QNAP Improper Authentication Mechanism Vulnerability Discovered and Patched – Update NOW
QNAP Systems, recently found itself at the center of another security scrutiny following the discovery of multiple vulnerabilities within its product software. Among these, a particularly critical vulnerability, designated as CVE-2024-21899, with a Common Vulnerability Scoring System (CVSS) score of 9.8, poses a significant threat to the security of numerous businesses and individuals relying on QNAP’s NAS solutions. This flaw, rooted in improper authentication mechanisms, potentially allows unauthenticated attackers to gain access to the devices over a network, compromising the integrity and confidentiality of the data stored within.
We discussed QNAP safety in greater detail previously in this article HERE, as well as this video HERE.
Normally, I would not create posts or videos focusing on individual reported CVE vulnerabilities, as this is a common occurrence that all NAS brands, including Synology, TrueNAS, Asustor, UnRAID, and others, regularly address by publishing updates on their respective security advisory pages. However, one of the CVEs reported in this recent disclosure stands out as particularly concerning. The severity and potential impact of this specific vulnerability merit a deeper discussion beyond the usual update advisories. It underscores a critical security risk that could affect a wide range of users and enterprises relying on these storage solutions. Given the potential ramifications of this vulnerability, it’s imperative to bring heightened awareness to our community, encouraging immediate action and a thorough understanding of the measures needed to mitigate the risk.
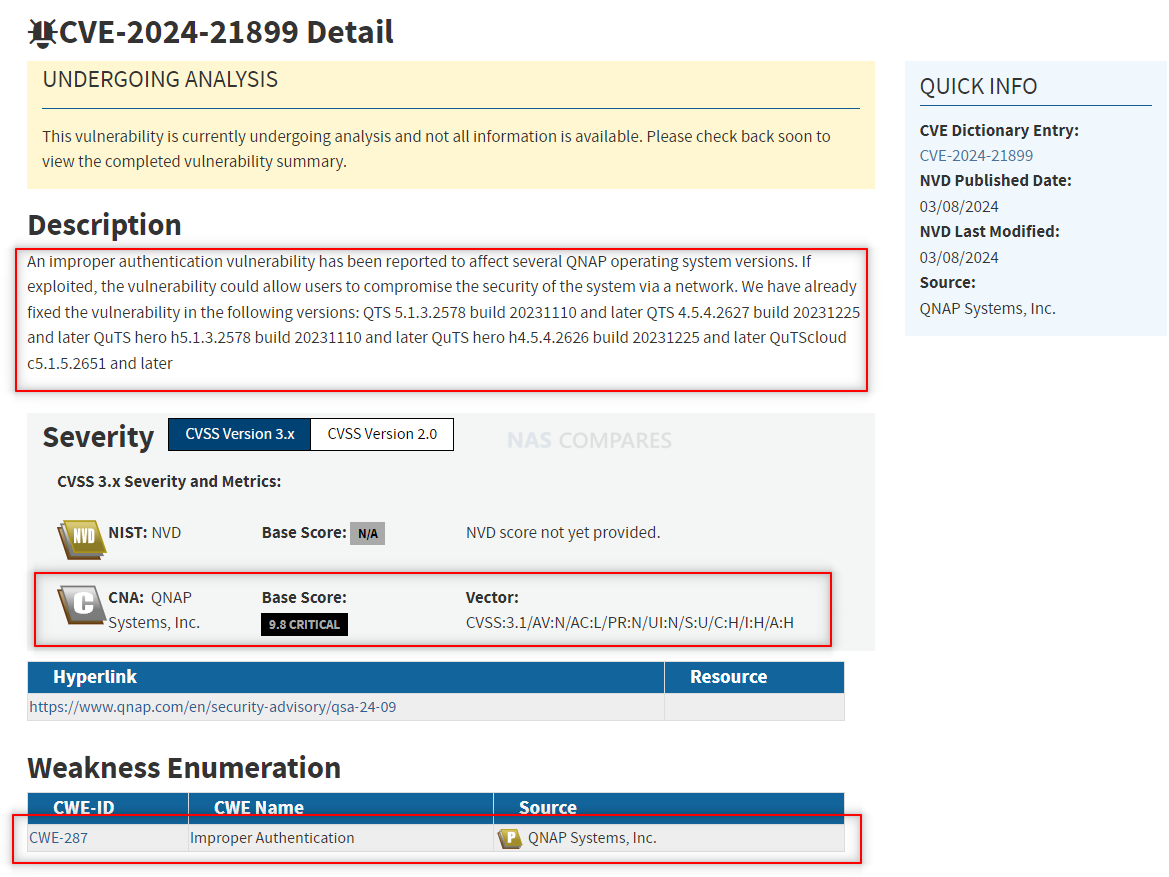
The gravity of CVE-2024-21899 is underscored by its capability to allow remote attackers to bypass authentication processes and execute malicious activities, including data theft, malware deployment, and further system compromise. This vulnerability impacts a wide range of QNAP’s offerings, including its QTS, QuTS hero, and QuTScloud products, highlighting a broad attack surface for potential exploitation. In response, QNAP has released patches for affected versions, urging users to update their devices to the latest firmware versions to mitigate the risk of exploitation.
