Be Regularly Updated on Security Concerns with Synology & QNAP NAS
Recently there has been a spotlight on some NAS brands and their security and protection from attacks by hackers and online intruders. In some cases, this has been down to holes being found in the system software or system protocol over time that, if left unpatched can lead to Ransomware like the QNAP QLocker of 2021, the Synology Synolocker of 2014. Typically, these can stem from many methods but ultimately revolve around hackers boarding the latest firmware and finding loopholes/backdoors within the system software each time it has an official update. This is not unusual and practically ALL the computer software-related services and hardware in your home/business environment go through this – most updates to the firmware in everything from your phone to your TV, router, console and more are specifically designed to close these newly found chinks in the armour. It is a constant game of cat and mouse, however, in almost all cases the vulnerability in software (that led to your system being penetrated) will be down to the fact your device has not been updated in firmware/software in a considerable length of time.
Why Do People Not Update Their QNAP or Synology NAS System Software Immediately?
Of course, updating the firmware on your NAS every single time a new system software version is released is not quite as simple as that. Sure, the actually ACT of updating is super easy and the NAS system will constantly remind you of updates in your system firmware or individual app software – but many still do not immediately action this update. This is by no means exclusive to NAS either, with many, MANY users choosing to ignore the windows update icon at the bottom right of the screen right now, or the recommended system update restart/remind option at the top right on a Mac. There are several reasons that people do not immediately update their firmware, such as:
- The system is currently in use and there is no time right now to allow a restart, as well as having current projects/tabs/services operational
- You once/twice experienced an update on a NAS (or really any device that has regular updates) that made the system unable to perform to the previous standard (software feature changed/removed), so you had to perform a complicated firmware roll-back/downgrade and it left you less keen on immediately firmware actions
- It is a major firmware update that changes the system GUI and system options notable, so you do not wish to action a software update that will increase the learning curve
- (less common but certainly happens) Your NAS system is part of a wider network of systems (part of a CMS) that either cannot or is not recommended to be individually updated without updating every other system at the same time
So, it is all fair and well for me to say ‘you should always update’, but the truth is that many have rather valid/understandable reasons for not actioning these straight away. Of course, the alternative would be for brands to automatically FORCE system updates through, or restrict an app/system able to connect with online services until the update is installed (as found with gaming services like Playstation Network and XBox Live) – but in a NAS, or even desktop/computer/phone-based systems these options would be INCREDIBLY UNPOPULAR! So, that is how we reached the current state of affairs between the NAS Brands, their system updates, individual app updates and how/when users choose to action them. So, how do we resolve this?
| How to Remove QSnatch from your QNAP NAS | Protecting Your Synology NAS from Ransomware |
| [youtube https://www.youtube.com/watch?v=qoFnhVGPXDM] | [youtube https://www.youtube.com/watch?v=DUwUnyr9Om8] |
| What is QNAP QLocker? | How to Remove QLocker from your QNAP NAS |
| [youtube https://www.youtube.com/watch?v=cQjOn5Hc7Jg] | [youtube https://www.youtube.com/watch?v=aq_cIdY_ksQ] |
