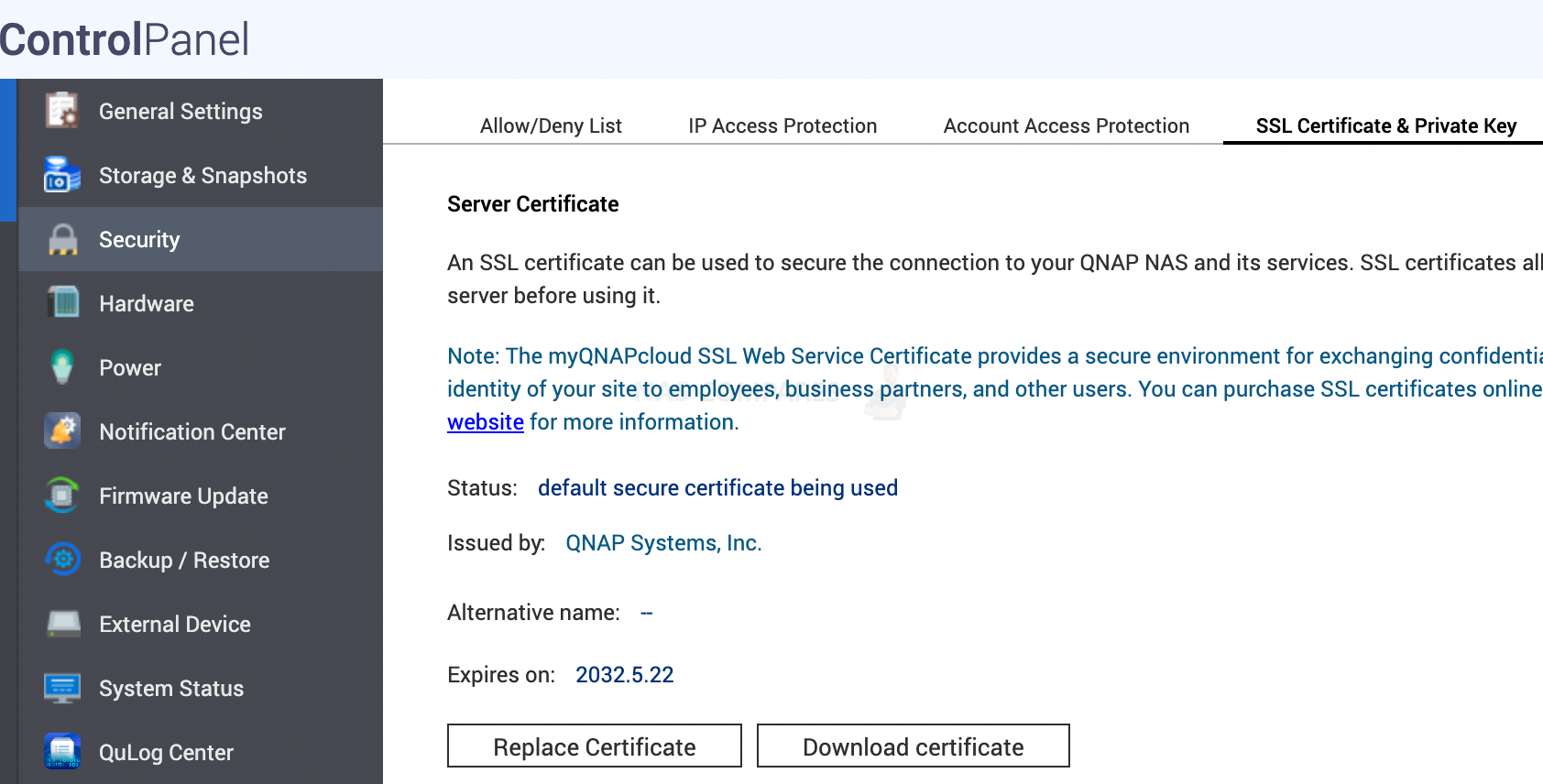
If you do not have VPN installed on your laptop and you are for some reason connected to free wifi or work wifi that you do not trust, always make sure you use HTTPS in the URL. This will encrypt any user names, passwords and any other data you fill in boxes on any website. Same applies to the URL when visiting NAS applications. If for some reason it has no HTTPS/ SSL/ TLS encryption enabled, you can install a new certificate in Control Panel/ Security/ SSL & private Key tab.
