Severe D-Link Security Vulnerability Discovered – CVE-2024-3273 and CVE-2024-3274 Hard-Coded Credential Backdoor

The cybersecurity landscape has been significantly impacted by the discovery of two vulnerabilities in D-Link NAS devices, designated as CVE-2024-3273 and CVE-2024-3274. These vulnerabilities affect multiple (approx 92,000 internet facing devices, the bulk of which are UK based) D-Link NAS models that are no longer supported by the manufacturer due to their end-of-life (EOL) status. This detailed analysis aims to unpack the complexities of these vulnerabilities, their operational implications, and the necessary user responses.
Impact and Affected D-Link NAS Model:
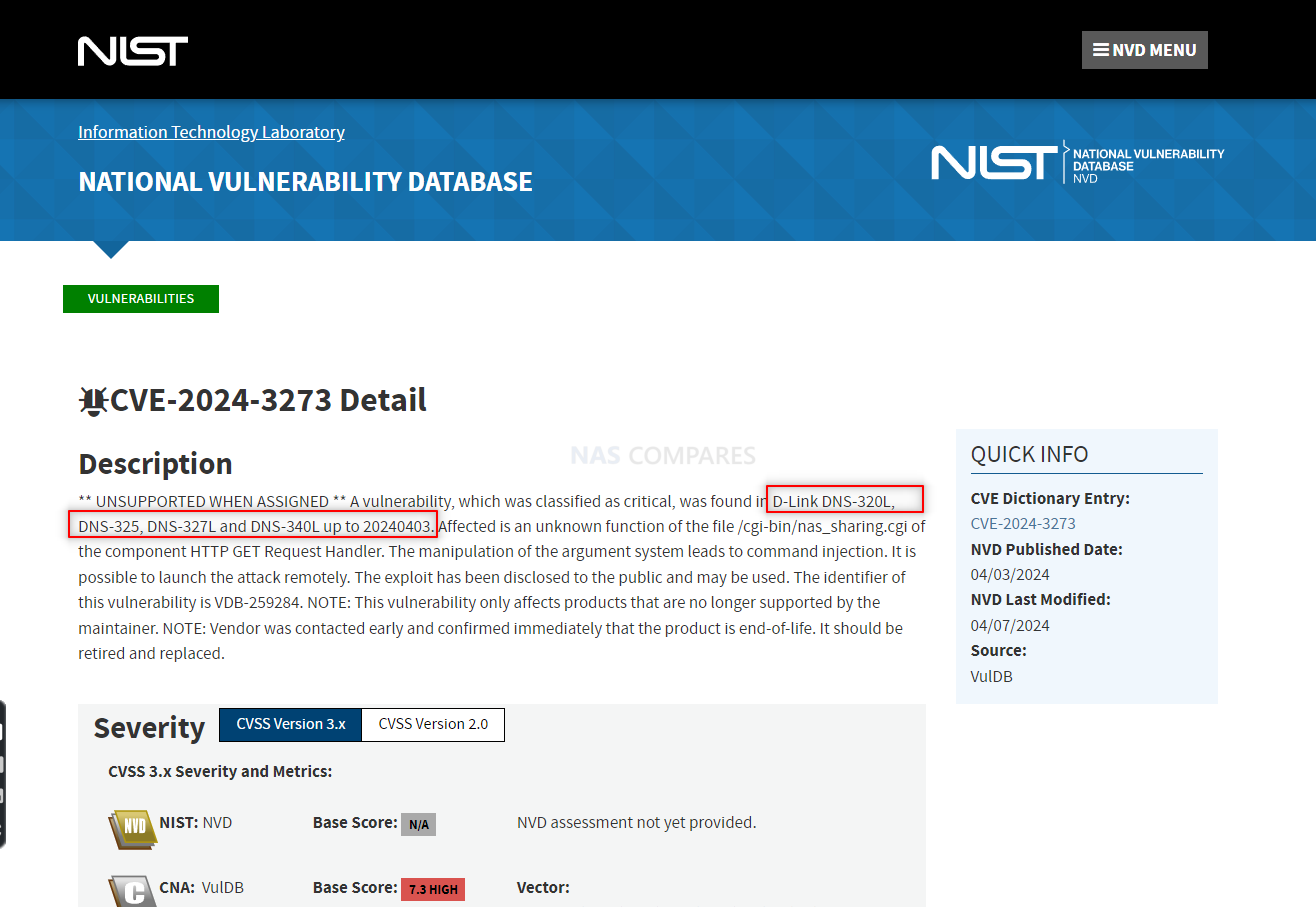
The confirmed list of affected D-Link NAS models includes:
| Model | Region | Hardware Revision | End of Service Life |
Fixed Firmware | Conclusion | Last Updated |
| DNS-320L | All Regions | All H/W Revisions | 05/31/2020 | Not Available | Retire & Replace Device |
04/01/2024 |
| DNS-325 | All Regions | All H/W Revisions | 09/01/2017 | Not Available | Retire & Replace Device | 04/01/2024 |
| DNS-327L | All Regions | All H/W Revisions | 05/31/2020 | Not Available | Retire & Replace Device | 04/01/2024 |
| DNS-340L | All Regions | All H/W Revisions | 07/31/2019 | Not Available | Retire & Replace Device | 04/01/2024 |
These devices, pivotal in small office/home office (SOHO) environments for data storage and management, are now susceptible to remote attacks that could compromise sensitive data integrity, availability, and confidentiality.