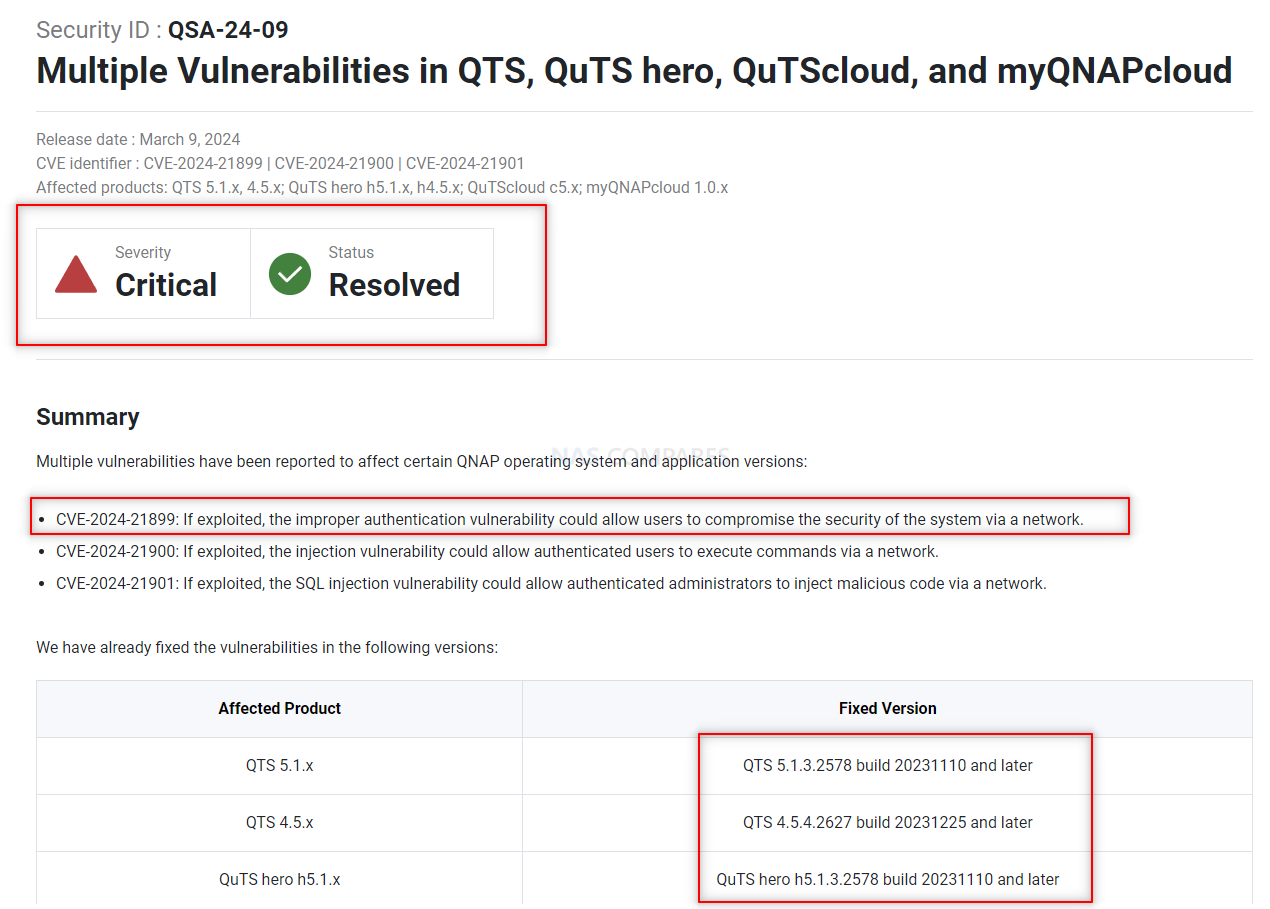
In addition to the critical CVE-2024-21899, QNAP has identified and patched two other vulnerabilities of medium severity: CVE-2024-21900 and CVE-2024-21901. These vulnerabilities, involving command execution and SQL injection, respectively, require authenticated access, making them less severe but still noteworthy. CVE-2024-21900 allows authenticated users to execute arbitrary commands over a network, whereas CVE-2024-21901 enables authenticated administrators to inject malicious SQL code. Patches for these vulnerabilities have been included in the latest firmware updates across QNAP’s product lines, including QTS, QuTS hero, QuTScloud, and myQNAPcloud.
