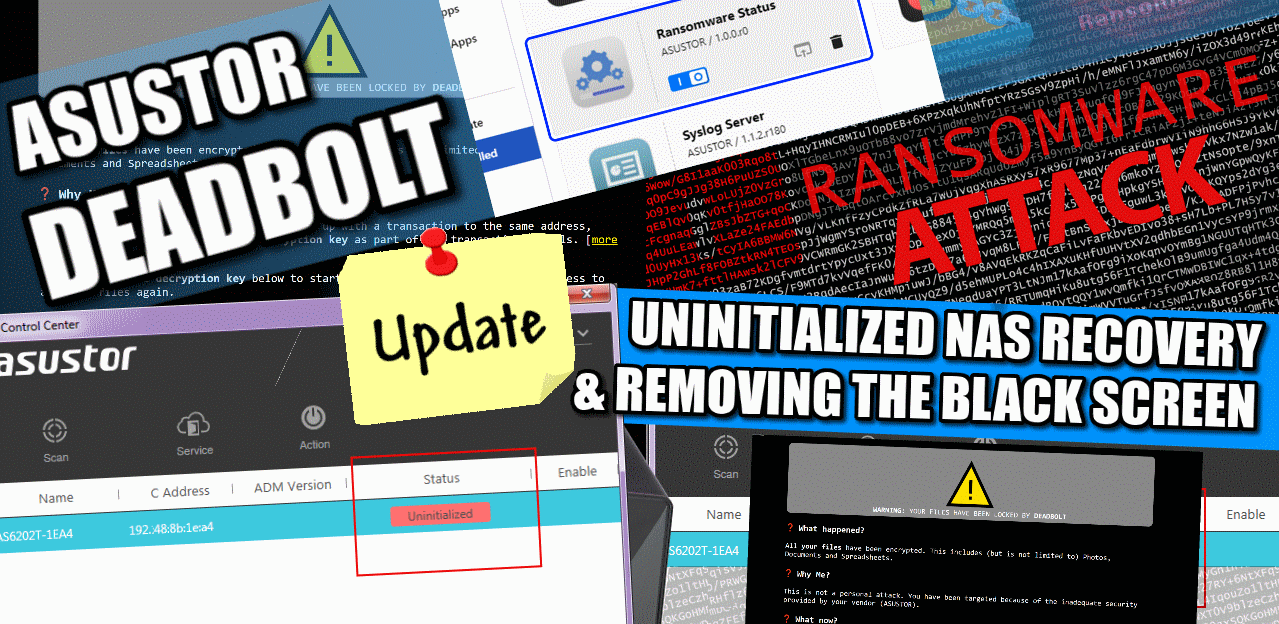
Getting Your Asustor NAS System Up and Running Again After Ransomware Attack
It has now been a few days since the initial attack of Asustor NAS systems by the deadbolt ransomware attack and although full recovery is still not a complete option for a lot of users (without having to take the agonizing step of paying the group for an encryption key – gah!), there have been steps by users, the linux community and Asustor to mitigate some of the damage for some and for those unaffected, allow them to use their systems with a little more confidence and comfort. Below are some instructions that will be of use to users who are currently in the following situations with their Asustor NAS:
- When the encryption/attack first started (or you first noticed the NAS activity) you powered down your system abruptly and your NAS now shows as Uninitialized’
- You Have the Asustor NAS working, but are being greeted by the black deadbolt threat screen that you want to navigate around WITHOUT using SSH/Command line
- You are in either of the above two positions AND you have snapshots or a MyArchive routine setup on your NAS
If any of those three setups are how you would describe the position that you/your Asustor NAS is currently in, then you may well find this guide useful. However, DO remember that you are still dealing with your data and although this guide has been provided for the most part by the band themselves (with additions by myself – Robbie), you should immediately have a backup of your data (even if it’s encrypted in case of a system failure etc) and/or an external drive ready to move any/all data over too. If you caught the ransomware encryption early, then you might still have a good % of your data still ok. Observing numerous affected machines have shown us that the encryption/changes begin at the system level (ie so it can change the index screen and renaming, etc), so in some cases, some people have reported that they caught it in time for some data to have been RENAMED (i.e the .deadbolt prefix that is affecting access or older structure in some cases) but not actually encrypted. So, this guide is about getting you into a position to access your Asustor NAS GUI and whatever the state of your data is. After that, you may still have no option but to format your system, wait for any kind of brand/community recovery method or (and I do not say this lightly, as the thought of continuing this kind of behaviour is disgusting) pay the ransom to get your data back. I appreciate that this is S&!T but some business users might have little choice. Let’s discuss access recovery options. If you are unaware of everything that has occurred to asustor and the deadbolt ransomware, you can use the attached video below:
Asustor NAS – How to Get Your NAS Running Again If It Is Saying Uninitialized
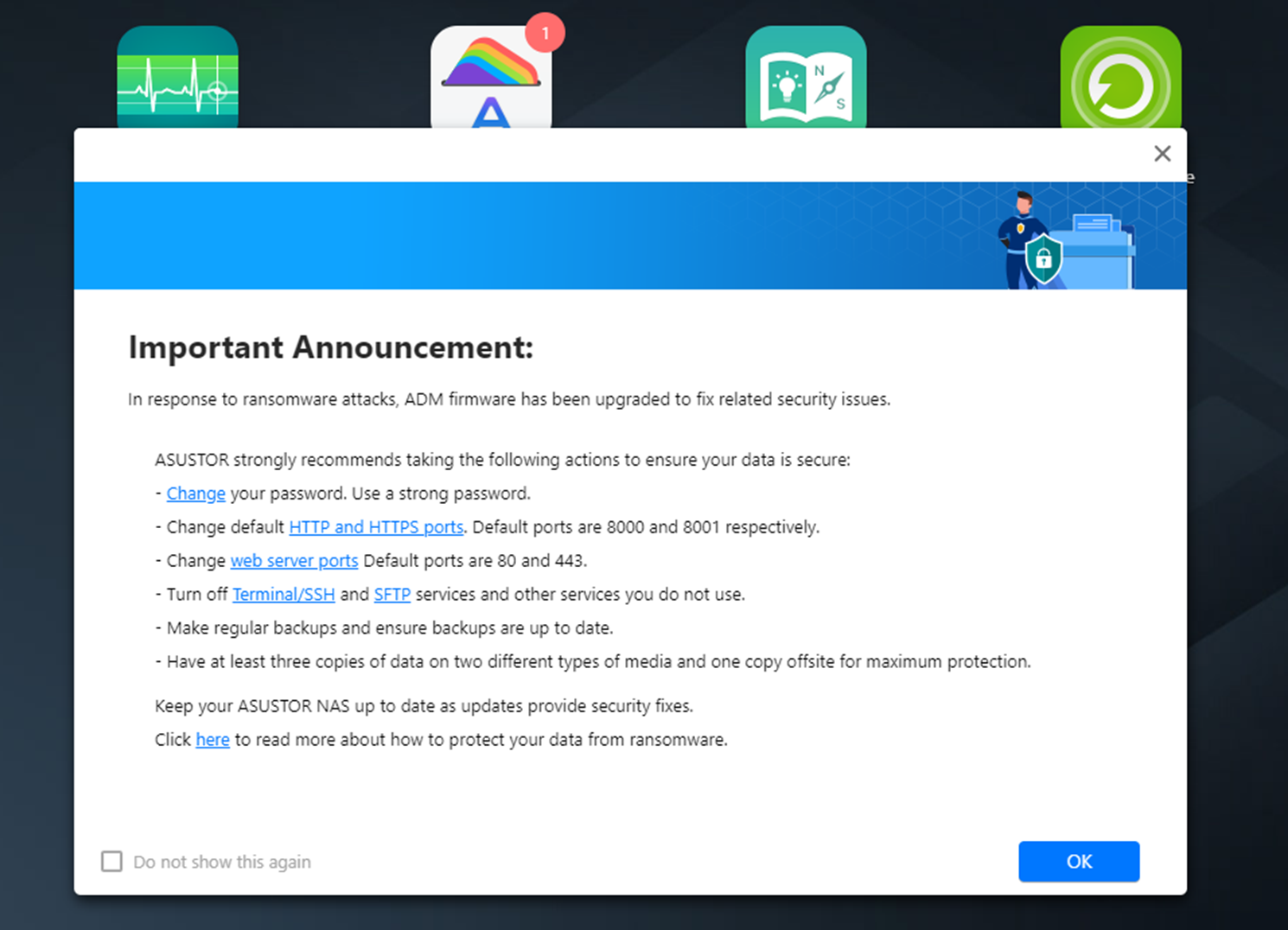
If you powered down your NAS abruptly when you saw the black threat screen OR unusual activity on your NAS (either by pulling the power cord or holding the power button for 5-10 seconds), then chances are that as the encryption hits the system files first and was in progress, that your NAS is not showing as ‘uninitialized’. This is because the system software is no corrupted. Yesterday Asustor released a new firmware update that closed the vulnerability (they claim, I have not verified personally yet). So, the following steps in the guide using the client desktop software Control Center and an internet connection (can be just on your PC/Mac and you directly connect with your Asustor if you choose) will allow you to access your NAS login GUI.
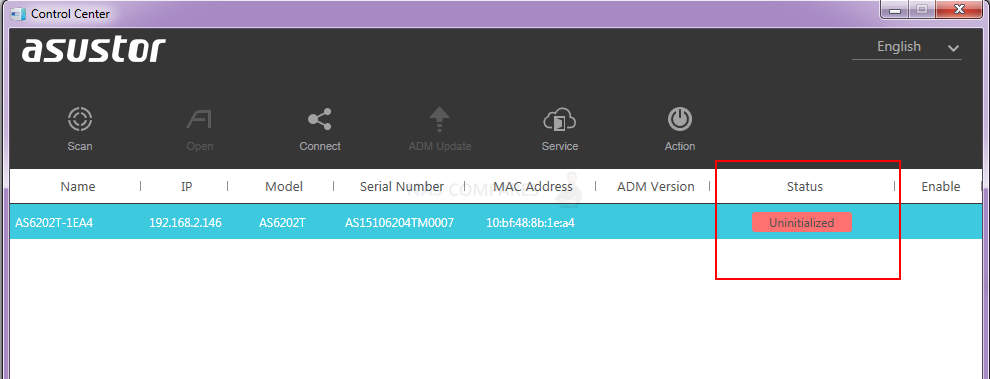
If you have shut down before, please connect to a network. If you enter the initialization page, please follow the instructions below to update your NAS:
Step 1
- If you enter the initialization page and have an Internet connection, please press Next.
