New Reports of Deadbolt Ransomware Attacks on QNAP NAS via Photo Station
It would appear that the Deadbolt ransomware attack that has been a persistent pain for QNAP (and other NAS brands) in 2022 continues to remain current, with new reports emerging of further attacks of NAS systems in September 2022. The vulnerability that has been reported to be being exploited is in the QNAP Photo Station application and although a day one patch for the application for all current use QTS software systems has been issued, it has still resulted in users being hit in this new wave of attacked by the deadbolt ransomware group. Although the scale of this latest attack does not match that of previous attacks by the group, it is worth highlighting that the encryption of how this ransomware deploys and presentation to the user upon execution have changed a little, so even if you are not affected, it might still be worth getting clued up on this. In this article, I will cover everything that is known so far about this Photo Station vulnerability that was exploited, why deadbolt is still a thing, how it attacks, what you can do to avoid it and what can you do if you have been hit.
How Does Deadbolt Attack QNAP NAS?
Deadbolt Ransomware’s methodology in attacking your system has not changed much at all since its first attacks. We will touch on in a bit about why deadbolt is still around and the nature of software updates vs vulnerabilities, but for now we can discuss this specific instance. A vulnerability was found in Photo Station for QNAP NAS QTS/QuTS this week and this vulnerability created a small hole in the access control of the NAS that could be used to exploit as an attack vector for ransomware to be executed. It would still require your NAS to be setup in a weak remote access state (i.e. you allowed internet access to your system without sufficient layers of encryption, protection and/or authentication, such as a VPN, Firewall or disabling UPnP – will touch on these later) in order to reach ‘photo station’, but if it could, it could then execute the command to the QNAP NAS to encrypt it’s contents, create a ransom text not and modify the login screen to show the deadbolt warning. This one:
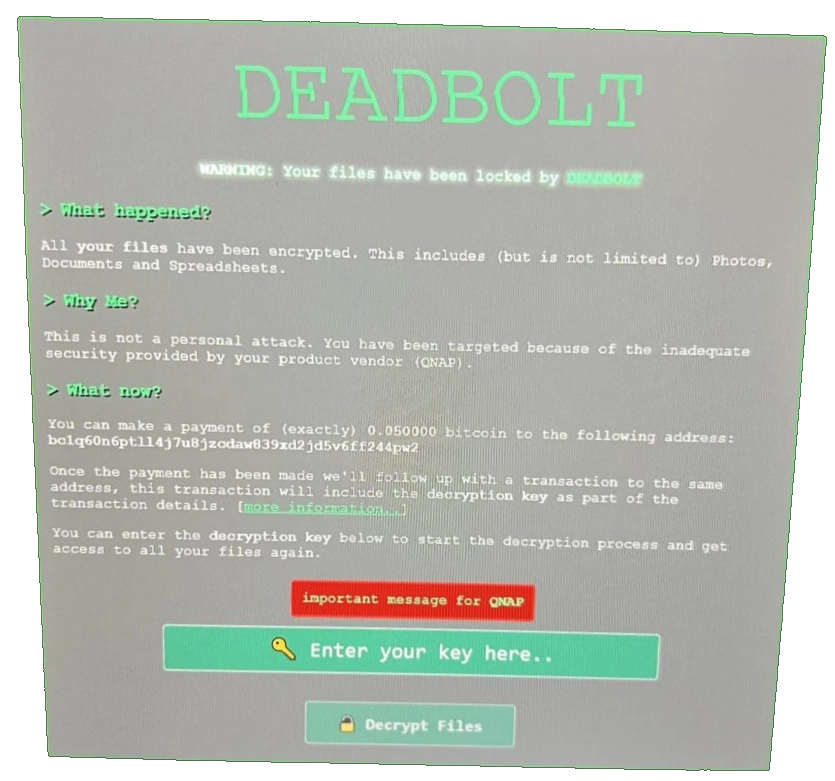
QNAP highlighted this vulnerability on their security advisor page, here under ID QSA-22-24 and state that they detected a new DeadBolt ransomware campaign on the morning of September 3rd, 2022 (GMT+8). The campaign appears to target QNAP NAS devices running Photo Station with internet exposure. This is not via the myQNAPCloud services, but rather users allowing remote access with open router ports, but no VPN or restrictive access rules in place. QNAP issued the following statement:
QNAP Product Security Incident Response Team (QNAP PSIRT) had made the assessment and released the patched Photo Station app for the current version within 12 hours. QNAP urges all QNAP NAS users to update Photo Station to the latest available version. QuMagie is a simple and powerful alternative to Photo Station. We recommend using QuMagie to efficiently manage photo storage in your QNAP NAS. We strongly urge that their QNAP NAS should not be directly connected to the Internet. This is to enhance the security of your QNAP NAS. We recommend users to make use of the myQNAPcloud Link feature provided by QNAP, or enable the VPN service. This can effectively harden the NAS and decrease the chance of being attacked.
Additionally, this warning that is displayed to the end user also has an additional note directed towards QNAP themselves that highlights that they are willing to share the nature of the exploited vulnerability for 5BTC. See here:
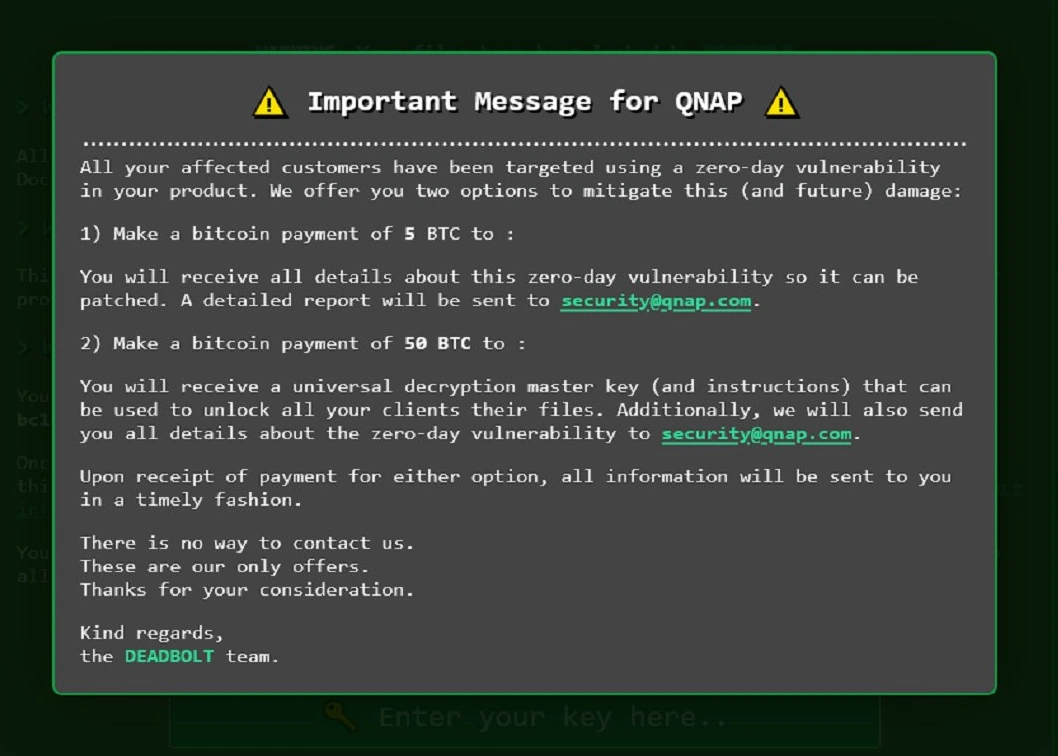
Now, as nefarious and immoral as you might find the Deadbolt ransomware attackers and what is being done here, we also have to put the spotlight on QNAP. In their defence (I will go into more detail on this later on in the article), they are a software developer that provides a range of tools and services to maintain many backups of your data, hugely configurable security options/variables to their system, a remote access cloud portal that acts at a checkpoint in myQNAPCloud, they provide regular updates to their software/service applications with automated update options and they provide a public security advisory panel and can only remain a single step ahead of vulnerabilities. HOWEVER, when vulnerabilities are found in their platform and services (even if patched out – which relies on users remaining updated), it continues to bring into question the strength, depth and attention to detail of their security teams during development. It is true that QNAP is not the only brand that has been successfully targetted by deadbolt (see Asustor HERE and Terramaster HERE) as well as not being the only brand targetted by malware (see Synology Synolocker HERE) , but QNAP still seems to persistently be the one that gets hit most. Ultimately, ARE QNAP NAS SAFE? We discussed this over on the YouTube channel back on Febuary 2022
PSA – GET YOUR BACKUPS IN ORDER!
Before you even go one paragraph further, I have a simple question for you – do you have a backup in place? If yes, then carry on to the next part. If not, and I cannot stress this enough, GET ONE NOW. The time you are spending reading this you could be susceptible to data loss in about 10 different ways without even factoring in ransomware (Power failure leading to hard drive corruption, Malware from a slightly iffy google search this morning, cloud storage provider going bust, OS failure on your device, etc). In this day and age owning a sufficient data backup is as sensible as buying a raincoat or looking both ways when you cross the street – you don’t do it because you like rain or like looking at cars, you do it because they are peace of mind, they are a safety net, they are for caution in case of the worst. It is a bit tenuous, but owning one or multiple backups always make me think of this quote from Shawshank Redemption by Stephen King:
“There are really only two types of men in the world when it comes to bad trouble,” Andy said, cupping a match between his hands and lighting a cigarette. “Suppose there was a house full of rare paintings and sculptures and fine old antiques, Red? And suppose the guy who owned the house heard that there was a monster of a hurricane headed right at it. One of those two kinds of men just hopes for the best. The hurricane will change course, he says to himself. No right-thinking hurricane would ever dare wipe out all these Rembrandts, my two Degas horses, my Jackson Pollocks and my Paul Klees. Furthermore, God wouldn’t allow it. And if worst comes to worst, they’re insured. That’s one sort of man. The other sort just assumes that hurricane is going to tear right through the middle of his house. If the weather bureau says the hurricane just changed course, this guy assumes it’ll change back in order to put his house on ground zero again. This second type of guy knows there’s no harm in hoping for the best as long as you’re prepared for the worst.”
Get a Backup in place
Why Is Deadbolt Ransomware STILL HAPPENING?
First and foremost, it is INCREDIBLY IMPORTANT that users understand the risks of allowing remote access to their NAS system (not just QNAP, but ANY NAS Drive) without specific port discipline, a VPN, a Firewall and/or custom admin credential/enabling. In the case of this recent resurgence of the ransomware attack that was executed by the Deadbolt group, it is important to note that it is made possible by two KEY VARIABLES! Weaknesses and Opportunity.
Now, with weakness, this stems from a vulnerability is found in a software/application – not uncommon and ALL software can only be one step ahead of those looking to break it. to give it a little context. In 2022 there have been 671 vulnerabilities found in Microsoft software services, 22 in Synology NAS software services and Apple iOS has had 79. This is not to besmirch their software/platforms, but ultimately the minute a software maker releases a new version/update (often to plug vulnerabilities that were found), the nefarious will then get to work on finding vulnerabilities in which to exploit for financial gain. That is why software updates are so incredibly important! However, a weakness is no good without access and/or an opportunity.
