
Cybersecurity continues to be a major concern as we spend more and more time on the internet. You’ll want to keep your data secure whether you’re at work, at home, or using public WiFi. With so many VPN services to choose from, how can you settle on the best one for you? Do you really […]
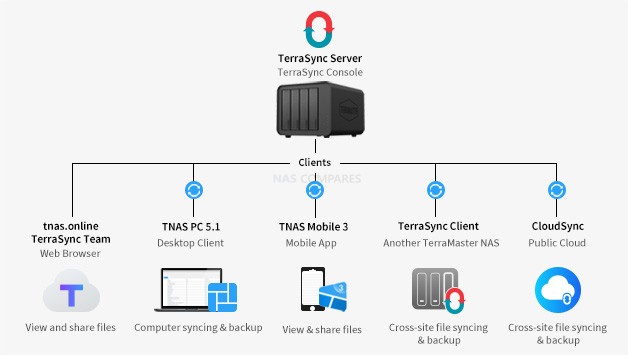
TerraMaster Launches TerraSync, a Backup Solution to Turn Your TNAS into a Private Cloud Server, Achieve File Synchronization Between Multiple Devices TerraMaster, a professional brand dedicated to providing innovative storage products for homes and businesses, recently released TerraSync, a backup solution which runs on TNAS and works with TerraSync Client. With the TerrSync application, users […]

Subheading: Introducing the F2-424 with Intel Celeron N95 Processor, 8GB DDR5 Memory, and Blazing-Fast 2.5G Ethernet TerraMaster, a leading provider of innovative storage solutions, has announced the release of its latest 2-bay NAS, the F2-424. Tailored for the needs of Geeks and Small Office/Home Office (SOHO) users, this high-performance NAS delivers exceptional speed, reliability, […]

How to prevent hackers from stealing your data via smart devices like smart light bulbs, sockets, smart speakers, android HDMI TV dongles, and cheap android tablets and phones. Here is a vulnerabilities discovered yesterday: CVE-2023-38906 An issue in TPLink Smart bulb Tapo series L530 v.1.0.0 and Tapo Application v.2.8.14 allows a remote attacker to obtain […]

Exciting news for all security surveillance enthusiasts! The QVP-63B QVR Pro dedicated machine has just been released, and it is a game-changer in the world of surveillance technology. This desktop security surveillance server provides real-time image and audio surveillance, high-quality video recording, and simultaneous playback of multiple IP cameras. One of the standout features of […]

QNAP, a leading provider of storage, networking, and computing solutions, has announced the launch of its QNAP Security Vulnerability Reward Program. The program aims to actively protect information security and ensure network security by inviting global information security experts and researchers to participate in creating a more secure network environment and storage services. The QNAP […]

Introduction Brief overview of VPN technology VPN (Virtual Private Network) technology allows users to securely access the internet by encrypting their internet connection and routing it through a remote server. This creates a virtual “tunnel” between the user and the internet, effectively hiding the user’s internet activity and location. VPNs are commonly used by individuals […]