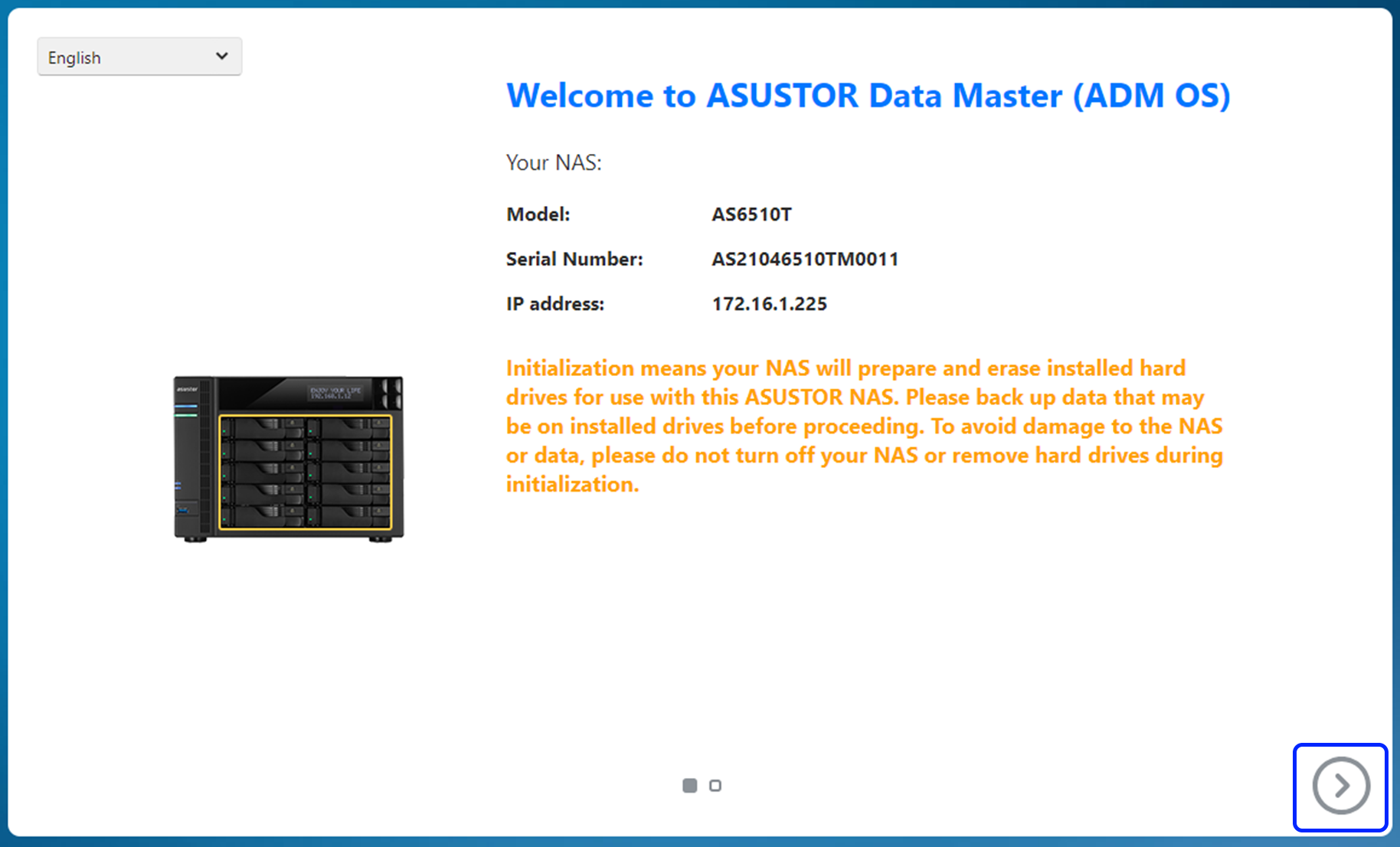
- Please click Live update and then click Next.
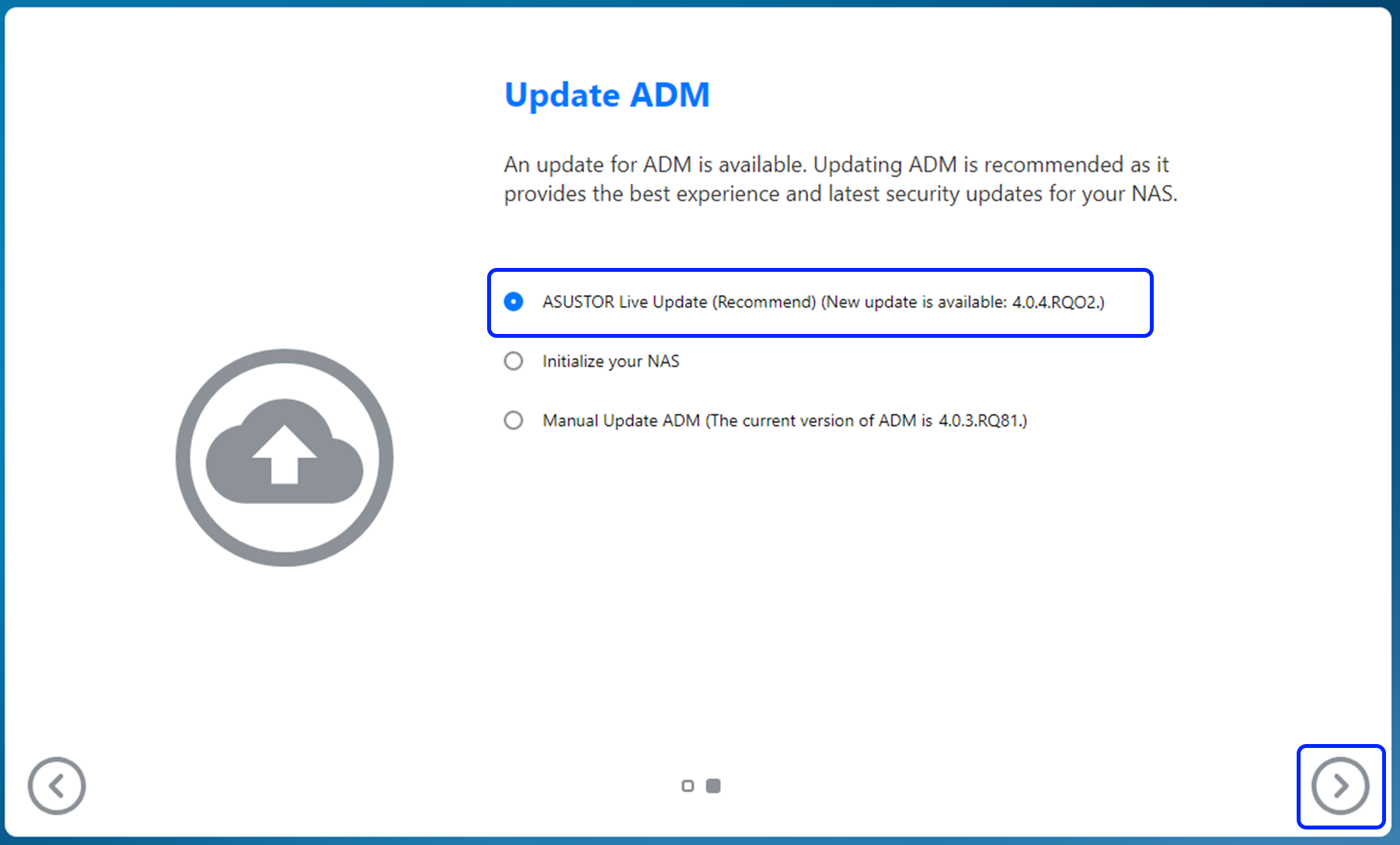
Step 2
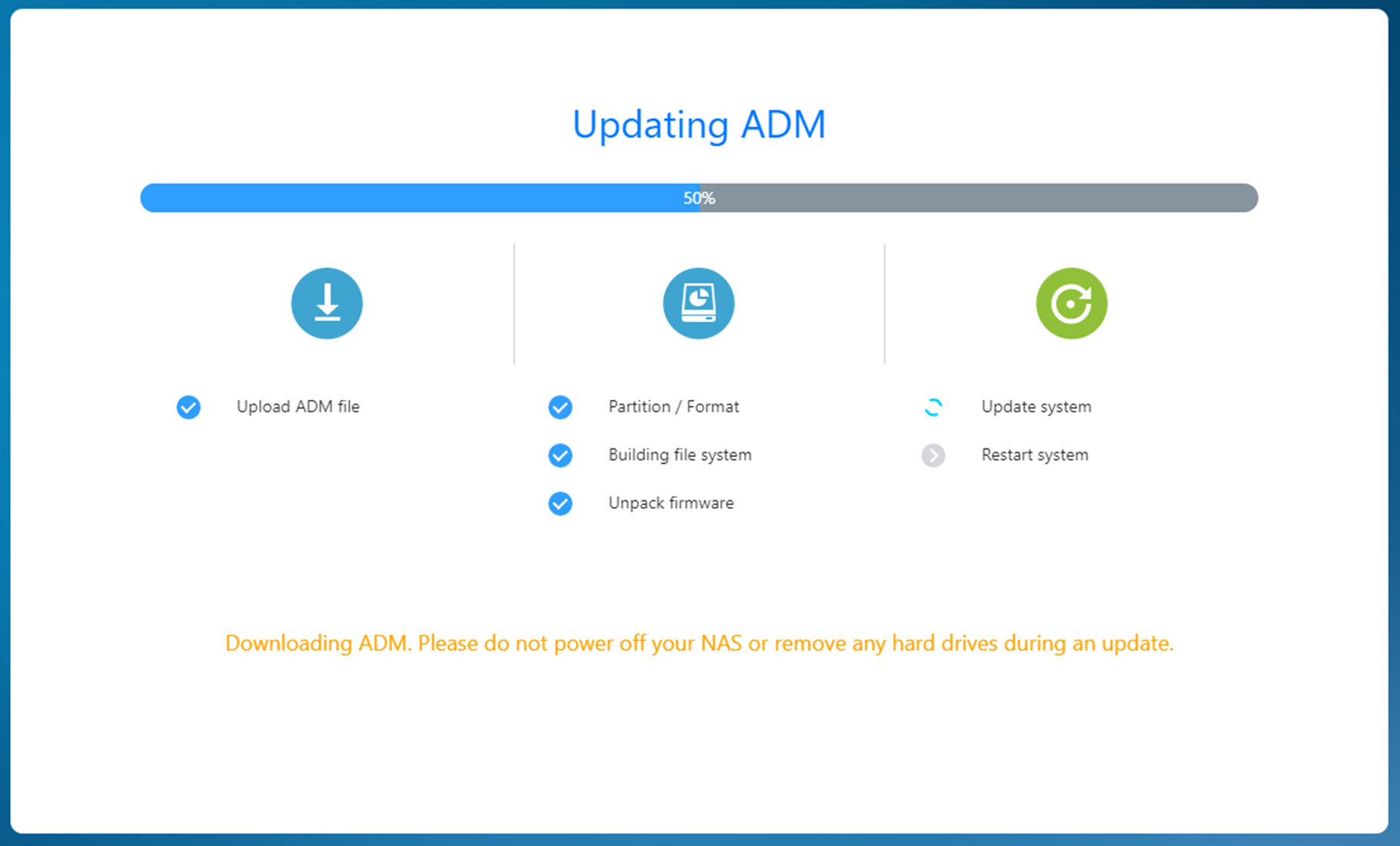
- If you’re on the initialization screen and not connected to the Internet, please download ADM from ASUSTOR Downloads to your computer.