An Opportunity (in the context of ransomware and malware attacks) can largely be defined as an open door (no matter how small) that can be used to inject a command to the NAS as an administrator (eg. encrypt everything). THIS is where one of the biggest misconceptions (and indeed finger-pointing) happens when an incident of ransomware, malware or data loss occurs. A vulnerability in a software platform (especially when the bulk of software in common use today is built on Linux universally) is only any use when it can be executed. So, in the case of a NAS vulnerability, such as the Photo Station vulnerability that has been identified, it can only be exploited if the NAS user has allowed external access to their NAS via the internet. This access may well be behind user login credentials, but lacked the barrier of a VPN, a Firewall setup with amply restrictions, trusted access credentials/identity, limited/zero admin control, 2-step verification, specific port access to a GUI and many other restrictions/limitations/authentications that can be enabled. Not all these hurdles and/or barriers are as effective as others (with some vulnerabilities being built on backend access), but all/most of these should be considered when allowing any form of external access to your NAS outside of your local network. Equally, you NEED to become more acquainted with your router! Get into your router and reactive UPnP settings, as this eliminates the possibility of applications on your NAS inadvertently opening ports remotely without your direct knowledge.
- Disable the Port Forwarding function of the router: Go to the management interface of your router, check the Virtual Server, NAT, or Port Forwarding settings, and disable the port forwarding setting of NAS management service port (port 8080 and 433 by default).
- Disable the UPnP function of the QNAP NAS: Go to myQNAPcloud on the QTS menu, click the “Auto Router Configuration,” and unselect “Enable UPnP Port forwarding.”
Do keep in mind though that you might well be using external UPnP services on your router for other things in your home or office environment.
What is UPnP Port Forwarding?
Universal Plug and Play (UPnP) is a way of quickly forwarding the ports in use to other devices on a network automatically with one setting change and no additional configuration needed. UPnP Port Forwarding is widely used by many network devices, allowing them to communicate with each other more efficiently and to automatically create workgroups for data sharing, among other applications.
Is UPnP Port Forwarding safe?
UPnP is not a secure protocol. It uses network UDP multicasts, no encryption and no authentication. Since UPnP is not authenticated, one device could request port mapping for an another one. Hackers can abuse UPnP to attack through malicious files to infect your system and gain control. Despite its convenience, UPnP may expose your device to public networks and malicious attacks. It is recommended that your QNAP NAS stay behind your router and firewall without a public IP address. You should disable manual port forwarding and UPnP auto port forwarding for QNAP NAS in your router configuration
How Many QNAP NAS Users Have Been Affected by Deadbolt?
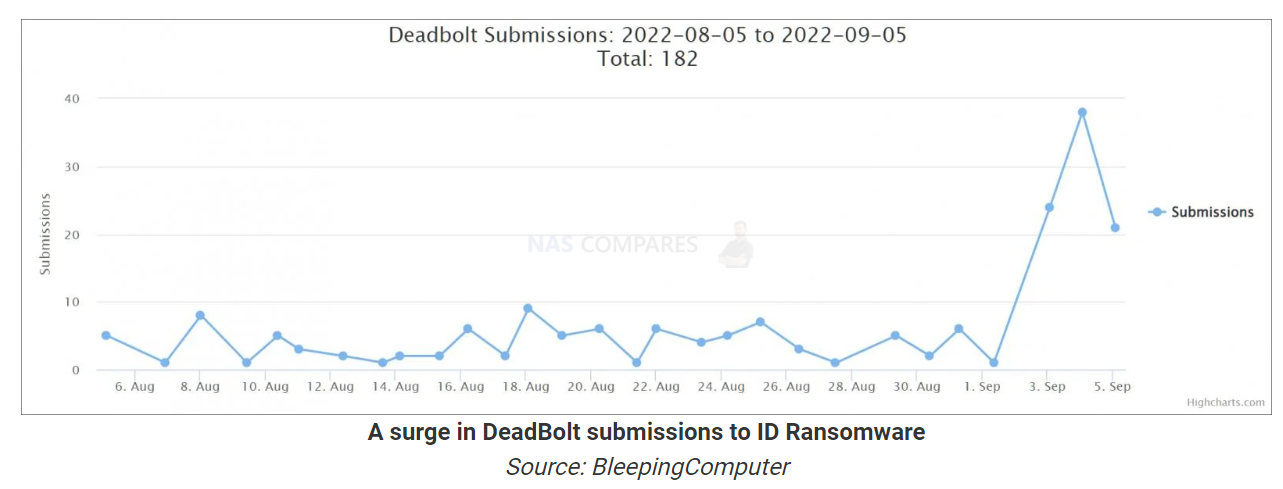
Getting the numbers on how many users have been impacted by this recent attack by the deadbolt group on QNAP NAS devices is exceedingly hard to identify. On the one hand, as this photo station vulnerability has been identified and effective in QTS 5 it has the potential to be high, however, it still heavily relies on having a system set up in a comparatively weak remote access configuration AND having a specific application with access credentials running. This is further reduced in scope as the Photo Station has been largely overtaken in use by QNAP users by the AI-powered QuMagie application. Still, the Photo Station application still has several ‘professional photographer’ services/structural qualities that keep it in use. The Bleeping Computer website identified 182 submissions to the ID Ransomware site reported for ‘Deadbolt’ (which requires uploading an encrypted file, attacker address and/other identifies for clarification of an attack type) with a spike that started on the 3rd of September (necessitating the patch o nthe 4th Sept). How many of the previously submitted reports in August 2022 were related to this photo station vulnerability (at that point unidentified) and how many were repeats by any one user or related to a QNAP NAS that was not updated since the early phase of the Deadbolt ransomware attacks of Jan 2022 cannot be confirmed. Nevertheless, these are still noticable numbers and can comfortably be classed as victims hitting the 3 digit mark.
Source for the below graphic and article – https://www.bleepingcomputer.com/news/security/qnap-patches-zero-day-used-in-new-deadbolt-ransomware-attacks
Alternatively, you can use server/internet service monitors such as censys to search for reported text that is used in the Deadbolt ransomware note. However, this is not the most precise and only further highlights that only QNAP themselves and Deadbolt know the extent of impact of this campaign. Unlike the original Deadbolt attacks of Jan 2022 of QNAP devices, research and strategic advisors at Unit42 noted back in May ’22 that the attack/injection of the ransomware and how it is presented to the user changed (though seemingly still using the same exploit that remained in systems that were not updated, therefore still vulnerable to the exploit in older QTS/QuTS versions and/or continued use in weak internet-facing access scenarios:
Unit 42 is observing a new wave of attacks of the Deadbolt #ransomware targeting QNAP NAS devices involving a new lock screen with updated JavaScript. Cortex Xpanse discovered ~3000 instances of infected devices. Details at https://t.co/uj0TOqACxu pic.twitter.com/RmSzZOAsTq
— Unit 42 (@Unit42_Intel) May 16, 2022
There has been no substantial analysis of the latest version of DeadBolt, but Unit 42 said in it’s May summary that the ransomware program made some significant changes since the March campaign. Specifically, the DeadBolt program now uses revised JavaScript code with a stronger SHA-256 implementation, building on the previous, lower-level ‘SubtleCrypto’ cryptography. Unit 42 researchers said this was likely changed to a stronger standard to accelerate the key verification process and also to ensure the verification works on browsers that do not support the SubtleCrypto API.
What Should You Do To Protect Your QNAP NAS from Deadbolt Ransomware Attacks?
If you are using the QNAP Photo Station application, then you need to suspend using it until you have updated to the latest version. It is worth highlighting again that this vulnerability will ONLY affect you if you have your QNAP NAS directly connected to internet access services (i.e NOT using a VPN or the myQNAPcloud link service). Updates for Photo Station have been issued for QTS 4 and QTS 5 on the brand’s official app portal of your NAS and directly downloadable from their official website:
- QTS 5.0.1: Photo Station 6.1.2 and later
- QTS 5.0.0/4.5.x: Photo Station 6.0.22 and later
- QTS 4.3.6: Photo Station 5.7.18 and later
- QTS 4.3.3: Photo Station 5.4.15 and later
- QTS 4.2.6: Photo Station 5.2.14 and later
Outside of QNAP Photo Station, it is incredibly important that users maintain a secure layer/barrier between your NAS and your external internet connection. To protect your NAS from the DeadBolt ransomware, QNAP strongly recommends securing your QNAP NAS devices and routers by following these instructions:
- Disable the port forwarding function on the router.
- Set up myQNAPcloud on the NAS to enable secure remote access and prevent exposure to the internet.
- Update the NAS firmware to the latest version.
- Update all applications on the NAS to their latest versions.
- Apply strong passwords for all user accounts on the NAS.
- Take snapshots and back up regularly to protect your data.
Now, QNAP myQNAPCloud services are not the same as just opening your NAS connection from LAN only to LAN+Remote. myQNAPCloud creates a connection between the NAS and the QNAP access servers via a secure portal (with encryption, SSL certificates and other configurable options that can prevent interception via this tunnel). Then, if you want to create a connection remotely with your NAS, you do so via the QNAP access server – as opposed to the directly NAS connection. This DOES result in a drop in file transmission speeds remotely (as you are moving through an additional transit point), but increases security and authentication substantially. The alternative to this would be to use restrictive/specific open of ports on your router AND recommended use of a VPN – which is definitely a valid and ‘best of all worlds’ solution, but a little more technically advanced than many users are able to configure effectively/securely). If you want to set up a remote myQNAPcloud connection, you need to:
- Log on to QTS as an administrator.
- Open myQNAPcloud.
- Disable UPnP port forwarding.
- Go to Auto Router Configuration.
- Deselect Enable UPnP Port forwarding.
- Enable DDNS.
- Go to My DDNS.
- Click the toggle button to enable My DDNS.
- Do not publish your NAS services.
- Go to Published Services.
- Deselect all items under Publish.
- Click Apply.
- Configure myQNAPcloud Link to enable secure remote access to your NAS via a SmartURL.
- Go to myQNAPcloud Link.
- Click Install to install myQNAPcloud Link on your NAS.
- Click the toggle button to enable myQNAPcloud Link.
- Restrict which users can remotely access your NAS via the SmartURL.
- Go to Access Control.
- Next to Device access controls, select Private or Customized.
Note: Selecting Private allows only the QNAP ID logged in to myQNAPcloud to access the NAS via the SmartURL. Selecting Customized allows you to invite other QNAP ID accounts to access the device via the SmartURL. - If you selected Customized, click Add and specify a QNAP ID to invite the user.
- Obtain the SmartURL by going to Overview.
The final thing to do is to have two applications running on your QNAP NAS regularly. Malware Remover and the QNAP Security Counselor. The Malware tool is for scanning your system for existing threats that may have been installed/engineered inside your system. It then isolates, quarantines as appropriate and removes. The Security Councilor tool is designed to periodically check the security of your entire system, find any potential for an opening that a vulnerability could be exploited via, then makes recommendations on how to close it. This latter tool can be configured via a number of pre-set profiles that scale in severity, but can also be set to custom variables too. These (alongside having updates on both the QTS/QuTS OS and apps via the app center set to automatically download and install) should be among the FIRST things you set up on your QNAP NAS.
