Terramaster NAS Devices Being Targetted by Ransomware – IMPORTANT
If you are a current Terramaster NAS user, then immediately log into your system and check that your data is in order. In a little over the last week, numerous users have been reporting that their TNAS systems have been hit by ransomware attacks (bearing similarity in structure and protocol to the eCh0raix attacks that were attempted/executed on QNAP and Synology NAS systems in 2020/2021) and a considerable number of users are reporting that the data has now been encrypted, with the usual ranSom note for payment (bitcoin to X wallet etc) left for the user’s attention. Despite any internet-accessible device always having to take into consideration (and preparation) for the possibility of an outside intruder getting in, there are questions being raised about the extent to which this has been the fault of Terramaster to secure their systems, re-enforce security protocol/workflows onto their audience (many of whom purchasing their value series devices with a domestic level of technical knowledge) as well as questions being raised about vulnerabilities in the uPnP (previously raised in April 2021). Here is a breakdown of everything we know so far at the time of writing.
The Terramaster NAS Ransomware Attack – The Story so far and what Terramaster Recommend You Do
On the 11th Jan 2022, Terramaster raised this post on their official forum and news pages here regarding reports of ransomware attacks on TNAS systems. The key points and recommendations for actions from that post were as follows:
Recently, we have received reports that some TNAS devices have been attacked by ransomware. Based on the case study, we preliminarily concluded that this was an external attack targeting TNAS devices. To keep your data safe from attack, please take action immediately!
We suggest you take the following countermeasures:
1. Upgrade your TOS to the latest version;
2. Install good anti-virus software on your computer, TNAS device and router to help you detect and resist malicious threats;
3. Disable port forwarding on your router.
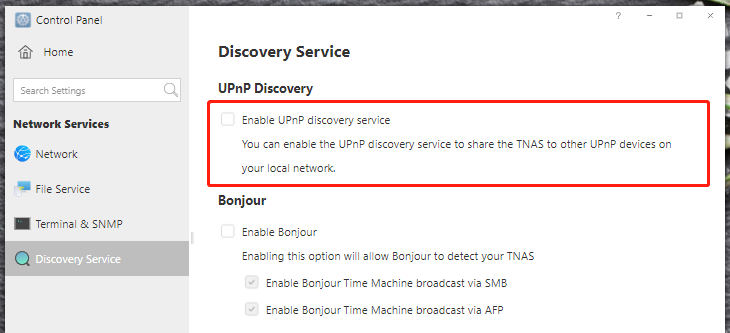
4. Disable the UPnP function on your TNAS.
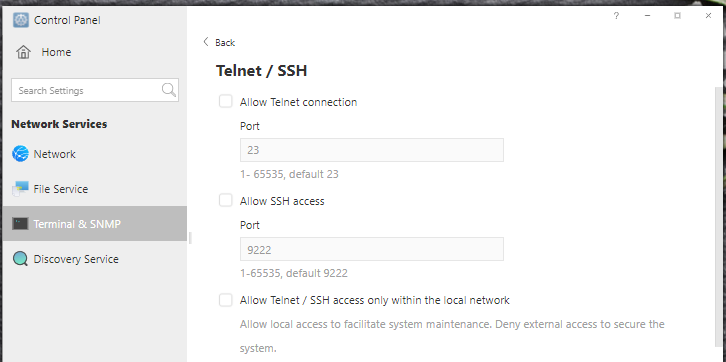
5. Disable RDP, SSH and Telnet when not in use;
6. Change the default port of FTP.
7. Set a high security level password for all users;
8. Disable the system default admin account, re-create a new admin account, and set an advanced password;
Note: For versions after TOS 4.2.09, you can set the administrator account without using the default admin username when installing the system. If it was upgraded from a version before TOS 4.2.09, you need to reset the system configuration, then you can customize the user name.9. Enable firewall and only allow trusted IP addresses and ports to access your device;
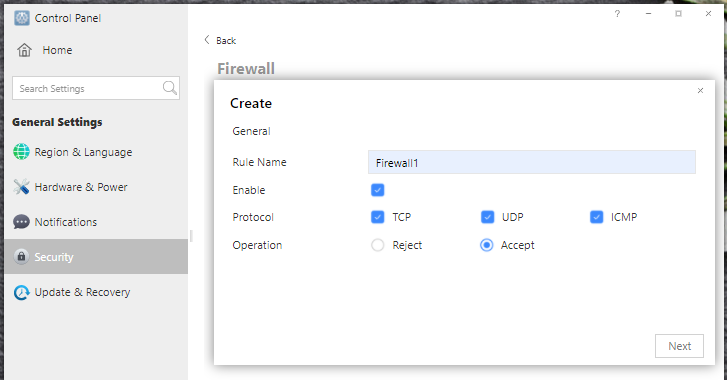
a. Go to Control Panel > General Settings > Security > Firewall.
b. Create a firewall rule and choose the operation of allow or deny.
c. Fill in the IP range you allow or deny access to.
