If you own an Asustor NAS and are reading this – CHECK IT NOW
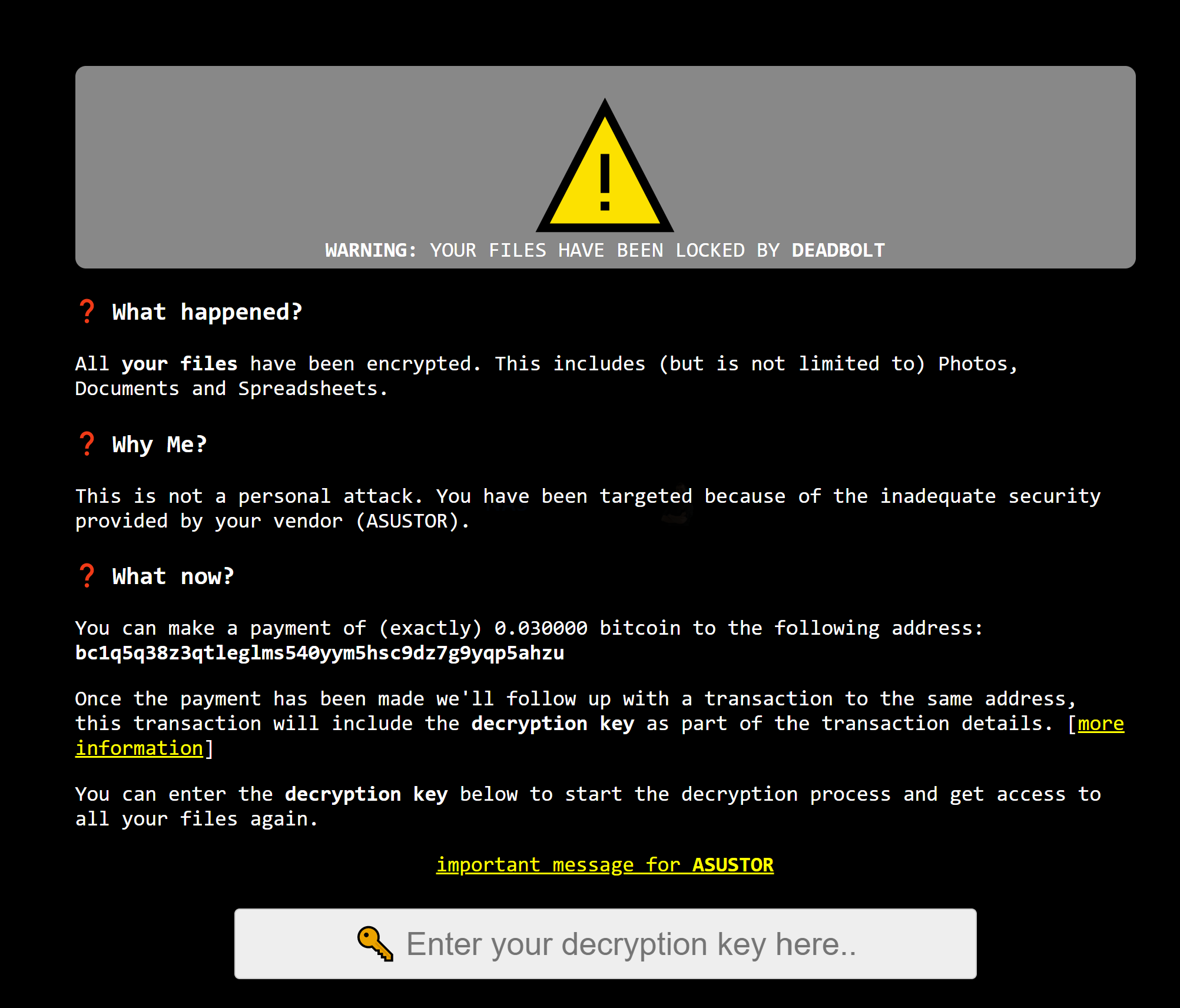
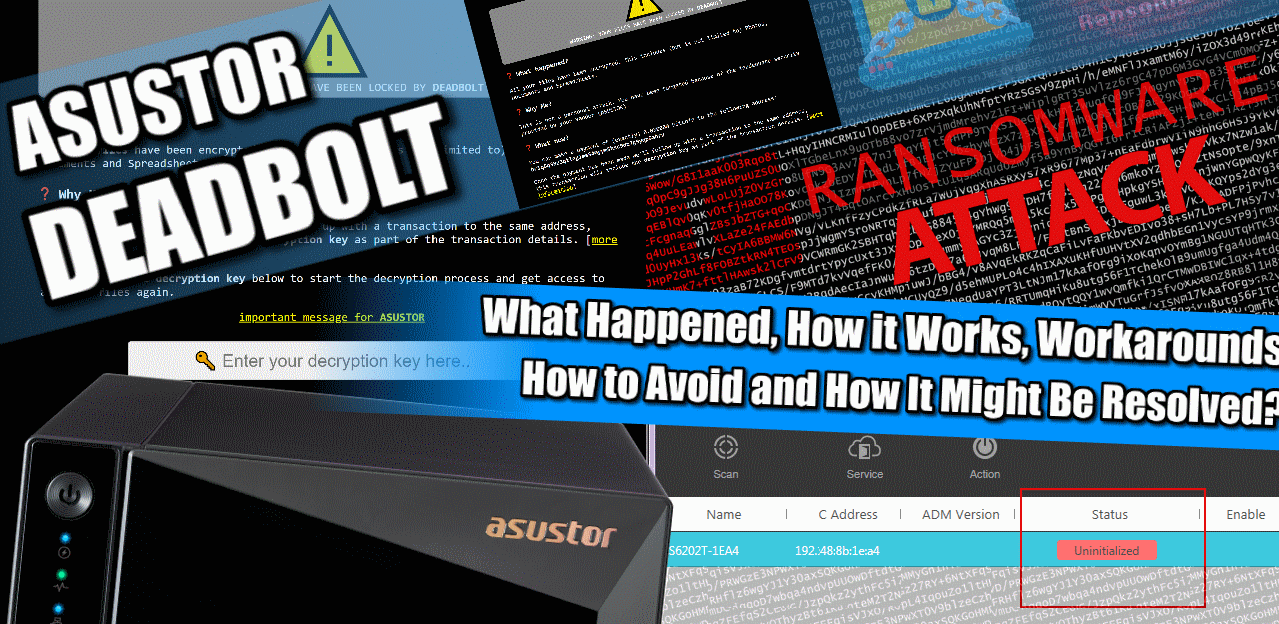
Original Article – As of around 1 hour ago, multiple users online are reporting that their Asustor NAS systems have been attacked by ransomware known as Deadbolt. Much like the ransomware attack of QNAP NAS systems of the same name, this is a remote-command-pu#sh encryption attack that takes advantage of a vulnerability in the system software to command the system to encrypt the data on the NAS system, but with the added twist in this recent update of adding a new login GUI style space screen asking for 0.03BTC.
Updated 06:50 GMT

Asustor has issued the following statement and recommendation for those who are (or believe they have been affected by the Deadbolt ransomware):
In response to Deadbolt ransomware attacks affecting ASUSTOR devices, ASUSTOR EZ-Connect, ASUSTOR EZ Sync, and ezconnect.to will be disabled as the issue is investigated. For your protection, we recommend the following measures:
Change default ports, including the default NAS web access ports of 8000 and 8001 as well as remote web access ports of 80 and 443.
Disable EZ Connect.
Make an immediate backup.
Turn off Terminal/SSH and SFTP services.For more detailed security measures, please refer to the following link below:
https://www.asustor.com/en-gb/online/College_topic?topic=353If you find that your NAS has been affected by Deadbolt ransomware, please follow the steps listed below.