- Once done, manually update ADM by uploading the ADM image file from your computer as shown below.
- Please press Next.
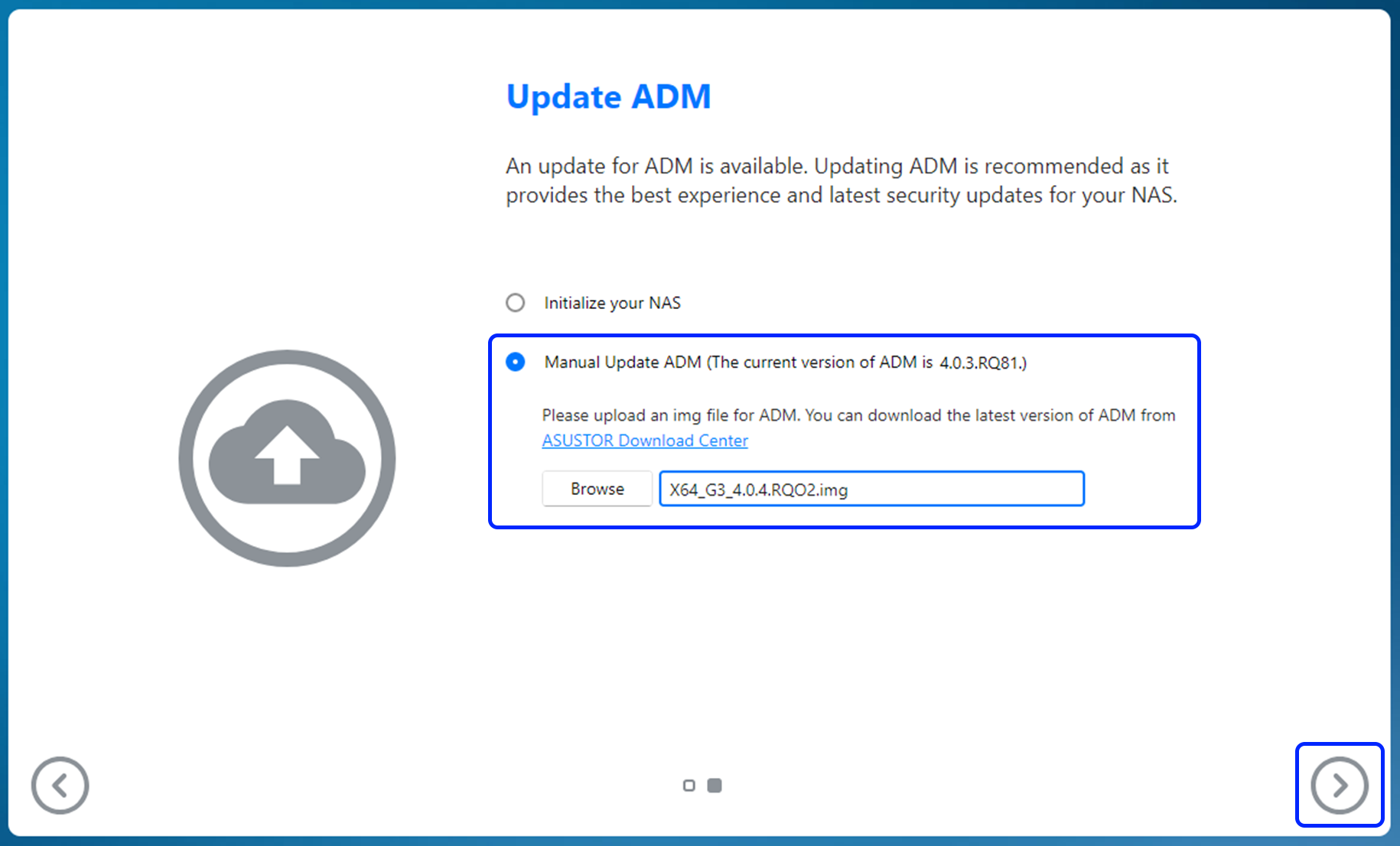
Step 3
- Update.
- After the update has completed, you’ll be able to return to ADM.
Asustor NAS – If You Are Still Seeing the Black Threat Deadbolt Ransomware Screen
If you have access to your NAS drive BUT are faced with the black threat login screen replacement that replaced the previous one AND have followed the previous steps to install the latest firmware, the next three steps should allow your to navigate AROUND this and remove it entirely.
If the ransomware page remains after you connect to a network:
- Please turn off your NAS, remove all hard drives and reboot.
- When the initialization page appears, reinsert the hard drives.
- Please follow the instructions above to update your NAS.
Asustor NAS – How to Restore Data with Snapshots, MyArchive Backups or Mirrored Volumes
Now, the next step is not going to be an option for everyone. Once you have logged in and accessed the extent of the file damage by encryption (eg, % of files affected, are they encrypted completely OR just renamed? etc). The following steps will be of use to those of you who are running a BTRFS setup and setup snapshots and/or the MyArchive backup/sync storage service. This part of the guide also includes the means to install a ransomware tool that (I know, ANNOYINGLY) gain access BACK to the black encryption entry screen. So if you have no choice (I am not judging you, the importance of your data is your call) and are going to choose to pay the ransom as it is going to cost you less than not retrieving your data, then you can use this ‘ransomware status’ tool to gain access back to the payment screen, encryption key window and ultimately allows you to pay the hackers. Again, it’s your call.
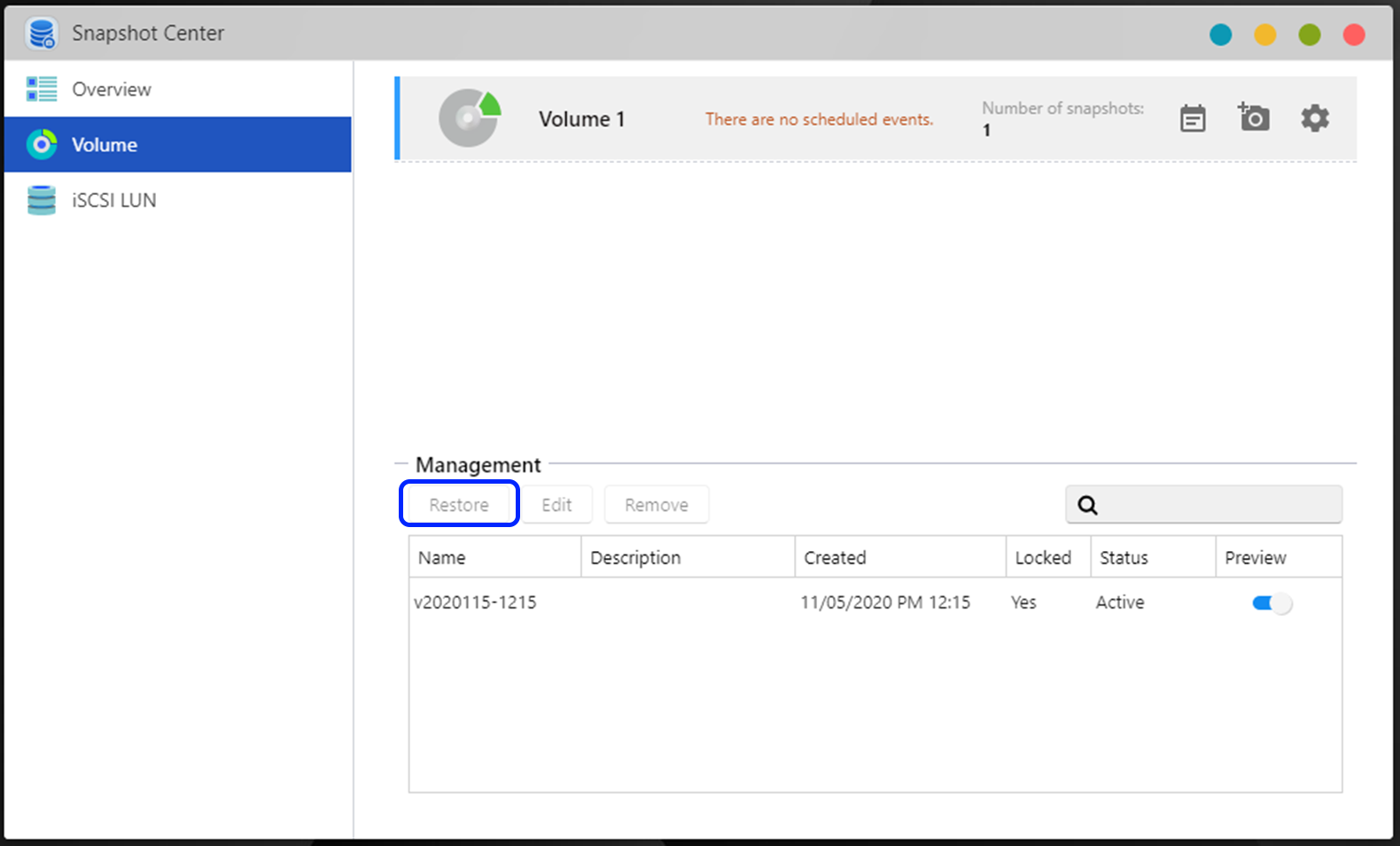
If you want to restore data and you have more than one volume installed on your NAS, use MyArchive drives, or have previously made Btrfs snapshots, please refer to the following instructions below. Restore all backups that you may have. Alternatively, if you have Btrfs snapshots, use Snapshot Center to restore previous versions of files and erase changes done by ransomware.