16. How to Separate and Isolate NAS Applications
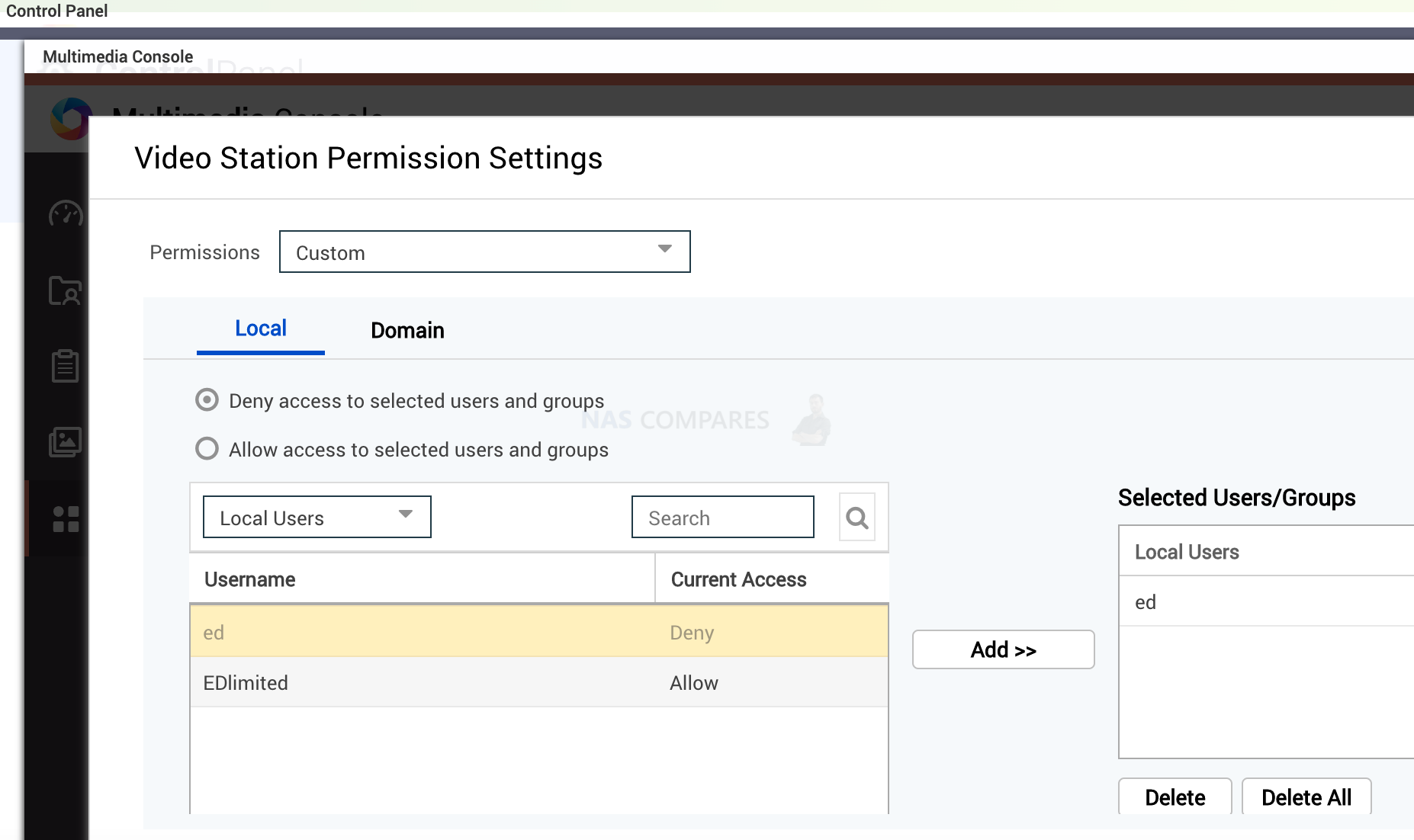
If there is a security hole within an app like Video Station, hackers will damage as much data as possible using the username from this app. If an app is using Admin-level access rights, hackers can not only damage this app but also gain access to anything else on your NAS. With Synology, you will notice that for example, Plex app has its own username and shared folder created automatically. This user has no other access. The worst hackers can do is delete or enjoy your movie collection. On QNAP you will need to create a Video user manually. Then you go to settings and allow only this user within the app. No admin.
Control panel/ multimedia console/ video station permission settings is the place to configure this. Similar steps apply to other apps.
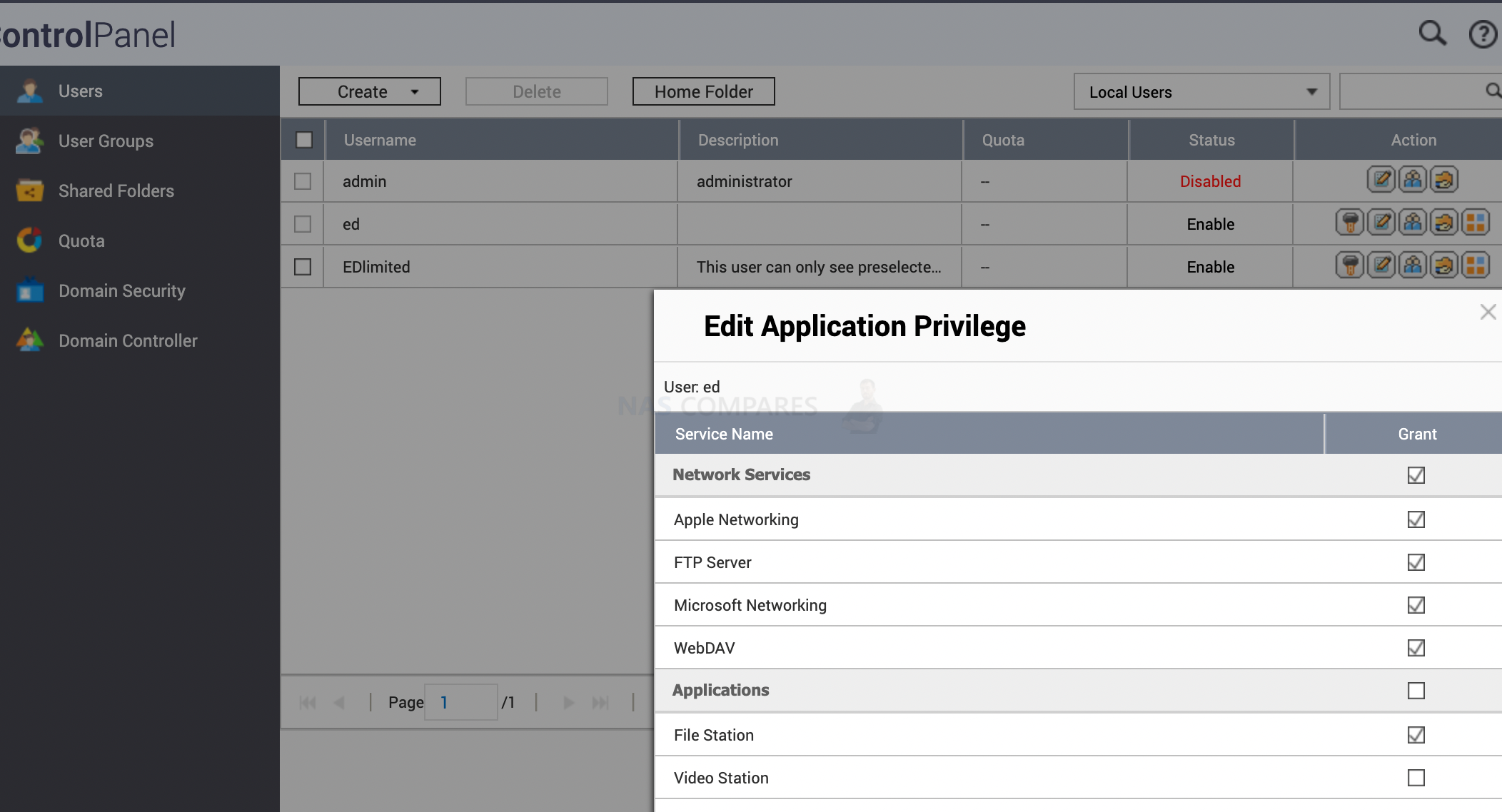
If you go to Control panel/ user groups and click the last icon (application privilege), you can choose which apps user can have access to.