1. Unplug the Ethernet network cable
2. Safely shut down your NAS by pressing and holding the power button for three seconds.
3. Do not initialize your NAS as this will erase your data.
4. Fill out the form listed below. Our technicians will contact you as soon as possible.https://docs.google.com/forms/d/e/1FAIpQLScOwZCEitHGhiAeqNAbCPysxZS43bHOqGUK-bGX_mTfW_lG3A/viewform
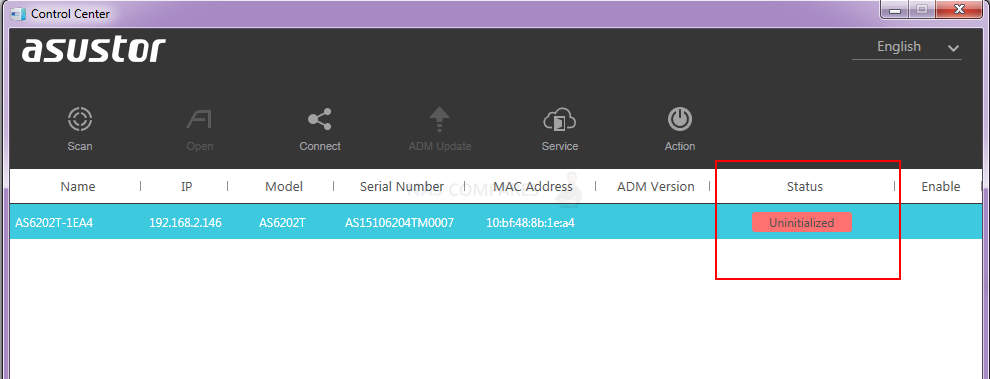
Regarding filling out the technical support form, this is likeLy to help the brand identify the scale of the issue, but also allow a faster sharing (to those affected) of any recovery tools that might be possible. However, the culprit is looking increasingly like the EZ Connect Asustor Remote service. This has been further backed up by the fact that the official Asustor ADM demo page has also been hit by the Deadbolt ransomware (now taken offline). Additionally, many users who powered down their device during the deadbolt attack, upon rebooting their NAS system have been greeted with the message in the Asustor Control Center application that their system needs to be ‘re-initialized’. The most likely reason for this is that during the encryption processes, the core system files are the first files that get targeted and if the system was powered down/powered off immediately during this process, it may have corrupted system files. We are currently investigating if a recovery via mounting a drive in a Linux machine is possible (in conjunction with roll-back software such as PhotoRec).
If your Asustor NAS is in the process of being hit (even if you simply suspect it) as your HDDs are buzzing away unusually (and the HDD LEDs are flickering at an unusual hour), then it is recommended that you head into the process manager and see if the encryption process has been actioned by Deadbolt. The following suggestion of action was suggested by NAScompares commenter ‘Clinton Hall’ :
My solution so far, login vis ssh as root user
cd /volume0/usr/builtin
ls
you will see a 5 digit binary executable file For me it was 22491. I use that in the following command to get the process ID
ps | grep 22491
from this I got the Process id 25624. I kill that process
kill 25624
I then remove the binary file
chattr -i 22491
rm -f 22491
Now, restore the index as above
cd /usr/webman/portal
chattr -i index.cgi
rm index.cgi
cp index.cgi.bak index.cgi
Now for the fun part…. a LOT of file had been renamed (not encrypted) to have .deadbolt appended to the end of the filename… So rename them back
(note, you may want to do this folder by folder and check it is working). The following will do for the entire /volume1
cd /volume1
find . -type f -name "*.deadbolt" -exec bash -c 'for f; do base=${f##*/}; mv -- "$f" "${f%/*}/${base//.deadbolt/}"; done' _ {} +
After these are all renamed, everything should work. Probably a good idea to reboot to restart the services etc.
Also, I’m not sure if the above will definitely traverse the .@plugins etc… so I did this manually
cd /volume1/.@plugins
find . -type f -name "*.deadbolt" -exec bash -c 'for f; do base=${f##*/}; mv -- "$f" "${f%/*}/${base//.deadbolt/}"; done' _ {} +
If you have not been hit, I would recommend you action the following from within your Asustor NAS (or better yet, where possible) power the device down until an official statement and a possible firmware patch is issued.
- Disable EZ Connect
- Turn off automatic updates
- Disable SSH (if you do not need it for other services)
- Block all NAS ports of the router, and only allow connections from inside the network
Updated 19:30 GMT
More details are coming up and it looks like (at least looking at the messages on the official Asustor Forum and Reddit) the vulnerability stems from a vulnerability in EZConnect that has been exploited (still TBC). User billsargent on the official Asustor forums has posted some useful insights into how to get around the login screen and also details on the processes:
Take your NAS OFF of ezconnect. Block its traffic incoming from outside.
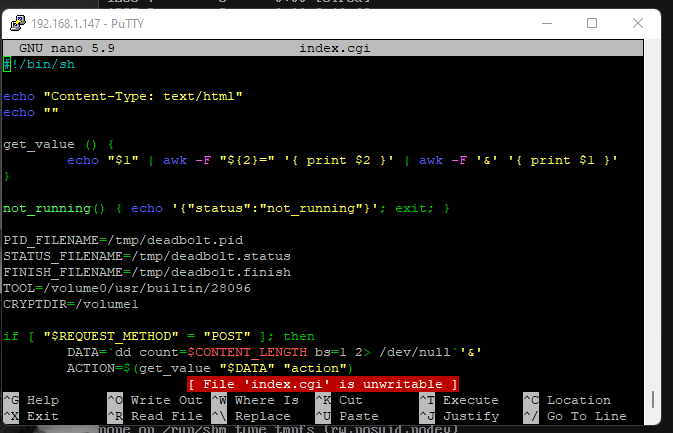
This overwrites the index.cgi with their own. In /usr/webman/portal there is a backup copy of your index there.
