A History Lesson on NAS Security Incidents – STAY SAFE!
As someone who has long relied on Network Attached Storage (NAS) devices for both personal and professional use, I’ve come to appreciate the convenience and functionality they offer. These devices provide a centralized and easily accessible repository for my important data, making them indispensable tools in my digital life. However, with this convenience comes a significant risk: the ever-present threat of cyberattacks. Over the past 15 years, we’ve seen numerous high-profile security incidents targeting NAS devices, underscoring the vulnerabilities inherent in these systems.
In this article, I want to take a closer look at some of the most significant security breaches that have impacted NAS devices from major brands like QNAP, Synology, Asustor, Terramaster, Western Digital, Netgear, and Buffalo. I’ll delve into each incident, exploring the specific vulnerabilities that were exploited, the methods used by attackers, and the devastating impacts on users and organizations. To make this information more accessible, I’ll provide user-friendly explanations that demystify the technical details, helping even those without a technical background understand how these attacks were carried out. Beyond recounting these incidents, I aim to identify commonalities among the attacks, highlighting recurring themes and valuable lessons we can all learn from. Finally, I’ll offer comprehensive recommendations on settings, setup options, and security measures that we can implement to protect our NAS devices from similar threats. By understanding these past incidents and adopting proactive security measures, we can better safeguard our valuable data and ensure the integrity of our NAS systems against future cyber threats.
Which NAS Security Settings Should You Focus On (TL;DR)?
Enhance your NAS device’s security by keeping firmware updated, using strong passwords, enabling multi-factor authentication, disabling unnecessary services, and using VPNs. Implement firewalls, IP access control, and regularly monitor logs. Ensure backups, use antivirus software, encrypt connections, set user permissions, and disable default admin accounts. Employ auto block for failed logins, utilize security scanning apps, limit client access with tools like Tailscale, disable SSH when not in use, and disable unused network protocols.
| Setting to Change | What It Prevents |
|---|---|
| Update Firmware Regularly | Prevents exploitation of known vulnerabilities. |
| Use Strong, Unique Passwords | Prevents brute-force attacks and unauthorized access. |
| Enable Multi-Factor Authentication (MFA) | Adds an extra layer of security to prevent unauthorized access even if passwords are compromised. |
| Disable Unnecessary Services | Reduces potential entry points for attackers. |
| Enable Firewall | Blocks unauthorized access and potential attacks from the internet. |
| Use a Virtual Private Network (VPN) | Ensures secure remote access to your NAS, preventing exposure to the internet. |
| Implement IP Access Control | Restricts access to trusted IP addresses only. |
| Disable UPnP (Universal Plug and Play) | Prevents automatic opening of ports which could be exploited by attackers. |
| Regularly Backup Data | Ensures data recovery in case of ransomware attacks or data loss. |
| Monitor NAS Logs | Helps detect suspicious activities early. |
| Enable Antivirus and Anti-Malware Protection | Protects against malware and other malicious software. |
| Use Encrypted Connections (HTTPS/FTPS) | Ensures data is securely transmitted, preventing interception. |
| Set Up User Permissions | Limits access to sensitive data to authorized users only. |
| Disable Default Admin Account | Prevents attackers from exploiting known default credentials. |
| Enable Intrusion Detection/Prevention Systems (IDS/IPS) | Helps identify and block potential threats. |
| Enable Auto Block for Failed Login Attempts | Prevents brute-force attacks by temporarily blocking IP addresses after multiple failed login attempts. |
| Use Security Scanning Apps Provided by NAS Brands | Identifies and addresses vulnerabilities and misconfigurations. |
| Use Apps Like Tailscale to Limit Client Access | Restricts access to a limited number of authenticated clients, enhancing security. |
| Disable SSH Access When Not Needed | Prevents unauthorized remote access to the NAS. |
| Disable Unused Network Protocols (FTP, SMB, etc.) | Reduces potential attack surfaces by limiting unnecessary network services. |
By implementing these suggested security measures, you can greatly enhance the protection of your NAS device against various cyber threats.
1. QNAP NAS Devices and QLocker Ransomware (2021)
- Vulnerability: Exploited the SQL injection vulnerability in QNAP Photo Station.
- CVE: CVE-2020-36195
- Vulnerability Explained: A SQL injection vulnerability occurs when an attacker can insert or “inject” malicious SQL code into a query through an input field or parameter. In the case of QNAP’s Photo Station, the application didn’t properly sanitize user inputs, allowing attackers to manipulate database queries. This manipulation gave attackers unauthorized access to the NAS system. They used this access to execute commands that should have been restricted, effectively bypassing normal authentication controls. This type of vulnerability is particularly dangerous because it can provide attackers with full control over the database and, by extension, potentially the entire system.
- Exploitation: Attackers exploited a SQL injection vulnerability in the Photo Station app to gain unauthorized access and used 7-Zip to encrypt files.
- User-Friendly Explanation: Imagine you have a house with a poorly designed lock on one of the windows (the Photo Station app). The attackers found this weak spot and used a special tool (SQL injection) to open the window and sneak inside. Once inside, they didn’t steal anything right away. Instead, they put all your valuable items into strong, locked boxes (using 7-Zip to encrypt the files) and took the keys with them. Now, you can’t access any of your valuables unless you pay them to get the keys back (paying the ransom). They demanded the payment in Bitcoin, which is like asking for payment in an untraceable form of digital cash.
- Brand Impacted: QNAP
- Impact: Thousands of QNAP NAS devices were affected, with users unable to access their files unless they paid the ransom in Bitcoin. Reports indicate that over 1,000 devices were infected within the first few days of the attack. The total financial impact on users was significant, as the ransom demands ranged from $200 to $1,200 per device. The attack caused widespread disruption, with many users losing access to critical data.
- Resolution: QNAP released security updates to patch the vulnerabilities and provided instructions for mitigating the attack.
- Link: QNAP Security Advisory
- Link: Official QNAP Response and Suggestions for Mitigation
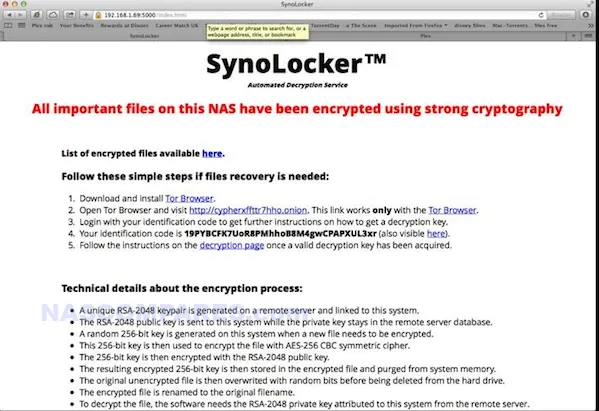
2. Synology NAS Devices and SynoLocker Ransomware (2014)
- Vulnerability: Targeted vulnerabilities in DSM software, particularly outdated firmware and weak passwords.
- CVE: Not specified.
- Vulnerability Explained: The vulnerabilities in Synology’s DiskStation Manager (DSM) software were primarily due to outdated firmware and weak passwords. Outdated firmware often contains known security flaws that have been patched in later versions, but if not updated, these flaws remain exploitable. Weak passwords are easily guessed or cracked using brute-force attacks, where attackers systematically try all possible password combinations until the correct one is found. These vulnerabilities made it relatively easy for attackers to gain unauthorized access to Synology NAS devices, especially those that were not properly secured.
- Exploitation: Attackers used brute-force methods and exploited known vulnerabilities in outdated DSM software to encrypt files and demand ransom.
- User-Friendly Explanation: Think of your NAS as a safe in your home. The attackers used two main strategies to break in. First, they used brute-force attacks, which is like trying millions of different combinations on the safe’s lock (password) until it opens. Second, they exploited known vulnerabilities in the DSM software, similar to using a master key that fits because of a flaw in the safe’s design (old software bugs). Once they got in, they didn’t steal anything outright. Instead, they locked everything inside the safe with their own lock and told you that you need to pay them (ransom) to get the new combination to open it.
- Brand Impacted: Synology
- Impact: Thousands of Synology NAS devices were encrypted, causing significant disruption and data loss. The attack highlighted the importance of updating firmware and using strong, unique passwords. Users reported substantial financial losses and operational downtime, with ransom demands typically around $350 to $400 in Bitcoin. This attack prompted many users to reevaluate their security practices and invest in better protection measures.
- Resolution: Synology released security updates and tools to help users check their systems and advised on strengthening security settings.
- Link: Synology Security Advisory
- Link: Official Synology Response and Suggestions for Mitigation
3. QNAP, Asustor, and Terramaster NAS Devices and DeadBolt Ransomware (2022)
- Vulnerability: Targeted unspecified vulnerabilities in NAS firmware.
- CVE: Not specified.
- Vulnerability Explained: The exact vulnerabilities exploited by DeadBolt ransomware were not publicly disclosed, but they likely involved flaws in the NAS firmware or application software that allowed unauthorized access. Such vulnerabilities can include weak authentication mechanisms, unpatched software bugs, or misconfigurations that leave the system exposed to external attacks. These types of vulnerabilities can be exploited to gain administrative access, allowing attackers to execute arbitrary commands, including deploying ransomware.
- Exploitation: Attackers exploited vulnerabilities in the NAS firmware to gain unauthorized access and encrypt users’ files.