CVE-2024-3273: Command Injection Vulnerability Explained
CVE-2024-3273 exposes a command injection flaw within the web interface of affected D-Link NAS devices. The vulnerability is located in the handling of the system parameter within the nas_sharing.cgi script, which improperly sanitizes user-supplied input. This oversight allows authenticated remote attackers to inject and execute arbitrary shell commands encoded in base64. The execution context of these commands is particularly concerning, as it typically runs under the web server’s privileges, potentially leading to unauthorized access to the system, modification of system settings, or initiation of a denial of service (DoS) attack.
Technical Dive into CVE-2024-3274: Hardcoded Credentials
CVE-2024-3274 reveals a hardcoded credential vulnerability, manifesting as a backdoor account (messagebus) embedded within the device firmware. This account, notably lacking a password, permits unauthenticated remote access to the device’s administrative interface. The presence of such hardcoded credentials significantly lowers the complexity of unauthorized device access, making it a critical vulnerability. This backdoor could be exploited in tandem with CVE-2024-3273 to elevate privileges or gain persistent access to the compromised device.
Who Found the D-Link Vulnerability?
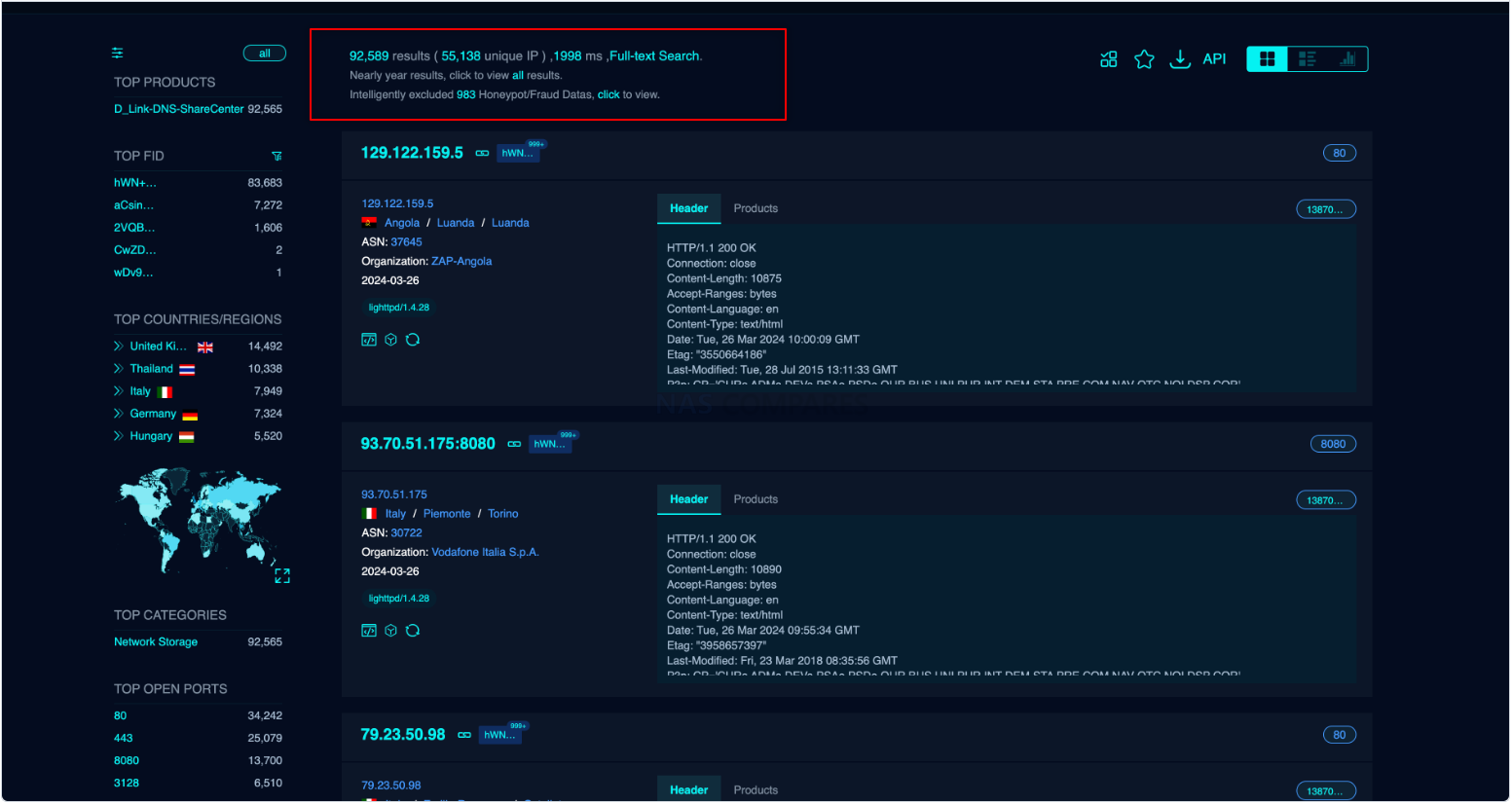