It is also REALLY important to note that these applications analyze and identify KNOWN vulnerabilities. They are not omnipresent and, much like in the case of the Photo Station vulnerability that has been identified here and a day 1 patch issued, until it IS recognized as a threat/attack-vector, it will not be seen
What Should You Do If Your QNAP NAS was Hit By Deadbolt Ransomware?
Unfortunately, as it stands, there is little resolution in place to reverse Deadbolt ransomware encryption without paying the 0.05 BTC to the attackers. Some users have reported that snapshots have been useful in reversing the impact (heavily dependent on your retention policy and location, as you still need the original file in a comparable form for snapshots to work). However, a full means to reverse deadbolt is not available. Previous attacks were able to be reverse using data recovery tools such as PhotoRec to restore them to their original version on an external drive, but success in this method with deadbolt has not been exactly positive. If you have no backup in place and your data is truly irreplaceable, then paying might be the only option (at least in the short term). You can follow the instructions that are attached to the Deadbolt warning page on your QNAP NAS GUI. If you have lost access to this GUI in an QNAP update (understandable that you might action this in the vein hope of halting/reversing damage), here is a Deadbolt Decryptor tool (this still requires the encryption key however) – https://www.emsisoft.com/ransomware-decryption/deadbolt
There are several useful references and setup pointers listed in the exceptionally long QNAP forum port HERE and here are their recommendations for you in the event you have been hit:
- If you have full external intact backups, reset your NAS and restore from backups
- If you have no backups and don’t intend to pay, try Qrescue (if your NAS has more than 50% free space and was not written to, chances are ‘OK’ to recover most files)
- If you decide to pay, here is a ‘user’ story’ (Make sure that all auto-updates are disabled during the decryption, so the process is not interrupted)
- To find your decryption key after paying the ransom check here.
- If you are missing the ransom note and bitcoin address (removed by a QNAP firmware update or Malware remover) check here

The Sad Truth about Servers, Security and Vulnerabilities
Vulnerability > Update > vulnerability > update > rinse > repeat
No platform, software or service is going to be 100% bulletproof. You can increase your personal layers of security (VPNs, Encryption, layers, restrictive white lists, etc) to hit 99.99% but whatever way you are looking at it, everything we use is software-based and therefore, fallible. Equally, users cannot pretend that it is still the early days of the internet anymore and still be annoyed when a statistical possibility that should have been factored against was not. Do I think QNAP NAS are safe? I’m sorry to say that the answer is never going to be a simple Yes/No. I think they provide what they say they provide and I think that QNAP hardware is still the best in the market right now. But their software needs to be less rushed, the extra time/budget be spent on that software, or utilize a trusted 3rd party. The need to relinquish some of the customization of their platform in efforts to remove some of the configuration out of the hands of less tech-savvy users who end up overly reliant in defaults. Perhaps a much more rigorous setup policy that, on day 1, have an EXPERT door and a NOVICE door, with randomized defaults and extremely regimented update rules on the latter. Equally, the brand (though better than it was) needs to work on its communication with its end-user base, both in the event of critical issues and education on what the user base needs to have to increase security OUTSIDE of their product. I still recommend the brand, I still think users should use their products, but we need to be realistic and honest with ourselves about what we buy and our expectations. If I buy a QNAP NAS, I expect it to store the data I store in it and allow me access to it on my terms, but ‘my terms’ might be a lot more/less strict than the next person and with that comes due diligence in 2022. I hope that the most recent ransomware attack, deadbolt, is the last ‘big’ one we hear about the year/moving forward, but I do not think it will be. More than just QNAP, one look at the vulnerabilities listed on security advisories of all the brands tell us that there is big money to be made by these intruders and the brands can only stay 1 step ahead. As always, me and Eddie here on NASCompares have been running a page that links to the bigger NAS security Advisory pages that gets regularly updated, so if you want to get notifications on these as they get added (pulled from the official pages themselves), then you can visit the page below and put your email in for updates when they happen. Have a great week and backup, backup, BACKUP.
Click Below to Read
📧 SUBSCRIBE TO OUR NEWSLETTER 🔔
🔒 Join Inner Circle
Get an alert every time something gets added to this specific article!
This description contains links to Amazon. These links will take you to some of the products mentioned in today's content. As an Amazon Associate, I earn from qualifying purchases. Visit the NASCompares Deal Finder to find the best place to buy this device in your region, based on Service, Support and Reputation - Just Search for your NAS Drive in the Box Below
Need Advice on Data Storage from an Expert?
Finally, for free advice about your setup, just leave a message in the comments below here at NASCompares.com and we will get back to you. Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.
Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.

|
 |
Best Cheap NAS of 2025
Minisforum MS-02 Ultra - WHO IS THIS FOR??? (The First 48HRs)
Why People Use TrueNAS, UnRAID and Proxmox to Turnkey NAS (Synology, QNAP, etc)
Why People Prefer Turnkey NAS vs TrueNAS, UnRAID and More
The Top 5 Mistakes NAS Buyers Make
Top 5 PLEX/Jellyfin NAS of 2025
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.







It seems like if you’re using their product doing everything you should do to keep secure that the company should pay your ransom. They make ginormous profits and aren’t making something secure to start with.
REPLY ON YOUTUBE
Fantastic video. Thank you very much.
REPLY ON YOUTUBE
Great video with lots of good info. I have had my TS-853 Pro for 9 years now and I have not had any malware. I keep it off of the internet and always keep updates applied.
REPLY ON YOUTUBE
This video needs an update and to go a bit more in depth
REPLY ON YOUTUBE
Lots of things to check. I have noticed in the new version of 5.1.5 QTS. The login options include 2 step verification (password and OTP/authenticator) or passwordless (1 step) – last option is username and authenticator. I am thinking the 2 steps seems safer.
REPLY ON YOUTUBE
For security reasons I blocked every internet-traffic in my QNAP VLAN using my firewall. When there are update available I either put them in manually or change the firewall rules for some minutes. I am operating a cloud in a different VLAN, I never wanted my QNAP to be available thru the internet.
REPLY ON YOUTUBE
im getting a DAS as NAS is not safe
REPLY ON YOUTUBE
i was going to buy a nas— im not now
REPLY ON YOUTUBE
Great Video content. Fire your editor though. You need to use the “clap” method if he’s struggling sync the audio to the video.
REPLY ON YOUTUBE
just recently got the qnap love it its been amazing, was wondering if i take all the precautions you say can i use the qlink?
REPLY ON YOUTUBE
Please make an updated version of this video
REPLY ON YOUTUBE
Do Qnap Os have Reverse Proxy?
REPLY ON YOUTUBE
Qnap make amazing kit. I’ve been running them for over ten years without any major issues – the minor ones being due to the hardware slowly getting older and associated problems with that such as firmware updates requiring manual steps to install (although big kudos for them still releasing security updates for my ancient systems), and lack of support for larger drives. Yes, I’ve recently bought another one.
I am impressed with what you can do with their NAS systems *but* as much as it is tempting to use these extras I never would. Years before this deadbolt etc thing happening I was recommending people not to use the remote features. That is not because I specifically don’t trust QNAP to get things right. I would not trust any third party to be able to ensure that there are no holes or backdoors. That includes, by the way, systems such as Teamviewer. Responsibility for the security of my data on my network is up to me – if I hand any of that over to anyone else then that is an act of faith that I am not willing to take. The risk vs reward does not add up.
My recommendation is yes to ensure that your devices are patched and kept up to date, but I would also recommend to not directly expose anything like that to the internet. Rather, I use a VPN to get to my network and from then on it is like I am at home. For a ‘hacker’ to get to my data, they would need to be able to get in through that one hole that is as secure as I can possibly make it.
The other recommendation is to not focus on backups to prevent loss of data due to a hack. That is a concern of course, but there is also a big risk of loss of data due to hardware failure. I have seen total data loss due to two disks failing in a RAID, data loss due to corruption, even a direct lightning strike (although in that case I was able to recover the data through some miracle). Backup because bad stuff happens – like insurance, you may not need it but it is really good to have just in case. Also make sure there is an air gap between at least one of your backups – I have seen data loss due to the corrupted data being backed up over good. Minimum I would suggest would be to have two backups – one where all the data is regularly backed up to a second device on site (maybe an old NAS with drives in a RAID0 array) that is usually physically disconnected when the backups are not running, and the other to a remote site such as a cloud service. Note that you may have a huge amount of data that could be backed up – and to do that to a cloud service might take an inordinate amount of time as well as cost a fortune – but you can also structure your backups so you only backup what you really need eg family photos and important documents that cannot be replaced. Local copies of most movies, for example, can always be ripped again from the originals or simply watched from streaming services.
Finally, I would note that I do like being able to install updates based on my own schedule. If they are forced by default (and I agree that is a good setting for most people) at least provide me with the option to turn off forced updates and perhaps just pester me. This enables me to ensure I have backed up my data before an update is applied. Yes the updates should be applied, but I have seen issues – not with Qnap, but that doesn’t mean it couldn’t happen – where a device is basically bricked after a failed update. I know that I should have a fairly recent backup, but I would rather do it when I know I have a valid and current backup just in case. 🙂
REPLY ON YOUTUBE
This was a bit of a skimmy.
Overviews are one thing, but you did say you would show how to set this up securely. That wasn’t delivered here.
REPLY ON YOUTUBE
The more secure you make things, the harder it will be to manage and jump through to get what your after. You could use 2FA, and encrypt volumes, for single person or two, all of that really is not required.. as long as you have good passwords for each user., and just gets in the way anyway.
encrypted volumes also slow down you NAS as well, but depends on the CPU/RAM your NAS has. eg TS-451 would better than TS-251
I would prefer user-based folder access for security than 2FA just because 2FA and volume encryption works as a “whole” where as user password and permissions are “per-user”
Much more simple to manage. Many people may disagree, but its my NAS so… ???? Just make sure you use strong passwords and that’s it.. Also, its bad practice to keep changing passwords every 180 days,,
Companies used to do this in the past ,thinking it was more secure changing regularly, but all it REALLY did was ****** off employees.
Sorry, i manage my own security
REPLY ON YOUTUBE
not gonna lie I wasn’t thinking 20 minutes later all i’d hear is change password and scan for malware, that hardly keeps the NAS secure, if I had a good password to begin with my security isn’t increased by changing it constantly. and doing a malware scan isn’t keeping me secure, stopping malware get on my system would be. and being notified of the lack of security is moot and not keeping me secure. password, update and scan malware. that takes 20 seconds. I thought you were going to show us how to disable certain ports, etc.
REPLY ON YOUTUBE
I have been hit. Is there a way to fix this without ruining or losing all my data? Admittedly, I am a noob who thought of QNAP as a plug and play with all the appropriate security built in. Any help, would be very much appreciated.
REPLY ON YOUTUBE
I mean, I don’t have enought money to backup my 120TB
REPLY ON YOUTUBE
With all due respect you have blown past the single biggest issue that is 105% QNAPs fault. And still persists to this day. EVERYTHING. And I do mean EVERYTHING on their OS runs as root. As a perfect example:
[/] # ps -elf | grep admin | wc -l
587
I have 3 apps installed on my system that don’t ship by default, and I’ve removed and disabled as much as possible and still…..587 processes are running as “root” or admin as it were. This is beyond unacceptable. No process outside basic core processes required to make the OS work should be running as admin and sure as hell not something like Plex. This screams that QNAP is incompetent as everything is running wide open. This is exactly how these malware apps were able to encrypt the content. They used the tools on the system to encrypt it because they were running as admin. They could do whatever the heck they wanted.