- User-Friendly Explanation: Picture your NAS as a highly secure filing cabinet. The attackers discovered secret weaknesses (unspecified vulnerabilities) in the cabinet’s lock system that weren’t known to the public. They exploited these weaknesses to sneak into the cabinet. Once inside, they didn’t take the documents but instead locked them in new folders with padlocks and took the keys with them. Now, if you want to access your documents, you need to pay the attackers to get the keys to these new padlocks. The ransom was typically requested in Bitcoin, a form of digital currency that is hard to trace.
- Brands Impacted: QNAP, Asustor, Terramaster
- Impact: Significant number of NAS users across these brands found their files encrypted and were unable to access them without paying the ransom. The DeadBolt ransomware was particularly widespread, affecting thousands of devices globally. Reports indicated that over 3,600 QNAP devices alone were compromised. The financial impact was substantial, with ransom demands often exceeding $1,000 per device. This attack caused major disruptions for both personal and business users, highlighting the critical need for robust security measures and regular updates.
- Resolution: QNAP, Asustor, and Terramaster released firmware updates and provided steps for users to secure their devices. They also advised users to disconnect their NAS from the internet when not in use and to implement strong security practices.
- Links: Our Article on ‘Are NAS Drives Safe?‘ which covers each incident in more detail + video links
4. WD My Book Live Devices Wiped by Exploit (2021)
- Vulnerability: Remote command execution vulnerability in My Book Live firmware.
- CVE: CVE-2018-18472
- Vulnerability Explained: Remote command execution vulnerabilities allow attackers to run arbitrary commands on a device from a remote location. This specific vulnerability (CVE-2018-18472) was due to a flaw in the My Book Live firmware that allowed unauthorized users to send commands to the device over the internet. These commands could be used to perform actions such as factory resetting the device, deleting all stored data. Such vulnerabilities are critical because they provide full control over the device to the attacker without requiring physical access.
- Exploitation: Attackers exploited the vulnerability to perform remote factory resets, wiping data from the devices.
- User-Friendly Explanation: Imagine your NAS is like a digital storage box that holds all your important files. The attackers found an old flaw (CVE-2018-18472) that allowed them to send a command from far away (remote command execution) telling the box to reset itself to the way it was when it was brand new. This reset deleted all the data stored inside, similar to wiping everything off a computer when you restore it to factory settings. Because of this command, all your files were erased, causing significant distress and data loss.
- Brand Impacted: Western Digital
- Impact: Thousands of users reported complete data loss, causing significant distress. The attack was widespread, affecting users globally. Estimates suggest that tens of thousands of devices were potentially vulnerable, with a significant portion being affected. The total impact included not only the loss of personal and business data but also the trust in the security of Western Digital products.
- Resolution: Western Digital advised users to disconnect devices from the internet and offered data recovery services and discounts on newer products.
- Link: Western Digital Advisory
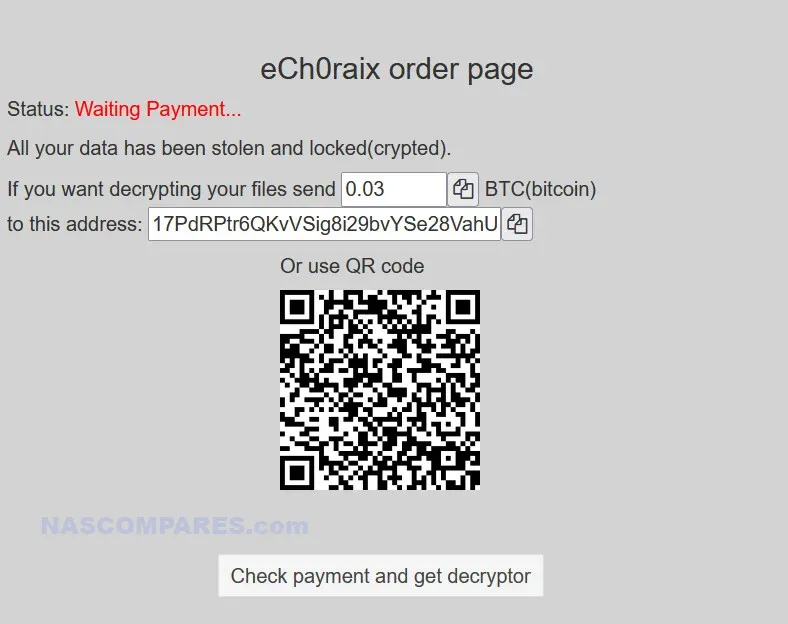
5. QNAP NAS Devices and eCh0raix Ransomware (2019)
- Vulnerability: Exploited weak passwords and vulnerabilities in QNAP firmware.
- CVE: CVE-2019-7192, CVE-2019-7193
- Vulnerability Explained: The eCh0raix ransomware exploited two primary vulnerabilities in QNAP devices: weak passwords and specific software flaws. CVE-2019-7192 and CVE-2019-7193 were vulnerabilities that allowed attackers to bypass authentication and gain administrative access to the NAS. Weak passwords compounded the issue by making it easier for attackers to perform brute-force attacks, systematically guessing passwords until they found the correct one. Once inside, the attackers could deploy ransomware to encrypt files.
- Exploitation: The ransomware used brute-force attacks and exploited known firmware vulnerabilities to encrypt files and demand ransom.
- User-Friendly Explanation: Imagine your NAS as a secure vault. The attackers used two main methods to get in. First, they used brute-force attacks, which is like trying every possible combination to guess the password of your vault (weak passwords). Second, they took advantage of known software bugs (CVE-2019-7192 and CVE-2019-7193) that had not been fixed, similar to using a skeleton key that works because of a design flaw. Once inside, they locked all your files with their own locks and demanded money (ransom) to provide the keys to unlock them.
- Brand Impacted: QNAP
- Impact: Many QNAP NAS users found their files encrypted, leading to operational downtime and data accessibility issues. The attack impacted thousands of users worldwide, with ransom demands typically around $600 to $1,000 in Bitcoin. The financial burden on users and businesses was significant, as many had to pay the ransom or face permanent data loss. The attack highlighted the need for better password practices and timely software updates.
- Resolution: QNAP released firmware updates, advised on using strong passwords, enabling two-factor authentication, and updating systems.
- Link: QNAP Security Advisory
6. Synology NAS Devices and Bitcoin Miner Malware
- Vulnerability: Exploited outdated DSM software.
- CVE: CVE-2013-6955
- Vulnerability Explained: The vulnerability in Synology’s DSM software (CVE-2013-6955) allowed attackers to gain unauthorized access to the NAS devices. This specific flaw was related to inadequate input validation, which let attackers run arbitrary commands on the device. The attackers exploited this to install cryptocurrency mining software, which used the device’s resources to mine Bitcoin. This kind of malware doesn’t steal data but hijacks the system’s processing power, leading to reduced performance and potential hardware damage due to overheating.
- Exploitation: Attackers installed cryptocurrency mining malware on devices, utilizing system resources for Bitcoin mining.
- User-Friendly Explanation: Think of your NAS as a computer that runs software to manage files. The attackers found an old software bug (CVE-2013-6955) that let them sneak in and install a program that forces your NAS to work extra hard, like making a computer solve complex puzzles to create digital coins called Bitcoins. This process uses a lot of the NAS’s processing power, making it slow and possibly causing it to overheat, similar to how a computer might slow down and get hot if it’s running too many programs at once.
- Brand Impacted: Synology
- Impact: Reduced performance, potential overheating, and increased electricity costs for users. The attack affected thousands of Synology devices globally. Users reported significant drops in performance, and some devices even experienced hardware failures due to the increased load and heat. The financial impact included increased electricity bills and costs associated with hardware repair or replacement.
- Resolution: Synology released updates to patch vulnerabilities, remove malware, and advised on regular updates and security monitoring.
- Link: Synology Official Post and eTeknix Article

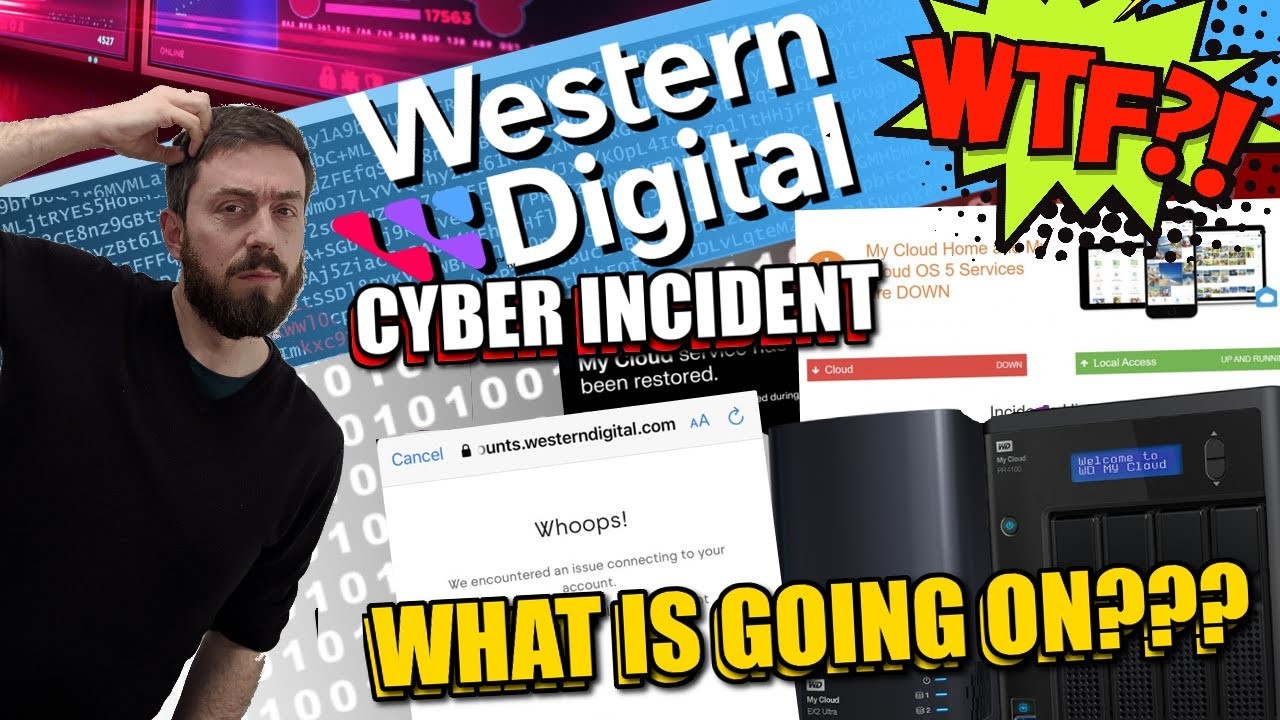
7. WD My Cloud Security Incident (2023)
- Vulnerability: Unauthorized access to Western Digital in-house servers.