To remove theirs, you need to chattr -i index.cgi and replace it with the backup.
But you’ll also have to kill the process. Mine had a process that was just numbers running. I killed it, then deleted it. In /tmp there was another binary that was just numbers.
This is probably not possible to fix without a reset but you can get back into your portal with the above info. Right now though mine is still immediately replacing the index.cgi.
And:
I am assuming you have ssh capabilities? If so you just need to ssh in and login as root and run these commands. This should help you get back into the portal.
cd /usr/webman/portal
chattr -i index.cgi
rm index.cgi
cp index.cgi.bak index.cgiIf you look at the index.cgi they created before you delete it, its a text script.
I am still in the investigative stages but nothing in my shares have been locked up with this yet. Just things in /root so far.
I’ve pulled out a ton of LTO tapes to backup my data. I think this is going to require a full reset. I hope asustor releases a fix for this but I will never again allow my NAS to have outside access again.
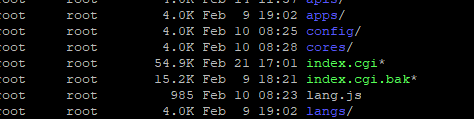
For clarification. This is what my /usr/webman/portal directories looked like. the .bak file is the original index.cgi.
I apologize if my posts seem jumbled up a bit. I’m trying to help and also figure this out as well. So I’m relaying things as I find them in hopes that others will be able to at least get back to their work.
Thank you to Asustor user billsargent for the above and full credit to him on this of course.
(Continuing with the Original Article from 21/02 17:30 GMT)
Although it is still very early in the actioning of this encryption attack, these attacks are slowly starting to emerge on forums right now, as well as twitter, see below:
やばい!!家のASUSTOR製NASがDEADBOLTとか言うランサムウェアに攻撃された!QNAP製のNASに最近入るってのは見たけど、まさか自分のNASもやられるとは…
そこまで大事なデータ入れてなかったのが不幸中の幸いだけど700GBくらいのデータ死んだのショックASUSTOR NAS使ってる人すぐネット切断した方がいい pic.twitter.com/gBFu8yx4hG— sudara (@sudara_hodara) February 21, 2022
Additionally, this splash message contains a call-out to Asustor themselves (much like the QNAP NAS deadbolt attack) that states a message and a link for the brand to open a discussion (i.e pay) towards a master key and details of the vulnerability they have exploited:
“All your affected customers have been targeted using a zero-day vulnerability in your product. We offer you two options to mitigate this (and future) damage:”
Details are still emerging, so I will keep this article short and sweet for now (and add more later as details emerge), if you own an Asustor NAS drive, check it immediately! Regardless of whether you have enabled remote access via EZConnect or not (as that is not necessarily the key to the attack vector and possible remote DLNA port changes by your system, for example), check it now and ideally disconnect it from the internet. Currently, there is not enough information to ascertain if this relates to a case of ‘out of date firmware’ having an existing vulnerability or something inherent in the current firmware. Regardless, check your system and where possible, disconnect it from the internet until further details are confirmed here, on reputable sites such as Bleeping Computer or via direction from Asustor themselves.
Once you log into your NAS, check your logs and check your processes. If you have the means to backup to a NEW location, do so. DO NOT overwrite your existing backups with this backup unless you are 100% certain you have not been hit by deadbolt ransomware.