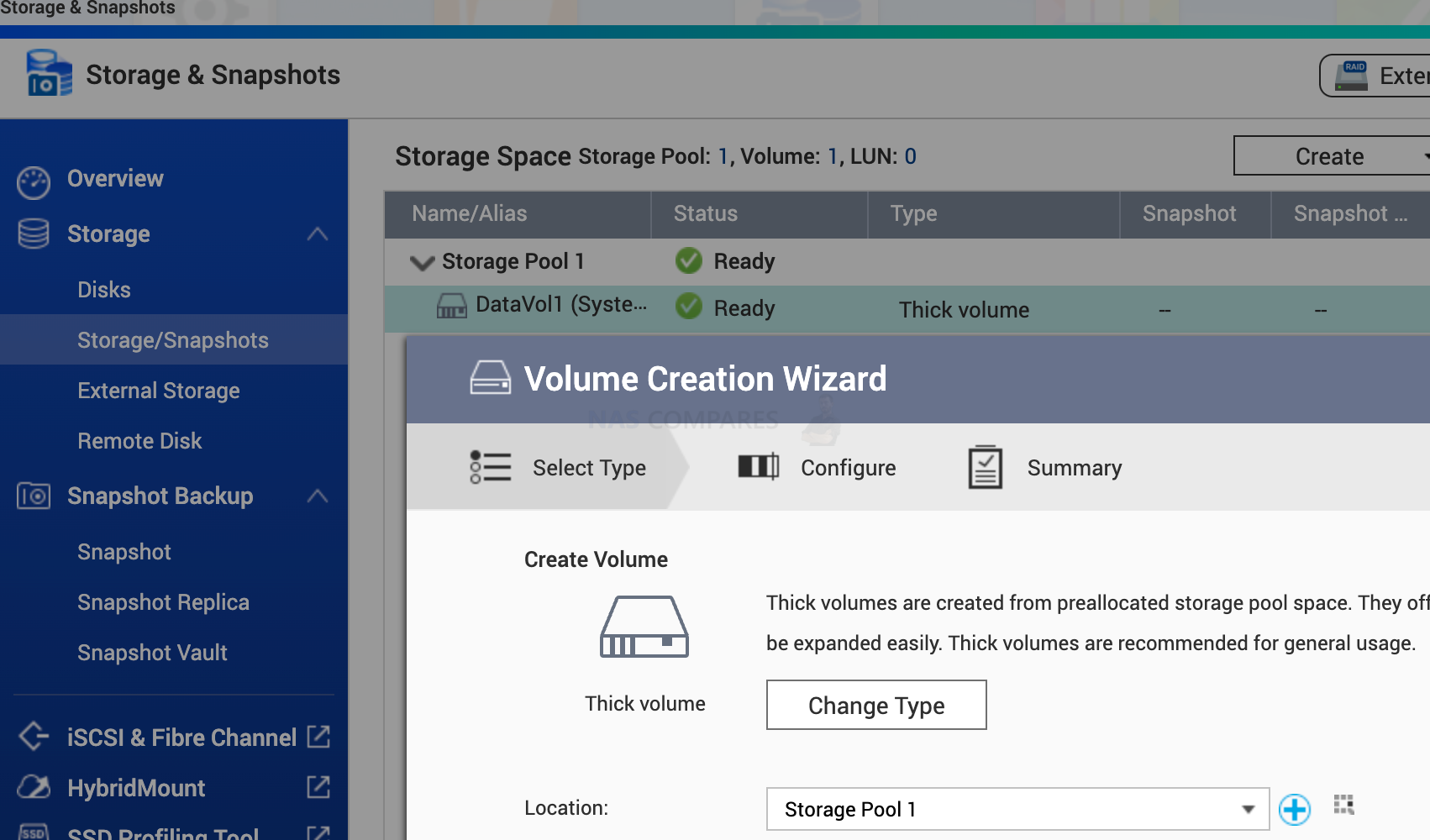
17. How to Separate Volume for Storage and the OS Installation/Storage
If you have separate volumes, this might save you from lazy hackers. In the last ransomware attack, they only targeted volume1. This saved a lot of people’s data.
You can create volumes under Storage & Snapshots / Create
18. Hide NAS IP with VPN
You can install VPN on your router or NAS. This way, no one knows what your real IP address is. This can prevent targeted attacks. Nord VPN will change your IP every 5 minutes. This is the average time hackers will need to scan through every single port on your network. So if they find open ports or vulnerabilities, it is too late. You now have a different identity. Do this only with trusted VPN service providers. At the end of the day, when you connect to any VPN server/proxy, you do not know who else is connected to that VPN.
I would use a separate MR2200ac router connected to my main router. All unsafe devices like smart plugs, light bulbs and other similar devices would connect to this individual WiFi network. These smart devices if hacked would have no access to your NAS and other important devices with sensitive data.