- CVE: Not specified.
- Vulnerability Explained: The security incident involved an unauthorized infiltration of Western Digital’s in-house servers, which managed WD My Cloud devices. Attackers exploited a vulnerability within the server infrastructure, leading to a breach that compromised sensitive data and potentially manipulated device functions. This vulnerability was linked to insufficient security protocols and inadequate monitoring, allowing attackers to access and control server operations without authorization.
- Exploitation: Attackers infiltrated Western Digital’s servers, compromising sensitive data and potentially affecting the functionality and security of WD My Cloud devices.
- User-Friendly Explanation: Imagine the WD My Cloud as a secure vault where you keep your important files. The attackers found a way to break into the main control system of this vault (Western Digital’s servers). Once inside, they could access sensitive information and possibly control how the vault operated. This is like thieves breaking into the control room of a bank vault, gaining access to all the safes and the ability to manipulate the vault’s systems.
- Brand Impacted: Western Digital
- Impact: Compromised security, potential data breaches, and loss of user trust. The attack affected numerous WD My Cloud users globally, exposing sensitive information and causing significant inconvenience due to the disabled cloud services. Users faced operational disruptions, especially those who depended solely on remote access. The incident underscored the importance of comprehensive server security measures and the necessity for users to configure local access options as a contingency plan.
- Resolution: Western Digital implemented robust security enhancements, released patches to address the vulnerabilities, and restored cloud services once the environment was secured. They also advised users on best practices for securing their devices and data, including enabling local/LAN access to ensure uninterrupted access in case of future incidents.
- Link: Western Digital Advisory and Public Disclosure on Business Wire
(Click HERE or Below to Learn More about the WD Cyber Incident)
8. Buffalo NAS Devices and Persistent XSS Vulnerabilities (2017)
- Vulnerability: Multiple persistent XSS vulnerabilities in the web interface.
- CVE: Not specified.
- Vulnerability Explained: Cross-site scripting (XSS) vulnerabilities occur when an application allows users to inject malicious scripts into web pages viewed by others. In Buffalo NAS devices, these persistent XSS vulnerabilities allowed attackers to inject scripts into the web interface that would execute whenever an authorized user accessed the page. This could lead to unauthorized actions performed on behalf of the user, theft of session cookies, and other malicious activities. The flaws were due to inadequate input validation and sanitization in the web application.
- Exploitation: Attackers injected malicious scripts into the web interface, potentially gaining access to sensitive information.
- User-Friendly Explanation: Think of your NAS’s web interface as a control panel you access through a browser. The attackers found a way to insert malicious code (scripts) into this control panel, which would run when you or others accessed the panel. This is like someone sneaking into a control room and installing hidden cameras to watch and capture sensitive information whenever you use the controls, potentially stealing passwords, personal data, or other sensitive information.
- Brand Impacted: Buffalo
- Impact: Risk of data theft and unauthorized access, compromising device security. The vulnerabilities affected many users globally, although exact numbers were not disclosed. The primary risk was the theft of sensitive information, which could be used for further attacks or identity theft. The incident highlighted the need for better web application security in NAS devices.
- Resolution: Buffalo released firmware updates to address XSS vulnerabilities and advised users to update firmware regularly.
- Link: Buffalo Security Advisory and CVE listings
9. Netgear ReadyNAS Devices and Remote Code Execution Vulnerability (2016)
- Vulnerability: Critical remote code execution vulnerability in ReadyNAS devices.
- CVE: CVE-2016-1524
- Vulnerability Explained: Remote code execution vulnerabilities like CVE-2016-1524 allow attackers to run arbitrary code on a device from a remote location. This specific vulnerability was due to inadequate input validation and poor access control in the ReadyNAS firmware. Attackers could exploit this flaw to send specially crafted requests that would execute commands on the device without proper authorization. This level of access could be used to steal data, modify configurations, or install malware.
- Exploitation: Attackers executed arbitrary code on affected ReadyNAS devices, leading to potential data theft and system compromise.
- User-Friendly Explanation: Imagine your NAS as a secure storage unit. The attackers found a flaw (CVE-2016-1524) that allowed them to send commands to the NAS from a remote location, as if they had a remote control that could do anything. This meant they could make the NAS perform any actions they wanted, such as stealing files, changing settings, or installing harmful programs, without needing physical access to the device.
- Brand Impacted: Netgear
- Impact: Compromised security, potential data breaches, and unauthorized control over devices. The vulnerability affected a significant number of Netgear ReadyNAS devices globally. The potential for data theft and system compromise was high, leading to a considerable security risk for users.
- Resolution: Netgear released firmware updates and guidelines on securing ReadyNAS devices.
- Link: Netgear Security Advisory
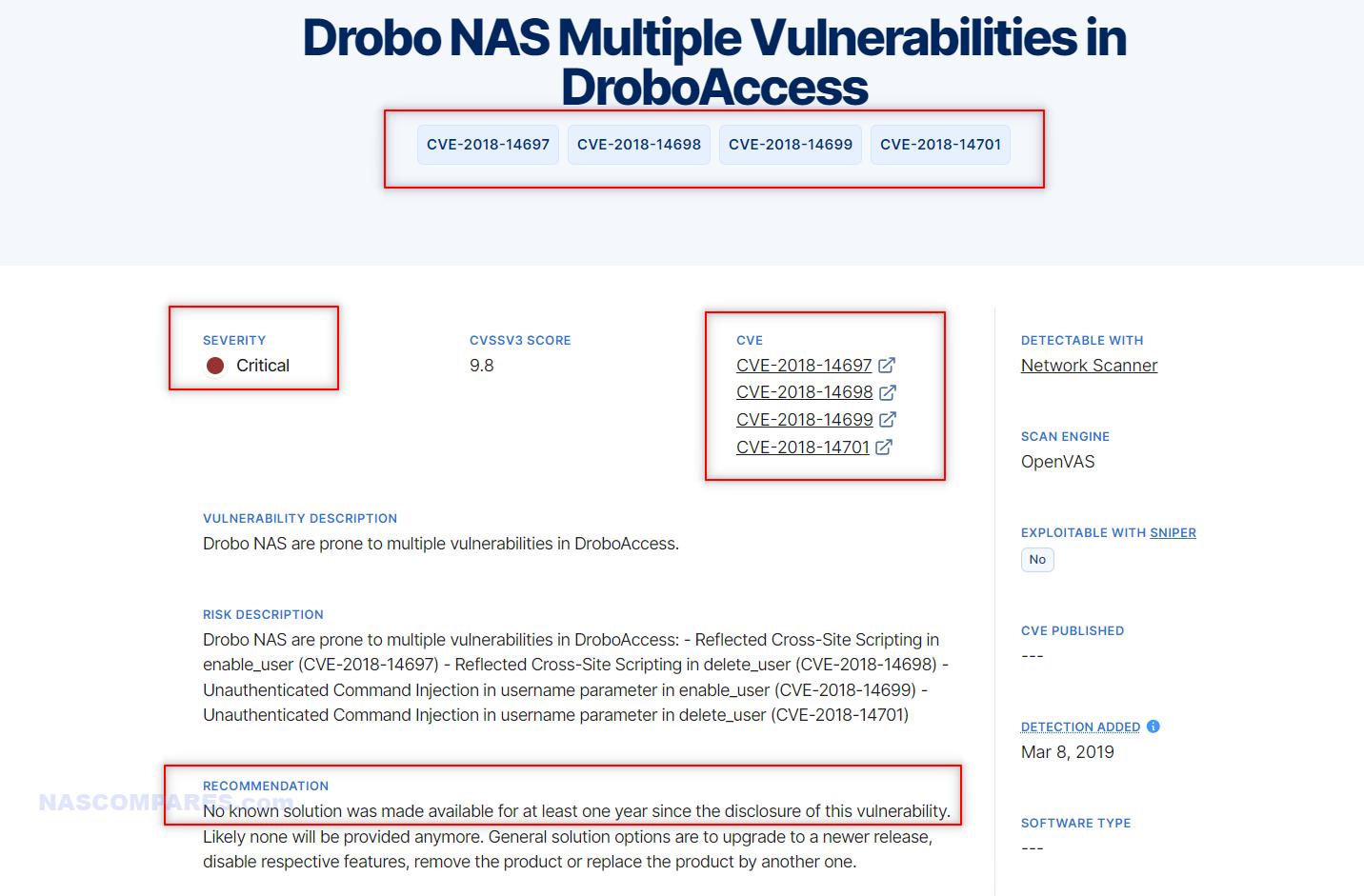
10. Drobo NAS Devices and Vulnerabilities in Web Interface (2015)
- Vulnerability: Weak authentication mechanisms and potential command injection flaws in the web interface.