10. Avoid using default port numbers 5443 for https and 8181 for http;
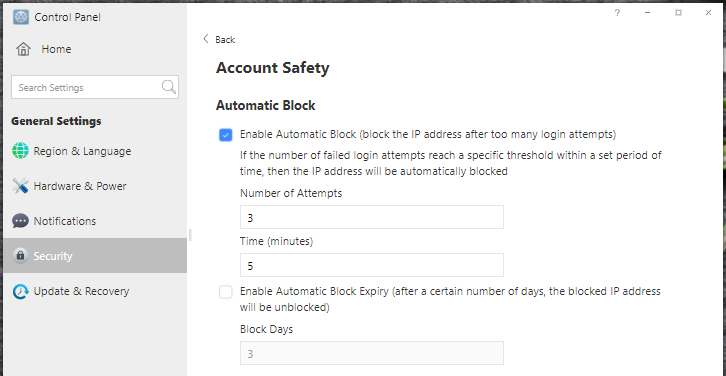
11. Enable automatic IP block in TOS Control Panel to block IP addresses with too many failed login attempts;
12. Backing up data is the best way to deal with malicious attacks; always back up data, at least one backup to another device. It is strongly recommended to adopt a 3-2-1 backup strategy.
If unfortunately, you have found that your data is infected by ransomware:
1. Disconnect your computer and TNAS device from the Internet immediately;
2. Before restoring data, thoroughly remove the infection in the computer system and TNAS; You need to restore your TNAS to factory settings and completely format all your hard drives.
Now, how did this occur? It seems like details are being circulated regarding a vulnerability that was found online in December. A remarkably comprehensive and detailed breakdown of how this vulnerability into a Terramaster was exploited can be explored here, published in December 2021 – https://thatsn0tmy.site/posts/2021/12/how-to-summon-rces/
There has been several criticisms raised against Terramaster and their recommendations that were raised, as well as how loud the brand is being, outside singular forum posts, to raise awareness of this. Criticisms range from not adequately explaining methods of actioning the recommendations (such as how to disable the admin account and how it is not simply a case of an on/off option accessible via a separate account immediately to all) or detailing how these changes will impact system use afterwards. An official Terramaster support team member has responded:
First of all, it is very sad that this happened to all the victims. Terramaster has been working hard to strengthen the security of TNAS devices. Various security tools are integrated in TOS, and we also provide you with various possible countermeasures. However, once your device is exposed to the Internet, there is a risk of being attacked. Because you are dealing with very professional hackers, hackers will do anything to gain profits. Only one method is not enough to avoid attacks. In order to improve the security level, multiple security measures must be adopted. Even so, there is still no guarantee that your device is completely secure. A large number of devices are attacked by ransomware every day, including Terramaster, QNAP, Synology, and even the servers of some large enterprises or government agencies.
https://unit42.paloaltonetworks.com/ech … ware-soho/If you expose your device to the internet but don’t want to do anything, you may be one of the victims. After studying the cases of individual victims, we found that the hackers continued to attack the victim’s device through the ftp service for more than dozens of hours. If you use the system default port, low security level account and password, you are very likely to become a victim. However, ftp is definitely not the only way to attack, please act immediately and follow our countermeasures one by one to reduce the risk of being attacked.
We will continue to study how the ransomware invaded TNAS devices and will release updates in a timely manner.
Now, one recommendation that has raised particular scrutiny is disabling the default admin account. Many users highlight that Disabling the default administrator account is easier said than done as it is dependant on your installation and version of TOS. To disable the admin account (taken from the official Terramaster official forum and their service team), you need to be a new user with a new TOS installation from 4.2.09 or later versions. For all users with TOS versions installed before 4.2.09 or update to a later version is not possible to disable the default admin account, you need to re-install a new TOS later than 4.2.09. If you are considering re-installing TOS fresh on your terramaster (for security or as a last alternative to get your system storage back without paying ransomware payments regardless of lost data, a guide from terramaster to recover can be found here – https://forum.terra-master.com/en/viewtopic.php?f=76&t=423
Additionally, Terramsater is currently working on TOS 5.0, the latest version of their software (currently still in early alpha/beta testing) and some users on the official forum are highlighting that jsut waiting on this new full release is preferable.