If you have Synology router with SMR 1.3 you can avoid setting this up on your NAS itself
To use your Synology Router as a VPN client, go to Network Center > Internet > Connection > Primary Interface > VPN settings to modify the settings.
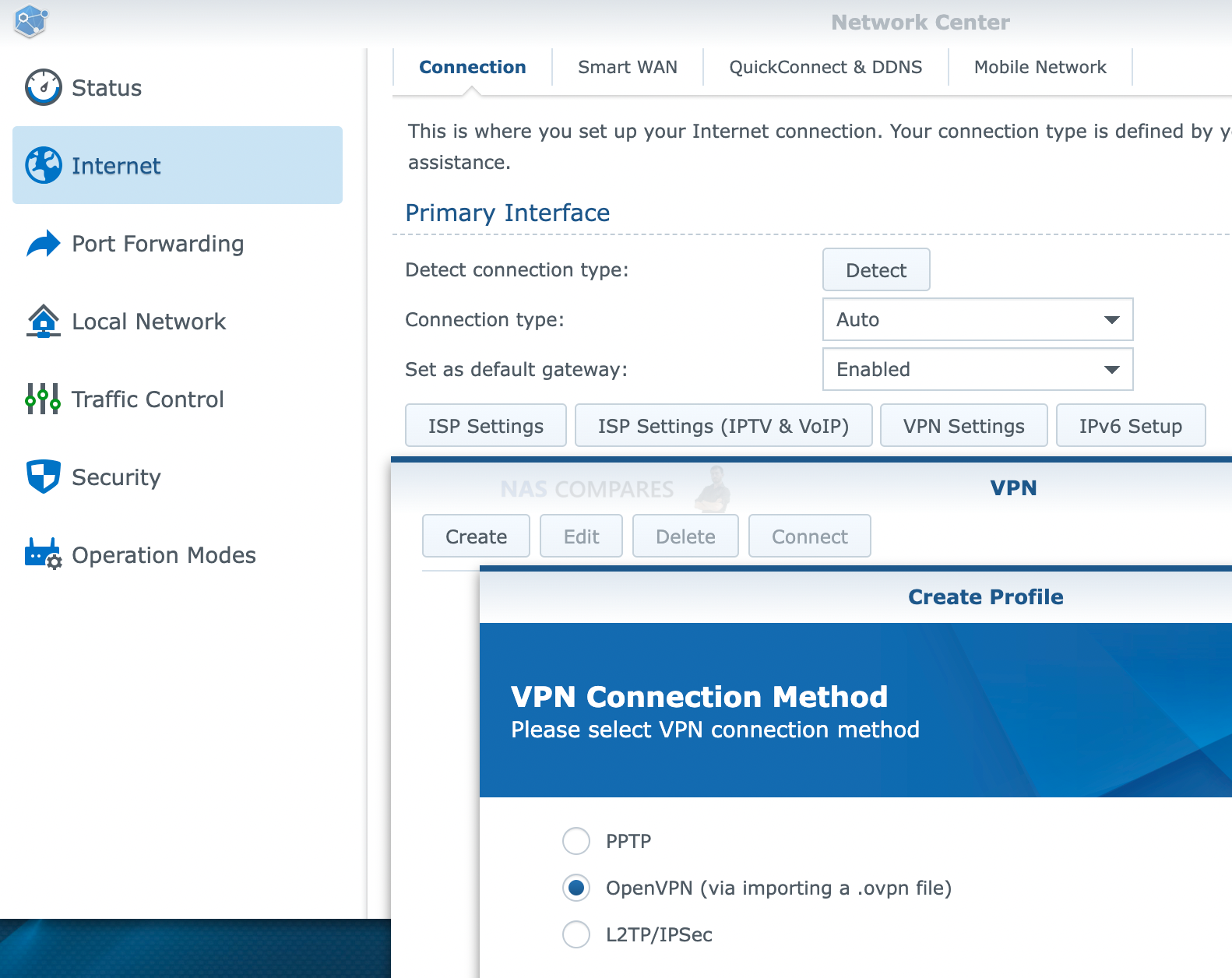
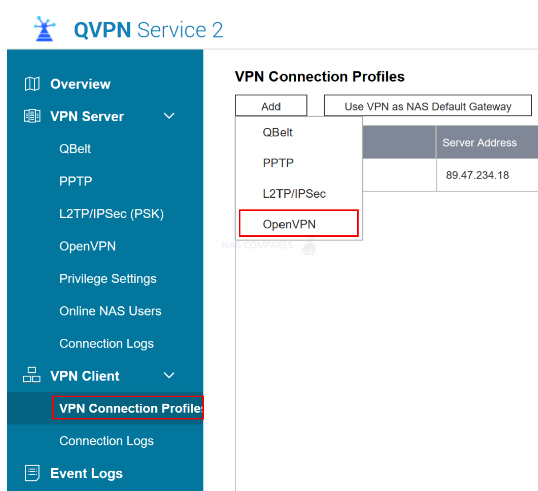
19. Alternatively, How to Use Open VPN, TeamViewer, nConnect , quWAN
You can create a VPN server on your NAS. You can then connect to your NAS via a computer client using this encrypted tunnel.
https://www.QNAP.com/en/how-to/tutorial/article/how-to-set-up-and-use-qvpn
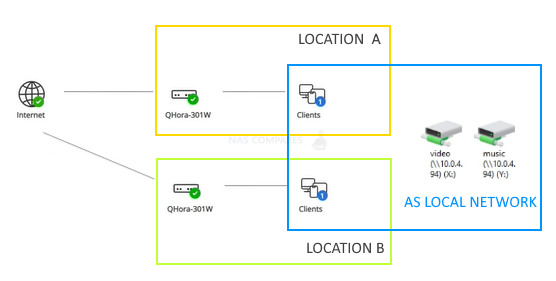
If you own QNAP smart switches and you want to link your office with your home, use quWAN. This will link these two networks together. This will give a feeling that you NAS and other network devices are actually in the same room.
