In today’s digital world, network-attached storage (NAS) devices like Synology have become essential for home and business users alike. These devices store everything from personal photos and files to essential business data, making them a prime target for cyber threats. Recently, several zero-day vulnerabilities in Synology NAS products were discovered, posing significant risks for users if not addressed promptly. This article breaks down these vulnerabilities and provides actionable steps to help you secure your Synology NAS and keep your data safe.
Understanding the Recent Synology NAS Vulnerabilities
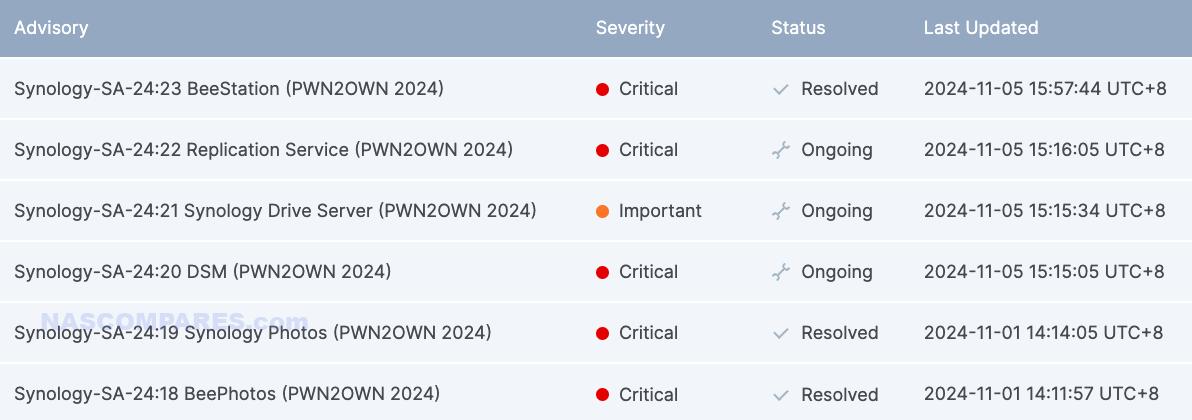
A zero-day vulnerability refers to a security flaw that is exploited before the vendor has a chance to release a fix. Hackers can take advantage of these vulnerabilities to gain unauthorized access, install ransomware, or steal data. Synology’s recent vulnerabilities affect a variety of popular applications and services, including Synology Photos, Replication Service, Drive Server, and the DiskStation Manager (DSM) operating system. Here’s a closer look at the risks in each of these areas:
1. Synology Photos Vulnerability
Synology Photos is widely used to store and share photos. The recent vulnerability exposed a zero-day attack vector, meaning that hackers could access your Synology Photos files if the device was accessible online through open ports. Hackers could potentially inject malicious code, encrypt files, or steal sensitive images.
Solution: To protect your data, update Synology Photos to the latest version, and avoid exposing it to the internet via open ports. Instead, use a VPN for secure remote access.
2. Replication Service Risks
The Replication Service feature in Synology NAS allows users to create backup snapshots on remote devices, adding an extra layer of data redundancy. However, vulnerabilities in this service can create entry points for attackers if ports are left open or the NAS is directly accessible over the internet. If exploited, an attacker could intercept data during replication, potentially leading to data theft or tampering.
Solution: Ensure you’re using the latest DSM update, which includes a patch for replication service vulnerabilities. For enhanced security, use a VPN or other secure method instead of open ports for replication tasks.
3. Synology Drive Server Vulnerabilities
Synology Drive serves as an alternative to services like Dropbox, providing synchronization and backup for files across multiple devices. A recent flaw in Drive Server may allow hackers to hijack active sessions or inject SQL code, especially when the NAS device is exposed to the internet. While this vulnerability is marked as less severe, it still poses risks in shared networks where unauthorized access could compromise session integrity.
Solution: Keep Synology Drive updated, and avoid leaving it directly accessible on the web. Protect your network with secure configurations and antivirus software to minimize exposure.
4. DSM Operating System (DiskStation Manager) Weaknesses
The DSM operating system is at the core of every Synology NAS. Vulnerabilities in DSM (especially versions 7.1 and earlier) leave NAS devices open to zero-day exploits. If hackers discover an open port on your device, they can launch attacks to encrypt, steal, or manipulate your data.
Solution: Synology has released patches for DSM 7.2 to address these issues. Update to DSM 7.2 if possible, and apply the latest patches as soon as they’re available. To protect DSM, avoid open ports and always use VPNs or firewalls.
Steps to Secure Your Synology NAS
With these vulnerabilities in mind, here are the best practices for securing your Synology NAS and protecting it from future threats:
1. Use a VPN for Remote Access
- Instead of exposing your NAS to the internet with open ports, use a VPN service like Tailscale to create a secure private network. This method will keep your NAS hidden from external scans and prevent unauthorized access.
2. Enable Firewalls and Restrict IP Access
- Configure your NAS firewall to only allow access from specific IP addresses. You can also set up regional restrictions to only allow connections from your country, adding an extra layer of protection.
3. Change Default Ports and Update Regularly
- Changing the default ports for services can deter hackers who rely on scanning common ports. Also, keep your DSM, Synology apps, and all NAS software up-to-date, as patches are released to fix vulnerabilities.
4. Secure Synology QuickConnect
- QuickConnect allows remote access to your NAS without a VPN but can be a vulnerability. Use a complex, unique username to make unauthorized access harder. Avoid using any dictionary words in your QuickConnect ID.
5. Monitor for Suspicious Activity
- Enable activity logs on your Synology NAS to monitor who’s accessing it and from where. Regularly review these logs for any suspicious IP addresses or login attempts.
What’s Next? Staying Vigilant Against Zero-Day Vulnerabilities
Zero-day vulnerabilities are a constant risk, especially with internet-connected devices. While vendors like Synology work hard to release patches quickly, there’s always a window of opportunity for hackers. To stay ahead of these threats, make cybersecurity a regular part of your routine by keeping all software updated, using VPNs, and configuring network settings securely.
Final Thoughts
Your Synology NAS is a powerful tool, but like any connected device, it requires proper security measures to stay safe. By following these best practices, you can protect your NAS from unauthorized access and minimize the risks posed by zero-day vulnerabilities. If you’re unsure about any of the steps, Synology’s support and resources are available to help guide you through setting up a secure configuration.
Stay proactive and secure—because with data security, it’s always better to be safe than sorry.
| Where to Buy a Product | |||
|
|
    