[/] # ps -elf | grep -i Plex
4906 admin 103212 S /share/CACHEDEV1_DATA/.qpkg/Tautulli/bin/python3 Tautulli.py –daemon –port=XXXX –datadir=/share/CACHEDEV1_DATA/XXXXXXX
21774 admin 84 S Plex EAE Service
25832 admin 298956 S ./Plex Media Server
25879 admin 13616 S N Plex Plug-in [com.plexapp.system] /share/CACHEDEV1_DATA/.qpkg/PlexMediaServer/Resources/Plug-ins-ca0c45ff8/Framework.bundle/Contents/Resources/Versions/2/Python/bootstrap.py
28587 admin 756 S /share/CACHEDEV1_DATA/.qpkg/PlexMediaServer/Plex Tuner Service /share/CACHEDEV1_DATA/.qpkg/XXXXXXXXXXXXXXXXX
Going back to your house analogy. If I lived in a shitty part of town I damn well would have video surveillance in my house and have a safe for valuable when I’m away. QNAP has locked the front door. Sure. But the windows are open and all the valuables are out and can easily be seen inside the house.
PS- And before saying I should be running Plex as a different user. I created a plex user, selected application priv and Plex never populated under that. If there is a way of running apps under alaternate user creds it is far and away hidden from the common user interface. Even a simple google search results in people asking why would you even want to do that.
REPLY ON YOUTUBE
Yeah right. AS soon as I have a good solution to backup 92TB of data…..I’ll do it. upload speed is 40mbit a second. (Thanks shitcast….like I care about the gig download speed.) and 100TB external storage is expensive AF. I looked at tape……5K for a tape drive.
REPLY ON YOUTUBE
You talk to much and say to little
REPLY ON YOUTUBE
You talk to much and say to little
REPLY ON YOUTUBE
You talk to much and say to little
REPLY ON YOUTUBE
You talk to much and say to little
REPLY ON YOUTUBE
You talk to much and say to little
REPLY ON YOUTUBE
In the age of VPN technologies such as used by Tailscale, I think all NAS vendors from now on should integrate Tailscale or similar and offer an easy solution for remote access. Like what was said in this video, allow users to set up remote access with open ports, but warn them several times before allowing. Tailscale does not require any open ports on your router to the outside world, and even works through carrier grade NAT.
REPLY ON YOUTUBE
That sucks. I was leaning this way over Synology due to the proprietary crap they seem to be missing ing to. I’m also looking to use this as an alternative to Google Photos and Amazon but it sounds like it isn’t even close to secure.
REPLY ON YOUTUBE
Always update if the update is security related at all.
REPLY ON YOUTUBE
Very BASIC security settings but the best security for QNAP is to keep all services OFFLINE completely so I absolutely NEVER use QNAP Cloud!
As of January 2023 QNAP still has major online security issues so I will not trust QNAP online servers, nor cloud services and especially not email notifications handled by QNAP.
For email notifications to be sent…QNAP needs QNAP email servers. Today QNAP products are still vectors for ransomware so please Do NOT connect to QNAP servers!
Novice QNAP users should be offline ONLY, therefore should not be using notifications nor QNAP Cloud.
REPLY ON YOUTUBE
A backup is not a backup if it is online
REPLY ON YOUTUBE
I found the txt files in my /home folders for each user. Luckily my Nasbook wasn’t encrypted. I setup firmware updates to check at 6am every morning and auto update all apps. I also deleted every app I don’t use and have it set so that the NAS reboots every morning at 5:30am. I deleted the HelpDesk app. For some reason the latest firmware doesn’t start the app automatically anymore, sounds suspect to me. My Nasbook seems to be ok. The only thing that bothers me is that the OS will randomly shut down but the router ports still active, maybe once a month. I’ll have to unplug the Nasbook twice to get it running again.
REPLY ON YOUTUBE
I only use my QNAP NAS to store videos so I can watch them via Plex on my internal network. The router must have some open ports since it is needed for my security cameras (port 80 and 6036). It has taken me weeks to rip my DVDs to the QNAP and because of deadbolt, they are all useless now. So I can start again. I have a large house with IoP devices throughout. Any useful suggestions?
REPLY ON YOUTUBE
17:00m FORCED UPDATES TO EAT YOUR MEAT OR YOU CAN’T HAVE ANY PUDDING
The minority but visible issue of RANSOMWARE points to the same conclusion of managed time only on the internet and a different access and use infrastructure, harking back to CompuServe and even military peer to peer access only to break the back of the Time Jack and Slave issue.
REPLY ON YOUTUBE
For many years now Why is NASCompares still always running defence and public relations for QNAP incompetence?
REPLY ON YOUTUBE
QNAP products are a colossal Waste of time and money. QNAP has become a constant worry and threat to my valuable Data. It has been only a few years that I have been configuring and securing my data on these and I have lost all confidence in this company and its software and hardware. The Ransomware attacks go on and on and on and on… I call BS.
QNAP software and security is awful. Two years ago I got hit with Ransomware from the QNAP Cloud itself because lets face it… even if you secure your end you can bet QNAP is NOT secure on their end. Never. No way.
QNAP is not for amateurs and it is especially not for professionals. Professionals don’t waste their time on crap. The QNAP products are so laughably insecure that you might as well kiss everything you put on these boxes goodbye. ????
REPLY ON YOUTUBE
What if the NAS manufacturers created an auto update that Only access their site, but otherwise disallows internet access altogether. ?
REPLY ON YOUTUBE
Is there a way to not expose my nas to the internet but have it on my local area network?
REPLY ON YOUTUBE
Thank you for this I was hit in Sept and my photos mostly traditional formats but most of my RAW files were not.
EVERYTHING said here is accurate and correct . I travel on the months sept -Jan and enable MyQnap for remote access. When I went in to access files for Xmas photo book for family I found out I had been hit
Also because I was running daily virus checks with Malware … it saw scanned the problem at 3am Sept 8 2022 and quarantined the virus… so make sure you have this running. I also had auto updates on firmware
I have ripped out photo station for time being until I can get back to physical hardware. I hope this help
But this Video is exactly correct
REPLY ON YOUTUBE
I agree the owner should have total power over their equipment. Forced updates and forced restrictions do not sit well with me. I am responsible for my data and my device security. That said Qnap is totally at fault for producing insecure apps, and not notifying users in a reasonable time.
REPLY ON YOUTUBE
Is myqnapcloud the only thing that “connects us to the internet.”
So my question is as long as I disconnect from myqnapcloud then a large majority of my risk goes away?
REPLY ON YOUTUBE
This video is like payed by QNAP:
“It’s customers fault that they allow QNAP apps to run”.
It’s better to say it simply:
– QNAP apps are unusable gimmicks
– The entire QNAP platform is not usable for internet access.
(previous hack was trough their cloud accounts, so nothing related to local user setup could help)
It’s ridiculous to blame user, routers, protocols (like UPnP) etc. as NONE of the hacks were because of them.
ALL of the hacks were due POOR security (like hardcoded passwords in the source) in QNAP own software and platform.
REPLY ON YOUTUBE
Perhaps QNAP is not for those of us who are not computer experts. Some of my files have been corrupted by DEADBOLT and I now have to recover them from lots of backup discs which will be a day’s work. Suggestion about uPnP Auto config tools, disable SSH and Telnet services appear daunting to those of us not well versed in computer jargon. I would certainly “radomize port numbers” if only I knew how. I have tried to follow the advice given by QNAP and on this video but must confess, that for me, it is not easy to find the controls that will disable these things.
REPLY ON YOUTUBE
When he says “any NAS should not be ”directly” connected to the internet” does that mean it is not behind a router? Also, I don’t need SSL if I only connect to my NAS while I’m at home, connected to the NAS with my own wifi, right? I have telnet, ssh, etc., all disabled.
REPLY ON YOUTUBE
i have both qnap and synology 2 units each. They crash and i mainly purchased to store data. Many headaches, moving forward it is cheaper to just buy a wd 20tb drive for $400ish. The unit with good drives is 1k+ . having a difficult time seeing the value. An old server is also cheaper.
REPLY ON YOUTUBE
My understanding is that even if you follow all the security guidelines and update everything daily you would have fell into the attack prior to Sept 3rd. Assuming you are using Photostation through the internet.
REPLY ON YOUTUBE
Can you do a video with the best firewall configuration for a multimedia qnap server like the tvs h674 without using the upnp method?…. thanks again.
REPLY ON YOUTUBE
I think this video, fails to address the elephant in the room – Everything on the QNAP runs under a single SU account… meaning, all apps, have access to all data. A fundamental security feature on Linux (and modern OSs) is the running of processes under separate account, which allows us to restrict what data they can access – meaning, if an app does have a vulnerability, the impact of an attack is minimised… but because QNAP do not use this, the fallout is basically nuclear!
Synology know this, and have implemented this application segregation.. and the ridiculous thing is, QNAP also know this, they spoke about implementing it 4 years ago, they also spoke about moving to containers to provide application isolation… neither of these have seen the light of day.
REPLY ON YOUTUBE
Just a wild thought: what if some of the Qnap engineers themselves are behind this?
REPLY ON YOUTUBE
And I just ordered QNAP TS-251D today 🙁
REPLY ON YOUTUBE
I was hit by deadbolt ransomeware some weeks ago. Finally I got the key and my files have been fully decrypted. Thank you…
REPLY ON YOUTUBE
I was hit by deadbolt ransomeware some weeks ago. Finally I got the key and my files have been fully decrypted Thank you.
REPLY ON YOUTUBE
Starting to think qnap is skimping out and not paying top dollar in their security department. Maybe increase ur expenses in the security department and this type of crap will happen less frequently or non at all
REPLY ON YOUTUBE
My Asustor was hit the first time around here in Australia. Before this time I HAD locked down my 6510T by IP address, was assisted by an Asustor tech to do so, ezconnect & unused services were not activated. After some investigation an Asustor tech admitted one of the attack vectors discovered was through their own automatic update system! You CANT protect against that!
REPLY ON YOUTUBE
Snapshots should give us the ability to rollback in time and retrieve our data before it was encrypted by ransomware. Is taking snapshots regularly a reliable safety-net against ransomware. If a hacker has root access to the nas couldn’t he just delete all snapshots before and after encrypting all data?
REPLY ON YOUTUBE
We have dealt with so many deadbolt cases
REPLY ON YOUTUBE
Lucky enough for me i got help from this guys “mouse”????⬆️, my files were successfully decrypted and recovered
REPLY ON YOUTUBE
Lucky enough for me i got help from this guys “mouse”????⬆️, my files were successfully decrypted and recovered
REPLY ON YOUTUBE
I’m not convinced this latest wave was using photostation. I don’t have this installed and managed to get caught by 0xxx virus but based on this exact situation.i used it for media storage and I did have 443 exposed to web so I can access remotely via qfile app. Upnp disable on both qnap / router.