Here is some more info https://www.QNAP.com/en-uk/software/quwan
Here is a video on how to set this up.
You can also achieve similar results with two MR2200AC routers (priced at around $100 each).
20. How to Isolate smart devices VLAN (plugs, speakers etc)
This allows you to create an invisible fence in your existing network. You can connect all devices using LAN ports on your switches/router. In the management portal you can select which LAN ports can or can not tlk to each other. So this way you can connect your NAS, computer and other important devices on VLAN1 and less trustworthy devices such as smart home system and speakers on VLAN2. Even though you ports on the router are closed, these smart devices are allowed to open doors from inside. Similar to your computer. You can only received data back after your computer have sent a request to some destination. This opens a private hole in your network for this transaction. Who knows how safe those cheap smart home devices are.
Here are some cheapest devices that support VLAN
21. Ubiquiti unify dream machine, pfsense, Synology switch with an intrusion system
As I mentioned in the paragraph above, your devices in your local network are opening and closing holes in your network every second. If your computer has a malware infection, it will be opening ports and sending your private data to hackers. You will notice your computer being slower than usual. I would recommend going to the system monitor and checking the resources consuming most of the CPU, running time etc. Then research what is service name is about. Also, go through installed apps and see if there is something you don’t recognise. And install Antivirus and scan the system when you notice unusual activity.
If you purchase DreamMachine router, pfsense or Synology router, you will get an intrusion system built in. This will scan all your internal network devices. What ports they are opening and where data is being sent. This traffic will be compared against databases that daily update IP lists from hackers etc. These routers will also block traffic from unknown devices that run a suspiciously high number of requests.
Here are a few DreamMachine, pfsense and Synology routers/switches.
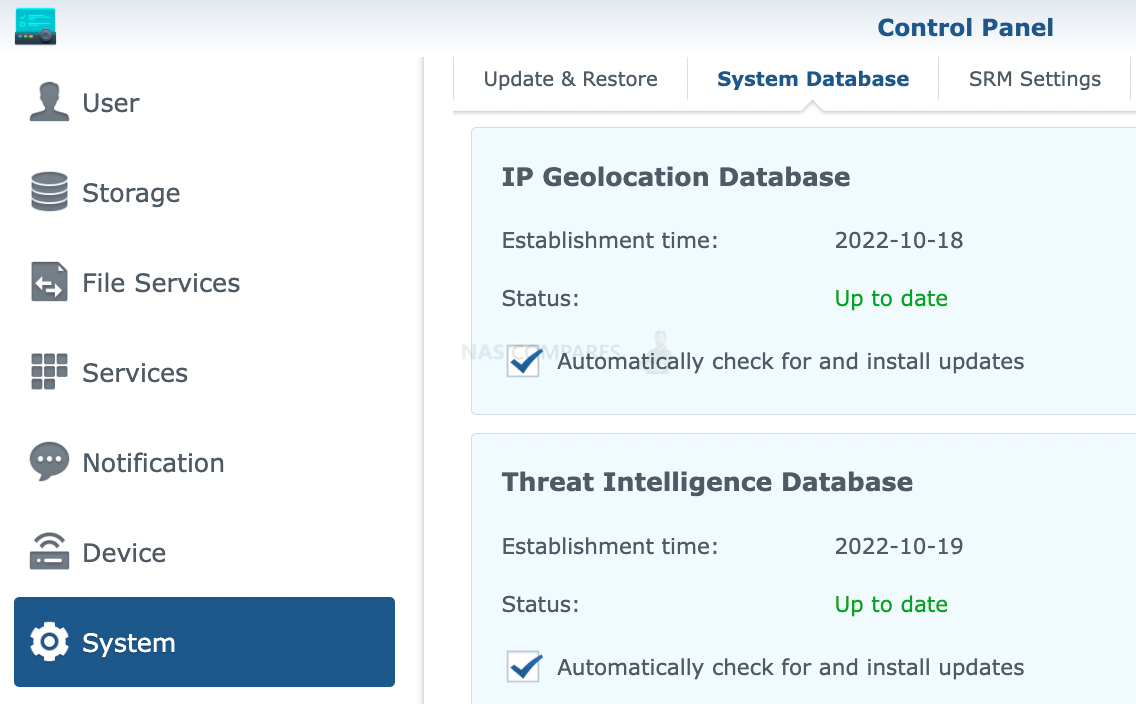
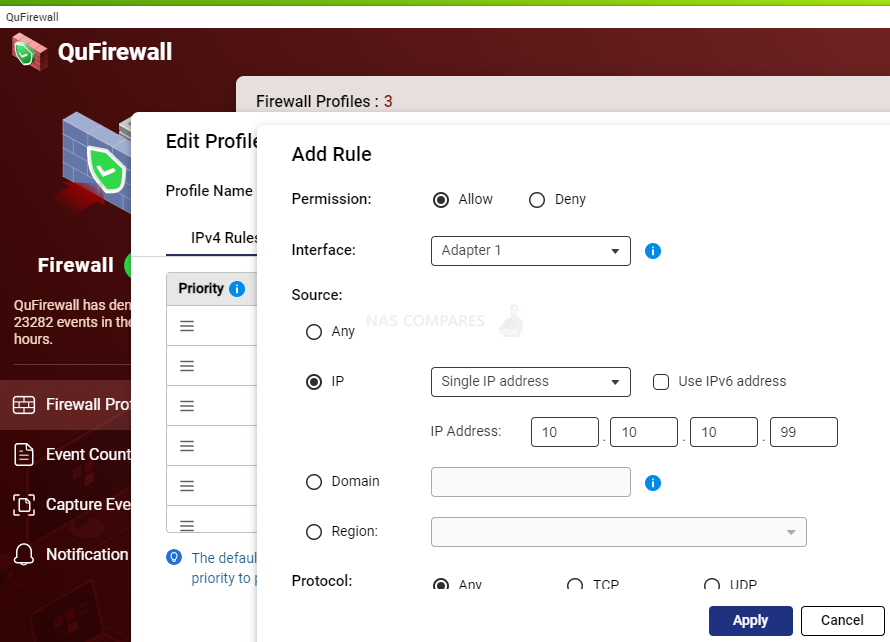
22. Firewall (IP based)
23. Backup, Backup, BACKUP!!!! Set up a QNAP NAS 3-2-1 Backup Routine
The last and most overlooked thing to do is a backup. It is not IF, but WHEN your NAS will be attacked, stolen or broken. Runing automated backups nowadays is easy. You can even make an agreement with a friend that you back up each others NAS. One reserves some space on their NAS for you, and you do the same for them. Every night or hour your data will be encrypted and stored there. Only you can access it.