How Can You Stay On Top Of NAS Updates and Be Aware of Vulnerabilities on your NAS?
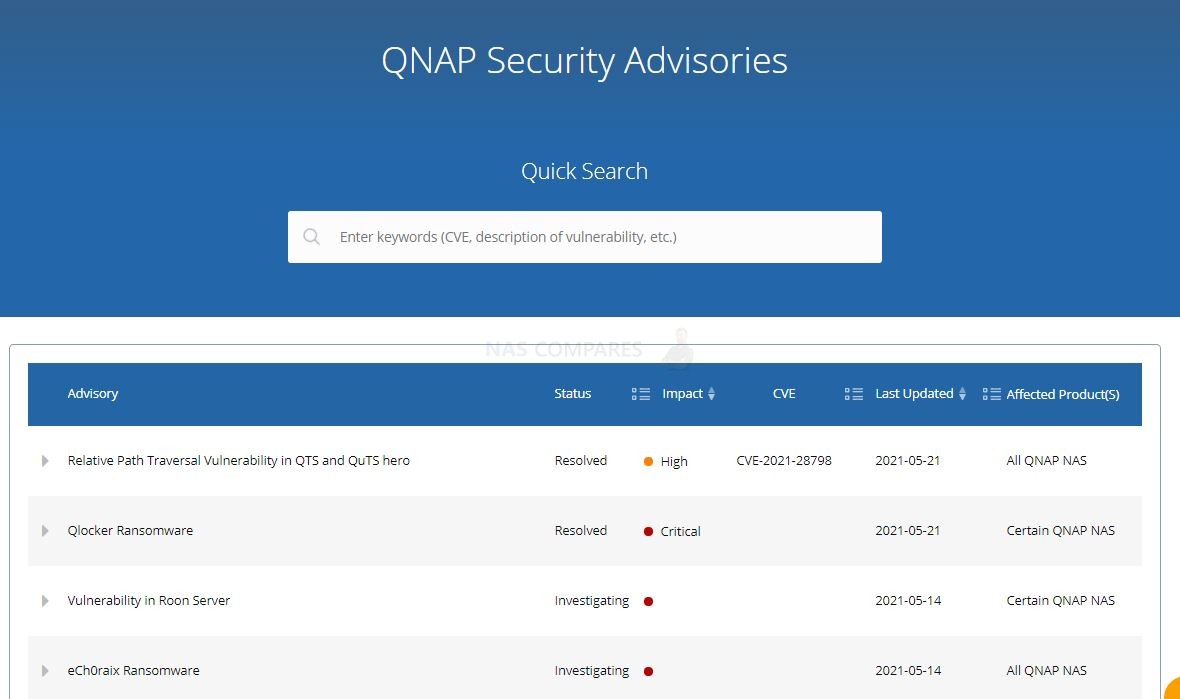
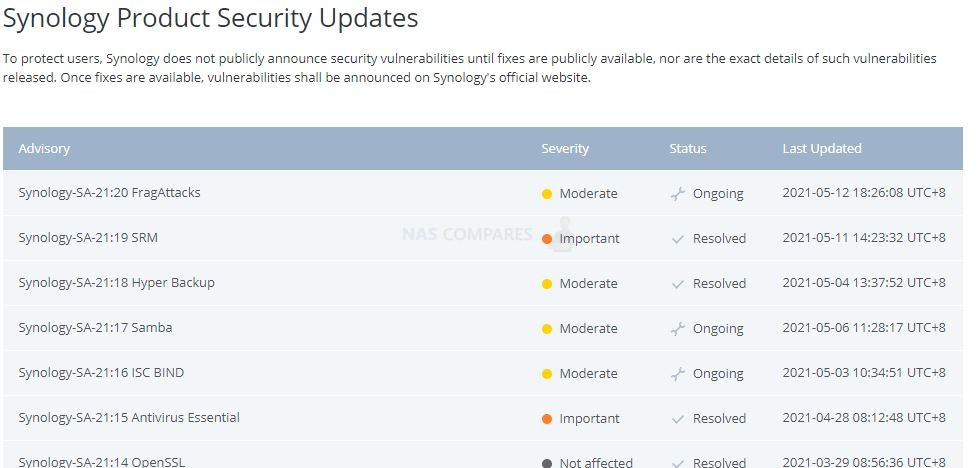
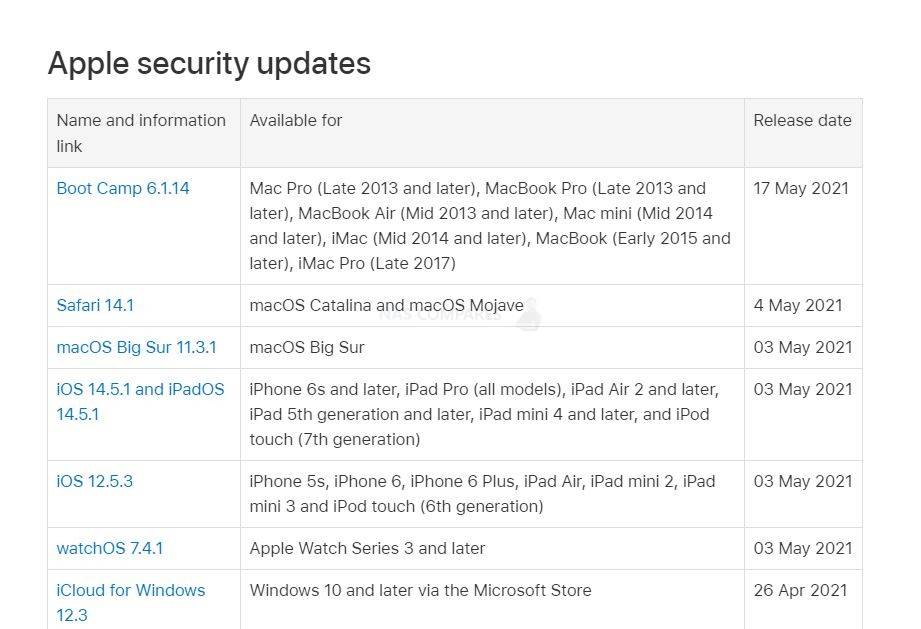
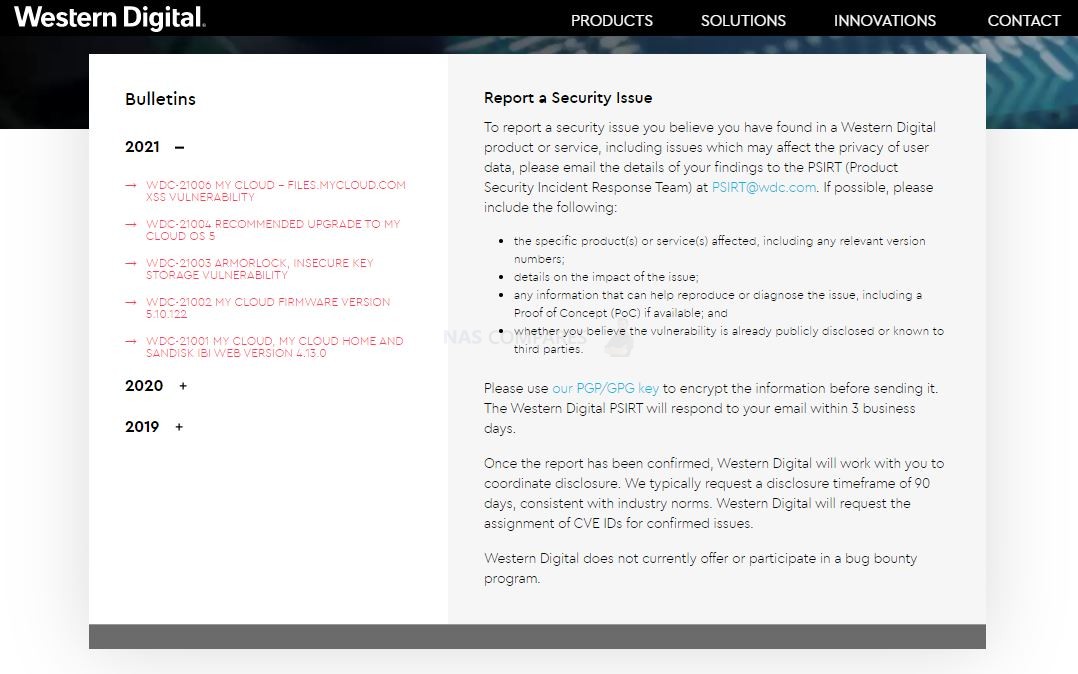
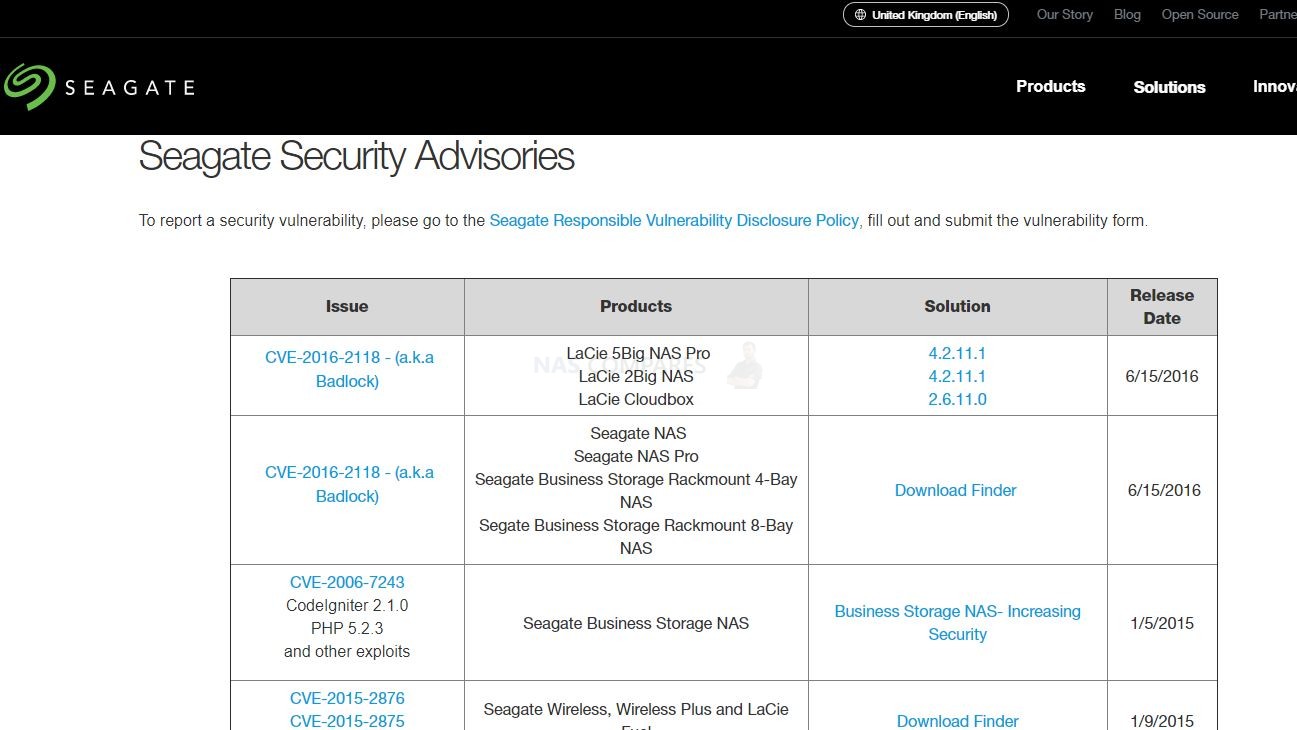
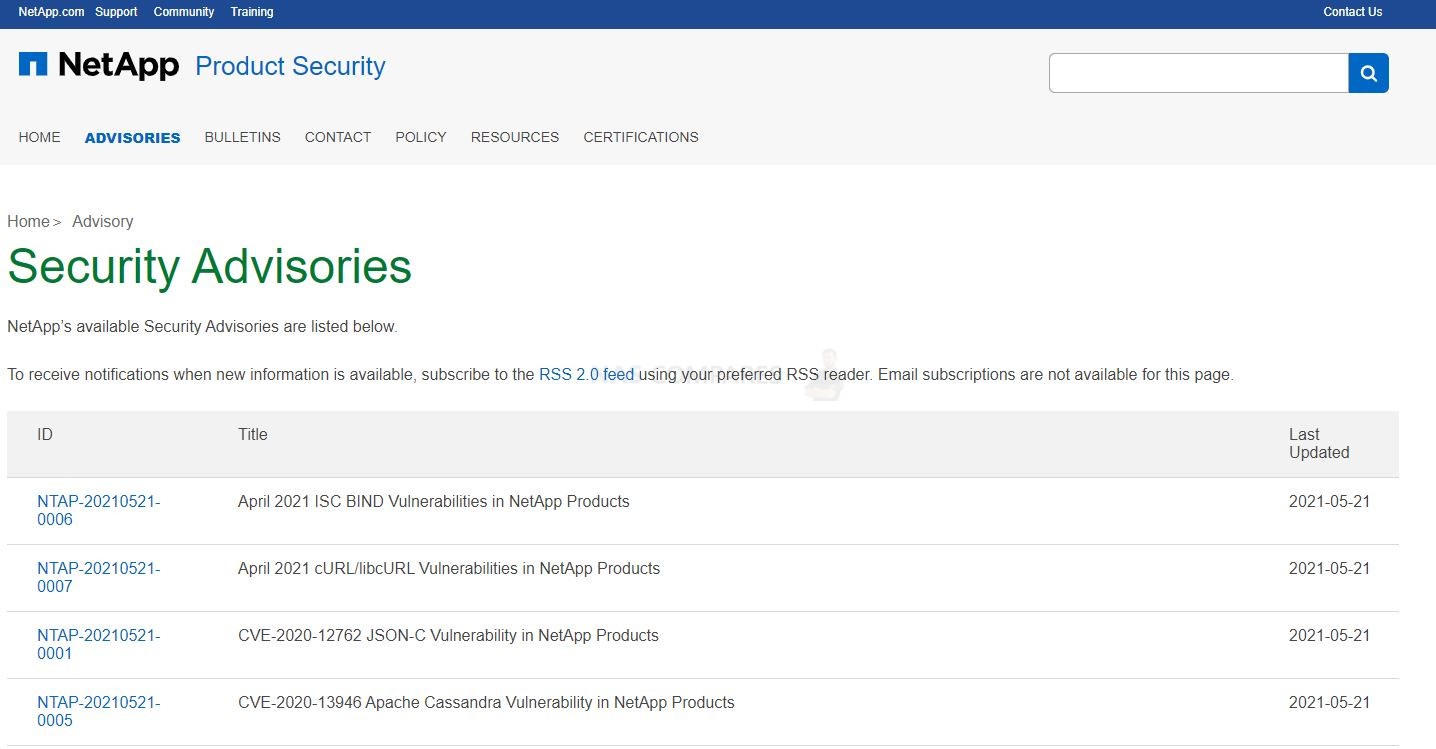
Many users might not be aware, but the majority of NAS brands (and indeed this extends to enterprise service providers like NetApp, cloud storage like Google Drive and large blob type storage like AWS and Azure) have an online portal that, known as the Security Advisory, that details the latest vulnerabilities, issues, faults and issues that are raised on their respective platforms. These are then available for public view (as they are submitted) and their effect, danger, current investigated status, date of the resolution and recommended action are then displayed. See Below:
These pages are almost certainly a legal requirement as part of their term of service and due diligence, not just a kind and wholesome gesture. However, it can be INCREDIBLY INTIMIDATING to read through them – even a 5-minute glance will make you question how on earth you have not been hacked yet! However, many of these vulnerabilities are exceptionally small and are built on exceptionally outdated firmware (perhaps 2-3 years overdue), require exceptionally weak security settings in place, DMZ network settings or simply are specific to a particular tool being used in a certain way. Nevertheless, many users will see these listings of issues and go one of two ways. One, they IMMEDIATELY UPDATE EVERYTHING and regularly update as soon as updates appear (regardless of the reasons against it listed earlier). Two, they look at the vulnerabilities, scroll through, see that none of them appear to be applicable to their own network hardware/storage setup and then continue to not-update until something more specific to their setup appears. There are pros and cons to either action of course, but better to have all the facts and listed vulnerabilities at your disposal than to proceed on just hunches and guesses!