I only had 1 account and actually had my usb still plugged in with all my backup data. I left it transferring and forgot to unplug it and still the attackers didn’t or couldn’t encrypt it. Based on this I feel thqis may have been dnla/media server related as multimedia is the only folder the media servers are restricted to.
REPLY ON YOUTUBE
DEADBOLT hit my files by adding a suffix to the file names, that’s it. Weird
REPLY ON YOUTUBE
I feel so desperate for QNAP for their products which are frequently subject to ransomware attacks with no solution. I think it’s the right time to shift to other brand NAS for better protection of NAS data..
REPLY ON YOUTUBE
It would be perfect if they had an option of ‘file storage only’ . I could sell 25 a year if that was an actual option. Locking everything down is nearly impossible
REPLY ON YOUTUBE
27:00 most of that is default and requires user to enable insecure setup (like you said have a backup like another nas that isn’t a qnap or bunch of USB external hdds ideally 2 separate )
REPLY ON YOUTUBE
Question:
Is there a way to completely remove QTS from the QNAP server and install something else such as TrueNAS on the metal even if that means having to install a new DOM or is the BIOS so propitiatory it can’t be done without a board swap? Yes it would no longer be QNAP but I feel it would be much more secure and I could at least keep the servers updated without having to buy all new hardware.
The QNAP systems should be forbidden from access to and from the cloud, remote access of any kind or via the internet in any way such as api’s, by out of the box default. The administrator should have to manually configure any setups after acknowledging warnings and security should be enforced period.
I try to keep all my equipment up to date on firmware (including routers, switches, etc.) but QNAP makes even this hard by deciding to not support older enterprise (their term for rack mount) systems and I really don’t believe their reasoning on this either. I have a rack mount sever 4.36.2050 (5-26-2022) which they rarely update firmware on; only doing so as an after thought. The other is newer and still gets the newest updates. I have removed most of the remote access apps from both servers and have done QNAPS suggested disabling of stuff, changing settings etc.. I do have a few cloud apps still in use, but am thinking of moving away from those too to an external program I use.
REPLY ON YOUTUBE
I remember the same attack done at Synology, ransomware attack demanding 1.2 bitcoin, unfortunately I paid them and they gave the key and I unlocked all of my 10 years worth of files .
since then I unplugged my NAS from internet and don’t use its feature.
what synology did? they sent me $30 headphone… imagine that, I paid 1.2 bitcoin for cheap headphone.
I was considering Qnap until I find this video
REPLY ON YOUTUBE
QNAP are damned if they do and damned if they don’t on warning, big scary warnings upset alot of people, some from the “Mah Freedom” view where they just want to do what they like and dont want to be told otherwise by some sort of nanny, and others from the “Thats scary im going to return it/call support and complain” QNAP are behind on the security aspect but they are moving alot faster now than they were, alot of systems are now asking users to configure updates automatically now, Unifi as an example do it on setup, it should be on by default and if you want to manage it then you can turn it off
REPLY ON YOUTUBE
I’m about to outmode my three redundant Drobo NASs (none have ever given me an issue, but it’s time to move on). I have QNAPs in my shopping cart because I’m moving to a fast network.
All I want is a simple NAS. How secure am I if I disable everything but basic functions?
REPLY ON YOUTUBE
My PhotoStation was not exposed to the internet but I still got hit by this wave. AND I had just updated my firmware a couple days before the attack. I do not think PhotoStation was at an older version at the time of the attack either (I cannot remember and be 100% sure, but I do not recall updating PhotoStation recently, and there is no pending update in AppCenter).
Could it be Transmission from QNAP Club app source? The only ports open are Transmission and OpenVPN server.
I did briefly open management web over 443 and forgot to turn it off. But that is not PhotoStation and at the time the firmware had already been updated to the latest version.
Also the malware remover tool cannot find any malware. The anti-virus scan could not find anything related to DeadBolt.
REPLY ON YOUTUBE
QNAP user here who has not been attacked by Deadbolt or any other ransomware as of yet. My devices are not accessible from the internet, and I have no QNAP cloud features turned on. And UPnP is always disabled everywhere.
Just in case, however, I do have all my data backed up.
REPLY ON YOUTUBE
btw I like the first 30 seconds!!!! I wish you could just add…..more info explaining the responsibility of the major brands! why should I be having to pentest…..neways
REPLY ON YOUTUBE
Have you done a video on how to set up let’s encrypt SSL for secure remote access to a NAS?
I’m just a simple Plex user and moved awhile ago, that whole time my Nas was unplugged and unused for 2 years and I recently plugged it back in after setting up a media room. My NAS wouldn’t update firmware so I updated it manually with a flashdrive and I needed to make a whole new mycloud account for some reason. It’s been a pain getting it all set up but it’s currently in sleep mode. Am I still safe?
I did manage to set up 2FA on admin and basic user account and I’ll see about setting up the X failed password revoking privileges
REPLY ON YOUTUBE
I just got hit by this ransomware few days ago. Without knowing what happened, I updated the firmware and ran Malware remover and they removed my ransom note. I have thousands of photos and videos got encrypted and i’m doomed now.
REPLY ON YOUTUBE
It’s all good sitting in the ivory tower surround by free NASs however if someone spends 2k plus on a NAS e.g. 8 12 16 Bay you not going to have USB hdd to backup to as your invested in a beast system which one would hope has security features to block or apps to under scans etc. Qnap need to work better with the Linux distributior or change the flavour or OS they use.
REPLY ON YOUTUBE
Make sure PnP is turned off on your router. You don’t want something being made public without your knowledge. If you make it public at least you know you did it. If PnP did it, you might be unaware.
I agree about forced updates. At the very least set a reboot window time. 3am in the morning. I know that won’t work for everyone, but it should work for the majority.
REPLY ON YOUTUBE
I wonder if most NAS units were just being used as a simple SAMBA file server if we would have all these attacks and vulnerabilities??
REPLY ON YOUTUBE
Great video. At 27:25 you mentioned a video you did on security settings/randomising ports. Please can you post link. TY
REPLY ON YOUTUBE
What about the snapshot functionality that Synology has? Other than a HW failure would you consider it as an extra point of defence in case of data alteration?
REPLY ON YOUTUBE
Does the upgrade to the photo application in question actually require a reboot? If it does, that sounds like it’s completely unnecessary.
I’d add that the recommendation to create a low-privilege account to host individual apps sounds sounds like it ought to be a QNAP recommendation—if it’s their app, shouldn’t their installers do that by default?
REPLY ON YOUTUBE
I guess we can put FreeNAS on our QNAPs?
REPLY ON YOUTUBE
I got hit today as I only found out when my plex server didn’t show my library 🙁
now all my files are encrypted by .deadbolt I contacted qnap support and got nothing.
any way to decrypt my files or some one or firm that can help?
REPLY ON YOUTUBE
My QNAP is in the trash. They suck. I get constant email advertising new products, but not one email about ransomware that infected QNAP. Had they warned me, maybe I could have updated my QNAP before it was infected. Be careful how you back up your data. My QNAP was set up to automatically backup to a second QNAP NAS. The infected files overwrote the good files on the backup NAS. My third backup was Dropbox. Those files were over written too. Thankfully Dropbox has the ability to go back in time and all of my data on Dropbox was recovered. The bulk of my data on the NAS are movies in the MKV format, thankfully those were not infected.
Any NAS or computer can be infected, but QNAP in particular suck as a company because of ow poorly they handled it. It as if they tried to hide it. DO NOT BUY QNAP.
REPLY ON YOUTUBE
Why not simply access the nas through a local vpn needed to gain access?
REPLY ON YOUTUBE
I was hit… thank goodness that I found it early and I have offsite backup. Nothing permanently lost, but it took a WEEK of personal effort to recover it back to normal (re-downloading lost data + removing the ransom note/malware, which QNAP’s updates do not yet handle, outside of halting the file locking itself). Others will surely have a worse time.
Good moment to update my backup strategy (offsite backup was great, but slow… I need local backup… now I get that whole 3-2-1 backup thing ????). And yeah, lock it the F down from outside access! I’m surprised this isn’t the default state of the Nas out of the box, given what I know now… Live and learn.
REPLY ON YOUTUBE
The defaults need to be biased towards security instead of ease of access. If qnap wants these security issues to be the users fault they should force the users to explicitly misconfigure their systems. Rather than misconfiguring the system on the users behalf and then blaming the user for the fallout.
REPLY ON YOUTUBE
Qnap is AIDS. I’ve never known an operating system on any other platform to be as weak, or vulnerable as QNAPs operating system. If you’re interested in protecting your files buy a Synology or use some open source software. I’m sick of getting vulnerability notifications online about QNAPs, it makes me sick to my stomach.
REPLY ON YOUTUBE
Simple Solution “Do Not Give People The Choice” No Bypass, Nothing.
REPLY ON YOUTUBE
Absolutely pro forced security and critical updates.
REPLY ON YOUTUBE
NAS for Lan only
REPLY ON YOUTUBE
I would also advise upping TLS to the highest version on your NAS or homebuilt, I don’t agree with buying VPN, setup your own all vendors have OpenVPN (QVPN for QNAP) that way you don’t rely on a third-party company
REPLY ON YOUTUBE
As a long QNAP user, I remember when I was on a holiday and saw first Russian IP trying to breach the NAS, as a former IT guy I was watching all logs almost on a daily basis… In 10min I turned off NAS from the Internet and moved everything to local VPN gate closing all ports which were exposed to the internet… Not even 1 problem anymore. If somebody needs an access from the Internet I turn on ports for the time of the access, and immediately turn them off once this person got what he wanted. I still can’t believe in current environment people risk exposing NAS to full internet access… Regular QNAP patching to recommended software versions and regular router (Mikrotik) patching.
REPLY ON YOUTUBE
The breaking wheel or crucifixion should be re- introduced specifically for these people. They lay the blame on Qnap but they are the ones exploiting the loop hole, crushing users, many of whom have not recovered from the immense financial losses of Covid shutdowns and job losses.
REPLY ON YOUTUBE
No.
REPLY ON YOUTUBE
I think most folks need to educate themselves a bit more, bit it’s not all on the user.
Also, using a VPN as the only way into your network is really the way to go IMO
REPLY ON YOUTUBE
qnap has auto update on the os and on the applications. but is disabled as default. I use it on my nas to keep my data more save.
REPLY ON YOUTUBE
am I safe again if I delete or stop the photo app? on older drive NAS.
REPLY ON YOUTUBE
Unfortunately I must admit that I have not deactivated the default admin and don‘t have 2-step verification active. I once tried 2-step and it somehow stopped working after a few days and I was locked out. That‘s the reason why I fear disabling the default admin. Based on QNAPs software quality I fear losing access to my data due to messed up access rights. What is your advise. Start over again from scratch?
REPLY ON YOUTUBE
After getting hit with qlocker I haven’t had my nas connected online since. Recently connected it again just this week and I hear about this deadbolt stuff. Thankfully i sind be fine because I connected after all these new updates.
I have backups of my data om external drives. Heck my nas is no longer a backup means really I just want it to be able to access my data remotely as my own personal cloud storage with terabytes of data.
But now I’m worried I can’t do this without possible future hacks.