If regular backups were not kept and you want to enter the decryption key to retrieve lost data:
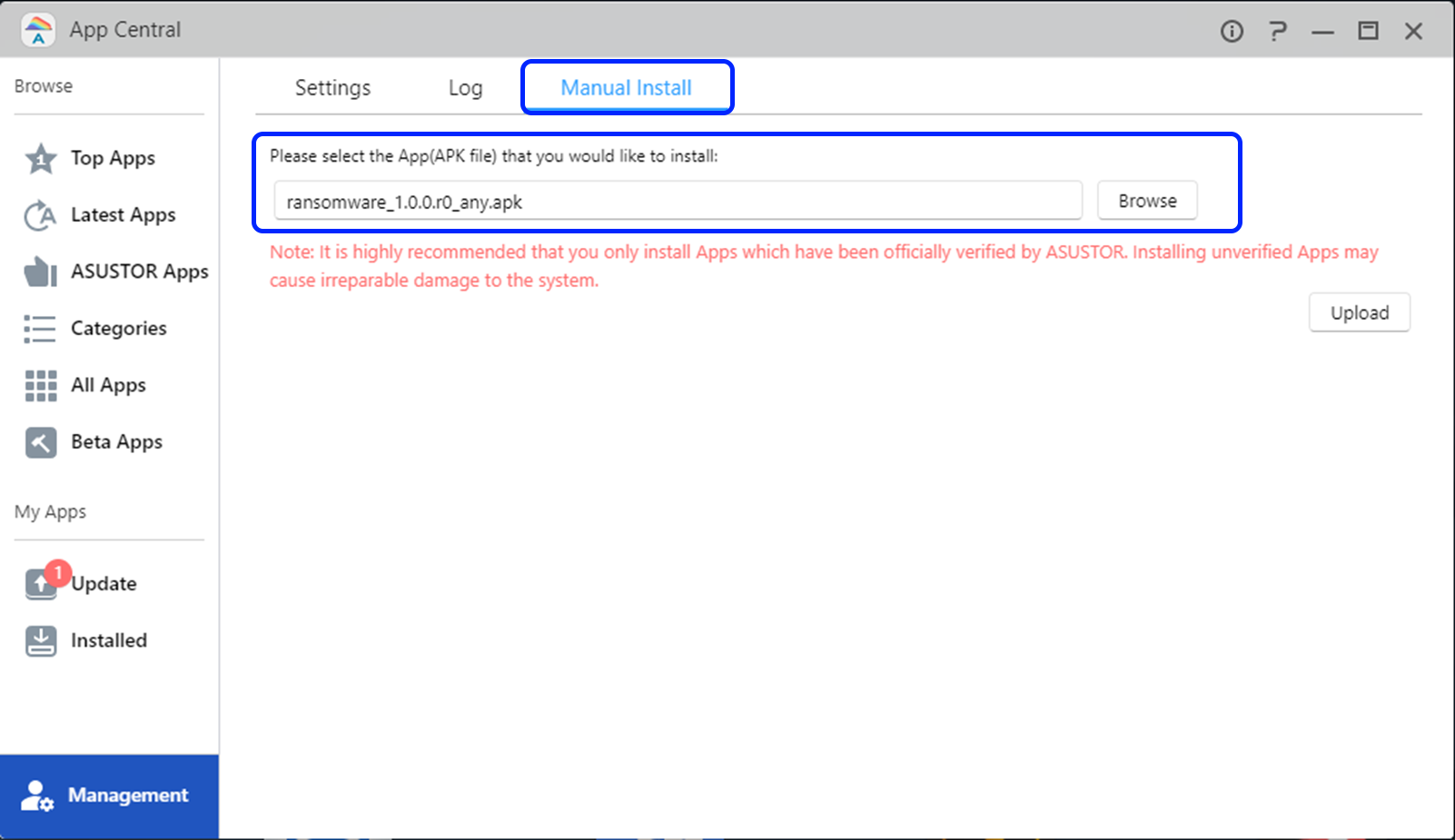
- Please download and install Ransomware Status by sideloading it into App Central.
- Confirm details and press Install.
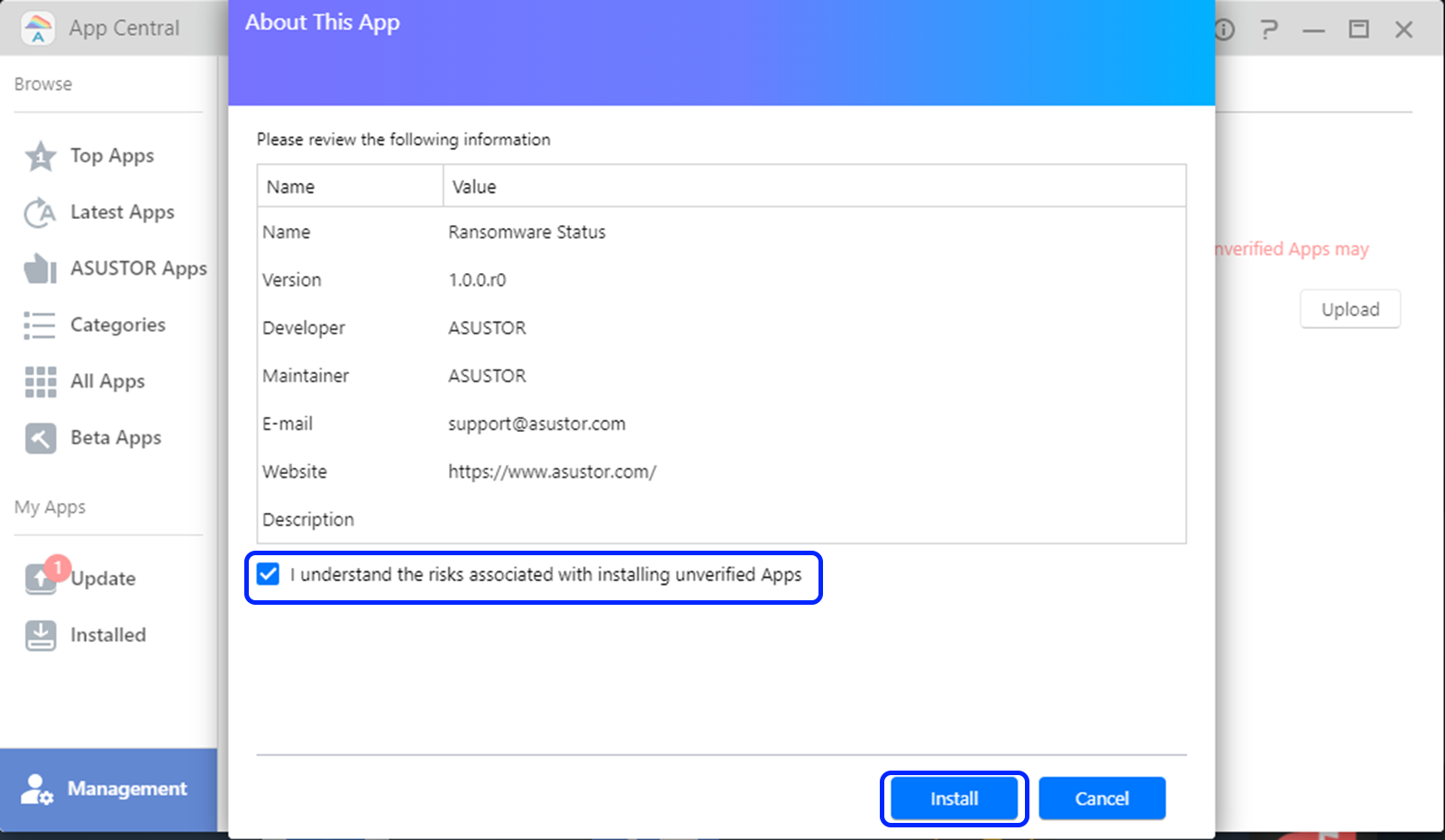
- Wait for installation to complete.