- CVE: Not specified.
- Vulnerability Explained: The vulnerabilities in Drobo NAS devices’ web interface included weak authentication mechanisms and command injection flaws. Weak authentication mechanisms made it easier for attackers to bypass login protections, gaining unauthorized access. Command injection flaws allowed attackers to execute arbitrary commands on the device by injecting malicious input into web forms or URLs. These vulnerabilities were due to poor input validation and inadequate security controls in the web application.
- Exploitation: Attackers exploited these vulnerabilities to gain unauthorized access and execute malicious commands.
- User-Friendly Explanation: Think of your NAS’s web interface as the login screen to access your secure storage. The attackers discovered flaws in the authentication process, making it easier for them to bypass security checks (weak authentication mechanisms). Additionally, they found ways to send harmful commands through the interface (command injection flaws), similar to tricking the system into executing their instructions. This allowed them to gain control over the NAS and perform malicious activities, such as stealing data or damaging the system.
- Brand Impacted: Drobo
- Impact: Risk of unauthorized access, data breaches, and system compromise. The vulnerabilities affected many Drobo NAS users, putting their data at risk. The incident underscored the importance of robust web application security and strong authentication mechanisms.
- Resolution: Drobo released firmware updates to address vulnerabilities and advised on best practices for securing devices.
- Link: An article on 15 Different Drobo Vulnerabilities
What Have All of these NAS Security Incidents Have in Common?
All these NAS security incidents share several common elements. Firstly, they all involve exploiting vulnerabilities in firmware or software that was either outdated or had inherent flaws. Attackers took advantage of these weaknesses to gain unauthorized access, highlighting the critical importance of keeping firmware and software up to date. Many NAS devices were targeted because their users had not applied the latest security patches, leaving them vulnerable to known exploits. Secondly, weak or compromised authentication mechanisms were a recurring theme. Many attacks succeeded because of weak passwords, brute-force attacks, or poor authentication practices. This underscores the need for strong, unique passwords and multi-factor authentication (MFA) to provide an additional layer of security. Brute-force attacks and weak password policies allowed attackers to easily gain access to NAS devices, facilitating the deployment of ransomware, malware, or unauthorized command execution.
Lastly, the impact of these incidents was significantly exacerbated by the interconnected nature of NAS devices. Many users had their NAS devices directly connected to the internet without adequate security measures, making them easy targets for remote attacks. This highlights the importance of securing network access and employing best practices for internet-connected devices. Implementing proper firewall settings, VPNs, and avoiding unnecessary exposure to the internet can greatly reduce the risk of such attacks.
Conclusion – Lock it DOWN!
To protect your NAS from these types of attacks, it is essential to implement a robust security setup. Start by ensuring that your NAS firmware and all installed applications are always up to date. Regularly check for updates from the manufacturer and apply them as soon as they are available. These updates often include patches for known vulnerabilities that could otherwise be exploited by attackers. Strong authentication measures are also crucial. Use complex, unique passwords for your NAS device and any associated accounts. Enable multi-factor authentication (MFA) wherever possible to add an extra layer of security. MFA requires users to provide two or more verification factors to gain access, making it much harder for attackers to compromise your device even if they manage to obtain your password. Securing network access is another key aspect. Avoid exposing your NAS directly to the internet. If remote access is necessary, use a Virtual Private Network (VPN) to create a secure connection to your NAS. Configure your firewall to block unauthorized access and only allow trusted IP addresses if possible. Disabling unnecessary services and ports can also minimize potential entry points for attackers. Regularly review and update these settings to adapt to new security threats. By following these recommendations and staying vigilant about security practices, you can significantly reduce the risk of your NAS device being compromised. Regular monitoring, prompt application of updates, and robust authentication and network security measures are essential to safeguarding your data and maintaining the integrity of your NAS system.
How to Automatically Get Updated When Synology and QNAP NAS Vulnerabilities are Reported
Pretty much ALL of the brands in NAS, Data Storage and Cloud services have these security advisory pages, but the idea of checking these pages manually (i.e. bookmark etc) every day, week or month is too much of a hassle for many. On the other hand, they all arrive with an RSS feed link that allows users to subscribe to updates BUT many users are not even aware of how to apply an RSS feed (it’s a complex XML feed of text that needs to be injected into an appropriate RSS feed client/agent – so yeah, hardly noob friendly). So, in order to make this 1000x easier, I have (and by me, I mean Eddie the Web Guy spent time on it and I made this article!) made this page that will be constantly updated with the latest vulnerabilities reported on the popular NAS brands and storage-related manufacturers. It is still being built (so more brands are being added) but it will allow you to just chuck your email address below (will not be used for profit or spamming etc) and then you will get an alter EVERY TIME a new security vulnerability is updated by the brands (this is automated, so it will appear here as soon as it appears on the respective security advisory page). Additionally, there will be links back to the brand/manufacturer site so you can find out more about individual exploits and vulnerabilities, how they work, what they do and (most importantly) give you a better idea of whether you should update your NAS/Storage system or not.
Click Below to Visit the FULL Article
📧 SUBSCRIBE TO OUR NEWSLETTER 🔔🔒 Join Inner Circle
Get an alert every time something gets added to this specific article!
This description contains links to Amazon. These links will take you to some of the products mentioned in today's content. As an Amazon Associate, I earn from qualifying purchases. Visit the NASCompares Deal Finder to find the best place to buy this device in your region, based on Service, Support and Reputation - Just Search for your NAS Drive in the Box Below
Need Advice on Data Storage from an Expert?
Finally, for free advice about your setup, just leave a message in the comments below here at NASCompares.com and we will get back to you. Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.
Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.

|
 |
Gl.iNet Flint 4 10G+2.5G Router Revealed @CES 2026
EVERYTHING NEW from Minisforum @ CES 2026
Gl.iNet Slate 7 PRO Travel Router (and Beryl 7) REVEALED
Minisforum N5 MAX NAS - 16C/32T, 128GB 8000MT RAM, 5xSATA, 5x M.2, 2x10GbE and MORE
The BEST NAS of 2026.... ALREADY??? (UnifyDrive UP6)
How Much RAM Do You Need in Your NAS?
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.







One reason I don’t click on popups is because I can’t tell it’s legit or not. I assume it’s not. But I don’t know.
REPLY ON YOUTUBE
I’m not exactly a stranger to the concept of security, but I had set my qnap up for internet access without any clue it could be hacked until I started reading about how vulnerable they are to it without doing all the stuff you recommended. Part of that is because between the router and the qnap you see nothing but features you can use only to find out later that you have to disable all of those features. So from the start it’s kind of like false advertising, and you have to become an expert in security to understand what you’re supposed to do. And then DOING it becomes next to impossible. I don’t NEED external access, so I disabled it, even though I had it working, and now that I’ve learned to do all of this stuff, I can’t get it working again. I can do it if I wipe my router and start over again, but sooner or later it quits working. I was using a vpn to get into my router and send a wol signal to the qnap, but I had thought this was insecure from everything I read, only to find out that it is very secure. But now I can’t make it work for more than a day or two. The average person simply is NOT GOING TO DO ANY OF THIS. So, they shouldn’t advertise it with all of these capabilities if they aren’t going to walk you through how to make it secure, keep it secure, and make it WORK.
REPLY ON YOUTUBE
Used to manage a fleet of Readynas units. Had some issues with btrfs but overall reliable units
REPLY ON YOUTUBE
@NASCompares I need your help please.. I have a Netgear ReadyNAS Ultra 4, I havent accessed it in a few years. I recently had to reset the OS to be able to reset the password, but I cant seem to access the drive. Any idea how to access it? Im sure it doesnt have OS6, its probably much older. Anyways, I see the NAS on the network, when I click on it I get some odd error, and when I enter the IP I get a window that pops up and says no shares.. I KNOW the device has LOTS of files on it, but for the life of me I cant access them.. Any help would be greatly appreciated..
REPLY ON YOUTUBE
The hackers are probably from Apple iCloud. Annoying subscription based program from Apple that keeps popping up on my Mac and iPhone, im pretty curious to think they have something to do with that mybook attack, till this day I still store data on mybook but never connected it online, because I always been WOKE!
REPLY ON YOUTUBE
what can we do now with the old hardware ? at least save the HD but they look not compatible with Synology NAS. Advices would be appreciated: thanks
REPLY ON YOUTUBE
6:20
What about using Zerotier? No need to do port-forwarding and you can add your ReadyNAS to a private network (it’s pretty much a VPN alternative) along with your computer/phone/tablet? 25 devices can be added for the Basic/Free account.