The vulnerabilities were disclosed by a security researcher operating under the pseudonym “netsecfish,” who provided detailed technical insights and proof-of-concept (PoC) code. This disclosure highlighted the risk of widespread exploitation, given the estimated 92,000 devices exposed online across various regions, including the UK, Thailand, Italy, and Germany. The timing of the disclosure, subsequent to the affected models reaching their EOL, exacerbated concerns around feasible mitigation strategies.
You can find the full and very detailed outlining of the Vulnerability and Potential attack vector HERE on Netsecfish’s github listing
Mitigation Strategies for Users Who Are Still Using A D-LInk NAS
In light of D-Link’s stance on not providing firmware updates for EOL products, affected users are faced with limited mitigation options. The primary recommendation is the retirement and replacement of vulnerable devices. Interim measures, for those unable to immediately replace their devices, include isolating the NAS devices from the internet, implementing strict network segmentation, and employing firewall rules to restrict access to the management interface. Additionally, monitoring for unusual network activity can provide early detection of exploitation attempts.
D-Link Official Response
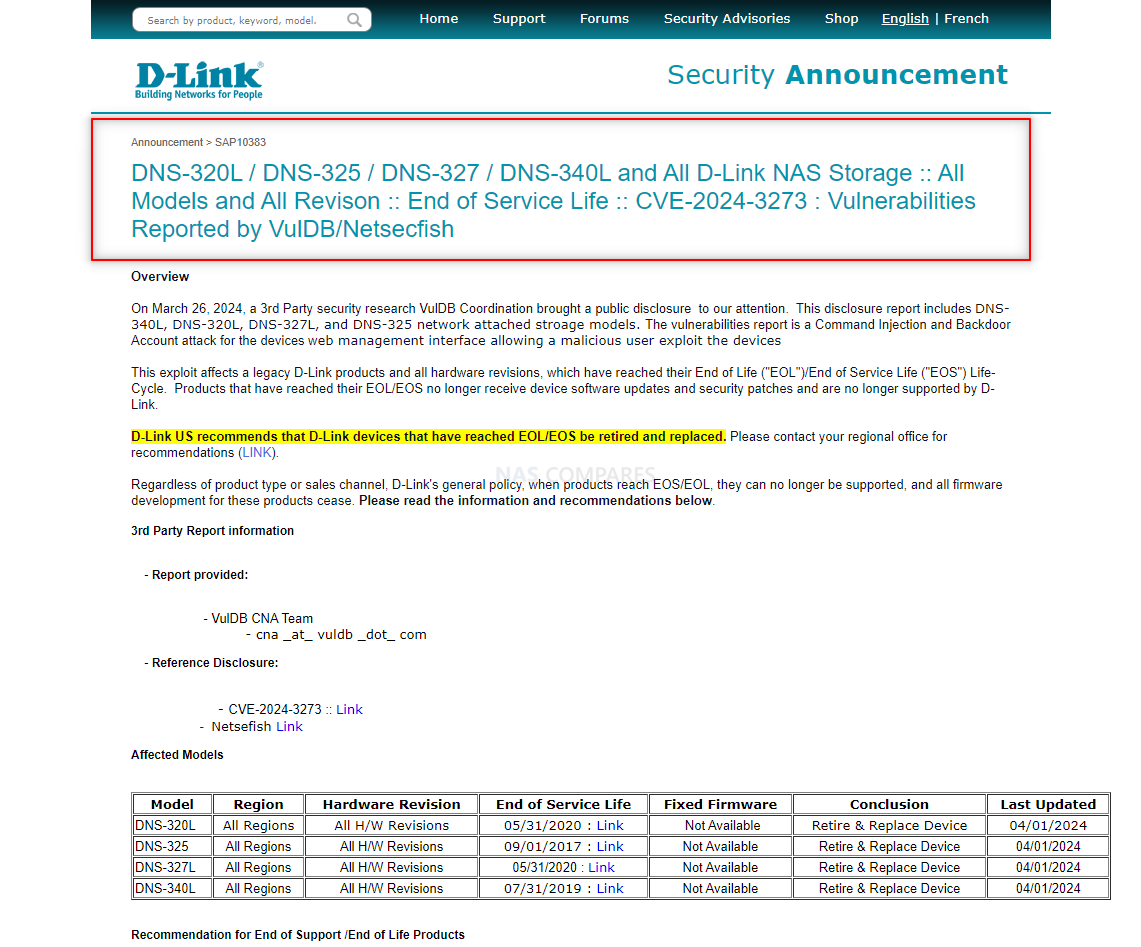
D-Link has acknowledged the vulnerabilities but emphasized the EOL status of the affected models, which precludes official firmware updates or patches. The company has issued advisories urging users to replace outdated devices with supported models. This situation underscores the importance of adhering to device lifecycle policies and maintaining an updated infrastructure to mitigate security risks.