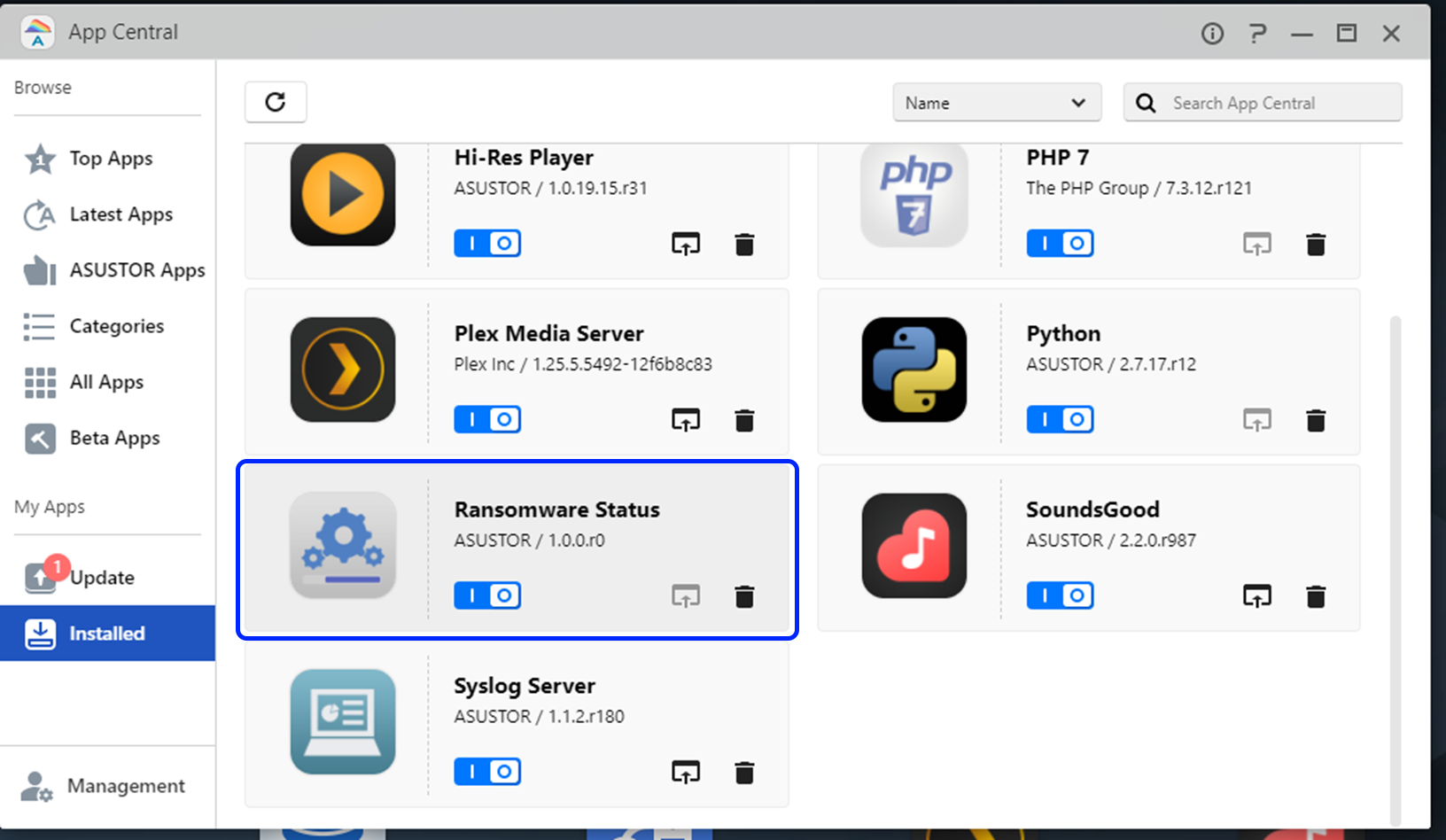
- Reload the webpage to enter the ransomware screen again. You’ll be able to enter the decryption key.
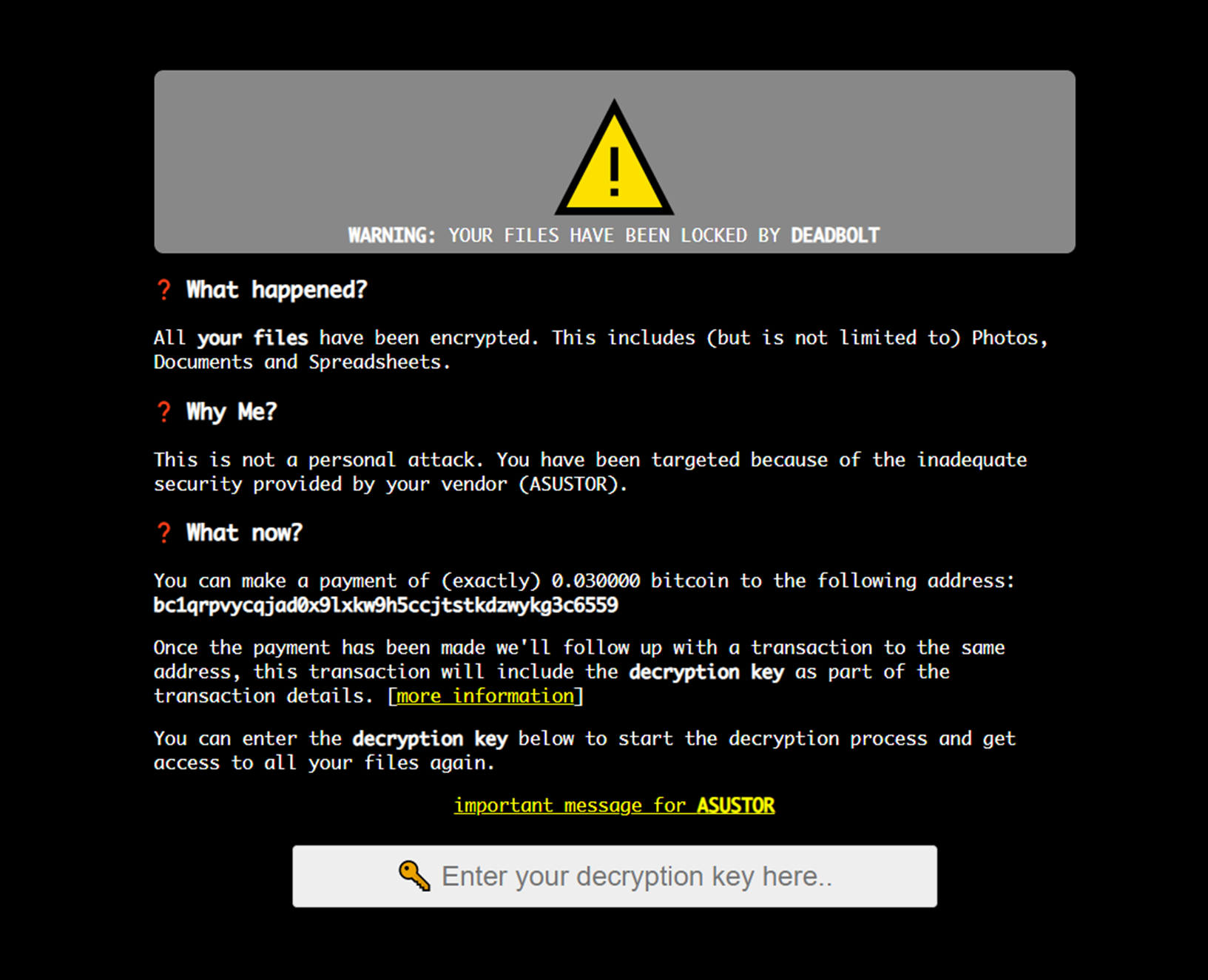
- If you want to return to ADM, you can do this in one of three ways. You can add backup.cgi after/portal/ in the address bar of your browser, you can hold the power button for three seconds to shut your NAS down and turn it on again or you may use ASUSTOR Control Center or AiMaster to restart your NAS.
![]()
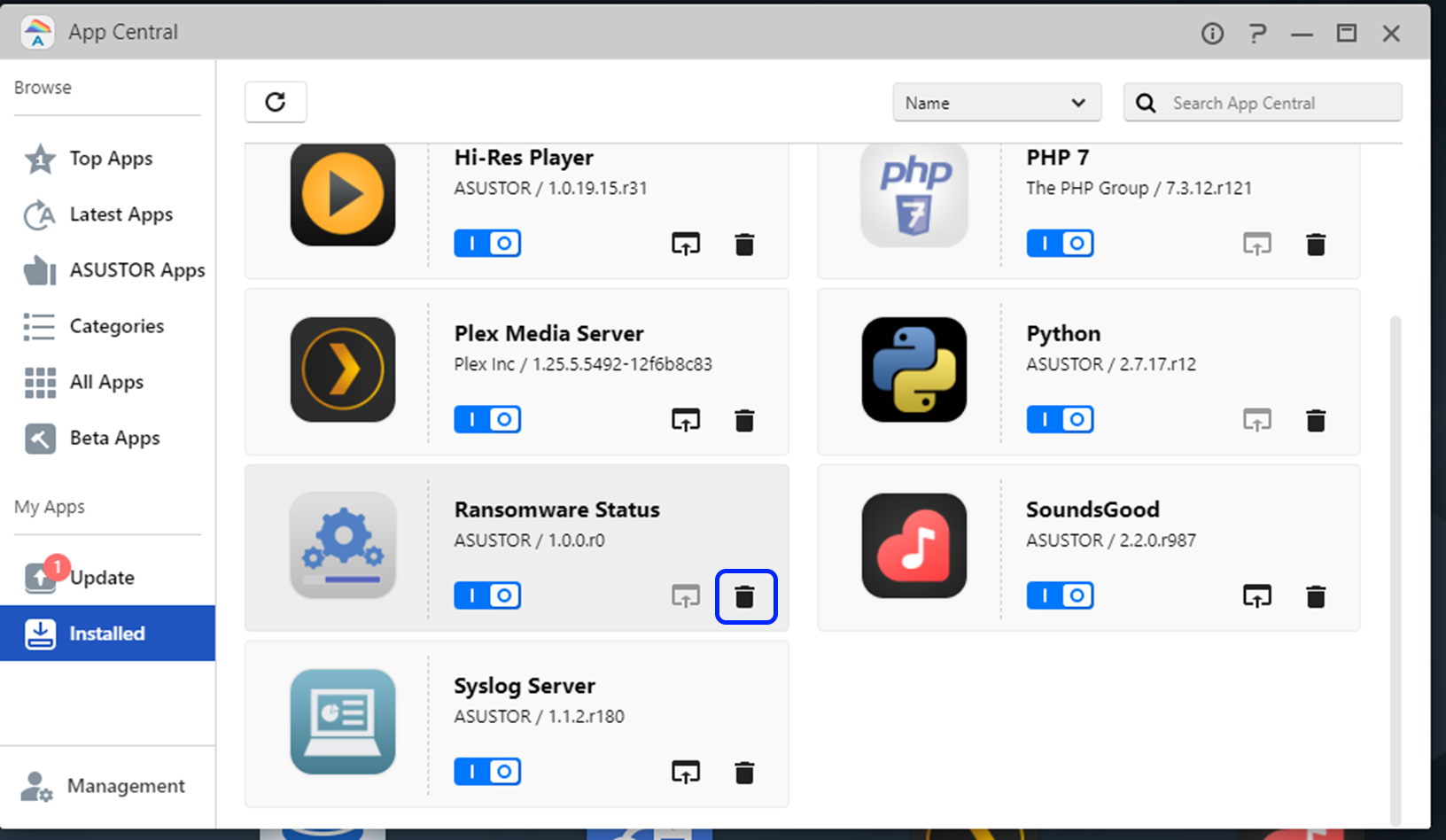
- Afterwards, it is imperative to uninstall Ransomware Status from App Central.