If you have been hit by the Terramaster Ransomware Attack?
Currently, it seems (at least at the time of writing) that if your Terramaster NAS has been hit by this ransomware, there is little to no 3rd party tool/decryption solution available online. However, much like when QNAP was hit by eChoraix and Qsnatch, over time some solutions were made (some in executional form such as QRescue with PhotoRec addons) and some in reverse engineering methods might be possible, so if you have important data that you hope to have recovered, but bulk at the prospect of paying the attackers, it might be worth moving this data off the NAS and onto another storage system (USB, Cloud, offline server, etc) in the meantime. Of course, if you still wish to use your terramaster NAS system, it will require a system reset/format. Indeed, Terramaster themselves raised it (rather bluntly one might say) in their official forum regarding the process of the malware attack in this (and most) cases and the result, if no decrypted can be put together (as has been the case on a few of the 2020/early-2021 ransomware attacks on other platforms such as QNAP:
Since the ransomware creates a random sequence as the AES Key, and then encrypts the previously generated AES Key with the locally generated RSA public key, and uses the AES CFB algorithm to encrypt the files in the infected device, each encrypted device uses a different key. Likewise, once files are encrypted by ransomware, there is usually no way to decrypt them. If your data is so important that you need to get it back, paying the ransom might be the only way. It’s worth reminding that even paying the ransom is not a 100% guarantee that your data will be rescued. If you are not willing to pay the ransom, intend to give up the encrypted data. You can go to Control Panel > Storage, delete volumes and storage pools, and restore the system to factory settings.
If I was in the shoes of someone who had their data encrypted, without a backup in place, then (where possible) I would still hold out for recovery methods. It was rightly raised by Charlie Crocker on the Terramaster forum that decryption of previous NAS ransomware is still ongoing and so if you have the means to move this data elsewhere (along with the ransom .txt, as this is often incredibly useful for identifying the encryption campaign method later), I would recommend that – rather than wiping it all! But I can appreciate that this can be an expensive option.
Criticism of Terramaster in their Response to this Ransomware Attack
Currently, Terramaster is being heavily criticized on their own forums for their handling of this. Understandably, some users were already unhappy with the raised reminders if UPnP weaknesses in a previous version of TOS. An older vulnerability in the Terramaster NAS system was reported in April 2021. As it turns out though, their NAS systems are accessible across the entire internet via the UPnP protocol. Universal Plug and Play (UPnP) is used by an infinite number of network devices, including NAS, routers, computers, gaming consoles, printers, mobile devices, IoT devices, and many more. A full breakdown of this vulnerability in TOS last year was covered over on StorageReview here – https://www.storagereview.com/news/terramaster-nas-vulnerability-found-over-upnp/
This is a developing matter and I will continue to update this article and compile it in a video over on YouTube shortly (when available, it will be published below).
📧 SUBSCRIBE TO OUR NEWSLETTER 🔔🔒 Join Inner Circle
Get an alert every time something gets added to this specific article!
This description contains links to Amazon. These links will take you to some of the products mentioned in today's content. As an Amazon Associate, I earn from qualifying purchases. Visit the NASCompares Deal Finder to find the best place to buy this device in your region, based on Service, Support and Reputation - Just Search for your NAS Drive in the Box Below
Need Advice on Data Storage from an Expert?
Finally, for free advice about your setup, just leave a message in the comments below here at NASCompares.com and we will get back to you. Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.
Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.

|
 |
UGREEN iDX6011 Pro NAS Review
Beelink ME PRO NAS Review
UGREEN iDX6011 Pro - TESTING THE AI (What Can it ACTUALLY Do?)
OWC TB5 2x 10GbE Dock, UGREEN NAS Surveillance Software, AceMagic Retro PCs, Gl.iNet Comet 5G @CES
What IS the Digiera OmniCore NAS? Is it Worth $599?
New UGREEN NAS Expansion, DXP4800 PRO NAS and eGPU Revealed
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.






DISCUSS with others your opinion about this subject.
ASK questions to NAS community
SHARE more details what you have found on this subject
IMPROVE this niche ecosystem, let us know what to change/fix on this site