You can see the full official D-Link Response HERE
At the time of writing, there is no mention of this on their social media pages. Hopefully this changes, as the potential 82,000 internet facing units in the wild need to be addressed.
Exploitation in the Wild of the hard-code credential D-Link Vulnerability
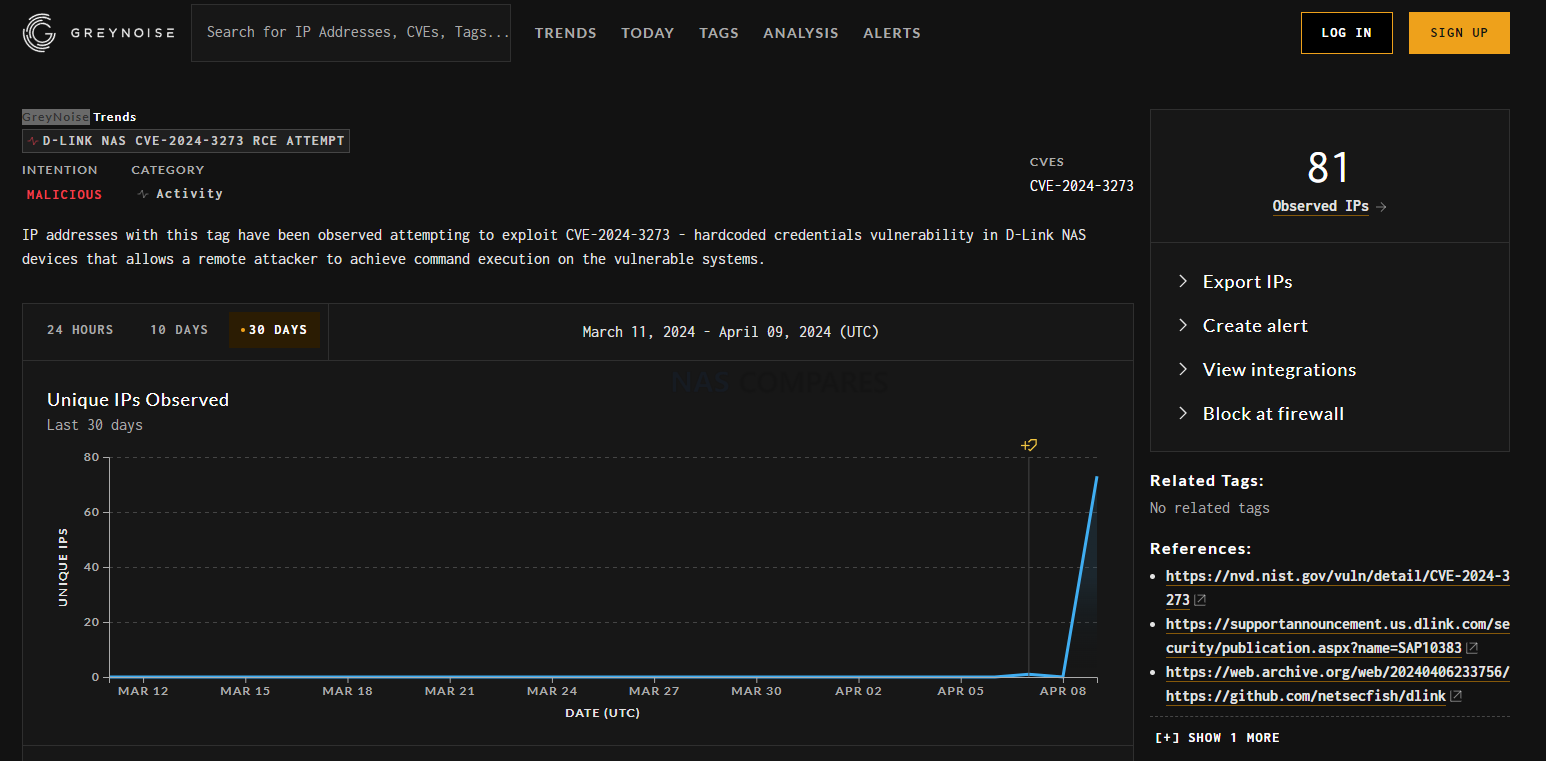
GreyNoise, a cybersecurity firm specializing in analyzing internet-wide scan traffic to identify threats, has provided valuable insights into the exploitation attempts of the D-Link NAS vulnerabilities. According to their analysis, a significant uptick in scan activity targeting the specific vulnerabilities CVE-2024-3273 and CVE-2024-3274 was observed shortly after their disclosure. This activity suggests that attackers are actively seeking out vulnerable D-Link NAS devices for exploitation. GreyNoise’s findings indicate that the exploitation attempts are not isolated incidents but part of a broader effort by malicious actors to identify and compromise affected devices. The data collected by GreyNoise highlights the real-world implications of these vulnerabilities and serves as a critical alert for organizations and individuals to take immediate protective actions against potential unauthorized access and exploitation of their D-Link NAS devices.
You can learn more about this on Greynoise’s official page on this matter HERE
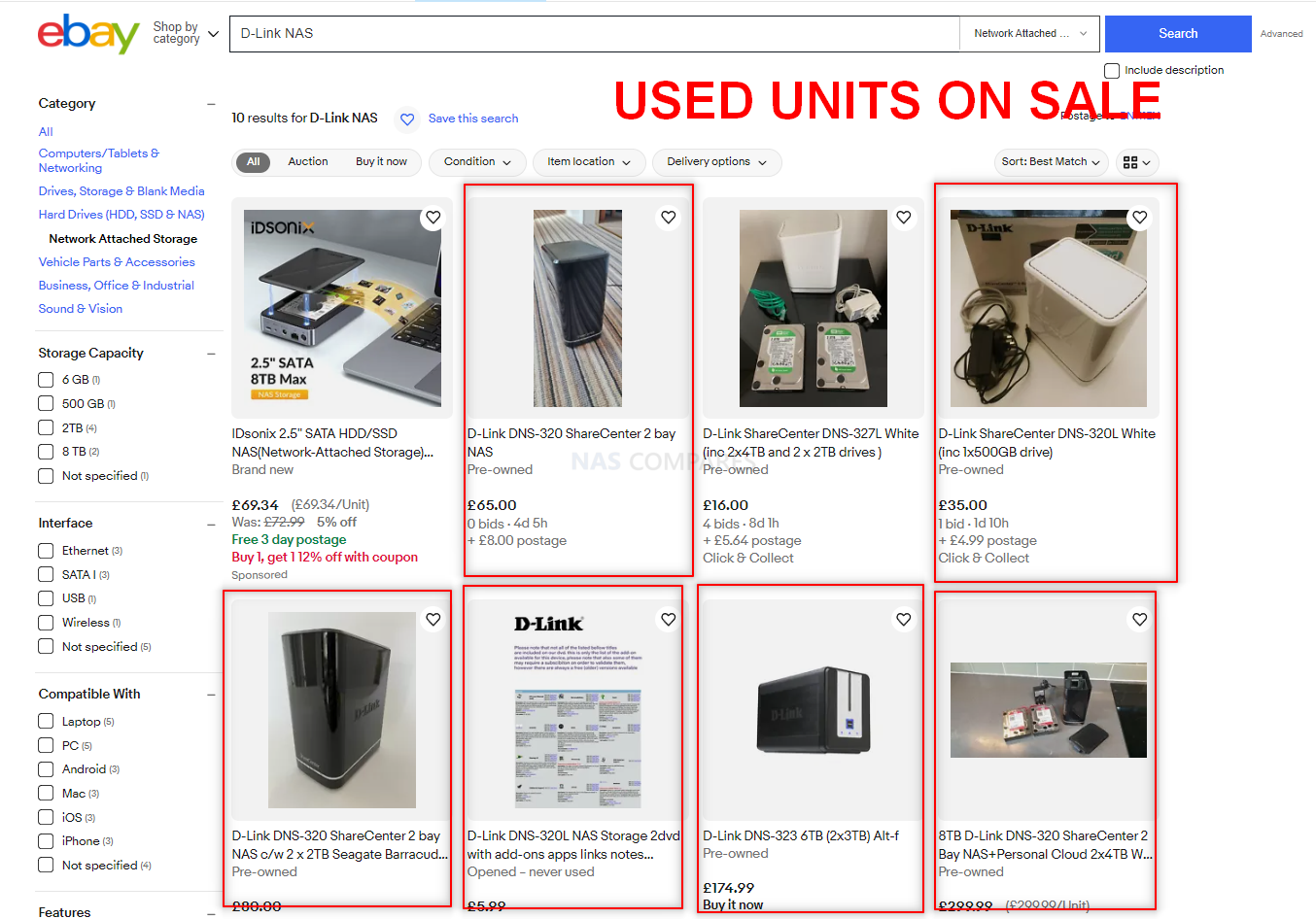
The D-Link NAS Series is Still For Sale (Technically)
Despite the end-of-life status and known vulnerabilities of D-Link NAS models DNS-340L, DNS-320L, DNS-327L, and DNS-325, these devices continue to find a marketplace on platforms such as eBay and other online resale venues. This ongoing sale of used units poses a significant cybersecurity risk, as many sellers and buyers may not be fully aware of the devices’ vulnerability to exploits. Alarmingly, at the time of writing, it is reported that over 80,000 of these units remain actively internet-facing, directly exposing them to potential exploitation by attackers leveraging