|

|
VISIT RETAILER ➤ |
 |
    
|

|
VISIT RETAILER ➤ |
 |
    
|

|
VISIT RETAILER ➤ |
 |
    
|

|
VISIT RETAILER ➤ |
We use affiliate links on the blog allowing NAScompares information and advice service to be free of charge to you. Anything you purchase on the day you click on our links will generate a small commission which is used to run the website. Here is a link for Amazon and B&H. You can also get me a ☕ Ko-fi or old school Paypal. Thanks! To find out more about how to support this advice service check HERE
The Best Bits (and Worst Bits) of NAS of 2025!
Minisforum MS-02 Ultra Review
Minisforum N5 NAS, 6 Months Later - Better, Worse, the Same?
Beelink ME Pro NAS Revealed
Best SOLID STORAGE NAS of 2025
Should You Worry About the NanoKVM Hidden Microphone?
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.






So I think I know but have to ask anyway. If I have a firewall on my router with all inbound ports closed and the firewall turned on within the NAS with all inbound ports closed and all remote access turned off, am I safe from these zero days attacks? My 5-bay Synology NAS is so old that I can’t upgrade to 7.x.x. Thanks in advance. Waiting for the 1524 or 1525 to come out.
Yes, if there is nothing you access from outside the home like Plex, Photos, DSM etc. You can have all those ports closed on the firewall. Even if there is a hole in one of those app, hackers can not execute attack with no access to the NAS. I would set up firewall to block every connection and only allow LAN access using your local IP range.
As an owner of a DS1815+, I’m feeling left high & dry on security updates. I didn’t need 8 bays when I bought it in March 2017, but plumped for this device thinking that I was future proofing myself rather than considering the risk of all updates being turned off in the future (and unaware of the DS1817+ coming out the following month). I know Synology have great software, and charge a premium for that. As a (perhaps naive) consumer, I never thought about my “future proofed” hardware and software becoming unsupported 6 years later.
I can see extended EOL support ended 1 Oct 2024, and here’s a bunch of critical vulnerabilities found 3 weeks later…. Poor timing
You’re right to feel frustrated, especially given that you invested in a premium product like the DS1815+ with the intention of future-proofing your setup. While Synology excels in software and usability, their decision to sunset support for older models highlights the challenge of balancing hardware longevity with evolving security demands.
Critical vulnerabilities surfacing so soon after EOL support is indeed poorly timed and underscores the risks of relying on an unsupported system. It might be worth considering migrating to a newer Synology NAS (like the DS1823+), which carries similar expandability while benefiting from modern hardware and security updates for years to come. Alternatively, you could mitigate short-term risks by isolating the DS1815+ from external networks and using it solely within a secure LAN until you decide on a replacement.
When you start reading a post and starts with: “In today´s digital world….” we all know what it means…