REPLY ON YOUTUBE
I can confirm that this deadbolt attack occurred at 9pm on Saturday night Australia EST, I was at work. I agree with you but there are issues with their firmware updates….my NAS was telling me there were no firmware updates when there actually was in August. You are correct there are several simple solutions but the ultimate protection is the 321 backup. I also found that it’s probably a good idea to reinitialise your NAS after a deadbolt attack and restore from a backup…..this is because there are issues with to Qnap operating software.
REPLY ON YOUTUBE
nice video, may i know when the galayou G2 video is published?
REPLY ON YOUTUBE
Put the NAS behind a NAT router at the minimum.
REPLY ON YOUTUBE
Awesome as always! Thank you! ????
REPLY ON YOUTUBE
How about a good video class (Long and lots of detail) on Secure https connections ssl Certs and the like?
I know Qnap installed a default secure certificate but that’s all I know. I did not do anything to set it up. 100% Lost on that stuff.
REPLY ON YOUTUBE
can encrypted files be unencrypted?
REPLY ON YOUTUBE
Dang Bro. Gotta check that authoritarian coming out. When someone says “you shouldn’t be allowed to” regarding a product you own it’s over the line. Do you really want to live in a world of “we’ll assume you’re to stupid to know what’s best for you so we’ll give you no choice”? Did you learn nothing from the lockdown scamdemic? People have to take responsibility.
REPLY ON YOUTUBE
What I don’t get is how someone can be knowledgeable enough to research and buy a NAS but dumb enough to leave it exposed. Even a turnkey solution like most Synology’s and QNAP NAS’s can be, require some knowledge on how computers work. Before I am attacked, almost all novice computer users think backing up is using a simple external HD solution, so if you are using a NAS you have more knowledge than the majority.
REPLY ON YOUTUBE
This dude is on point and honest in the first 60 seconds! I admire his perspective and knowledge, keep it up brother.
REPLY ON YOUTUBE
Is this true
https://youtu.be/2TE0Evn8eB0
REPLY ON YOUTUBE
I got hit with DEADBOLT on Saturday night. I was patched up to the most recent patch and thought that my QNAP was not able to be seen from the outside world. I had my data on another USB hard drive as backup and a number of snapshots on the QNAP.
I reverted to the most recent snapshot on a volume level, as thought that this was the best way to recover and was able to get back in and files were back. Changed my password and reinstated 2 factor authentication.
The 2 factor came in clutch as on Monday afternoon my phone pinged and it was the 2 factor pinging with an authentication code, which they weren’t getting.
Do you have a video of how to setup a QNAP NAS so it is total on your home network…????
REPLY ON YOUTUBE
It’s a pity. There are some really robust older QNAP NAS models (Rack mountable too) that have better specs then many of the newer retail models going for a song on eBay,……but aren’t upgradable to the latest QTS version. Practically criminal it is, real shame that. What with QNAP venerabilities as they are, you might as well pay the ransomware attackers in advance,….
REPLY ON YOUTUBE
I’ve been git by the last attack so I’ve followed your advice and isolated my Qnap from the internet as best as I could, I’m backing up my data as up for now, haven’t checked but I’m pretty sure I’m good to go. Your the best man
REPLY ON YOUTUBE
brilliant video. accountability works both ways
REPLY ON YOUTUBE
The solution could be to split up updates in different areas (“Security”, “Perfomance” and “Apps”, for example) or based on their importance (“Critial”, “Moderate” and “Optional”). And force the user to download the most important ones (following the examples, “Security” and “Critical”). And allow the user to choose the time he/she wants the NAS to reboot to apply the updates (“As soon as downloaded”, “At 1AM”, etc). I have a NAS for personal use and I would apply all of them and reboot as soon as possible. Besides, I think it would be a great idea if QNAP opens a Beta Program so people like me with a personal NAS can join it and get beta versions. Regards!
REPLY ON YOUTUBE
Society, citizens, and their governments and resources need to start taking these crimes more seriously. The message should be sent that if you develop these life ruining, economy ruining, malicious bits of code, then the people of the world will find you, hunt you down, and publicly execute your sorry ass. I don’t care if it’s a two year old coder, when a person is evil, they are truly evil, and need to be snuffed out. I’d personally contribute to a vigilante group do get rid of these sick people. The worst part is I was just reading how a hospital got infected and someone died. Think about it, everything is going to be computerized and require firmware updates and coding.
REPLY ON YOUTUBE
I have been hit on the 3d of September .. F***g QNAP not checking these holes! now I have some stuff that was not backed up.
BTW I followed almost all the recommendations and have automatic updates.. this is how the deadbolt was stopped before all the NAS was ecripted, but not fast enough.
REPLY ON YOUTUBE
Synology should buy Qnap for their hardware. And by combining the best hardware with the best software you get the killer combo…
REPLY ON YOUTUBE
I generally like QNAP’s products — but as a NAS user, I would not expose my equipment to external access for any reason and for any purpose. It may be an occasional hassle but, IMO, it’s a big hassle to discover that your NAS has been taken over by a hacker. The other thing is that I am a former IT guy who has experienced a few situations where entire workplaces were shut down due to virus attacks. And I learned early on the hard way that the “that can’t happen to me because I’m not a big corporation” factor is a big fallacy. Because it can and it did happen to me. Which brings me to this — QNAP as well as all NAS manufacturers should do everything they can to ensure that end users understand the importance of securing their equipment. As well, there should be proper measures to ensure proper security measures are set up on a NAS — like preventing use of a default admin account by forcing users to create a admin account which will have a less likelihood of being attacked.
REPLY ON YOUTUBE
This has been said before on similar videos, but it is not good security practice to connect any device to an open internet connection. If the device or applications running on the device have vulnerabilities, or poor coding, then an external threat actor could exploit and compromise the device. My suggestion would be to enable the device firewall. Do regular patching, inc routers/modems/NAS, Disable UPNP, which can cause issues with online games services, but can help.
REPLY ON YOUTUBE
But thanks for the update.
REPLY ON YOUTUBE
No photo station and no wan access to my nas
REPLY ON YOUTUBE
When you have 80tb of data to back up its not cheap to back up either locally or in a cloud service.
REPLY ON YOUTUBE
Fingers crossed that I did my backup properly…I just got hit. What a pain in the a$$!!!! And yes…firmware updated…just forgot my new router had upnp enabled.
REPLY ON YOUTUBE
Some really good points were made here. However, while the default Admin account should obviously be disabled the neophytes among us won’t necessarily know this. So it’s a fair point to suggest that it’s on QNAP for not forcing the user to change it at initial setup. They may do this now with the latest version of QTS / QuTS Hero but they didn’t always and as such they share some of the responsibility.
REPLY ON YOUTUBE
There is some merit in saying “NAS should remain storage appliance, not as webserver / media server”, but since virtually all NAS vendors market their products as such, I think it should be reasonable to expect they are hardened as such. System vendors should really restore the old way of calling software bug a bug and FIX it, not some ‘vulnerability’ that sounds like job for security experts to discover.
I got hit myself in this wave, still I must respectfully disagree that “using well known port is dangerous”. This is blaming victim at best and misleading at worst. Everyone connect to youtube on port 443, and no one should underestimate the scale of challenge this site is facing every second. To continue the analogy, it won’t offer extra you security by moving the front door to face the back street, or give it a camouflage paint. What matters is a quality door and lock, as well as to close & lock it properly in daily routine.
Well I get the argument that thieves pick easy target to begin with, yet lowering the chance of being attacked does not replace the need to get prepare for up coming attacks.
Technically the question is how is QNAP handle traffic to port 443, or 80 or 8080 etc. Is it using the battle tested httpd to listen, to authenticate, and to reverse proxy request to actual apps? Why does it need a separate firewall app that is not turn on by default? I was surprised to see different QTS apps happens to be separate FCGI threads spawning off cgi-bin/ directly, and handle authentication individually. These imply each app running, and each app update, introduce new risk.
Bottom line: I pay a premium for NAS appliance in exchange of peace of mind. This is a major let down.
REPLY ON YOUTUBE
Thank you for providing well-needed information to the general public…
REPLY ON YOUTUBE
Can you do a video of your thoughts on TrueNAS and it’s place in this torrent of ransomware attacks? (see what I did with the word ‘torrent’ there 😉
Also, could you share your thoughts of replacing OS in a QNAP box to TrueNAS?
Thanks!
REPLY ON YOUTUBE
It should be clear to everyone now that qnap is not up to the task for external access. It is just not worth it.
REPLY ON YOUTUBE
Unsecured external access to the NAS and Photostation,…….who in their right mind would ever,….???
REPLY ON YOUTUBE
I´ve got a TS-653D not running any QNap apps whatsoever. External access possible but no standard usernames or passwords, no standard ports, 2FA, SSL cert etc pp.
REPLY ON YOUTUBE
Ransomware sucks
REPLY ON YOUTUBE
So how do you update the various apps with out being connected to the internet?
And
How do you hide the nas from the internet if you don’t want remote access yourself?
The answer is firewall on a NAS or on your router/switch. You can enable only those IPs that host app updates.
I se one that one Simon
I have secured my QNAP and it has been safe until Saturday when I got hit by Deadbolt, but my most recent snapshot come to the rescue……the thing is that my QNAP was secured as far as I was aware…..????????????????????????????
REPLY ON YOUTUBE
I am IT consultant for 20 years and i loved to had the opportunity to watch this video. To me the thing that QnAP does not have any guilt in their product its at least a bit biased. I know people want to sell NAS and make a good chunk of commissions, its how things works i got that.
But lets face it with a great example, if you have a Tesla, are driving and the car crushes because the system does not allow you to stop, then even if there is a bug there, the brand is responsible, not the end-user for sure.
When we translate the NAS issues, well sure , the end-user needs to have a specific skill set to be able to know how to work with the technologies, but the brand does not say its it can be challenging for some people, who does not understands, a,b,c… etc…. Instead they tell you that you can have everything setup by clicking a simple button, and the more features it has the more people will activate.
I never saw a disclaimer from QNAP or any other NAS brands about what can happen if the users does not have that skillset, and even worst, they market it as a product that is top notch in technology, like having access to the nas content from everywhere. That´s where they have responsibility, i am quite sure some lawsuits will occur sooner then later.
Because they have the responsibility to explain clearly what a basic user should do and should not do…
They also should explain that someone before buying a NAS should have at least a 3-2-1 backup solution , because the NAS is not the backup solution.
I know that for many people, the NAS itself its quite expensive to buy and so many users cant afford to buy external drives for Local backups and also a cloud backup system, that is the bare minimum for whom thinks about having a NAS as home or in a SOHO
And here again i never seen QNAP explaining in a very clear way in their sale pages about their NAS products, when i am talking about QNAP, its not only QNAP , other brands do the same, but are they responsible brands by doing so? in my honest opinion nope.
Probably many small business went out business, some because ethically they don’t want to pay to criminals and others because they cant afford to pay due to the crisis that have impacted so many people worldwide.
Here i believe that QNAP should paid the ransom to solve this issue for their customers, are they obliged to? of course not, but in the other hand they would not have their image burned out and their online reputation is not good to say the least.
I have a QNAP nas devices and i am quite sure that i will never ever buy another from this brand again.