the CVE-2024-3273 and CVE-2024-3274 vulnerabilities. The persistence of these devices in active operational environments underscores the critical need for heightened awareness and proactive measures among current users. Potential buyers should be cautioned against acquiring these models, and existing users are strongly advised to consider secure alternatives that receive current manufacturer support and updates, mitigating the risk of compromise.
I own a Synology/QNAP NAS, Should I Care? How to Automatically Get Updated When Synology and QNAP NAS Vulnerabilities are Reported
Pretty much ALL of the brands in NAS, Data Storage and Cloud services have these security advisory pages, but the idea of checking these pages manually (i.e. bookmark etc) every day, week or month is too much of a hassle for many. On the other hand, they all arrive with an RSS feed link that allows users to subscribe to updates BUT many users are not even aware of how to apply an RSS feed (it’s a complex XML feed of text that needs to be injected into an appropriate RSS feed client/agent – so yeah, hardly noob friendly). So, in order to make this 1000x easier, I have (and by me, I mean Eddie the Web Guy spent time on it and I made this article!) made this page that will be constantly updated with the latest vulnerabilities reported on the popular NAS brands and storage-related manufacturers. It is still being built (so more brands are being added) but it will allow you to just chuck your email address below (will not be used for profit or spamming etc) and then you will get an alter EVERY TIME a new security vulnerability is updated by the brands (this is automated, so it will appear here as soon as it appears on the respective security advisory page). Additionally, there will be links back to the brand/manufacturer site so you can find out more about individual exploits and vulnerabilities, how they work, what they do and (most importantly) give you a better idea of whether you should update your NAS/Storage system or not. I hope you find it helpful and if you have any recommendations or idea of what we should add to this page/service to make it even better – let us know in the comments or directing here – https://nascompares.com/contact-us