How to Automatically Get Updated When Synology and QNAP NAS Vulnerabilities are Reported
Pretty much ALL of the brands in NAS, Data Storage and Cloud services have these security advisory pages, but the idea of checking these pages manually (i.e. bookmark etc) every day, week or month is too much of a hassle for many. On the other hand, they all arrive with an RSS feed link that allows users to subscribe to updates BUT many users are not even aware of how to apply an RSS feed (it’s a complex XML feed of text that needs to be injected into an appropriate RSS feed client/agent – so yeah, hardly noob friendly). So, in order to make this 1000x easier, I have (and by me, I mean Eddie the Web Guy spent time on it and I made this article!) made this page that will be constantly updated with the latest vulnerabilities reported on the popular NAS brands and storage-related manufacturers. It is still being built (so more brands are being added) but it will allow you to just chuck your email address below (will not be used for profit or spamming etc) and then you will get an alter EVERY TIME a new security vulnerability is updated by the brands (this is automated, so it will appear here as soon as it appears on the respective security advisory page). Additionally, there will be links back to the brand/manufacturer site so you can find out more about individual exploits and vulnerabilities, how they work, what they do and (most importantly) give you a better idea of whether you should update your NAS/Storage system or not. I hope you find it helpful and if you have any recommendations or idea of what we should add to this page/service to make it even better – let us know in the comments or directing here – https://nascompares.com/contact-us
Sign Up Below to Get Updates as New Vulnerabilities Are Reported
Get an alert every time something gets added to this specific article!

