https://nascompares.com/podcasts/weekly/week48-2025.m4a React2Shell Vulnerability Threatens Nearly 150,000 Servers Worldwide A critical security flaw in React Server Components, designated CVE-2025-55182 and dubbed React2Shell, has emerged as one of the most severe vulnerabilities of late 2024. The Shadowserver Foundation’s latest scans reveal approximately 148,740 internet-exposed servers remain vulnerable to this unauthenticated remote code execution exploit, with nearly 94,000 […]

https://nascompares.com/podcasts/weekly/week10-2025.wav Here’s your Weekly NAScompares Digest – Week 10, 2025, covering 13 major topics in NAS, storage, and networking. 1. AOOSTAR WTR MAX NAS with 11 Drive Bays & Ryzen 7 PRO 8845HS AOOSTAR has announced the WTR MAX NAS, a high-performance storage solution powered by the AMD Ryzen 7 PRO 8845HS, an enterprise-grade CPU […]
In today’s digital world, network-attached storage (NAS) devices like Synology have become essential for home and business users alike. These devices store everything from personal photos and files to essential business data, making them a prime target for cyber threats. Recently, several zero-day vulnerabilities in Synology NAS products were discovered, posing significant risks for […]
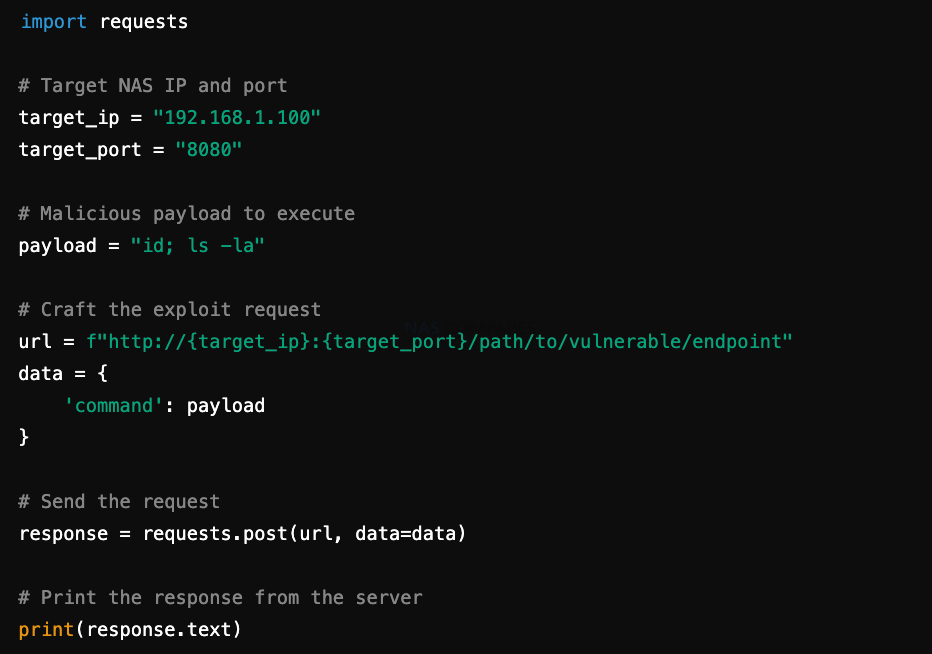
In today’s digital landscape, Network Attached Storage (NAS) devices are becoming increasingly popular for personal and business use. They provide a centralized location for storing, sharing, and accessing files across networks. However, as the use of NAS devices grows, so does the risk of cyberattacks, particularly ransomware. One significant factor that can expose these […]

In a grand showcase at COMPUTEX 2023, QNAP Systems, Inc., the renowned innovator of storage, networking, and computing solutions, left visitors in awe with their groundbreaking lineup of new products and services. QNAP’s commitment to integrating AI, cloudification, performance enhancement, and security is evident in their impressive range of offerings. Let’s delve into the exciting […]
[UPDATE] DSM 7.2 Now Live! Download link at the bottom. Synology has officially released DSM 7.2, the latest version of its operating system for NAS devices. The new update brings several improvements, enhancements, and important changes to the Synology DiskStation Manager. Let’s take a closer look at what DSM 7.2 has to offer. Important Note: […]

QNAP, a leading provider of storage, networking, and computing solutions, has announced the launch of its QNAP Security Vulnerability Reward Program. The program aims to actively protect information security and ensure network security by inviting global information security experts and researchers to participate in creating a more secure network environment and storage services. The QNAP […]

Introduction Brief overview of VPN technology VPN (Virtual Private Network) technology allows users to securely access the internet by encrypting their internet connection and routing it through a remote server. This creates a virtual “tunnel” between the user and the internet, effectively hiding the user’s internet activity and location. VPNs are commonly used by individuals […]
What are the signs someone is trying to hack into your home network? There are several signs that someone may be trying to hack into your home network. Some of the most common signs include: Unusual network activity: If you notice an increase in network activity, especially at unusual times, it may be a sign […]