Sign Up Below to Get Updates as New Vulnerabilities Are Reported
Get an alert every time something gets added to this specific article!
Find an updated vulnerability list here:
Comprehensive User Recommendations
Beyond immediate mitigation, users should consider several best practices for network device security:
- Conduct regular security audits of network devices.
- Update all devices to the latest firmware versions where possible.
- Employ network firewalls and intrusion detection systems to monitor and control inbound and outbound traffic.
- Practice the principle of least privilege by restricting device access to necessary personnel.
Conclusion
The vulnerabilities identified as CVE-2024-3273 and CVE-2024-3274 in D-Link NAS devices present significant security challenges. The absence of official firmware updates for these EOL products necessitates proactive user measures to mitigate risks. This analysis serves as a call to action for users to evaluate their network security posture critically, implement robust security measures, and ensure that all network-attached storage devices operate within their supported lifecycle.
📧 SUBSCRIBE TO OUR NEWSLETTER 🔔
🔒 Join Inner Circle
Get an alert every time something gets added to this specific article!
This description contains links to Amazon. These links will take you to some of the products mentioned in today's content. As an Amazon Associate, I earn from qualifying purchases. Visit the NASCompares Deal Finder to find the best place to buy this device in your region, based on Service, Support and Reputation - Just Search for your NAS Drive in the Box Below
Need Advice on Data Storage from an Expert?
Finally, for free advice about your setup, just leave a message in the comments below here at NASCompares.com and we will get back to you. Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.
Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.

|
 |
| Where to Buy a Product | |||
|
|
    
|

|
VISIT RETAILER ➤ |
 |
    
|

|
VISIT RETAILER ➤ |
We use affiliate links on the blog allowing NAScompares information and advice service to be free of charge to you. Anything you purchase on the day you click on our links will generate a small commission which is used to run the website. Here is a link for Amazon and B&H. You can also get me a ☕ Ko-fi or old school Paypal. Thanks! To find out more about how to support this advice service check HERE
UnifyDrive UP6 Mobile NAS Review
UniFi Travel Router Tests - Aeroplane Sharing, WiFi Portals, Power Draw, Heat and More
UGREEN iDX6011 Pro NAS Review
Beelink ME PRO NAS Review
UGREEN iDX6011 Pro - TESTING THE AI (What Can it ACTUALLY Do?)
OWC TB5 2x 10GbE Dock, UGREEN NAS Surveillance Software, AceMagic Retro PCs, Gl.iNet Comet 5G @CES
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.







I have a DNS-323, but there’s NO WAY that I’d let it be accessible from the Internet. Also, I stopped buying D-Link around a decade ago when they shut down some service that the router I had needed to contact on boot, which essentially bricked it without warning. They have lost all credibility IMO.
REPLY ON YOUTUBE
I know someone who has the DNS-320 Pulse (not the 320L). I checked with him and he has the latest available BIOS for it and it is NOT forwarded to the internet.
Anyone knows if this model is affected and if so he has anything to worry about with these settings?
Answers are much appreciated.
REPLY ON YOUTUBE
A hard-coded vulnerability like this is intentional and was meant to be there. My guess is to remain a hidden vulnerability that both law enforcement and d-link themselves can access your data.
REPLY ON YOUTUBE
Ive found a few TP link routers with hardcoded, non public SSH creds.. Apparently its for their app.
REPLY ON YOUTUBE
Take it offline, put it on a Vlan, config yiur firewall and 98% of the risk is gone.
REPLY ON YOUTUBE
If you put your NAS online, you only have yourself to blame. Plenty of alternatives like Talescale, ZeroTier, CloudFlare Tunnels etc
REPLY ON YOUTUBE
Wow. D-Link should be sued.
REPLY ON YOUTUBE
Just one more reason to build DIY nas
REPLY ON YOUTUBE
You wanna piss off QNAP user? Show him D-Link NAS boot time. 😀 (30 sec)
REPLY ON YOUTUBE
Hey!
I know this isnt about ugreen, so sorry about that..
They posted this as power consumption on kickstarter:
“DXP8800 Pro: Standby 125.95W, Full load 206.84W.
DXP2800: Standby 51.29W, Full load 73.96W
DXP4800: Standby 73.138W, Full load 103.73W
DXP4800 Plus: Standby 51.437W, Full load 111.5W”
This seems ridiculous, can you confirm this? Or maybe get more info out of them? They are quite slow on kickstarter
Thanks and greetings 🙂
REPLY ON YOUTUBE
I’m upset that Dlink ever used hard-coded passwords, especially poor-quality passwords.
REPLY ON YOUTUBE
I do have an 340L which I found very cheap on a local 2nd hand store. I was thinking of using it to give some purpose to some HDDs I have laying around the house.. The problem is that it doesn’t do samba v2/3 and now this exploit… Alt F is also not available for this model which is unfortunate as the hardware is good enough to maintain a simple storage service
REPLY ON YOUTUBE
Yet another reason to DIY a NAS and BYO-OS : artificial end of life imposition on perfectly functional hardware!
REPLY ON YOUTUBE
The device can be connected to the internet, it just needs to be not accessible from the outside. Which is something you should not risk anyways.
REPLY ON YOUTUBE
I think my very first NAS was a D-link, the DNS-320. That brought back memories ????
REPLY ON YOUTUBE
Anyone familiar with D-Link already know their products should be thrown away once the warranty is over. D-Link are well known for making the sale, following the legal minimum for warranty, and then abandoning their own products to the detriment of their own customers who don’t know any better. This is every D-Link product they have ever made. There are NO exceptions. Expect this if you buy anything from D-Link.
REPLY ON YOUTUBE
Something similar happened to the WD NAS I used to use. One day there were news about some vulnerability that allowed bad actors to do all kinds of nasty crap. WD never updated the firmware but instead told you to make sure it wasn’t connected to the internet. I think they had some kind of replacement program but I never used it as I already had the NAS on a separate network not connected to the internet.
Still copied all the files and discarded the NAS.