REPLY ON YOUTUBE
I think every brand should add a choice at setup that asks, what is your data classification: very private, private, public. And what is your update tier: beta, innovative, stable and secure. From that the system can make the appropriate choices.
REPLY ON YOUTUBE
You didn’t mention running a VPN. 🙁 That saves so much complexity.
REPLY ON YOUTUBE
Worker with a reliable hacker is what I think is all over the world and I recommend a hacker parfait who works with good heart and sincerity Dee_hack11 is in Seoul☝️☝️☝️.
REPLY ON YOUTUBE
Worker with a reliable hacker is what I think is all over the world and I recommend a hacker parfait who works with good heart and sincerity Dee_hack11 is in Seoul☝️☝️☝️.
REPLY ON YOUTUBE
If i don’t have QNAP Cloud installed, does that mean that i am not connected to the internet?
Is sending email notification not a good idea, considering i don’t want to link my NAS to the internet?
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
*I was hit, so unplugged, shutdown, external USB backs fine. Plex user, was watching at the time no issues, went to update saver denied, then found the splash screen, no on reboot, water gapped on an independent switch no WiFi etc, it instantly goes to initialization. So save to assume the service themselves have been affected. Did safe shutdown. After some time I turn on everything then I found out I’ve been truly hit by deadbolt. I did as many research as I could and I found out that scott can actually decrypt the encrypted files So I paid some money not upto what deadbolt team are asking, then he decrypted my files*
REPLY ON YOUTUBE
*I was hit, so unplugged, shutdown, external USB backs fine. Plex user, was watching at the time no issues, went to update saver denied, then found the splash screen, no on reboot, water gapped on an independent switch no WiFi etc, it instantly goes to initialization. So save to assume the service themselves have been affected. Did safe shutdown. After some time I turn on everything then I found out I’ve been truly hit by deadbolt. I did as many research as I could and I found out that scott can actually decrypt the encrypted files So I paid some money not upto what deadbolt team are asking, then he decrypted my files*
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
.You can message *SCOTTS_HACK*
REPLY ON YOUTUBE
.You can message *SCOTTS_HACK*
REPLY ON YOUTUBE
Forgive that this may be a stupid question. But – if you have a QNAP NAS plugged in to your computer – and your computer is connected to the internet – does that mean your NAS is connected to the internet also? Or – is the hacking security risk purely for if you choose to directly connect the NAS to the internet (and therefore if you don’t, you risk free)?
REPLY ON YOUTUBE
will adding 2step verification change the way using share links work (ie: sending a share link to a shared folder on my nas to friends via email)?
REPLY ON YOUTUBE
Let Eddie say something…
REPLY ON YOUTUBE
I wouldn’t touch QNap with a barge pole until they drastically change their approaches to the user base, contempt for the user base isn’t a great strategy.
REPLY ON YOUTUBE
Hi, Thanks for the great video!
Would you be able.to elaborate on sharing the file process to an external temporary user, please?
REPLY ON YOUTUBE
You’re ???? such a genius, I really appreciate your services, fast and safe recovery process..
REPLY ON YOUTUBE
You’re ???? such a genius, I really appreciate your services, fast and safe recovery process..
REPLY ON YOUTUBE
I miss the most important step, formatting and throwing away the QNAP.
REPLY ON YOUTUBE
My QNAP NAS used UPnP to open all of the ports needed for bad actors to try brute forcing their way in. I was getting over 1200 login attempts per hour.
REPLY ON YOUTUBE
I think forced updates should be a requirement for utilizing certain features. So, if I enable remote access through a firewall of any sort, forced updates should be enabled. IT enabled organizations wouldn’t be making use if these features anyway and in can absorb the risk of automatic/manual updating.
REPLY ON YOUTUBE
I think they get attacked because they move into Face/Facial/Eye/Mask screening. People don’t like that. This is a threat to privacy. I think that is the root cause of it. I don’t know if Synology is in the same as such.
REPLY ON YOUTUBE
I regret I have missed this video 2 weeks ago. #asustor #deadbolt
REPLY ON YOUTUBE
I’m sorry I purchased a NAS as a means to have a BACKUP of what is/was on my laptop or pc. And it’s even sold as a backup. It started with ‘consumers’ being told to connect an external hard drive to backup their data. They would even supply at times backup software. So you backed up to this external drive. Then they started to sell NAS which was a way to still Backup and be able to access those backed up files from any connected computer.
So I disagree that you cannot thing of the NAS as a Backup.
Evidence: Why do they supply NetBak. Which can backup or copy your PC to the NAS.
So if you say the NAS is not a Backup tell these companies to stop supplying backup software that works to copy to these systems.
When I was told I needed a Backup I bit the bullet and purchased a second NAS which is used only to receive a Backup Data from the Main NAS! Its stupid but I understand it.
Especially since this last issue I had to erase my partitions to fix my issue. Great!
REPLY ON YOUTUBE
Wow I liked how you pointed out tech support being abrupt.
I reported a problem months and months ago and it was just impossible to arrange for remote support.
Then there was an update which fixed the problem we were trying to work on. So I basically wasted tons of time trying to recreate the problem and pin pointing the actual issue.
So why was I spinning my wheels for months when they knew about the issue.
Just tell me and ask me to be patient while they fix the bug. Why make me waste my important time for this sh*t.
I also had a problem of the NAS running so slow I could not even log in via the web. Thankfully I have a unit that has a hdmi port and was able access it via direct. But still could not use the system.
That was months and months. I was planning on dumping the whole thing. But it meant dumping two QNAP units. The cheaper of the two worked perfectly. I was angry.
Then I read something in a forum and decided to try it. I had to stop running Q’Center. Once I turned it off and removed it my system ran normally.
The same thing happens when you run McAfee. Of all things to slow down your unit so its unusable what is the purpose of having anti-virus. And whomever says its not needed needs their hand examined. You do!
The built-in anti-virus finds things that McAfee does not? And yes they could be false flags but it works.
REPLY ON YOUTUBE
Great video! I just saw lex friedman video and he talks about his devastating qnap ransom attack.
REPLY ON YOUTUBE
your videos could be a bit shorter and more concise. Lots of filler that doesn’t give a lot of information.
REPLY ON YOUTUBE
Not an IT expert but I bought an entry level Qnap NAS, which is now not connected to the internet and I’ve manually updated. What I’d really like to see is a guide to setting the NAS up safely so that the NAS is available to the home users, but protected from the internet outside. Backing up to two USB drives BTW!
REPLY ON YOUTUBE
Great discussion, can an OpenVPN / windows vpn on QNAP do it? and not juse myQNAPcloud? can it not be a good option? between one’s server and user outside of one’s network.
REPLY ON YOUTUBE
QNAP has significant blame in this latest attack. First, it was their operating system that was hacked (no one had to download a corrupt file). Second, they have all their users emails and all they needed to do is send out notifications to us users alerting us to all the attacks this past year not to mention warning us all to “unplug” immediately when this last attack started. Instead, they remain silent by email even to this day. The only reason I figured out I was hacked is after a month of not logging onto my NAS I found all my files encrypted when I went to grab some photos for my wife. I had to figure out for myself (with the help of bleepingcomputer forum) what was going on, how to get the ransom message back because they had quarantined it. No I didnt have a backup and I guess that is my fault for not understanding the hardware and risks better but I bought the NAS because it was supposed to “simple, safe and secure”. I only use my NAS on my LAN and I’ve never downloaded outside files to it but am not savvy enough to not have it connected to the internet thru my router. If Im lucky enough to get my data back after taking out a loan on my credit card and figuring out this whole Bitcoin thing this weekend, Im done with QNAP and their crappy equipment, buggy software and business approach. QNAP’s silence, irresponsibility and incompetence in dealing with these attacks this past year is the real story here that you all should be talking about as well.
REPLY ON YOUTUBE
What is the most concerning for me as a customer, not that hackers exists, they always did. But that Qnap has backdoor account to my own NAS…… they can remotely access to HBS, force update or whatever….. the clear answer to me to your question is : QNAP is not safe at all, period !
REPLY ON YOUTUBE
I don’t understand why so many “intelligent” people finger-point the victims. Do those guys blame their kids who’s got bullied in school? What a pathetic! NOBODY, NOBODY opened the port to the internet! QNAP got the port opened OUT OF THE BOX! I’m not using mycloud, I didn’t open any port. I didn’t enable auto-update because last year I ever lost files after migrating to the latest build!
This is not the first time they messed up everything. As always, QNAP is trying to escape from their own responsibilities. They pretends nothing happened. Custom service is non-existent. Users forum is full of everything but anything helps fix the issue.
Stay away from QNAP like a plague!
REPLY ON YOUTUBE
Infected last month, huge damages to us, and i guess it’s their ex-engneers who made ransom, and i am sure this company will fall.
REPLY ON YOUTUBE
I use my QNAP for Plex, and I share my Plex with two other friends. This is my second ransomware attack (thank goodness I had backups), so should I stop sharing? Can I make my QNAP secure and still share?
REPLY ON YOUTUBE
Thank you for making this enlightening video! I have now checked and switched off UPnP at my router. I was also watching your Plex setup video where you talk about setting remote access for Plex on a Synology NAS (with DSM 7) . How risky is setting up remote access for Plex to access my media remotely and are there ways to mitigate the risk?
REPLY ON YOUTUBE
Found the presentation very irritating. Why keep wizzing the cursor around the screen. Why not use a large black cursor. Don’t do everything so quickly.
REPLY ON YOUTUBE
I have found QNAP TVS-951X about 350£ (450$) used with 30 days free return + 6TB WD RED drives + 32GB RAM, should I buy it ?? it does look in a fair condition I want to use it for 4k streaming + 1080 and some backup + two or three members of my family watching 1080 content with me also to back up my stuff on it, should I buy it ??
thank you
REPLY ON YOUTUBE
Robbie and Eddie, Thank you for this in depth discussion, and guidance. I’m new to this, bought my nas at the end of November, and have been following a steep learning curve since then. I especially liked the advise to NOT TOUCH your network or nas settings if you do not understand the actions and results. I have to remind myself of that each time I mess with the settings, and have to reconstitute my nas.
REPLY ON YOUTUBE
I bought a single, large (16TB) HDD in recent weeks, plugged that into a free bay in my NAS, created a new storage pool & volume, and copied all my existing NAS Data onto it, and when complete, I pulled that Harddrive out. This is my ‘emergency’ back up, should the worst happen.
REPLY ON YOUTUBE
The Bank & Bank card analogy is a good one.
REPLY ON YOUTUBE
I don’t have remote access to either my QNAP or my Synology directly or through their respective relay systems. Instead, I use OneDrive (OD) as a relay point. My NAS is setup to sync with my OD account. When I’m on the road, my laptop syncs files with OD. So, when I edit a file on my laptop, it then syncs to OD which in turn syncs to my NAS. This won’t work for everyone but it can be a very effective way to effectively gain access to your NAS while working remotely. I don’t do this with the entire NAS, just the folders / files that I may need remotely.
REPLY ON YOUTUBE
Just bought a qnap nas yesterday. Really useful conversation. I have to admit i’m a little more concerned after watching this video than i was before.
REPLY ON YOUTUBE
Probably a recommended setting for beginners users from QNAP might works.