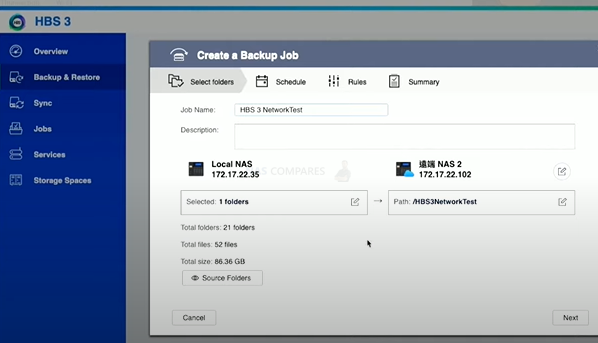
We covered pretty much ALL the ways you can backup your QNAP NAS in this video below:
Quick Setup – How to secure your Network?
- Secure your router
- Check open ports and close unnecessary ports
- Enable firewall
- disable ping response
- disable port forwarding [if there is no firewall and other measures in place]
- disable router remote management option
- Use WPA2 or newer WiFi mode and make sure the password is strong
- Guest WiFi (private)
- Use VPN
- Enable automated updates
- VLAN (smart devices)
- An intrusion detection system (Synology)
- Redesign your internal network
- Keep your network devices under different network segments
- Use switches with built-in firewalls and filters [Ubiquiti UniFi Dream Machine or unifi software]
- Add physical firewall [pfsense] https://shop.netgate.com/products/1100-pfsense
📧 SUBSCRIBE TO OUR NEWSLETTER 🔔
🔒 Join Inner Circle
Get an alert every time something gets added to this specific article!
This description contains links to Amazon. These links will take you to some of the products mentioned in today's content. As an Amazon Associate, I earn from qualifying purchases. Visit the NASCompares Deal Finder to find the best place to buy this device in your region, based on Service, Support and Reputation - Just Search for your NAS Drive in the Box Below
Need Advice on Data Storage from an Expert?
Finally, for free advice about your setup, just leave a message in the comments below here at NASCompares.com and we will get back to you. Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.
Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.

|
 |
Should You Worry About the NanoKVM Hidden Microphone?
Best Cheap NAS of 2025
Minisforum MS-02 Ultra - WHO IS THIS FOR??? (The First 48HRs)
Why People Use TrueNAS, UnRAID and Proxmox to Turnkey NAS (Synology, QNAP, etc)
Why People Prefer Turnkey NAS vs TrueNAS, UnRAID and More
The Top 5 Mistakes NAS Buyers Make
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.











I gotta say, as someone trying to find the videos you reference.. I am lost. Your organization could be improved. Also on the newest QNAP guide tour videos.. you named part 1 as Part 1…and then never again labeled anything else. SIGH.
REPLY ON YOUTUBE
Qnap’s in mo vlog’s house
REPLY ON YOUTUBE
Fantastic video. Thank you very much.
REPLY ON YOUTUBE
Hello! very good help! thank you! On the other hand, I have connected to OneDrive using HybridMount. I can see this new folder on QFile for Android but not in Qsync for Windows. How could I do that?
REPLY ON YOUTUBE
Great video with lots of good info. I have had my TS-853 Pro for 9 years now and I have not had any malware. I keep it off of the internet and always keep updates applied.
REPLY ON YOUTUBE
This video needs an update and to go a bit more in depth
REPLY ON YOUTUBE
Lots of things to check. I have noticed in the new version of 5.1.5 QTS. The login options include 2 step verification (password and OTP/authenticator) or passwordless (1 step) – last option is username and authenticator. I am thinking the 2 steps seems safer.
REPLY ON YOUTUBE
i was going to buy a nas— im not now
REPLY ON YOUTUBE
1:30 Your right a RAID is not a backup, but due to the functionality of how it’s implemented (ie. a nAS vs two external drives in sync), we call them different names, but the results are the same.
eg.. If you have 2x RAID 1 Hard drives, and one fails, the other still has your data..
If you have two external drives in sync (weather that be via software, or manually kept up to date),, if one of your external drives die, you STILL have your data safe on the other.
So, the way we think of a RAID vs backup depends on the environment itself, but they both keep our data safe if one drive dies.. ie they both serve the same purpose. For eg.. I don’t do raid, because I don’t want to loose storage capacity but I do have external drives synced.. so to me, that is just as good.
REPLY ON YOUTUBE
Please make an updated version of this video
REPLY ON YOUTUBE
Your walkthrough videos are incredible provide a plethora of valuable info. It would be super helpful if you could timestamp sections. Understably it’s tricky as many of you video are long form.
REPLY ON YOUTUBE
This was a bit of a skimmy.
Overviews are one thing, but you did say you would show how to set this up securely. That wasn’t delivered here.