Thing is there are so many to the users unknown dangers in the OS used on these. With say True NAS you are still able to keep the OS updated with fixes and so on, but with a WD, D-Link or a lot of other NAS solutions you are stuck with what the manufacturer hands out. Sure some can be hacked by the user, but the majority doesn’t have the knowledge of how to do that.
REPLY ON YOUTUBE
Probably team who made software for D-Link NAS are long time gone. I’m did not expect anything more from D-Link which is not NAS manufacturer. Choose new products carefully 🙂
REPLY ON YOUTUBE
I have one of those and honestly I’m not surprised… I disconnected mine a long time ago. The best thing was really the price and the fact you can access it… everything else was quite poor!
REPLY ON YOUTUBE
I have one of those and honestly I’m not surprised… I disconnected mine a long time ago. The best thing was really the price and the fact you can access it… everything else was quite poor!
REPLY ON YOUTUBE
A D-Link NAS?!?
REPLY ON YOUTUBE
Useless old news!
Unless you TRULY know what you are doing and have proper firewall, intrusion detection, IP Block lists and fully updated devices and OS:
DO NOT put ANYTHING on the Internet!
REPLY ON YOUTUBE
The age old advice as always: friends don’t let friends buy D-Link. I knew they were crappy from day one dealing with their god awful wireless network cards and routers that crash weekly for no rhyme and reason.
REPLY ON YOUTUBE
Sometimes these backdoors are the only way to put openwrt on a router. It can be a good thing.
REPLY ON YOUTUBE
Sometimes these backdoors are the only way to put openwrt on a router. It can be a good thing.
REPLY ON YOUTUBE
It’s negligence, nobody in their right mind would leave a backdoor in a production system with internet connectivity, any fool can see it’s a massive risk, and they would have known that. They are responsible, they just need somebody competent to go into the firmware, take out this account and recompile the firmware, that’s going to take a few hours at most. As said their reputation is on the line, I wouldn’t trust Dlink if they didn’t fix this, and quickly. Otherwise the internet might have another 92000 DoS bots.
REPLY ON YOUTUBE
It’s negligence, nobody in their right mind would leave a backdoor in a production system with internet connectivity, any fool can see it’s a massive risk, and they would have known that. They are responsible, they just need somebody competent to go into the firmware, take out this account and recompile the firmware, that’s going to take a few hours at most. As said their reputation is on the line, I wouldn’t trust Dlink if they didn’t fix this, and quickly. Otherwise the internet might have another 92000 DoS bots.
REPLY ON YOUTUBE
Cool
REPLY ON YOUTUBE
Cool
REPLY ON YOUTUBE
No one should use cheap NAS’es. Just use synology or build own NAS with True NAS OS.
REPLY ON YOUTUBE
No one should use cheap NAS’es. Just use synology or build own NAS with True NAS OS.
REPLY ON YOUTUBE
I would never ever in a million years allow a NAS to be forward facing to the internet, if I was going to do it I would be behind a router VPN .
PS , I don’t trust QNAP’s or Synology’s you can access your files through us .
REPLY ON YOUTUBE
Regardless of the EOL, there shouldn’t be any hardcoded auth mechanic. It should never have been there in the first place. I also agree that they should be publishing the warning through their platform branding or at least owning the mistake of doing a code audit on their equipment and looking for hard coded credentials that could be exploited in the future.
REPLY ON YOUTUBE
also new issue QNAP warns of critical auth bypass flaw in its NAS devices
REPLY ON YOUTUBE
Why all the fear mongering , I run a D-Link 323, yeah it has crappy security it is only SMB 1.0 capable. It works great as an anonymous download server. It’s behind my firewall and if I lose 4tb. They didn’t get my main server so reset and carry on
REPLY ON YOUTUBE
While I have 2 newer QNap nas , i do have 3 old Dlink. How do I disconnect from internet ? If I unplug network cable I will not be able to access in my local inTRAnet. Is there a way to only allow local access ? I only use any of my nas locally.
REPLY ON YOUTUBE
This is very bad, so what they are no longer making them, there is still truckloads of them out there. In a home environment mostly there is no one ‘managing’ these things, most people treat them as plug and play, if there is any problems the manufacturers will update them.
No normal home user will check their website to see if there is anything they should know about, the NAS will just sit there until it’s either updated to something bigger/faster, or if the owner is happy, until it dies. So basically they’ll be running for many years afterwards.
REPLY ON YOUTUBE
Is amazing how often these things are found.
REPLY ON YOUTUBE
Because the Company stop making a Device and call it EOL … Doesn’t mean it no longer does the Job !! ppl have Devices that they use day to day that you can no longer Buy !! ..
REPLY ON YOUTUBE
You could install ALT-F firmware
REPLY ON YOUTUBE