What to Do if you have been hit by the Deadbolt Ransomware
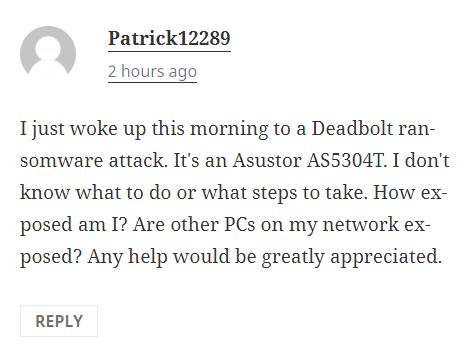
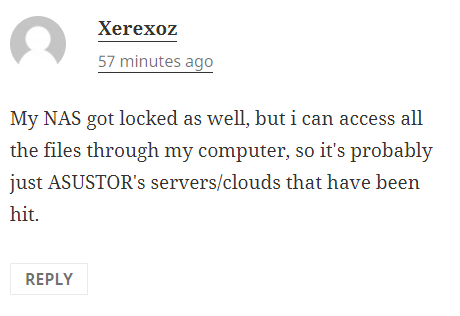
If you have been hit by the vulnerability, you will likely be unable to connect remotely with your NAS files/folders. Even if you can, you need to check whether you can open them or they have been encrypted to a new format (the extension/ .type or file will have changed). The following users commented onreddit and there are similar threads that we can see on their setup and how they got hit.
|
|
|
|
|
|
|
|
IF you still have access to your files, get your backups in order!!!!!
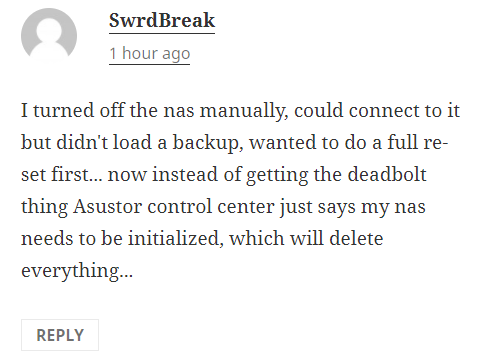
Otherwise, if you have been hit by this, then you need to disconnect your system from the internet. Killing any processes in the task manager is an option HOWEVER do bear in mind that doing so might corrupt currently encrypting files and therefore stop any kind of recovery. I am checking with a couple of affected users (as well as reaching out to Asustor as we speak to see if a suitable course of action can be recommended. Some users who have restarted their system or immediately pulled the power and rebooted have found that their system now states that it needs to be reinitialized.
One big factor to keep in mind right now is that not is still unclear if a) the deadbolt ransomware can be killed as a system process in the Asustor control center (I do not have an Asustor NAS that is affected in my possession right now) and b) if switching your system off DURING the deadbolt attack can lead to the data being unsalvagable as the encryption is partway through. So, disconnect from the internet (physically and via EZConnect for now) and if you can see youR CPU usage spiking and/or your HDD LEDs going nuts, you are likely being hit.
My Asustor NAS is Saying it is Uninitialized
DO NOT RE-INITIALIZE YOUR NAS. At least not yet, if you have already powered your NAS as a reaction to the attack (understandable, if not the best choice without knowing the full attack vectors or how this affects the encryption) and you are being greeted by the option to reinitialize in the Asusto Control Center application, then power the device down again. But again, I only recommend this action right now for those that already reacted to the attack by shutting down their system/restarting already post-attack
If I am not hit by Deadbolt, Should I disconnect my Asustor NAS from the internet?
For now, YES. As the act vectors are not clear and there are reports from some users right now that state that they had the latest firmware, they were still hit, there is so much unconfirmed info here to allow remote access (in my opinion) and until further info is made available, I strongly recommend disconnecting your Asustor NAS from the internet (wire AND via the software settings) and getting your backups in order.
I will update this article soon as more information becomes available.
| Where to Buy a Product | |||
|
|
    
|

|
VISIT RETAILER ➤ |
 |
    
|

|
VISIT RETAILER ➤ |
We use affiliate links on the blog allowing NAScompares information and advice service to be free of charge to you. Anything you purchase on the day you click on our links will generate a small commission which is used to run the website. Here is a link for Amazon and B&H. You can also get me a ☕ Ko-fi or old school Paypal. Thanks! To find out more about how to support this advice service check HERE
UGREEN DXP4800 PRO NAS Review
Minisforum G7 Pro Review
CAN YOU TRUST UNIFI REVIEWS? Let's Discuss Reviewing UniFi...
WHERE IS SYNOLOGY DSM 8? and DO YOU CARE? (RAID Room)
UniFi Routers vs OpenWRT DIY Routers - Which Should You Choose?
WHY IS PLEX A BIT S#!t NOW? IS 2026 JELLYFIN TIME? (RAID Room)
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.





DISCUSS with others your opinion about this subject.
ASK questions to NAS community
SHARE more details what you have found on this subject
IMPROVE this niche ecosystem, let us know what to change/fix on this site