REPLY ON YOUTUBE
No point in keeping a service active when the low user base doesn’t outweigh the costs and time to keep it up.
REPLY ON YOUTUBE
Great help! I have been using a RN104 for over 10 years with 10tb raid setup, fortunately I was mid transfer to alternate devices. Third or fourth time I have been stung by Netgear now. I’m done with non-physical storage and like others, I am absolutely done with Netgear!!
REPLY ON YOUTUBE
I have an Netgear RN31400, i cant log in at all to ready cloud anymore, found this video and can see why. We moved house and have a new internet connection etc and now have a different (LAN) how can i connect directly to pc or access my archived business files now? HELP 😉 I literally have a brick on my work desk now I have no idea how to access.
REPLY ON YOUTUBE
They lost my business!
REPLY ON YOUTUBE
Well Thank for the video. Was completely blindsided with this news 🙁
REPLY ON YOUTUBE
Hello, I have a question for several days I could not log in to my NETGEAR READYNAS 424 now I know that it could be due to the information you included in the video. But there is something even worse in a hurry I reset nasa by holding the reset button on the back and now I can’t run it boot stops on 98 % and what’s worse I’m afraid that I deleted all data. My question is, have I lost my drive forever and can it be restarted?
REPLY ON YOUTUBE
Have purchased many Netgear products over the years. For personal and a number of charities I support from an IT point of view. Often working remotely and running my own small print and design business… ReadyCloud was a solution I needed. I am very disappointed and quite annoyed by this. The lack of product post life support is frustrating to say the least. Without going off on a rant – the bottom line is that I will never support Netgear again with a purchase – personally or for any other organisations I support.
REPLY ON YOUTUBE
OMG, I work remotely for weeks at a time, I could log in a few days ago but not today. I logged in via an icon on my desktop and never saw a warning. I am dead in the water until I return to my home base next week. Most of what you talked about as workarounds is way above my pay grade ????
REPLY ON YOUTUBE
Isn’t there a possibilty to install different software on my ReadyNAS? There are plenty of freeware NAS OSes available. If i can install one of those on my ReadyNAS, at least my hardware can still be used?
REPLY ON YOUTUBE
People were buying that hardware with their software for having their own storage and remote access with sharing. That’s fraud. They fooled me too :/
REPLY ON YOUTUBE
lol, was just about to make an account
REPLY ON YOUTUBE
A sad day for my Readynas526 the cloud service has now been disconnected…..
REPLY ON YOUTUBE
Thanks for making the video, and responding so quickly to my email, I appreciate it! Y’all are awesome, and I appreciate all the advice and insight. I have decided that I am just going to ditch my Neatgear R9000 Router and NAS426, and start from scratch (now I need a video on how to properly dispose of them, lol). I’m not sure which router I will be going with, but I do think, based on your videos, that the Asustor Lockerstor 4 gen2 AS6704T will be my choice of NAS (I just wish it had the Synology interface, lol). Thanks again for responding to my email, I truly do appreciate it…
REPLY ON YOUTUBE
Another sad blow for using Cloud in conjunction with NAS. Makes it harder to trust storage that isn’t physical you own.
REPLY ON YOUTUBE
Whilst I hadn’t used it actively for quite some time, I did have it set-up for a family-member who passed away.
I did get a timely message that the service would stop, don’t recall the end-date exactly but also noticed the inaccuracies of that.
But then NG was not really that high on my radar, found them quite rough on some of their edges (pun intended)
I mainly use their switches as even though they might be old (and sometimes no longer maintained), they are okay for home-usage.
(as long as you keep in mind the security about that too!)
I predict in 5 to 10 years time, we will see more & more similar vendors making these kind of moves.
(indeed, WD will be next I predict)
Too bad as I believe the clouds are for blowing smoke (pun intended), and we should own our personal data on our own premisses with optional offsite backups. Your dependencies should only rely on what you own yourself and not rely on services from various vendors, you are in control.
My recommendation(s): do not go for the all-in-one solutions, consider vendors who are the true specialists with the focus (Synology, QNAP, Asustore etc) and backup, backup, B A C K U P!
REPLY ON YOUTUBE
I left my readyNAS rn202 (after owning since 2016) in february of this year for a Synology DS220+. Sounds like I made that move just in time. I need to access my files remotely and the ReadyNAS cloud app for mobile and in the browswer was not a proper solution for me anymore. My Synology has been a mountain of an upgrade over ReadyNAS and I have not looked back since.
REPLY ON YOUTUBE
Shocking
REPLY ON YOUTUBE
Twingate
REPLY ON YOUTUBE
I remember the same attack done at Synology, ransomware attack demanding 1.2 bitcoin, unfortunately I paid them and they gave the key and I unlocked all of my 10 years worth of files .
since then I unplugged my NAS from internet and don’t use its feature.
what synology did? they sent me $30 headphone… imagine that, I paid 1.2 bitcoin for cheap headphone.
I was considering Qnap until I find this video
REPLY ON YOUTUBE
No.
REPLY ON YOUTUBE
I have secured my QNAP and it has been safe until Saturday when I got hit by Deadbolt, but my most recent snapshot come to the rescue……the thing is that my QNAP was secured as far as I was aware…..????????????????????????????
REPLY ON YOUTUBE
I am IT consultant for 20 years and i loved to had the opportunity to watch this video. To me the thing that QnAP does not have any guilt in their product its at least a bit biased. I know people want to sell NAS and make a good chunk of commissions, its how things works i got that.
But lets face it with a great example, if you have a Tesla, are driving and the car crushes because the system does not allow you to stop, then even if there is a bug there, the brand is responsible, not the end-user for sure.
When we translate the NAS issues, well sure , the end-user needs to have a specific skill set to be able to know how to work with the technologies, but the brand does not say its it can be challenging for some people, who does not understands, a,b,c… etc…. Instead they tell you that you can have everything setup by clicking a simple button, and the more features it has the more people will activate.
I never saw a disclaimer from QNAP or any other NAS brands about what can happen if the users does not have that skillset, and even worst, they market it as a product that is top notch in technology, like having access to the nas content from everywhere. That´s where they have responsibility, i am quite sure some lawsuits will occur sooner then later.
Because they have the responsibility to explain clearly what a basic user should do and should not do…
They also should explain that someone before buying a NAS should have at least a 3-2-1 backup solution , because the NAS is not the backup solution.
I know that for many people, the NAS itself its quite expensive to buy and so many users cant afford to buy external drives for Local backups and also a cloud backup system, that is the bare minimum for whom thinks about having a NAS as home or in a SOHO
And here again i never seen QNAP explaining in a very clear way in their sale pages about their NAS products, when i am talking about QNAP, its not only QNAP , other brands do the same, but are they responsible brands by doing so? in my honest opinion nope.
Probably many small business went out business, some because ethically they don’t want to pay to criminals and others because they cant afford to pay due to the crisis that have impacted so many people worldwide.
Here i believe that QNAP should paid the ransom to solve this issue for their customers, are they obliged to? of course not, but in the other hand they would not have their image burned out and their online reputation is not good to say the least.
I have a QNAP nas devices and i am quite sure that i will never ever buy another from this brand again.
REPLY ON YOUTUBE
I think every brand should add a choice at setup that asks, what is your data classification: very private, private, public. And what is your update tier: beta, innovative, stable and secure. From that the system can make the appropriate choices.
REPLY ON YOUTUBE
Hello sir .. recently (3 weeks ago) I brought home the QNAP TS-673A NAS. It is my first. I am a musician, looking for a less complicated, faster data throughput option mainly to avoid the audio sample libraries’ often AGONIZINGLY slow loading times. (The ‘less-complicated’ meaning that, I don’t want a setup like my current – every USB port on my laptop taken, including the Thunderbolt4 port acting as a “super-fast 3.1 Gen2 interface” to a StarTech Gen2 hub, with 4 short Gen2 cables out to portable WD Gen2 drives…) YES, it’s a nightmarish mess, but gets me the speed I want. But when I update the Kontakt library database for example, I need to scan 5 folders on 5 separate drives – instead of just 1, which I hope to achieve, and with similar speed, in my new QNAP setup.
This would be up and running a few weeks ago, but I am busy touring with the band I play with this summer and seldom home on weekends. But in my research about QNAP NAS’s (including, thankfully, many of your fine contributions here on YT) .. it didn’t take long at all to learn of the security exploits and dreaded RW attacks. So my ‘rush’ to setup this NAS – turned into something not so rushed at all. One alternative, according to a review of my same product on Amazon, indicates the fellow used something called “TrueNAS Scale” – a freeware, open-source OS he claims to be much more secure than what QNAP offers, but what others say is incredibly complex and non-user-friendly.
So right now, I sit on a day off with the NAS plugged in (not powered on) populated with 1 WD “Gold” Enterprise 8 TB drive, along with 4 WD “Red Plus” NAS 8 TB drives, ready for a RAID 5 configuration. My laptop’s Thunderbolt 4 port is connected to one of the NAS’s USB faster ports (not the slower USB-C which you rightfully ridiculed in your TS-873A review). The ‘Power’ button has not been pushed yet. I have a network connection ready for a cloud install when I finally turn it on, and I have your 2022 QNAP NAS Setup Guide series of 6? videos all cued up and ready to follow with precision. So I guess my only question is: IS IT SAFE, on this day, TO DO THE STANDARD QNAP QuTS “hero” install??? Or should I try the alternative TrueNAS Scale install, for which there are a few walkthrough videos I could follow as well? I’m leaning toward QNAP … but only if it is safe. Answers from anyone well-experienced NAS’ers are welcome too. Thanks you sir, and keep up the great work you do!