REPLY ON YOUTUBE
We are preparing a new video about how to secure your NAS and your local network.
You can send your external IP address to us via NAScompares.com contact form and we will run free vulnerability tests for you.
This will allow you to identify your network vulnerabilities and open ports etc.
REPLY ON YOUTUBE
Thanks again, last year after qlocker Eddie was adamant that myQnapCloud was safe and I believe the issue was upnp allowing access a hard coded back door.
Do you both still feel myQnapCloud is safe ?
REPLY ON YOUTUBE
Really enjoyed this especially since they got me too. Thank you. Small piece of feedback – it’d be great if you gave Edward a bit more of a chance to speak at times. There are sections where it seems he’s just on the receiving end of a long lecture, as opposed to part of the conversation.
REPLY ON YOUTUBE
Rip out the DOM n install unraid on it 😀
REPLY ON YOUTUBE
Thanks Robert. Thanks Edward.
REPLY ON YOUTUBE
Could you do a video on how to secure your nas? Things like what port to put things on. Stuff like that?
REPLY ON YOUTUBE
im using a tricky way to remotely access my NAS files, by hiding them behind a nextcloud single user on a Pi thats not visible. not infallible, but takes breaking that, just to see files, not alter them or upgrade. if i have to upload, i have to remote into a computer and use other methods. rarely do i need to access files , but it can be done if i have to.
REPLY ON YOUTUBE
After using QNAP NAS devices for years – we’ve lost all confidence in the brand and it’s no longer on our supplier list.
REPLY ON YOUTUBE
TL:DW; version – its a security/ease of use trade-off. If you lock things down users find it too hard to use the features the vendor offers and berates them for it. If you open things up you give users the chance to shoot themselves in the foot, and some will.
Case in point being IoT “plug and play” devices. I was struggling to identify a device on my network today and discovered it had a password-protected web server – I guessed the password on the third attempt. You’d have thought vendors would have learned by now but clearly not.
Another interesting point given the mention of TrueNAS – Unraid ships with all security turned off by default. I think they’ve now realised they erred in doing that, but don’t seem to be in any hurry to fix it. I’ll be keeping any NAS behind a VPN. Wish I could do the same thing with Plex but it seems to need an opening to work properly, so I’ll have to isolate it on a VLAN.
REPLY ON YOUTUBE
One of the mistakes that QNAP made on this was that they actually identified and problem and issued a fix before the attack. But they didn’t make the update mandatory (they can override the user desire on when to take an upgrade). Users that had manually done the upgrade like myself or ones that didn’t have their NAS exposed to the Internet were fine. But other users were hijacked.
REPLY ON YOUTUBE
I did enjoy the video. I got a month ago a TVS-H1288X. We wouldn’t be talking about this if everyone had updated their NAS. QNAP needs to have a shout mode that you can’t miss if the patch fixes a vulnerability. The lack of organized information as not only to what to do but why? Example Port 443. It is recommended to change it but what range and why change it. I assume port scanners don’t deviate from assigned ports and look for low honing fruit. So by changing to 478 it is put out of the scanner range? If we do a router port forwarding to use QBelt on the NAS is that a direct open door to get into the NAS? I am guessing no otherwise why do assigned ports exist. At moment because of questions I have port forwarding off therefore I can’t use QBelt VPN which we are told it safe. My point is there needs to be a source that explains all of this that we can read. I am an engineer and programmer. First thing I did was set up QBelt to my android phone. UPnP was off from beginning. I have turned off myQnapCloud as I am unsure of where it stands safety wise. Has it been broken before? I even bought a certificate from Qnap and installed it. I think you should step in detail on each part of these security setting. What to change? Why you do it. And where to get more if on it. Love your videos
REPLY ON YOUTUBE
Data (physical or electronic) is arguably the most important thing you own the protection of it it more important than money.
If I loose a $50 note it can be replaced with any other $50 note the thing that makes it unique, the little string of numbers in the corner or any stains or creases are not what gives this value to you.
Conversely if you loose 50mb of data it can’t be replaced with any old 50mb of data as it’s uniqueness IS where the value was held. It is by definition irreplaceable/ priceless.
When average joe numpty buys an external HDD, NAS OR starts doing some form of online cloud storage or backup they have stumbled into the realisation that data holds value.
Often it’s a result of learning the hard way and loosing something.
NAS brands really should be held to account for some things but like you say not all.
From a consumer protection point of view, is it fit for purpose? Does it do everything it was advertised to do? Was it free of defects?
I buy a NAS, follow their instructions for setup while using the drives they recommend.
My expectations are:
– My data will be stored there without risk
– My data will be available using ALL advertised methods without putting it at risk
– I will be prevented from accidentally impacting the above two things.
During the setup process there should be a “most users” option that walks you through a VERY simple wizard (most users are not as smart as they think they are… see Dunning-Kruger effect).
Lock out or at least require a certain level of knowledge to unlock the most advanced features. Maybe a big warning when you select advanced option a big simple warning saying “by clicking this we no longer warrant the safety and security of your data” The stuff a car owner should touch is yellow under the bonnet of most cars now. Oil, wiper fluid, etc…
Also as joe numpty does not understand the difference between redundancy, backup etc etc. prompting them to locally encrypt and purchase a offsite data storage plan, backup to another offsite NAS or set up automatic email reminders for periodic backups.
Updates should always come with a have 3 options:
1. Update instantly on release. Early adopters on the bleeding edge (called that for a reason) “the is an update available and will be installed in x hours unless you hit cancel”
2. Delayed update (default most users). There is a new update available it’s currently being installed on some systems. This update will be automatically installed on this hardware after 30 consecutive days of bug free operation globally”. In this mode critical exploit patches are able to be forced if it impacts the last auto update.
3. Auto update off. Notifications on.
I think it’s absolutely NUTS that people give any nas company any form of slack for not treating your data at least as valuable as a bank treats your money. DONT share your pin, unusual behaviour lockdowns of accounts, etc.
Hard to type all this crap on a mobile phone.
REPLY ON YOUTUBE
Great Discussion! Driver’s license…????????????
REPLY ON YOUTUBE
Absolutely, I bought it for the hardware. Not always as inexpensive as I’d like — TS-873A vs 873-AU come to mind.
Is QNAP safe? Well, when it’s a NAS not an iNAS … mostly. I mean, there’s an IOT vector, but this is an IOT issue — does QNAP need to make its NAS safe against a determined in-network hacker? The IOT threat is just a whole nother topic….
The problem is that they market their internet-connectivity, and they need to stop doing that until they get their house in order, because they don’t have their house in order. Their responsiveness to CVEs has been lackluster at best, bordering on dangerously irresponsible. Security concerns are not as front-and-center as they should be. And magic, hard-coded backdoors in software is so gigantically awful — that stuff never should have been checked in to anything that ships to a customer. Astonishingly terrible.
REPLY ON YOUTUBE
Good discussion! But their privacy policy is what drove me away!
REPLY ON YOUTUBE
Great discussion. I like how you alluded to the “everyday man.” The reason I gravitated from Synology to QNAP was #1) Hardware comparison but most importantly #2) Capability to do more thanks to the software’s ability to have a lot less guardrails allowing me to do more.
I am by no means an IT expert, but I want the most hardware for my money and the software capabilities to do it. I also learned early on YOU HAVE to absolutely!!! know what you are getting yourself into before opening up your network with any NAS.
REPLY ON YOUTUBE
There is only one important rule. Never expose your NAS to the internet…until you know exactly what you are doing! Anyway, and always remember, a NAS is NO backup (RAID is not enough backup, either)!
REPLY ON YOUTUBE
Probably time for everyone to realize that these boxes are not good enough for external access. I have 3 qnap boxes and would never expose them to the outside. You want to go outside, go with the big boys like Azure. Qnap is not up for the job. It is fine for your LAN and leave it there.
REPLY ON YOUTUBE
As regarding the backup, one of the reason’s I am looking at buying a NAS is to allow me to put one in my home and one in my parents home, and allow us to both sync our data to have an off site backup.
But this means both need to be exposed on the internet to allow the sync. In this case it I think it makes sense to have both of these to be using the same platform as this includes software to sync.
However if I chose QNAP it is the process of wanting to get the backup capabilities that is exposing me to the data risk.
I am a software developer, (i.e. the worst person in this case since I know enough to be dangerous), but am no ‘Locksmith’, so would really welcome better hand holding and explanation of what the various features are actually doing behing the scenes and what the risks are.
REPLY ON YOUTUBE
QNAP need to open and honest about what vulnerabilities in what software exist on all of their models. If you fix the vulnerabilities sooner via auto-update (and not all vulnerabilities need reboots) then they wouldn’t be in this situation.
REPLY ON YOUTUBE
How about a step by step guide to secure your qnap nas?
REPLY ON YOUTUBE
No, absolutely, NO
REPLY ON YOUTUBE
Safe to save garbage files I guess.
REPLY ON YOUTUBE
I have an older TS-469 Pro running 4.3.4, so I guess my NAS is somewhat obsolete in terms of available applications such as Security Counselor
REPLY ON YOUTUBE
I don’t have the QuFirewall and the SSecurity Counselor available sadly, at least it just doesn’t want to install. Probably because my NAS is way too old, running QTS 4.2.6
REPLY ON YOUTUBE
WOW. Nice find here!! Great video.
REPLY ON YOUTUBE
Thank you. Wish I’d seen your recommendations BEFORE the Qlocker attack.
REPLY ON YOUTUBE
hello sir your videos is so helpfull for me but i am confuse with how to configure alnet ssystem software with qnap nas storage i have configure qnap nas storage raid 6 with 4tb *12 hdd 1 hdd in spare but i am able to see live video but not able save nas storage so can you help me how to add path in qnap nas storage for save recording. Thanks,Jerry Upadhyay
REPLY ON YOUTUBE
If Norton or Bitdefender is installed as your main antivirus, will they be able to work on Qnap NAS? Instead of MacAfee, which for instance I don’t like.
REPLY ON YOUTUBE
Dude. Just a side note after watching 150+ videos. I have NEVER heard “noise in the background” so please stop apologizing for it. Not. Once. Ever.
REPLY ON YOUTUBE
I wish I saw this video before ???? apparently Qnap got hit with a massive ransomware attack this year and I had no idea. My files are all encrypted by some hacker asking for Bitcoin in exchange for passwords ????
REPLY ON YOUTUBE
Changing the default port does not enhance security. Security by obscurity. Port scanners can detect open ports it might fool some scripts.
Most people who serious about securing administrative interfaces dont expose them directly to the internet period.
Thats terrible terrible terrible security pratice.
A seperate vpn server with a dedicated vlan for admin is what you should be using to secure the admin interface and remotely managing the nas.
Example
Setup vlan 100 for management
Setup vlan 201 for cifs
Setup vlan 202 for iscsi
Setup vlan 300 for public network (internet)
Setup vpn server in dmz with one arm into the public network (300) another arm into vlan 100.
Setup logging and auditing.
Ensure 2fa exists for vpn service.
The qnap should have ports trunked with vlan 100,201,202 or dedicated ports.
Assign the services ip addresses in each of the ranges.
I never ever bother changing port numbers it simply offers very little security and may just elude some scripts scanning on certain ports
REPLY ON YOUTUBE