QNAP NAS Current Vulnerabilities and Exploits [OPEN 🔗]
Cross-Site Request Forgery in Proxy Server Thu, 26 May 2022 LinkCross-Site Request Forgery in Proxy Server Multiple Vulnerabilities in OpenSSL Mon, 23 May 2022 Link
Multiple Vulnerabilities in OpenSSL in QVR Fri, 06 May 2022 Link
in QVR Path Traversal in thttpd Fri, 06 May 2022 Link
Path Traversal in thttpd Multiple Vulnerabilities in Video Station Fri, 06 May 2022 Link
Multiple Vulnerabilities in Video Station in Photo Station Fri, 06 May 2022 Link
in Photo Station Multiple Vulnerabilities in QTS, QuTS hero, and QuTScloud Fri, 06 May 2022 Link
Multiple Vulnerabilities in QTS, QuTS hero, and QuTScloud Multiple Vulnerabilities in Netatalk Mon, 25 Apr 2022 Link
Multiple Vulnerabilities in Netatalk Multiple Vulnerabilities in Apache HTTP Server Wed, 20 Apr 2022 Link
Multiple Vulnerabilities in Apache HTTP Server Multiple Vulnerabilities in ISC BIND Tue, 19 Apr 2022 Link
Multiple Vulnerabilities in ISC BIND Remote Code Execution in Apache Struts Mon, 18 Apr 2022 Link
Remote Code Execution in Apache Struts Infinite Loop in OpenSSL Tue, 29 Mar 2022 Link
Infinite Loop in OpenSSL Local Privilege Escalation in Linux (Dirty Pipe) Mon, 14 Mar 2022 Link
Local Privilege Escalation in Linux (Dirty Pipe) XSS Vulnerabilities in Proxy Server Fri, 25 Feb 2022 Link
XSS Vulnerabilities in Proxy Server Improper Authentication in Kazoo Server Fri, 11 Feb 2022 Link
Improper Authentication in Kazoo Server Multiple Vulnerabilities in Samba Thu, 10 Feb 2022 Link
Multiple Vulnerabilities in Samba DEADBOLT Ransomware Wed, 02 Feb 2022 Link
DEADBOLT Ransomware in QTS Thu, 13 Jan 2022 Link
in QTS Stack Overflow in QVR Elite, QVR Pro, and QVR Guard Thu, 13 Jan 2022 Link
Stack Overflow in QVR Elite, QVR Pro, and QVR Guard XSS and Open Redirect Vulnerabilities in QcalAgent Thu, 13 Jan 2022 Link
XSS and Open Redirect Vulnerabilities in QcalAgent
SYNOLOGY NAS Current Vulnerabilities and Exploits [OPEN 🔗]
Synology-SA-22:08 ISC BIND Not affected Resolved 2022-05-20 11:36:27 UTC+8Synology-SA-22:07 Synology Calendar Moderate Resolved 2022-05-17 14:18:27 UTC+8
Synology-SA-22:06 Netatalk Critical Ongoing 2022-05-24 14:38:28 UTC+8
Synology-SA-22:05 Spring4Shell Not affected Resolved 2022-04-06 16:04:22 UTC+8
Synology-SA-22:04 OpenSSL Moderate Ongoing 2022-04-11 10:19:19 UTC+8
Synology-SA-22:03 DSM Important Resolved 2022-03-02 08:33:43 UTC+8
Synology-SA-22:02 Samba Important Resolved 2022-04-15 18:38:33 UTC+8
Synology-SA-22:01 DSM Moderate Ongoing 2022-04-12 10:54:22 UTC+8
Synology-SA-21:30 Log4Shell Not affected Resolved 2022-01-04 18:20:28 UTC+8
Synology-SA-21:29 Samba Important Ongoing 2022-03-23 16:13:26 UTC+8
Synology-SA-21:28 Mail Station Important Resolved 2022-04-12 10:52:43 UTC+8
Synology-SA-21:27 ISC BIND Moderate Ongoing 2021-11-01 18:33:53 UTC+8
Synology-SA-21:26 Photo Station Important Resolved 2021-09-07 10:03:01 UTC+8
Synology-SA-21:25 DSM Moderate Ongoing 2021-09-29 17:24:02 UTC+8
Synology-SA-21:24 OpenSSL Important Ongoing 2021-09-29 17:22:50 UTC+8
Synology-SA-21:23 ISC BIND Not affected Resolved 2021-08-20 10:43:23 UTC+8
Synology-SA-21:22 DSM Important Ongoing 2022-05-18 09:34:35 UTC+8
Synology-SA-21:21 Audio Station Important Resolved 2021-06-16 16:05:29 UTC+8
Synology-SA-21:20 FragAttacks Moderate Accepted 2021-05-12 18:26:08 UTC+8
Synology-SA-21:19 SRM Important Resolved 2021-05-11 14:23:32 UTC+8

ASUSTOR NAS Vulnerabilities and Exploits [OPEN 🔗]
04 27 2022 ASUS RT-AX88U firmware update
04 26 2022 ScreenXpert Security Update for ASUS laptops
04 01 2022 Security Advisory update for Cyclops Blink
03 29 2022 Software update for the ASUS Control Center