REPLY ON YOUTUBE
Worker with a reliable hacker is what I think is all over the world and I recommend a hacker parfait who works with good heart and sincerity Dee_hack11 is in Seoul☝️☝️☝️.
REPLY ON YOUTUBE
The best person to contact is #GLOCYBER ON INSTAGRAM he got all the ideas on each of the virus extension. He was able to repair mine.
REPLY ON YOUTUBE
It has been a week when I got infected but today I saw a comment that recommended me to #GLOCYBER ON INSTAGRAM and he was able to open all my files.
REPLY ON YOUTUBE
My MacBook was affected and I had no option than to contact #GLOCYBER on instagram. He did helped me recover all my files.
REPLY ON YOUTUBE
I suggest you should all contact #GLOCYBER ON INSTAGRAM. He was able to help me fix my computer.
REPLY ON YOUTUBE
My company system was infected too. We all couldn’t use our computers because it spreads to everyone computer. Our manager has explained that he hire #GLOCYBER ON INSTAGRAM and he was able to fix it. At least, we could have our jobs again.
REPLY ON YOUTUBE
My mums computer was infected and she asked me to help her. Although I don’t know how to fix it so I contacted #GLOCYBER ON INSTAGRAM and he helped us. He charged us a bit but it was very affordable. Thanks to him.
REPLY ON YOUTUBE
I got infected too. It was annoying seeing your computer but can’t use it. I did asked my technician and he suggest I should contact #GLOCYBER ON INSTAGRAM. I did contact him and he was able to help me out.
REPLY ON YOUTUBE
Am a photographer and it affected all my clients files and pictures. It affects my animal documentation pics. I almost cried, then I make my research and found out that #GLOCYBER ON INSTAGRAM has been helping out. He did mine and thanks to him.
REPLY ON YOUTUBE
Thanks to #GLOCYBER ON INSTAGRAM. He was able to fix my computer and all my files are normal.
REPLY ON YOUTUBE
My NAS was attacked by the virus but I was able to reach out to #GLOCYBER on INSTAGRAM and he could figure it out.
REPLY ON YOUTUBE
I got affected by the division of the virus. And I could not read for my exam because it encrypted all my lectures note. Thanks to my lecturer who recommended #GLOCYBER ON INSTAGRAM to help me recover my files. He did and am so happy.
REPLY ON YOUTUBE
Am a student too and it lock all my pdf and everything other thing in my laptop. Am so happy I got help from #GLOCYBER ON INSTAGRAM. He did a marvelous work and now I have all my files back.
REPLY ON YOUTUBE
I recommend you all to contact #GLOCYBER ON INSTAGRAM. He was able to help me recover all my encrypted files. Am glad I met him earlier.
REPLY ON YOUTUBE
I was dead in need of my computer. But I could not all because of this virus. I was recommended to #GLOCYBER on instagram and he responded to me and helped me fix my laptop.
REPLY ON YOUTUBE
Am able to contact #GLOCYBER on INSTAGRAM and I showed him what has happened to my computer. He was able to assist and get my computer free from the virus.
REPLY ON YOUTUBE
I was affected too and I talked to #GLOCYBER ON INSTAGRAM . he could help and he did recover all my files and photo.
REPLY ON YOUTUBE
It was through the help of #GLOCYBER on instagram that we ware able to get our money photos decrypt. The virus has held all the pics in the system.
REPLY ON YOUTUBE
It was #GLOCYBER on instagram that was able to help me fix all my files and get them decrypt. He really did a great work and am happy I met him.
REPLY ON YOUTUBE
I found a legit cyber professional. He is #GLOCYBER on instagram. he was able to help me fix and decrypt all my encrypted files. Thanks to him for his kindness.
REPLY ON YOUTUBE
Contacting #GLOCYBER on instagram was the best thing I did after my files got infected. He quickly decrypt all my files and get me free from the virus.
REPLY ON YOUTUBE
This virus has been attached to my files for more than a week. It was my dad who directed me to #GLOCYBER on instagram and he was able to get rid of the virus. Thanks to him.
REPLY ON YOUTUBE
my files have been encrypted and I thought I would never use them again. My lecturer told me to reach #GLOCYBER on instagram and he was able to help me recover my files from the virus. Thanks to him.
REPLY ON YOUTUBE
Contacting #GLOCYBER on instagram was the best thing I did after my files got infected. He quickly decrypt all my files and get me free from the virus.
REPLY ON YOUTUBE
Am happy I could contact #GLOCYBER on instagram and he was able to help me remove all the virus. My exams files are free now.
REPLY ON YOUTUBE
My computer was affected too and it got stuck of all the virus. Thanks to my sister who had recommended #GLOCYBER on instagram. I search him on google and he responded to me. Thanks to him.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
*I was hit, so unplugged, shutdown, external USB backs fine. Plex user, was watching at the time no issues, went to update saver denied, then found the splash screen, no on reboot, water gapped on an independent switch no WiFi etc, it instantly goes to initialization. So save to assume the service themselves have been affected. Did safe shutdown. After some time I turn on everything then I found out I’ve been truly hit by deadbolt. I did as many research as I could and I found out that scott can actually decrypt the encrypted files So I paid some money not upto what deadbolt team are asking, then he decrypted my files*
REPLY ON YOUTUBE
*I was hit, so unplugged, shutdown, external USB backs fine. Plex user, was watching at the time no issues, went to update saver denied, then found the splash screen, no on reboot, water gapped on an independent switch no WiFi etc, it instantly goes to initialization. So save to assume the service themselves have been affected. Did safe shutdown. After some time I turn on everything then I found out I’ve been truly hit by deadbolt. I did as many research as I could and I found out that scott can actually decrypt the encrypted files So I paid some money not upto what deadbolt team are asking, then he decrypted my files*
REPLY ON YOUTUBE
*I was hit, so unplugged, shutdown, external USB backs fine. Plex user, was watching at the time no issues, went to update saver denied, then found the splash screen, no on reboot, water gapped on an independent switch no WiFi etc, it instantly goes to initialization. So save to assume the service themselves have been affected. Did safe shutdown. After some time I turn on everything then I found out I’ve been truly hit by deadbolt. I did as many research as I could and I found out that scott can actually decrypt the encrypted files So I paid some money not upto what deadbolt team are asking, then he decrypted my files*
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
…You can message *SCOTTS_HACK*
REPLY ON YOUTUBE
…You can message *SCOTTS_HACK*
REPLY ON YOUTUBE
????I was so glad when I finally realized and get in touch with Glo Cyber while I used the contact above. He is indeed a genius and his skill are authentic. I rec. everyone to appreciate his efforts.
REPLY ON YOUTUBE
People keep talking about Scott. I think he is good. I will try him.
REPLY ON YOUTUBE
Someone recommended you ????and you also helped me recover mine too. You a genius indeed
REPLY ON YOUTUBE
Someone recommended you ????and you also helped me recover mine too. You a genius indeed
REPLY ON YOUTUBE
Let Eddie say something…
REPLY ON YOUTUBE
I wouldn’t touch QNap with a barge pole until they drastically change their approaches to the user base, contempt for the user base isn’t a great strategy.
REPLY ON YOUTUBE
You’re ???? such a genius, I really appreciate your services, fast and safe recovery process..
REPLY ON YOUTUBE
You’re ???? such a genius, I really appreciate your services, fast and safe recovery process..
REPLY ON YOUTUBE
My QNAP NAS used UPnP to open all of the ports needed for bad actors to try brute forcing their way in. I was getting over 1200 login attempts per hour.
REPLY ON YOUTUBE
I think forced updates should be a requirement for utilizing certain features. So, if I enable remote access through a firewall of any sort, forced updates should be enabled. IT enabled organizations wouldn’t be making use if these features anyway and in can absorb the risk of automatic/manual updating.
REPLY ON YOUTUBE
You’re ???? such a genius, I really appreciate your services, fast and safe recovery process.
REPLY ON YOUTUBE
I think they get attacked because they move into Face/Facial/Eye/Mask screening. People don’t like that. This is a threat to privacy. I think that is the root cause of it. I don’t know if Synology is in the same as such.
REPLY ON YOUTUBE
I regret I have missed this video 2 weeks ago. #asustor #deadbolt
REPLY ON YOUTUBE
I’m sorry I purchased a NAS as a means to have a BACKUP of what is/was on my laptop or pc. And it’s even sold as a backup. It started with ‘consumers’ being told to connect an external hard drive to backup their data. They would even supply at times backup software. So you backed up to this external drive. Then they started to sell NAS which was a way to still Backup and be able to access those backed up files from any connected computer.
So I disagree that you cannot thing of the NAS as a Backup.
Evidence: Why do they supply NetBak. Which can backup or copy your PC to the NAS.
So if you say the NAS is not a Backup tell these companies to stop supplying backup software that works to copy to these systems.
When I was told I needed a Backup I bit the bullet and purchased a second NAS which is used only to receive a Backup Data from the Main NAS! Its stupid but I understand it.
Especially since this last issue I had to erase my partitions to fix my issue. Great!
REPLY ON YOUTUBE
Wow I liked how you pointed out tech support being abrupt.
I reported a problem months and months ago and it was just impossible to arrange for remote support.