📧 SUBSCRIBE TO OUR NEWSLETTER 🔔
🔒 Join Inner Circle
Get an alert every time something gets added to this specific article!
This description contains links to Amazon. These links will take you to some of the products mentioned in today's content. As an Amazon Associate, I earn from qualifying purchases. Visit the NASCompares Deal Finder to find the best place to buy this device in your region, based on Service, Support and Reputation - Just Search for your NAS Drive in the Box Below
Need Advice on Data Storage from an Expert?
Finally, for free advice about your setup, just leave a message in the comments below here at NASCompares.com and we will get back to you. Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.
Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.

|
 |
WHY IS PLEX A BIT S#!t NOW? IS 2026 JELLYFIN TIME? (RAID Room)
Synology FS200T NAS is STILL COMING... But... WHY?
Gl.iNet vs UniFi Travel Routers - Which Should You Buy?
UnifyDrive UP6 Mobile NAS Review
UniFi Travel Router Tests - Aeroplane Sharing, WiFi Portals, Power Draw, Heat and More
UGREEN iDX6011 Pro NAS Review
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.





Jeez, I’m glad I found this channel. So much good info.
REPLY ON YOUTUBE
Any solution for the “Uninitialized” situation? I’ve updated the firmware on my NAS, so it’s not encrypting files anymore, but I still have the “Uninitialized” status. If I initialize the drive, it will erase all data. It’s amazing how little information ASUSTOR has on this attack.
REPLY ON YOUTUBE
My reason for buying this is also to remote access my media through jellyfin. Is using reverse proxy + cloudflare safe enough?
REPLY ON YOUTUBE
Thank you smartcodetch666 he helped me recover everything I lost within 24/7.
REPLY ON YOUTUBE
Tudo graças a☝️☝️por me ajudar a recuperar meu dinheiro
REPLY ON YOUTUBE
Scary stuff. I have a Synology, but I would never have used EZ Connect anyway just as I would never use Synology Quick Connect, so I imagine the brand doesn’t matter in my case.
I have ports 80 and 443 forwarded from the router to the NAS, and one Plex port (which I could probably stop, to be honest, as I use Jellyfin now, and I only really have Plex still running for comparison purpose), nothing else if memory serves. I only even forward 80 because everything is set to autoredirect to HTTPS and I’m too lazy to type https:// before URLs.
My setup is that 80/443 are forwarded to the NAS, and the LSIO swag container on the NAS reverse proxies the request to everything else. I’m not sure if that layer between would obfuscate or help with this etc… but I do this because I don’t want to have to connect my phone to a VPN every time I want it to upload a picture to Nextcloud or something.
REPLY ON YOUTUBE
Just got mine fixed mine through the help Bobutensil.
REPLY ON YOUTUBE
Just got mine fixed mine through the help Bobutensil.
REPLY ON YOUTUBE
https://www.youtube.com/watch?v=UVgq3ZnMfP8&t=184s
REPLY ON YOUTUBE
This ransomware attack made me almost lost my project folders????. I was then recommended to the name on my bio⬆️????, who helped to decrypt
REPLY ON YOUTUBE
This ransomware attack made me almost lost my project folders????. I was then recommended to the name on my bio⬆️????, who helped to decrypt
REPLY ON YOUTUBE
I’m thinking about using Microsoft ONEDRIVE and paying Microsoft to avoid all this mess in the future.
REPLY ON YOUTUBE
I was hit by deadbolt ransomeware some weeks ago. Finally I got the key and my files have been fully decrypted Thank you.
REPLY ON YOUTUBE
All praise to this dude ???????????? cos I never thought I’d have my files back
REPLY ON YOUTUBE
Trusting him ???????????? is what you need to have your files back ASAP
REPLY ON YOUTUBE
Lucky enough for me i got help from this guys on my bio????⬆️, my files were successfully decrypted and recovered
REPLY ON YOUTUBE
Lucky enough for me i got help from this guys on my bio????⬆️, my files were successfully decrypted and recovered
REPLY ON YOUTUBE
My files were all encrypted with this ransomware virus, I was then recommended to this guys on my bio *mouse*⬆️⬆️ who finally helped me to recover my files
REPLY ON YOUTUBE
My files were all encrypted with this ransomware virus, I was then recommended to this guys on my bio *mouse*⬆️⬆️ who finally helped me to recover my files
REPLY ON YOUTUBE
900Ethics for assistance
REPLY ON YOUTUBE
900Ethics for assistance
REPLY ON YOUTUBE
Is it affect NAS only, or somehow PC too ? Will be problem solved is i will use some linux distro instead of official OS ? or it more hardware problem ?
REPLY ON YOUTUBE
he was able to help me track my device from
dump later, thank you sir. recommendation
I strongly envy you a message if you have????????
any lost device you still need????????????????
????????????????????
REPLY ON YOUTUBE
Worker with a reliable hacker is what I think is all over the world and I recommend a hacker parfait who works with good heart and sincerity Dee_hack11 is in Seoul☝️☝️☝️
REPLY ON YOUTUBE
????????????Contact this hacker he is honest he helped me recovered my files I’m grateful
REPLY ON YOUTUBE
????????????Contact this hacker he is honest he helped me recovered my files I’m grateful
REPLY ON YOUTUBE
????????????Contact this hacker he is honest he helped me recovered my files I’m grateful
REPLY ON YOUTUBE
you should remind all people watching your vids that they need 2 everything.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now
REPLY ON YOUTUBE
Am able to contact #GLOCYBER and I showed him what has happened to my computer. He was able to assist and get my computer free from the virus.
REPLY ON YOUTUBE
I recommend you all to contact #GLOCYBER. He was able to help me recover all my encrypted files. Am glad I met him earlier.
REPLY ON YOUTUBE
It was through the help of #GLOCYBER that we ware able to get our money photos decrypt. The virus has held all the pics in the system.
REPLY ON YOUTUBE
I found a legit cyber professional. He is #GLOCYBER. he was able to help me fix and decrypt all my encrypted files. Thanks to him for his kindness.
REPLY ON YOUTUBE
I was dead in need of my computer. But I could not all because of this virus. I was recommended to #GLOCYBER and he responded to me and helped me fix my laptop.
REPLY ON YOUTUBE
Contacting #GLOCYBER was the best thing I did after my files got infected. He quickly decrypt all my files and get me free from the virus.
REPLY ON YOUTUBE
Am happy I could contact #GLOCYBER and he was able to help me remove all the virus. My exams files are free now.
REPLY ON YOUTUBE
Contacting #GLOCYBER was the best thing I did after my files got infected. He quickly decrypt all my files and get me free from the virus.
REPLY ON YOUTUBE
It was #GLOCYBER that was able to help me fix all my files and get them decrypt. He really did a great work and am happy I met him.
REPLY ON YOUTUBE
my files have been encrypted and I thought I would never use them again. My lecturer told me to reach #GLOCYBER and he was able to help me recover my files from the virus. Thanks to him.
REPLY ON YOUTUBE
*I was hit, so unplugged, shutdown, external USB backs fine. Plex user, was watching at the time no issues, went to update saver denied, then found the splash screen, no on reboot, water gapped on an independent switch no WiFi etc, it instantly goes to initialization. So save to assume the service themselves have been affected. Did safe shutdown. After some time I turn on everything then I found out I’ve been truly hit by deadbolt. I did as many research as I could and I found out that scott can actually decrypt the encrypted files. So I paid some money not upto what deadbolt team are asking, then he decrypted my files*
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you
REPLY ON YOUTUBE
You can message *SCOTTS_HACK*
REPLY ON YOUTUBE
You can message *SCOTTS_HACK*
REPLY ON YOUTUBE
Am cool with #GLOCYBER idea. He has much research on the virus and has helped a lot including my self.
REPLY ON YOUTUBE
Am glad #GloCyber could help me decrypt all my files. He did the best and I will forever be grateful. Thanks to him.
REPLY ON YOUTUBE
????I was so glad when I finally realized and get in touch with Glo Cyber while I used the contact above. He is indeed a genius and his skill are authentic. I rec. everyone to appreciate his efforts.