REPLY ON YOUTUBE
The more secure you make things, the harder it will be to manage and jump through to get what your after. You could use 2FA, and encrypt volumes, for single person or two, all of that really is not required.. as long as you have good passwords for each user., and just gets in the way anyway.
encrypted volumes also slow down you NAS as well, but depends on the CPU/RAM your NAS has. eg TS-451 would better than TS-251
I would prefer user-based folder access for security than 2FA just because 2FA and volume encryption works as a “whole” where as user password and permissions are “per-user”
Much more simple to manage. Many people may disagree, but its my NAS so… ???? Just make sure you use strong passwords and that’s it.. Also, its bad practice to keep changing passwords every 180 days,,
Companies used to do this in the past ,thinking it was more secure changing regularly, but all it REALLY did was ****** off employees.
Sorry, i manage my own security
REPLY ON YOUTUBE
not gonna lie I wasn’t thinking 20 minutes later all i’d hear is change password and scan for malware, that hardly keeps the NAS secure, if I had a good password to begin with my security isn’t increased by changing it constantly. and doing a malware scan isn’t keeping me secure, stopping malware get on my system would be. and being notified of the lack of security is moot and not keeping me secure. password, update and scan malware. that takes 20 seconds. I thought you were going to show us how to disable certain ports, etc.
REPLY ON YOUTUBE
Is it better to use HBS 3 for time machine versus the build in qnap method by adding a user and a shared folder with smb 3? I think the second method is more flexible since I can add a user per mac and specify quota and stuff like that
REPLY ON YOUTUBE
I can’t find your updated version of QNAP NAS Setup Guide 2021/2022 #1 promised in the current version of #1 (https://youtu.be/_kCS6e1ZoiQ?t=2223). Could you provide that URL? Would be nice to have that link in this video’s description area as well us the #1 video.
REPLY ON YOUTUBE
very informative . i am movig from a drobo 5D to a qnap i wanted to know the best way to safley move 14TB of data tot he new qnap
REPLY ON YOUTUBE
Awesome vids. Thank you, mate! When enterprise versiones release?
REPLY ON YOUTUBE
Very BASIC security settings but the best security for QNAP is to keep all services OFFLINE completely so I absolutely NEVER use QNAP Cloud!
As of January 2023 QNAP still has major online security issues so I will not trust QNAP online servers, nor cloud services and especially not email notifications handled by QNAP.
For email notifications to be sent…QNAP needs QNAP email servers. Today QNAP products are still vectors for ransomware so please Do NOT connect to QNAP servers!
Novice QNAP users should be offline ONLY, therefore should not be using notifications nor QNAP Cloud.
REPLY ON YOUTUBE
Hello, I followed you previous video and now I looking at this one. I see that now you have THREE more
folders that where not there before. I see “home” “homes” and “Multimedia” can you explain where they came from? After a Drive failure and a NAS refusing to rebuild, I reset my NAS to default, formatting initializing everything, now I want my system working as it did before…..I am not seeing “default folders”
REPLY ON YOUTUBE
Is myqnapcloud the only thing that “connects us to the internet.”
So my question is as long as I disconnect from myqnapcloud then a large majority of my risk goes away?
REPLY ON YOUTUBE
Great Information! As a private User (I am interested in buying a NAS) I still have Problems to realize the borders of my „private“ network behind my router and the www.
For example why are some of my IoT appliances at home able to do an automatic SW update? So, they can somehow go into the www, even without getting an released port from my router. At least I did not manage any port on my router for this …
On my Notebook, I am using a Firewall & Virusscan. Now I understood, that the router is acting as a firewall. But still the same question, how can the Notebook or a NAS just get access to www… ?
Or does every IoT device which I add in my nerwork gets automatically the trust to access the www?
This is how it works. No one can access your home network from outside. But there is no limits for devices in your network to reach out of your network.
If a device in your internal network connect to a server outside your network it creates a temporary gateway for that external server to reply. Assuming that – if you reached out – this server must be safe. This is why you should keep cheap iot/ smart plugs etc in a separate virtual network- VLAN. Who know what gateways those things are opening.
I hope this helps.
Can you do a video with the best firewall configuration for a multimedia qnap server like the tvs h674 without using the upnp method?…. thanks again.
REPLY ON YOUTUBE
I was hit by deadbolt ransomeware some weeks ago. Finally I got the key and my files have been fully decrypted. Thank you…
REPLY ON YOUTUBE
Have you done a video on how to set up let’s encrypt SSL for secure remote access to a NAS?
I’m just a simple Plex user and moved awhile ago, that whole time my Nas was unplugged and unused for 2 years and I recently plugged it back in after setting up a media room. My NAS wouldn’t update firmware so I updated it manually with a flashdrive and I needed to make a whole new mycloud account for some reason. It’s been a pain getting it all set up but it’s currently in sleep mode. Am I still safe?
I did manage to set up 2FA on admin and basic user account and I’ll see about setting up the X failed password revoking privileges
REPLY ON YOUTUBE
Thanks a lot!
REPLY ON YOUTUBE
You didn’t mention running a VPN. 🙁 That saves so much complexity.
REPLY ON YOUTUBE
The first guide was fantastic. This guide is extremely confusing.
REPLY ON YOUTUBE
Worker with a reliable hacker is what I think is all over the world and I recommend a hacker parfait who works with good heart and sincerity Dee_hack11 is in Seoul☝️☝️☝️.
REPLY ON YOUTUBE
If i don’t have QNAP Cloud installed, does that mean that i am not connected to the internet?
Is sending email notification not a good idea, considering i don’t want to link my NAS to the internet?
REPLY ON YOUTUBE
Great stuff, I appreciate you sir!
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
*I was hit, so unplugged, shutdown, external USB backs fine. Plex user, was watching at the time no issues, went to update saver denied, then found the splash screen, no on reboot, water gapped on an independent switch no WiFi etc, it instantly goes to initialization. So save to assume the service themselves have been affected. Did safe shutdown. After some time I turn on everything then I found out I’ve been truly hit by deadbolt. I did as many research as I could and I found out that scott can actually decrypt the encrypted files So I paid some money not upto what deadbolt team are asking, then he decrypted my files*
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
.You can message *SCOTTS_HACK*
REPLY ON YOUTUBE
.You can message *SCOTTS_HACK*
REPLY ON YOUTUBE
These methods are great. Was wondering if there is a way to backup files from your PC (documents downloads desktop folders) periodically to the NAS?