Then there was an update which fixed the problem we were trying to work on. So I basically wasted tons of time trying to recreate the problem and pin pointing the actual issue.
So why was I spinning my wheels for months when they knew about the issue.
Just tell me and ask me to be patient while they fix the bug. Why make me waste my important time for this sh*t.
I also had a problem of the NAS running so slow I could not even log in via the web. Thankfully I have a unit that has a hdmi port and was able access it via direct. But still could not use the system.
That was months and months. I was planning on dumping the whole thing. But it meant dumping two QNAP units. The cheaper of the two worked perfectly. I was angry.
Then I read something in a forum and decided to try it. I had to stop running Q’Center. Once I turned it off and removed it my system ran normally.
The same thing happens when you run McAfee. Of all things to slow down your unit so its unusable what is the purpose of having anti-virus. And whomever says its not needed needs their hand examined. You do!
The built-in anti-virus finds things that McAfee does not? And yes they could be false flags but it works.
REPLY ON YOUTUBE
Great video! I just saw lex friedman video and he talks about his devastating qnap ransom attack.
REPLY ON YOUTUBE
your videos could be a bit shorter and more concise. Lots of filler that doesn’t give a lot of information.
REPLY ON YOUTUBE
Not an IT expert but I bought an entry level Qnap NAS, which is now not connected to the internet and I’ve manually updated. What I’d really like to see is a guide to setting the NAS up safely so that the NAS is available to the home users, but protected from the internet outside. Backing up to two USB drives BTW!
REPLY ON YOUTUBE
Great discussion, can an OpenVPN / windows vpn on QNAP do it? and not juse myQNAPcloud? can it not be a good option? between one’s server and user outside of one’s network.
REPLY ON YOUTUBE
QNAP has significant blame in this latest attack. First, it was their operating system that was hacked (no one had to download a corrupt file). Second, they have all their users emails and all they needed to do is send out notifications to us users alerting us to all the attacks this past year not to mention warning us all to “unplug” immediately when this last attack started. Instead, they remain silent by email even to this day. The only reason I figured out I was hacked is after a month of not logging onto my NAS I found all my files encrypted when I went to grab some photos for my wife. I had to figure out for myself (with the help of bleepingcomputer forum) what was going on, how to get the ransom message back because they had quarantined it. No I didnt have a backup and I guess that is my fault for not understanding the hardware and risks better but I bought the NAS because it was supposed to “simple, safe and secure”. I only use my NAS on my LAN and I’ve never downloaded outside files to it but am not savvy enough to not have it connected to the internet thru my router. If Im lucky enough to get my data back after taking out a loan on my credit card and figuring out this whole Bitcoin thing this weekend, Im done with QNAP and their crappy equipment, buggy software and business approach. QNAP’s silence, irresponsibility and incompetence in dealing with these attacks this past year is the real story here that you all should be talking about as well.
REPLY ON YOUTUBE
What is the most concerning for me as a customer, not that hackers exists, they always did. But that Qnap has backdoor account to my own NAS…… they can remotely access to HBS, force update or whatever….. the clear answer to me to your question is : QNAP is not safe at all, period !
REPLY ON YOUTUBE
I don’t understand why so many “intelligent” people finger-point the victims. Do those guys blame their kids who’s got bullied in school? What a pathetic! NOBODY, NOBODY opened the port to the internet! QNAP got the port opened OUT OF THE BOX! I’m not using mycloud, I didn’t open any port. I didn’t enable auto-update because last year I ever lost files after migrating to the latest build!
This is not the first time they messed up everything. As always, QNAP is trying to escape from their own responsibilities. They pretends nothing happened. Custom service is non-existent. Users forum is full of everything but anything helps fix the issue.
Stay away from QNAP like a plague!
REPLY ON YOUTUBE
Infected last month, huge damages to us, and i guess it’s their ex-engneers who made ransom, and i am sure this company will fall.
REPLY ON YOUTUBE
I use my QNAP for Plex, and I share my Plex with two other friends. This is my second ransomware attack (thank goodness I had backups), so should I stop sharing? Can I make my QNAP secure and still share?
REPLY ON YOUTUBE
Thank you for making this enlightening video! I have now checked and switched off UPnP at my router. I was also watching your Plex setup video where you talk about setting remote access for Plex on a Synology NAS (with DSM 7) . How risky is setting up remote access for Plex to access my media remotely and are there ways to mitigate the risk?
REPLY ON YOUTUBE
I have found QNAP TVS-951X about 350£ (450$) used with 30 days free return + 6TB WD RED drives + 32GB RAM, should I buy it ?? it does look in a fair condition I want to use it for 4k streaming + 1080 and some backup + two or three members of my family watching 1080 content with me also to back up my stuff on it, should I buy it ??
thank you
REPLY ON YOUTUBE
Robbie and Eddie, Thank you for this in depth discussion, and guidance. I’m new to this, bought my nas at the end of November, and have been following a steep learning curve since then. I especially liked the advise to NOT TOUCH your network or nas settings if you do not understand the actions and results. I have to remind myself of that each time I mess with the settings, and have to reconstitute my nas.
REPLY ON YOUTUBE
I bought a single, large (16TB) HDD in recent weeks, plugged that into a free bay in my NAS, created a new storage pool & volume, and copied all my existing NAS Data onto it, and when complete, I pulled that Harddrive out. This is my ‘emergency’ back up, should the worst happen.
REPLY ON YOUTUBE
The Bank & Bank card analogy is a good one.
REPLY ON YOUTUBE
I don’t have remote access to either my QNAP or my Synology directly or through their respective relay systems. Instead, I use OneDrive (OD) as a relay point. My NAS is setup to sync with my OD account. When I’m on the road, my laptop syncs files with OD. So, when I edit a file on my laptop, it then syncs to OD which in turn syncs to my NAS. This won’t work for everyone but it can be a very effective way to effectively gain access to your NAS while working remotely. I don’t do this with the entire NAS, just the folders / files that I may need remotely.
REPLY ON YOUTUBE
Just bought a qnap nas yesterday. Really useful conversation. I have to admit i’m a little more concerned after watching this video than i was before.
REPLY ON YOUTUBE
Probably a recommended setting for beginners users from QNAP might works.
REPLY ON YOUTUBE
We are preparing a new video about how to secure your NAS and your local network.
You can send your external IP address to us via NAScompares.com contact form and we will run free vulnerability tests for you.
This will allow you to identify your network vulnerabilities and open ports etc.
REPLY ON YOUTUBE
Thanks again, last year after qlocker Eddie was adamant that myQnapCloud was safe and I believe the issue was upnp allowing access a hard coded back door.
Do you both still feel myQnapCloud is safe ?
REPLY ON YOUTUBE
Really enjoyed this especially since they got me too. Thank you. Small piece of feedback – it’d be great if you gave Edward a bit more of a chance to speak at times. There are sections where it seems he’s just on the receiving end of a long lecture, as opposed to part of the conversation.
REPLY ON YOUTUBE
Rip out the DOM n install unraid on it 😀
REPLY ON YOUTUBE
Thanks Robert. Thanks Edward.
REPLY ON YOUTUBE
Could you do a video on how to secure your nas? Things like what port to put things on. Stuff like that?
REPLY ON YOUTUBE
im using a tricky way to remotely access my NAS files, by hiding them behind a nextcloud single user on a Pi thats not visible. not infallible, but takes breaking that, just to see files, not alter them or upgrade. if i have to upload, i have to remote into a computer and use other methods. rarely do i need to access files , but it can be done if i have to.
REPLY ON YOUTUBE
After using QNAP NAS devices for years – we’ve lost all confidence in the brand and it’s no longer on our supplier list.
REPLY ON YOUTUBE
TL:DW; version – its a security/ease of use trade-off. If you lock things down users find it too hard to use the features the vendor offers and berates them for it. If you open things up you give users the chance to shoot themselves in the foot, and some will.
Case in point being IoT “plug and play” devices. I was struggling to identify a device on my network today and discovered it had a password-protected web server – I guessed the password on the third attempt. You’d have thought vendors would have learned by now but clearly not.
Another interesting point given the mention of TrueNAS – Unraid ships with all security turned off by default. I think they’ve now realised they erred in doing that, but don’t seem to be in any hurry to fix it. I’ll be keeping any NAS behind a VPN. Wish I could do the same thing with Plex but it seems to need an opening to work properly, so I’ll have to isolate it on a VLAN.
REPLY ON YOUTUBE
One of the mistakes that QNAP made on this was that they actually identified and problem and issued a fix before the attack. But they didn’t make the update mandatory (they can override the user desire on when to take an upgrade). Users that had manually done the upgrade like myself or ones that didn’t have their NAS exposed to the Internet were fine. But other users were hijacked.
REPLY ON YOUTUBE
I did enjoy the video. I got a month ago a TVS-H1288X. We wouldn’t be talking about this if everyone had updated their NAS. QNAP needs to have a shout mode that you can’t miss if the patch fixes a vulnerability. The lack of organized information as not only to what to do but why? Example Port 443. It is recommended to change it but what range and why change it. I assume port scanners don’t deviate from assigned ports and look for low honing fruit. So by changing to 478 it is put out of the scanner range? If we do a router port forwarding to use QBelt on the NAS is that a direct open door to get into the NAS? I am guessing no otherwise why do assigned ports exist. At moment because of questions I have port forwarding off therefore I can’t use QBelt VPN which we are told it safe. My point is there needs to be a source that explains all of this that we can read. I am an engineer and programmer. First thing I did was set up QBelt to my android phone. UPnP was off from beginning. I have turned off myQnapCloud as I am unsure of where it stands safety wise. Has it been broken before? I even bought a certificate from Qnap and installed it. I think you should step in detail on each part of these security setting. What to change? Why you do it. And where to get more if on it. Love your videos
REPLY ON YOUTUBE
Data (physical or electronic) is arguably the most important thing you own the protection of it it more important than money.