REPLY ON YOUTUBE
my cloud sera seguro de usas en estos tiempo !!
REPLY ON YOUTUBE
Is synology also been affected? I see Asustor, qnap, terramaster, but not synology or truenas, truenas i get it since you don’t use a their dedicated cloud, but synology? Does this mean that synology is more secure, or others less?
REPLY ON YOUTUBE
Anything major targeting Synology or do they seem any safer?
REPLY ON YOUTUBE
Has Ausustor come up with a PhotoRec solution like Qnap did yet? Are they even working on that? I have been checking their web site but haven’t even seen mention of this. :/
REPLY ON YOUTUBE
I really whant to know how and where dit it enter on the NAS, some deadbolted Nas have SSH down, 2FA and hard password (note 2FA activated is also needed for SSH). I also note that as i have ear, that no password was pirated (If it’s true that elimimate the bad or Not enoungh Strong password). Because i Always ear “it’s the user fault”. And i dont think that all true.
REPLY ON YOUTUBE
Scott also helped us too to retrieve our files
REPLY ON YOUTUBE
People keep talking about Scott. I think he is good. I will try him.
REPLY ON YOUTUBE
Someone recommended you ????and you also helped me recover mine too. You a genius indeed.
REPLY ON YOUTUBE
Rather than spending a long time trying to retrieve data and risk my NAS being connected to my laptop, I’d prefer to just wipe clean the two drives in my AS6302T NAS and lose the data permanently. Can this be done and the NAS setup anew with clean disks as if they had just been installed? I have a Raspberry Pi with a Linux OS set up on the network as an Apple Airprinter server. Could this be used with a disk caddy connected by USB cable to wipe the disks?
REPLY ON YOUTUBE
I was looking at buying a buying a nas but with everything going on should I just wait?
REPLY ON YOUTUBE
can anyone help me recover my files if not, format everything and resetting up my NAS?
REPLY ON YOUTUBE
This is a warning to avoid trying to recover from deadbolt Ransomwhere using USA based business found on Instagram, Whats app and this forum . They are know as “900Ethics” in the forums. They offer to restore deadbolt files for a total of $300, then when they have that, they then ask for another $100 for decryption software, then when thats paid they are for a delivery and gas fee of $150, then when thats paid, they say you have paid $550 but others have paid $1000 so 900Ethics say we should pay more also.. These guys are dishonest crooks and scammers..
REPLY ON YOUTUBE
Luckily I wasn’t infected. But I feel bad for those who were. I applied the patch and changed to all the recommended settings. Now I have a NAS disconnected from the Internet and only on my LAN. Like a glorified bunch of drives. This shows once again that anything connected to the internet needs adequate security. And has to be security patched almost forever. Is it worth it having an internet connected fridge or heating system or smart meter or electric/fuel cell car and so on. I have a lot of doubts. I’m going to try and ignore Solutionism.
REPLY ON YOUTUBE
I had accidentally knocked the power off of my NAS before the attack. I plugged it back in when I figured it out. Went 2 days before I logged in only to see the splash screen. I was able to get to the main screen and shut it down from my office. Still seems like I lost my data.
REPLY ON YOUTUBE
Question:
If I am getting the black ransomware screen and my ssh is disabled, how can I get into the interface to enable ssh and stop the encryption process.
Also how can we find how much data was encrypted?
Thanks!
REPLY ON YOUTUBE
Updated ADM and had a snapshot from 8/21. Didnt loose too much. Only problem is now one of my drives is showing bad. Going to scan after its synced
REPLY ON YOUTUBE
My ASUSTOR was attacked by Deadbolt on 2/22/2022 and 2/23/2022. I get the black deadbolt extortion screen and some but not all of my video files .mkv received the extra deadbolt extension. I can access my ASUSTOR via SSH by logging into admin. However, I do not have the permissions to kill the process and make the change to replace the Index.CGI. Is logging into root different than admin? And when “ssh -l root” it asks if I want to create a finger print type key. Is this what I should do?
you can use sudo -i command to switch to ADMIN mode [root]
How likely is it for a personal Laptop connected to the internet (obviously) being attacked with Ransomware like Deadbolt? Are there any precautionany steps to take to mitigate such risk?
Yes, NAS brands might not be as fast as Windows in order to create a patch. But all software/hardware companies face similar threats to hackers that could use ransomware or other way of harm.
To keep you data safe you should always have a backup. Simple things like Firewall and Antivirus would slow down/ identify majority of suspicious activity.
I have my 4 drives that are in RAID5 connected to an Ubuntu based PC. The volume mounted itself, there was nothing to be done.
As I feared, most of my files have been encrypted (about 80%). The worst is, the most important are in that category.
Anyone has any clue how this could be encrypted?
REPLY ON YOUTUBE
It’s great news that Asustor came back so quickly with solutions. I am pleasantly surprised they went to the lengths they did to help with the restoring access to ADM to effected customers and then with a decrypting solution. When compared to QNAP, this is a step up on their solution. I guess the reputational damage would be huge, so they did what was right by their customers.
By the way, I don’t represent Asustor, just giving credit where it’s due.
The advice from Asustor to protect your device from these types of attacks is good but could be further extended to other controls they failed to mention.
Since getting my Asustor 6204T a few years ago, I noticed the “Auto Black List” was recording unrecognised attempts on my device (If don’t use Auto Black List, then you should, I believe it’s essential). When I looked into the source of these attacks, they came from China and USA.
This prompted me to use the “GEO IP Database – by Asustor” (app) which works with the “Black List” in “ADM Defender”. This allows you to Black List continents and regions of the world. In my case I blocked the entire world leaving only my country as permitted access. If I am not travelling abroad then there is no need to provide more than the minimum access. This goes a long way to protecting your device as this hugely reduces the likelihood of attempts on your device. Since then, no unexpected attempts have ever been recorded. (NOTE: If you ever need remote support from Asustor, then you will need to temporarilly permit Taiwan, to allow them access).
Another prevention measure should be – permanently disabling EZ-connect and Auto Port Forwarding (UPnP) in your router because of the security vulnerabilities they present. Ultimately these features are provide convenience for non-tech savvy users.
I avoid both these as you can still obtain remote access with a manual setup in ADM and your router.
To manually assign ports in ADM go to “Settings>Manual Connect>EZ Router>Port Forwarding”. There is no need to use “EZ-Router Setup” which does the setup for you automatically (this kind of works like UPnP but in your NAS).
On the router side, instead of using UPnP, manually assign port forwarding, which is technically safer. This can be found under “Wan>Port Forwading” in most Asus routers.
I knew very little about ports, until I learned about the risks of not knowing about them. If this doesn’t quite make sense, you will need to do some research on the vulnerabilites of UPnP, then learn about ports, how they work and how to implement them manually.
I wrote this because I once lost all my data, so I know how those of you who that have been affected feel – it’s devastating!
The lesson I learnt from that was to get a robust NAS, which is why I have an Asustor NAS. I implemented a robust back up plan (x3 copies – Raid 1, plus two backups) and utilised all the security measure made available on my NAS. To be frank, Asustor provides enough security measures, but unfortunately, there is a bit of learning and experimentation required to understand and implement them effectively.
Hope this is of some help.
I have ASUSTOR NAS AS1002T which has been hit with Deadbolt. But I have never seen or used AppCentral or Plex Server. Are these only valid for newer models of ASUSTOR NAS?
REPLY ON YOUTUBE
I got hit with this Deadbolt Ransomware a few days ago. On 24th morning, my internet was down. When the internet came up, I logged on to my laptop and tried to access the ASUSTOR NAS (AS1002T) – I had earlier mapped different volumes on the NAS to different drive letters on the laptop. When I clicked on a mapped drive, I could not access it. Control Centre did not display the device. I thought it has something to do with the internet going down, so I powered down the NAS (may have pressed the button longer than 3 secs). After that the Control Centre displayed the device but with the “Uninitialized” status.
A few questions:
1. If I do as the ASUSTOR support suggestions and update the ADM, and bypass the “Uninitialized” status, will the ransomware encryption (that had stopped earlier because of shutdown), start up again? Do I have to do something to stop that?
2. Will I see the Black screen message after the ADM is updated? If so how to bypass that and access the different volumes to check the status of the files?
3. At any stage after the ADM update, if I decide that I need to pay the ransom in order to recovery my data, is it possible? Or, the update will do away with that avenue?
4. Once I am able to see my files, do I need to immediately copy them to another disk drive (external drive attached to my laptop)? If I delay that copy for a few days, will the situation get worse? If so, I need to buy an external drive before I attempt to update the ADM. BTW. I have photos and videos of past 25 years on the NAS, and I do not have a backup of the data for last 3 years, and therefore recovery of as much data as possible, of the last 3 years, is important to me.
5. If I decide to pay the ransom, how do I pay in Bitcoin? I have never dealt in bitcoins before. BTW. I live in Canada.
Can the good folks who are knowledgeable on this issue be kind enough to provide some answers, please.
REPLY ON YOUTUBE
I would like to see a reply to this post. I ripped the power out of my Asustor when I realised what the noise was. I am too afraid to boot it incase the encryption restarts and I can’t quickly kill the process (having never touched ssh in the past). I am assuming my AS5304T (1 Volume, RAID5) is uninitialised.
* If I reboot my “uninitiallised” NAS will the encryption continue?
* Will I be able to roll back snapshots?
An update was published to solve the uninitialized issue: https://www.asustor.com/en/knowledge/detail/?id=6&group_id=630
REPLY ON YOUTUBE
What are the steps to pay the ransom. Yes I know I’m an idiot I didn’t have a backup. There are 10 years of picture of my kids that mean a lot to us. Once the decryption key is received. Can it be entered with the NAS not connected to the internet? Once it decrypts will it encrypt the files again or do I have time to move my files
I was able to get my NAS unit back on line following the instructions from 1 to 3 however my files all show the deadbolt extension. I tried to rename it back and run it but no luck’. Question I download the Ransomware Status app but Not sure how to use it. Install instructions are not clear.