REPLY ON YOUTUBE
Forgive that this may be a stupid question. But – if you have a QNAP NAS plugged in to your computer – and your computer is connected to the internet – does that mean your NAS is connected to the internet also? Or – is the hacking security risk purely for if you choose to directly connect the NAS to the internet (and therefore if you don’t, you risk free)?
REPLY ON YOUTUBE
will adding 2step verification change the way using share links work (ie: sending a share link to a shared folder on my nas to friends via email)?
REPLY ON YOUTUBE
Let’s see if I have this right: QSync is going to “merge” changes made to a single file by multiple users? So it is a content management app? Just asking…
REPLY ON YOUTUBE
What’s the difference between QSync and regular ‘map network drive’?
REPLY ON YOUTUBE
I have one hair follicle left after trying EVERYTHING to get a Qnap TS-212 to backup to a new TS-231P3. The ‘problem’ is that HBS is different on the old NAS and no matter what I do, I cannot get it to allow a backup. So, I worked around the problem by accessing the newer TS-231P3 using HBS 3 and telling that to ‘restore’ the folder of all my work, rather than backup. I’m at 5% and counting. Fingers are crossed.
REPLY ON YOUTUBE
Hi, Thanks for the great video!
Would you be able.to elaborate on sharing the file process to an external temporary user, please?
REPLY ON YOUTUBE
Is there something specific to do to make Qsync works ? I can’t connect to my NAS from windows with it. With the correct IP, login and password
REPLY ON YOUTUBE
I miss the most important step, formatting and throwing away the QNAP.
REPLY ON YOUTUBE
If you add a 00:00 time to the chapter list it will add the chapters to the scrubber (video progress bar), you can for example call it: 00:00 Intro
Great videos, love the in depth explanation. It is easy to set up the NAS, but to really use it is hard, so thanks a lot!
REPLY ON YOUTUBE
Found the presentation very irritating. Why keep wizzing the cursor around the screen. Why not use a large black cursor. Don’t do everything so quickly.
REPLY ON YOUTUBE
I have an older TS-469 Pro running 4.3.4, so I guess my NAS is somewhat obsolete in terms of available applications such as Security Counselor
REPLY ON YOUTUBE
Thank you very much for these helpful videos. I’ve got a TS-128A and a TS-230 to setup and I’ve only had experience with Synology and WD NASes previously. Seems like QNAP is more complex but more flexible at the same time with generally better hardware for the price.
REPLY ON YOUTUBE
Loving the videos! Thank you 🙂
My QNAP arrives next week. I’m at about 36 mins in this video so far so if my question get’s answered then don’t worry… I’m currently using Dropbox to sync a folder we’re both working in on my computer and a colleague’s computer over the internet. How would I do this with QNAP?
AND I send files to clients by right clicking and hitting “make transfer” with Dropbox. Can I do that with QNAP or do I have to use the web interface?
REPLY ON YOUTUBE
I don’t have the QuFirewall and the SSecurity Counselor available sadly, at least it just doesn’t want to install. Probably because my NAS is way too old, running QTS 4.2.6
REPLY ON YOUTUBE
WOW. Nice find here!! Great video.
REPLY ON YOUTUBE
“previous video i did guide You through how to set up a snapshot”…
You mean in video: QNAP NAS Setup Guide 2022 #1 ??
there i didnt found that.. 🙁
REPLY ON YOUTUBE
Your Synology NAS Setup Guide videos are still NOT AVAILABLE (only #1 – #3)
REPLY ON YOUTUBE
This was great. Keep it up with QNAP. Can we explore some of their media Apps? Believe me sir – you do everything right! Happy New Year!
REPLY ON YOUTUBE
Thank you. Wish I’d seen your recommendations BEFORE the Qlocker attack.
REPLY ON YOUTUBE
hello sir your videos is so helpfull for me but i am confuse with how to configure alnet ssystem software with qnap nas storage i have configure qnap nas storage raid 6 with 4tb *12 hdd 1 hdd in spare but i am able to see live video but not able save nas storage so can you help me how to add path in qnap nas storage for save recording. Thanks,Jerry Upadhyay
REPLY ON YOUTUBE
If Norton or Bitdefender is installed as your main antivirus, will they be able to work on Qnap NAS? Instead of MacAfee, which for instance I don’t like.
REPLY ON YOUTUBE
Dude. Just a side note after watching 150+ videos. I have NEVER heard “noise in the background” so please stop apologizing for it. Not. Once. Ever.
REPLY ON YOUTUBE
I wish I saw this video before ???? apparently Qnap got hit with a massive ransomware attack this year and I had no idea. My files are all encrypted by some hacker asking for Bitcoin in exchange for passwords ????
REPLY ON YOUTUBE
Changing the default port does not enhance security. Security by obscurity. Port scanners can detect open ports it might fool some scripts.
Most people who serious about securing administrative interfaces dont expose them directly to the internet period.
Thats terrible terrible terrible security pratice.
A seperate vpn server with a dedicated vlan for admin is what you should be using to secure the admin interface and remotely managing the nas.
Example
Setup vlan 100 for management
Setup vlan 201 for cifs
Setup vlan 202 for iscsi
Setup vlan 300 for public network (internet)
Setup vpn server in dmz with one arm into the public network (300) another arm into vlan 100.
Setup logging and auditing.
Ensure 2fa exists for vpn service.
The qnap should have ports trunked with vlan 100,201,202 or dedicated ports.
Assign the services ip addresses in each of the ranges.
I never ever bother changing port numbers it simply offers very little security and may just elude some scripts scanning on certain ports
REPLY ON YOUTUBE