03 25 2022 Security Advisory for Cyclops Blink
03 10 2022 Elevation of Privilege by ASUS System Diagnosis service of MyASUS
01 14 2022 ASUS Mini PC BIOS Security Update
12 17 2021 ASUS Response to Apache Log4j Remote Code Execution Vulnerability
12 06 2021 ASUS routers security updates (2021 Q4)
10 15 2021 ASUS SMM Privilege Security Update (CVE-2021-42055) for ASUS Laptops Vulnerability: CVE-2021-42055
05 24 2021 Security advisory for FragAttack
03 29 2021 ASUS ASMB8-iKVM and ASMB9-iKVM Firmware Security Update for ASUS Server Products
03 24 2021 ASUS SMM Privilege Security Update (CVE-2021-26943) for ASUS SKL Notebook PCs
03 09 2021 Security advisory for DNSpooq
07 10 2020 ASUS ScreenPad 2 Upgrade Tool Security Update (CVE-2020-15009) for ASUS PCs with ScreenPad 1.0 (UX450FDX, UX550GDX and UX550GEX)
04 14 2020 ASUS Update Regarding Mitigation for Known Intel CPU Vulnerabilities
04 09 2020 ASUS Device Activation Security Update (CVE-2020-10649) for ASUS Notebook PCs
03 18 2020 Security Advisory for CVE-2019-15126 (Kr00k)
03 09 2020 Security Notice for CVE-2018-18287
02 14 2020 ROG Gaming Center Package Security Update
11 26 2019 New firmware update for wireless router RT-AC1750_B1 RT-AC1900 RT-AC1900P RT-AC1900U RT-AC86U RT-AC2900 RT-AC3100 RT-AC3200 RT-AC51U RT-AC51U+ RT-AC52U B1 RT-AC66U RT-AC66U B1 RT-AC66U_WHITE RT-AC67U RT-AC68P RT-AC68R RT-AC68RF RT-AC68RW RT-AC68U RT-AC68U 2 Pack RT-AC68U_WHITE RT-AC68W RT-AC750 RT-AC87R RT-AC87U RT-AC87W RT-N66U RT-N66U_C1 RT-N14U
11 15 2019 Important information about ASUSWRT security:
10 21 2019 ATK Package Security Update (CVE-2019-19235) for ASUS Notebook PCs
06 14 2019 BIOS Update Announcement for ASUS Notebook PCs
05 16 2019 New firmware update for wireless router RT-AC1750_B1 RT-AC1900 RT-AC1900P RT-AC1900U RT-AC2900 RT-AC3100 RT-AC3200 RT-AC51U RT-AC5300 RT-AC56S RT-AC56U RT-AC66U RT-AC66U B1 RT-AC66U_WHITE RT-AC67U RT-AC68P RT-AC68R RT-AC68RF RT-AC68RW RT-AC68U RT-AC68U 2 Pack RT-AC68U_WHITE RT-AC68W RT-AC750 RT-AC86U RT-AC87R RT-AC87U RT-AC87W RT-AC88U RT-N18U RT-N66U RT-N66U_C1
05 02 2019 Latest software announcement for ZenFone devices
08 14 2018 Security advisory for OpenVPN server
08 07 2018 Latest software announcement for ZenFone ZenPad devices
06 08 2018 Security advisory for VPNFilter malware
04 03 2018 Security Vulnerability Notice (CVE-2018-5999, CVE-2018-6000) for ASUS routers
10 31 2017 Update on security advisory for the vulnerability of WPA2 protocol
10 18 2017 Security advisory for the vulnerabilities of WPA2 protocol
2022 & 8711;
2021 & 8711;
2020 & 8711;
2019 & 8711;
2018 & 8711;
2017 & 8711;
2016 & 8711;
Work In Progress – More Security Advisory Updates and Reports Coming Soon for Other Brands
📧 SUBSCRIBE TO OUR NEWSLETTER 🔔
🔒 Join Inner Circle
Get an alert every time something gets added to this specific article!
This description contains links to Amazon. These links will take you to some of the products mentioned in today's content. As an Amazon Associate, I earn from qualifying purchases. Visit the NASCompares Deal Finder to find the best place to buy this device in your region, based on Service, Support and Reputation - Just Search for your NAS Drive in the Box Below
Need Advice on Data Storage from an Expert?
Finally, for free advice about your setup, just leave a message in the comments below here at NASCompares.com and we will get back to you. Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.
Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.

|
 |
Terramaster F4 SSD NAS - Should You Buy? (Short Review)
Minisforum N5 Pro NAS Review - Did Minisforum just WIN at NAS?
What Can You ACTUALLY DO with HDMI on Your NAS?