How do I use the Ransomware Status app to decrypt my files.
FIXED Please read. A tech was able to get all data back! had the “Unitialized” situation. setup was 4 disks in RAID 10 (2 disks striped and then mirrored to the other two that were stripped. Just take disk one and use “EaseUS” to find the hidden data. Some of it was in folders with correct names and some were not but they did have the file names. I have no idea why this worked with only one disk and still sifting through the files (1000+) to see if they all work. So far so good. I dunno I can’t rap my head around why recovering from only one disk got this much information back. *I never use EaseUS btw. I have RapidSpar but the tech used it. JUST TRY IT! OR I DON’T CARE USE ANY RECOVERY SOFTWARE ON ONE DISK. I really hope this helps someone!
REPLY ON YOUTUBE
Asustor has released the instruction how to solve. But it is not clear and no FAQ etc. I regret to death to buy this crap.
REPLY ON YOUTUBE
Must admit this was a good video about a bad topic
REPLY ON YOUTUBE
Has anyone paid the ransom and confirmed they got their data back?
REPLY ON YOUTUBE
For those who want to know, there is a bit of an update on the “stuck on un-initialised” screen – New ADM version can actually bypass now for some users so you can access ADM and start to see how many files have been encrypted by deadbolt. Hope like me, many got off lightly (only volume 1 effected, but my drives were single volumes not in RAID)
REPLY ON YOUTUBE
i would love to see a synology version of this video
REPLY ON YOUTUBE
After the attack, we shut down the server with AiMaster. When we opened it again, we got a “Uninitialized” warning in the Control Center application. What are we supposed to do? Not all of our data was encrypted. We do not want our data to be deleted. What should we do?
REPLY ON YOUTUBE
Sadly I am also affected, and I feel sick and violated. Unlike others, I do not entirely blame Asus but it makes me sad that there are some very clever people in this world who’s morals are such that they feel it is okay to use their skills to take advantage of innocent people. My Asustor has (had?) backups from my PC and from my wife’s MacBook, all my music and over 100,000 digital images (20 years’ worth). I suppose the good news is that my music and all the digital images are safely backed up to an old NAS; I have just checked and all the files are safe. The backups can be rebuilt. I did the safe shut down of my affected NAS, so I will leave it off until the dust settles and advice emerges as to the best way forward.
REPLY ON YOUTUBE
How does one get effected in the first place❓ Is it a user clicking or downloading links from unknown sources or emails that leads to this❓
REPLY ON YOUTUBE
Fucking Seagulls again. Bastards shit all over everything worse than Pigeons.
JUST finished transferring a hard drive full of data over to my brand new Asustor NAS that I bought in a large part due to the videos on this channel. We’re going to see if I’m affected here soon after I get all the information I need and have a run at shutting down the offending processes if I log into that black screen. Haven’t even had time to setup a backup of the NAS yet but also haven’t had time to enable remote access or install Plex yet so I’m hoping I haven’t been hit. Wish me luck
REPLY ON YOUTUBE
I just found out that I have been attacked by the Deadbolt Ransomware. And ALL my files have been effected. Is there anyway to fix this? I have no backup all. Everything I have years and years of data all in my Asustor. This is such a shit situation and Asustor needs to be held accountable!
REPLY ON YOUTUBE
Everything you said is spot on. Especially the uninitialized issue.
REPLY ON YOUTUBE
My Asurtor system was attacked Monday. Luckily I had done a backup last Thursday so I only lost a day worth of work and still have all my files. All I did was reformatting the hdd erasing and going over 7 times to make sure all files were deleted. Back up and a good malware program can save you a lot of $$ and down time..
REPLY ON YOUTUBE
Will the Asustor hardware run any different Linux OSs? If I just want to build a NAS device can’t I do that with a server version of a different Linux OS? Most of them have some kind of GUI. Just a thought.
REPLY ON YOUTUBE
Its a really really crap day.
REPLY ON YOUTUBE
There are so many products and boxes in the studio that the presenter will become invisible in a few months 😉
REPLY ON YOUTUBE
I think that a good idea would be that all the files on the NAS are read-only (maybe with some exceptions for logging etc) and if for any reason the device needs to change them, there could be an option to ask you to authorize it.
REPLY ON YOUTUBE
Is there risk of contagion if I remove the drives, attach them to an external enclosure, then try to view them on my PC? Or is this an Asustor-hardware-only ransomware?
REPLY ON YOUTUBE
When I got my AS6510T I turned on all those services just because I wanted to see if there were security issues with them enabled. I had not transferred any data to the NAS yet so there was no data risk. I monitored the logs and within a few days I was getting attempted access from most of the countries where attacks originate like China, North Korea, Russia… etc. I shut down all remote access services and I have not seen a single access attempt since. I think Asustor needs to reassess their security model
REPLY ON YOUTUBE
How do I know what file system i’m using? Is it ext4 or btrfs? I don’t know
REPLY ON YOUTUBE
I pray I never find anyone responsible for such an attack or I’ll break every bone in his fingers at least twice.
REPLY ON YOUTUBE
I have a Synology but would this affect a backup on an external drive plugged into the Nas? Assuming that this same type of attack might be implemented on Synology Nas systems.
I’m going to be setting up a backup on my Synology with an external drive so I’m curious if that would be a version of back that you are talking about to help recover your data in this case?
REPLY ON YOUTUBE
Came across this video whilst reading up on the attack, I have an Asustor, not sure yet if its been effected, as I only accessed it remotely via Android login from work to shut it down. I will be checking it later using these tips and wanted to thank you in advance for your efforts. Hoping all data is OK, and if it is i will be changing all the ports and following your suggestions – Hope everyone else is OK too! Good luck everyone
REPLY ON YOUTUBE
Well Im screwed then, as I have a RAID5 and I shut down the machine as soon as I saw the message…
REPLY ON YOUTUBE
20 Years of photos deadbolt locked. Wedding, birthdays, births, holidays. Memories potentially lost forever. I’m beyond gutted and really upset. Of course, I am learning the painful way that if I ever get them back, to have a secondary backup but more than that I am furious as Asustor. If Qnap got hit last month, did they not consider warning the rest of us? I didn’t know about qnap attack until it happen to my asustor.
Have any Qnap owners got their data back without paying the ransom? I can’t afford $1100 without even the guarantee of the key working.
REPLY ON YOUTUBE
Hacking is a form of terrorism. Capital punishment is the only way to stop them.
REPLY ON YOUTUBE
I got it hit too but all able to access via network share and all backed up all my file so I’m not very worried but the day after my system file got encrypted I guess prolly I did force shutdown, since greeted to initialized the NAS
REPLY ON YOUTUBE
Several users affected by Deadbolt Ransomware did not even enable EZConnect. Plex is one of the suspect.
REPLY ON YOUTUBE
I agree with the other comments, I’d like to see a video on securing a Synology NAS. I figure some of these steps would work for Synology. I just wanna keep my home NAS secure.
REPLY ON YOUTUBE
Always backup your data separate from your NAS
You can never be to careful
REPLY ON YOUTUBE
Hi I followed the advice to clear the visus. However changing the files to remove the .deadbolt is not working
REPLY ON YOUTUBE
Gladly I never had remote access or ez-connect enabled and never used plex on it, also when this all started I happened to have my Asustor turned off. With that said, powered on, immediately switched off SSH-connection and swithed https-protocols, seems all good for me luckily. Also, I am using a VPN on my router.
REPLY ON YOUTUBE
Only I got notified of your upload I’d have never of known, thanks lad.
I haven’t been effected, it’s now shutdown.
REPLY ON YOUTUBE
I am on QNAP, but this is very usefull
REPLY ON YOUTUBE
Any updates on this issue?
REPLY ON YOUTUBE
My por-, I mean, my legal documents!
REPLY ON YOUTUBE
Make Hacking like this a Capital Offense, and treat it like terrorism.
REPLY ON YOUTUBE
How do I know what file system i’m using? Is it ext4 or btrfs? I don’t know
REPLY ON YOUTUBE
Does Snapshot on Synology prevent loosing all your Data ? – Does it help to recover encryptet files or would the snapshot files encrypted too ?
REPLY ON YOUTUBE
Can you make a similar video for Synology users focused on preventing this sort of attack?
REPLY ON YOUTUBE
I was thinking to buy an Asustor NAS, it seems not a good idea at this moment…
REPLY ON YOUTUBE
Should I as Synology owner be worried?
REPLY ON YOUTUBE
Thanks for the video! Maybe I was saved by using an OpnSense router that hasn’t Upnp
REPLY ON YOUTUBE
Yep, I got it yesterday thought my NAS was making a lot of noise but had to go to work immediately and forgot to check after, today found my whole NAS locked out. Immediately shut it down, just waiting for Asustor now to come with some more information 🙁
REPLY ON YOUTUBE
Just a reminder that your dealing with criminal and non-moral people who have no honor. Do not send money , if you send money your a put on a list of naïve people and the will attack again knowing your paying. Just be patient Asustor will find a solution. Also i can access my asustor with my phone app. So my plan is to wait for update and update with my asustor phone app. #iloveseagulls
REPLY ON YOUTUBE
Yikes. I feel a bit freaked out and I don’t even have an Asustore. Good luck to everyone!
REPLY ON YOUTUBE
high pass filter……that is all.
REPLY ON YOUTUBE
Apologies for the slightly rushed nature of this video. The Deadbolt ransomware attack on Asustor NAS systems largely kicked off yesterday afternoon and I have been pretty much non-stop on this since then (pulling an all-nighter like the old days!) and assisting a bunch of users, as well as finding out as much as I can and being as noisy as possible to alert any users left who might be targetted. As the video suggests, I will be updating the article on this as more info arrives and if a workable solution appears (I have a deadbolt affected Asustor arriving with me later in the week), I will make a video on this. Otherwise, night night everyone, I am bloody shattered! #Ihateseagulls
REPLY ON YOUTUBE