If I loose a $50 note it can be replaced with any other $50 note the thing that makes it unique, the little string of numbers in the corner or any stains or creases are not what gives this value to you.
Conversely if you loose 50mb of data it can’t be replaced with any old 50mb of data as it’s uniqueness IS where the value was held. It is by definition irreplaceable/ priceless.
When average joe numpty buys an external HDD, NAS OR starts doing some form of online cloud storage or backup they have stumbled into the realisation that data holds value.
Often it’s a result of learning the hard way and loosing something.
NAS brands really should be held to account for some things but like you say not all.
From a consumer protection point of view, is it fit for purpose? Does it do everything it was advertised to do? Was it free of defects?
I buy a NAS, follow their instructions for setup while using the drives they recommend.
My expectations are:
– My data will be stored there without risk
– My data will be available using ALL advertised methods without putting it at risk
– I will be prevented from accidentally impacting the above two things.
During the setup process there should be a “most users” option that walks you through a VERY simple wizard (most users are not as smart as they think they are… see Dunning-Kruger effect).
Lock out or at least require a certain level of knowledge to unlock the most advanced features. Maybe a big warning when you select advanced option a big simple warning saying “by clicking this we no longer warrant the safety and security of your data” The stuff a car owner should touch is yellow under the bonnet of most cars now. Oil, wiper fluid, etc…
Also as joe numpty does not understand the difference between redundancy, backup etc etc. prompting them to locally encrypt and purchase a offsite data storage plan, backup to another offsite NAS or set up automatic email reminders for periodic backups.
Updates should always come with a have 3 options:
1. Update instantly on release. Early adopters on the bleeding edge (called that for a reason) “the is an update available and will be installed in x hours unless you hit cancel”
2. Delayed update (default most users). There is a new update available it’s currently being installed on some systems. This update will be automatically installed on this hardware after 30 consecutive days of bug free operation globally”. In this mode critical exploit patches are able to be forced if it impacts the last auto update.
3. Auto update off. Notifications on.
I think it’s absolutely NUTS that people give any nas company any form of slack for not treating your data at least as valuable as a bank treats your money. DONT share your pin, unusual behaviour lockdowns of accounts, etc.
Hard to type all this crap on a mobile phone.
REPLY ON YOUTUBE
Great Discussion! Driver’s license…????????????
REPLY ON YOUTUBE
Absolutely, I bought it for the hardware. Not always as inexpensive as I’d like — TS-873A vs 873-AU come to mind.
Is QNAP safe? Well, when it’s a NAS not an iNAS … mostly. I mean, there’s an IOT vector, but this is an IOT issue — does QNAP need to make its NAS safe against a determined in-network hacker? The IOT threat is just a whole nother topic….
The problem is that they market their internet-connectivity, and they need to stop doing that until they get their house in order, because they don’t have their house in order. Their responsiveness to CVEs has been lackluster at best, bordering on dangerously irresponsible. Security concerns are not as front-and-center as they should be. And magic, hard-coded backdoors in software is so gigantically awful — that stuff never should have been checked in to anything that ships to a customer. Astonishingly terrible.
REPLY ON YOUTUBE
Good discussion! But their privacy policy is what drove me away!
REPLY ON YOUTUBE
Great discussion. I like how you alluded to the “everyday man.” The reason I gravitated from Synology to QNAP was #1) Hardware comparison but most importantly #2) Capability to do more thanks to the software’s ability to have a lot less guardrails allowing me to do more.
I am by no means an IT expert, but I want the most hardware for my money and the software capabilities to do it. I also learned early on YOU HAVE to absolutely!!! know what you are getting yourself into before opening up your network with any NAS.
REPLY ON YOUTUBE
There is only one important rule. Never expose your NAS to the internet…until you know exactly what you are doing! Anyway, and always remember, a NAS is NO backup (RAID is not enough backup, either)!
REPLY ON YOUTUBE
Probably time for everyone to realize that these boxes are not good enough for external access. I have 3 qnap boxes and would never expose them to the outside. You want to go outside, go with the big boys like Azure. Qnap is not up for the job. It is fine for your LAN and leave it there.
REPLY ON YOUTUBE
As regarding the backup, one of the reason’s I am looking at buying a NAS is to allow me to put one in my home and one in my parents home, and allow us to both sync our data to have an off site backup.
But this means both need to be exposed on the internet to allow the sync. In this case it I think it makes sense to have both of these to be using the same platform as this includes software to sync.
However if I chose QNAP it is the process of wanting to get the backup capabilities that is exposing me to the data risk.
I am a software developer, (i.e. the worst person in this case since I know enough to be dangerous), but am no ‘Locksmith’, so would really welcome better hand holding and explanation of what the various features are actually doing behing the scenes and what the risks are.
REPLY ON YOUTUBE
QNAP need to open and honest about what vulnerabilities in what software exist on all of their models. If you fix the vulnerabilities sooner via auto-update (and not all vulnerabilities need reboots) then they wouldn’t be in this situation.
REPLY ON YOUTUBE
How about a step by step guide to secure your qnap nas?
REPLY ON YOUTUBE
No, absolutely, NO
REPLY ON YOUTUBE
Safe to save garbage files I guess.
REPLY ON YOUTUBE
Just come here because my NAS has been compromised! I’m so annoyed and this has been a major blow for my business (video production company).
REPLY ON YOUTUBE
People should know about this this is madness, just happenned to me? 8 months later?? Could they have warned their F*ing customers??!!
REPLY ON YOUTUBE
i was infectet now on 7 dec 21
REPLY ON YOUTUBE
Shut T F Up! Nothing said!
REPLY ON YOUTUBE
I don’t use my over the cloud I only use it with my local network. Is it safe that way ?
REPLY ON YOUTUBE
Is it safe to keep using WD My Cloud if I turn off remote access in the menus? Or should I block access in the rougher? It’s just I find the WD my cloud useful for streaming Films and TV shows to TV. Also, it being a network drive it’s always on so don’t need to turn on PC for a network share. I did use to use it for backing up photos, off my phone, but don’t trust it with my personal files. So just use it for just media.
REPLY ON YOUTUBE
i have 2 of the my book live drive. none where wiped but i unpluged the bothe from being online. and i got my cupon for a new one at 40 percent discount , just waiting for my new device 😀 8 tb ex2 ultra .
REPLY ON YOUTUBE
The little graphics was very helpful. I learned my lesson for sure on what having a backup actually means.
I naively bought my NAS thinking it would be my own little personal cloud machine and sole backup (thinking raid would keep me safe forever) for my documents, photos, and videos.
Now I realize I’m going to still have to spend more money on cloud services and be very careful with my qnap nas.
I was immediately thinking of switching to Synology since you said it’s more user friendly and all I really use my NAS for is backup and as a cloud drive to put my files into it and be able to retrieve them on my phone. Unfortunately, from what I’ve seen on the appstore the other Nas company apps look like they are just as rough, slow, and confusing to use as Qnap’s (Qmanager and Qfile). I don’t understand how “downloads” and “Qsync” works on Qfile for example so I’ve been just moving files manually as I would on any other cloud app.
For now I’m staying with my TS-453D.
But still have mixed feelings about it.
REPLY ON YOUTUBE
i have a my book live duo 8tb it has a usb on it, can i just simple plug it into my pc usb, without router, to put more stuff on it, use it as a external drive, any info be appreciated
REPLY ON YOUTUBE
So I got stung by the Qlocker ransom ware attack and apparently it was caused by a back door issue relating one of the apps, hybrid desk station? I can’t recall I was too busy fuming at how a company could have this vulnerability. And I do appreciate the support the qnap staff have tried to give in recovering the files and data, but when the process broke down and they let communication fade, with lack of support to get a resolution I soon lost patients with them and decided to let go of some files. I thankfully did have back ups but when your sync does the backing up it basically just had a knock on effect so ran some files where synced to pc, and a back up hard drive before I had noticed. Thankfully larger files where left and they only went after the smaller file sizes.
Anyway long story short, always back up your data manually on an off line hard drive. This is the only real way you can secure a true back up of your files. Thankfully an old NAS gave that option to me.
REPLY ON YOUTUBE
Has there been a fix?
REPLY ON YOUTUBE
An attempt to kill off the old WD systems so it could be anybody.
REPLY ON YOUTUBE
But this doesn’t have any influence on the QNAP Nas?
REPLY ON YOUTUBE
I am also one of the affected users, I disagree that WD acted quickly as it was 2 days after I reported the issue I got the general disconnect email. I only had 1.2tb in use on a 4tb my book live duo but it now reports 3tb in use. Waiting for WD to say how to proceed, hopefully they will offer some sort of data recovery service, I bought mine new from PC World in 2016 so I guess it was old stock, but even so for a network connected device WD should be updating security regularly.
REPLY ON YOUTUBE
If you have VPN this can be prevented.
REPLY ON YOUTUBE