Best NAS for under $499
Best NAS for Under $250 (2025)
Minisforum N5 Pro NAS - FIRST IMPRESSIONS
Access content via Patreon or KO-FI











Hello sir .. recently (3 weeks ago) I brought home the QNAP TS-673A NAS. It is my first. I am a musician, looking for a less complicated, faster data throughput option mainly to avoid the audio sample libraries’ often AGONIZINGLY slow loading times. (The ‘less-complicated’ meaning that, I don’t want a setup like my current – every USB port on my laptop taken, including the Thunderbolt4 port acting as a “super-fast 3.1 Gen2 interface” to a StarTech Gen2 hub, with 4 short Gen2 cables out to portable WD Gen2 drives…) YES, it’s a nightmarish mess, but gets me the speed I want. But when I update the Kontakt library database for example, I need to scan 5 folders on 5 separate drives – instead of just 1, which I hope to achieve, and with similar speed, in my new QNAP setup.
This would be up and running a few weeks ago, but I am busy touring with the band I play with this summer and seldom home on weekends. But in my research about QNAP NAS’s (including, thankfully, many of your fine contributions here on YT) .. it didn’t take long at all to learn of the security exploits and dreaded RW attacks. So my ‘rush’ to setup this NAS – turned into something not so rushed at all. One alternative, according to a review of my same product on Amazon, indicates the fellow used something called “TrueNAS Scale” – a freeware, open-source OS he claims to be much more secure than what QNAP offers, but what others say is incredibly complex and non-user-friendly.
So right now, I sit on a day off with the NAS plugged in (not powered on) populated with 1 WD “Gold” Enterprise 8 TB drive, along with 4 WD “Red Plus” NAS 8 TB drives, ready for a RAID 5 configuration. My laptop’s Thunderbolt 4 port is connected to one of the NAS’s USB faster ports (not the slower USB-C which you rightfully ridiculed in your TS-873A review). The ‘Power’ button has not been pushed yet. I have a network connection ready for a cloud install when I finally turn it on, and I have your 2022 QNAP NAS Setup Guide series of 6? videos all cued up and ready to follow with precision. So I guess my only question is: IS IT SAFE, on this day, TO DO THE STANDARD QNAP QuTS “hero” install??? Or should I try the alternative TrueNAS Scale install, for which there are a few walkthrough videos I could follow as well? I’m leaning toward QNAP … but only if it is safe. Answers from anyone well-experienced NAS’ers are welcome too. Thanks you sir, and keep up the great work you do!
REPLY ON YOUTUBE
The best person to contact is #GLOCYBER ON INSTAGRAM he got all the ideas on each of the virus extension. He was able to repair mine.
REPLY ON YOUTUBE
It has been a week when I got infected but today I saw a comment that recommended me to #GLOCYBER ON INSTAGRAM and he was able to open all my files.
REPLY ON YOUTUBE
My MacBook was affected and I had no option than to contact #GLOCYBER on instagram. He did helped me recover all my files.
REPLY ON YOUTUBE
I suggest you should all contact #GLOCYBER ON INSTAGRAM. He was able to help me fix my computer.
REPLY ON YOUTUBE
My company system was infected too. We all couldn’t use our computers because it spreads to everyone computer. Our manager has explained that he hire #GLOCYBER ON INSTAGRAM and he was able to fix it. At least, we could have our jobs again.
REPLY ON YOUTUBE
My mums computer was infected and she asked me to help her. Although I don’t know how to fix it so I contacted #GLOCYBER ON INSTAGRAM and he helped us. He charged us a bit but it was very affordable. Thanks to him.
REPLY ON YOUTUBE
I got infected too. It was annoying seeing your computer but can’t use it. I did asked my technician and he suggest I should contact #GLOCYBER ON INSTAGRAM. I did contact him and he was able to help me out.
REPLY ON YOUTUBE
Am a photographer and it affected all my clients files and pictures. It affects my animal documentation pics. I almost cried, then I make my research and found out that #GLOCYBER ON INSTAGRAM has been helping out. He did mine and thanks to him.
REPLY ON YOUTUBE
Thanks to #GLOCYBER ON INSTAGRAM. He was able to fix my computer and all my files are normal.
REPLY ON YOUTUBE
My NAS was attacked by the virus but I was able to reach out to #GLOCYBER on INSTAGRAM and he could figure it out.
REPLY ON YOUTUBE
I got affected by the division of the virus. And I could not read for my exam because it encrypted all my lectures note. Thanks to my lecturer who recommended #GLOCYBER ON INSTAGRAM to help me recover my files. He did and am so happy.
REPLY ON YOUTUBE
Am a student too and it lock all my pdf and everything other thing in my laptop. Am so happy I got help from #GLOCYBER ON INSTAGRAM. He did a marvelous work and now I have all my files back.
REPLY ON YOUTUBE
I recommend you all to contact #GLOCYBER ON INSTAGRAM. He was able to help me recover all my encrypted files. Am glad I met him earlier.
REPLY ON YOUTUBE
I was dead in need of my computer. But I could not all because of this virus. I was recommended to #GLOCYBER on instagram and he responded to me and helped me fix my laptop.
REPLY ON YOUTUBE
Am able to contact #GLOCYBER on INSTAGRAM and I showed him what has happened to my computer. He was able to assist and get my computer free from the virus.
REPLY ON YOUTUBE
I was affected too and I talked to #GLOCYBER ON INSTAGRAM . he could help and he did recover all my files and photo.
REPLY ON YOUTUBE
It was through the help of #GLOCYBER on instagram that we ware able to get our money photos decrypt. The virus has held all the pics in the system.
REPLY ON YOUTUBE
It was #GLOCYBER on instagram that was able to help me fix all my files and get them decrypt. He really did a great work and am happy I met him.
REPLY ON YOUTUBE
I found a legit cyber professional. He is #GLOCYBER on instagram. he was able to help me fix and decrypt all my encrypted files. Thanks to him for his kindness.
REPLY ON YOUTUBE
Contacting #GLOCYBER on instagram was the best thing I did after my files got infected. He quickly decrypt all my files and get me free from the virus.
REPLY ON YOUTUBE
This virus has been attached to my files for more than a week. It was my dad who directed me to #GLOCYBER on instagram and he was able to get rid of the virus. Thanks to him.
REPLY ON YOUTUBE
my files have been encrypted and I thought I would never use them again. My lecturer told me to reach #GLOCYBER on instagram and he was able to help me recover my files from the virus. Thanks to him.
REPLY ON YOUTUBE
Contacting #GLOCYBER on instagram was the best thing I did after my files got infected. He quickly decrypt all my files and get me free from the virus.
REPLY ON YOUTUBE
Am happy I could contact #GLOCYBER on instagram and he was able to help me remove all the virus. My exams files are free now.
REPLY ON YOUTUBE
My computer was affected too and it got stuck of all the virus. Thanks to my sister who had recommended #GLOCYBER on instagram. I search him on google and he responded to me. Thanks to him.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
*I was hit, so unplugged, shutdown, external USB backs fine. Plex user, was watching at the time no issues, went to update saver denied, then found the splash screen, no on reboot, water gapped on an independent switch no WiFi etc, it instantly goes to initialization. So save to assume the service themselves have been affected. Did safe shutdown. After some time I turn on everything then I found out I’ve been truly hit by deadbolt. I did as many research as I could and I found out that scott can actually decrypt the encrypted files So I paid some money not upto what deadbolt team are asking, then he decrypted my files*
REPLY ON YOUTUBE
*I was hit, so unplugged, shutdown, external USB backs fine. Plex user, was watching at the time no issues, went to update saver denied, then found the splash screen, no on reboot, water gapped on an independent switch no WiFi etc, it instantly goes to initialization. So save to assume the service themselves have been affected. Did safe shutdown. After some time I turn on everything then I found out I’ve been truly hit by deadbolt. I did as many research as I could and I found out that scott can actually decrypt the encrypted files So I paid some money not upto what deadbolt team are asking, then he decrypted my files*
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
…You can message *SCOTTS_HACK*
REPLY ON YOUTUBE
…You can message *SCOTTS_HACK*
REPLY ON YOUTUBE
????I was so glad when I finally realized and get in touch with Glo Cyber while I used the contact above. He is indeed a genius and his skill are authentic. I rec. everyone to appreciate his efforts.
REPLY ON YOUTUBE
People keep talking about Scott. I think he is good. I will try him.
REPLY ON YOUTUBE
Someone recommended you ????and you also helped me recover mine too. You a genius indeed
REPLY ON YOUTUBE
Someone recommended you ????and you also helped me recover mine too. You a genius indeed
REPLY ON YOUTUBE
You’re ???? such a genius, I really appreciate your services, fast and safe recovery process.
REPLY ON YOUTUBE
Just come here because my NAS has been compromised! I’m so annoyed and this has been a major blow for my business (video production company).
REPLY ON YOUTUBE
People should know about this this is madness, just happenned to me? 8 months later?? Could they have warned their F*ing customers??!!
REPLY ON YOUTUBE
i was infectet now on 7 dec 21
REPLY ON YOUTUBE
I don’t use my over the cloud I only use it with my local network. Is it safe that way ?
REPLY ON YOUTUBE
The little graphics was very helpful. I learned my lesson for sure on what having a backup actually means.
I naively bought my NAS thinking it would be my own little personal cloud machine and sole backup (thinking raid would keep me safe forever) for my documents, photos, and videos.
Now I realize I’m going to still have to spend more money on cloud services and be very careful with my qnap nas.
I was immediately thinking of switching to Synology since you said it’s more user friendly and all I really use my NAS for is backup and as a cloud drive to put my files into it and be able to retrieve them on my phone. Unfortunately, from what I’ve seen on the appstore the other Nas company apps look like they are just as rough, slow, and confusing to use as Qnap’s (Qmanager and Qfile). I don’t understand how “downloads” and “Qsync” works on Qfile for example so I’ve been just moving files manually as I would on any other cloud app.
For now I’m staying with my TS-453D.
But still have mixed feelings about it.
REPLY ON YOUTUBE
So I got stung by the Qlocker ransom ware attack and apparently it was caused by a back door issue relating one of the apps, hybrid desk station? I can’t recall I was too busy fuming at how a company could have this vulnerability. And I do appreciate the support the qnap staff have tried to give in recovering the files and data, but when the process broke down and they let communication fade, with lack of support to get a resolution I soon lost patients with them and decided to let go of some files. I thankfully did have back ups but when your sync does the backing up it basically just had a knock on effect so ran some files where synced to pc, and a back up hard drive before I had noticed. Thankfully larger files where left and they only went after the smaller file sizes.
Anyway long story short, always back up your data manually on an off line hard drive. This is the only real way you can secure a true back up of your files. Thankfully an old NAS gave that option to me.
REPLY ON YOUTUBE