QNAP’s history with security vulnerabilities extends beyond these recent disclosures, as the company’s NAS devices have frequently been targeted by ransomware campaigns. These incidents have underscored the attractiveness of NAS systems to cybercriminals, due to the valuable data they often contain. In the past, ransomware such as Qlocker and eCh0raix have specifically targeted QNAP devices, exploiting known vulnerabilities to encrypt user data for ransom. Such attacks not only result in immediate data access issues and potential financial loss for the victims but also highlight the critical need for robust security measures and regular system updates. QNAP’s continued efforts to patch vulnerabilities as they are discovered are crucial in this ongoing battle against ransomware. However, the persistence of threat actors in targeting QNAP devices emphasizes the importance for users to remain vigilant, applying updates promptly and adopting comprehensive security practices to safeguard their data against future attacks.
The disclosure and subsequent patching of these vulnerabilities serve as a critical reminder of the importance of maintaining up-to-date software on network-connected devices. Users of QNAP NAS devices are strongly encouraged to review their systems, apply the necessary updates, and regularly monitor for any new security advisories. This incident underscores the ongoing battle between cybersecurity professionals and threat actors, highlighting the need for vigilance, timely updates, and a proactive security posture to protect against evolving cyber threats.
Recommended Action for QNAP Users
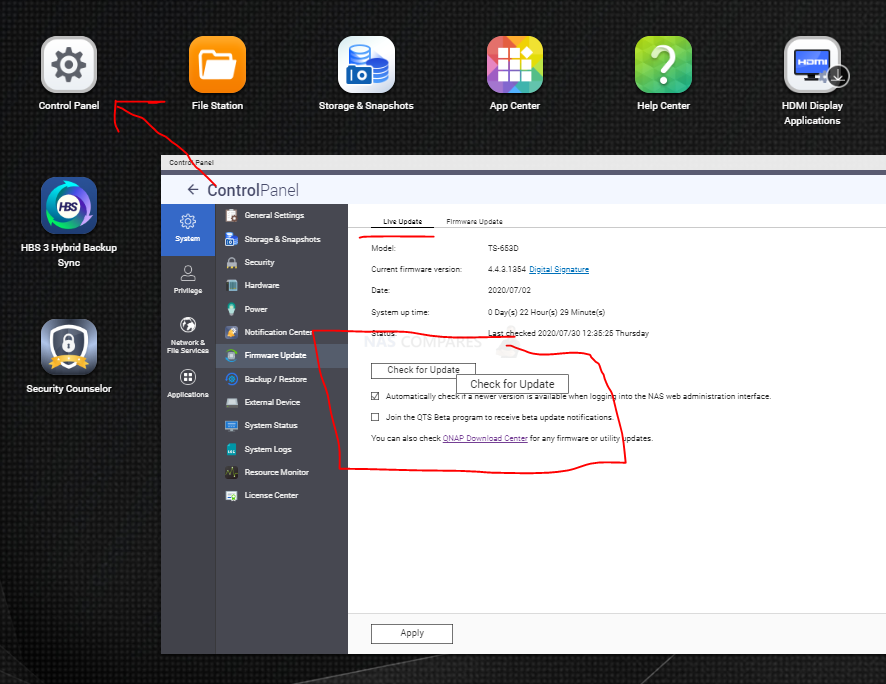
To secure your device, we recommend regularly updating your system and applications to the latest version to benefit from vulnerability fixes. You can check the product support status to see the latest updates available to your NAS model.
Updating QTS, QuTS hero, or QuTScloud
- Log in to QTS, QuTS hero, or QuTScloud as an administrator.
- Go to Control Panel > System > Firmware Update.
- Under Live Update, click Check for Update.
The system downloads and installs the latest available update.
Tip: You can also download the update from the QNAP website. Go to Support > Download Center and then perform a manual update for your specific device.
Updating myQNAPcloud
- Log on to QTS, QuTS hero, or QuTScloud as an administrator.
- Open App Center and then click
 .
.
A search box appears. - Type “myQNAPcloud” and then press ENTER.
myQNAPcloud appears in the search results. - Click Update.
A confirmation message appears.
Note: The Update button is not available if your myQNAPcloud is already up to date. - Click OK.
The application is updated.
Vulnerabilities And Exploits On Synology & QNAP NAS – Stay Updated!
(Click Below to Visit the NASCompares Confirmed NAS Vulnerability Pages)
📧 SUBSCRIBE TO OUR NEWSLETTER 🔔 This description contains links to Amazon. These links will take you to some of the products mentioned in today's content. As an Amazon Associate, I earn from qualifying purchases. Visit the NASCompares Deal Finder to find the best place to buy this device in your region, based on Service, Support and Reputation - Just Search for your NAS Drive in the Box Below
🔒 Join Inner Circle
Get an alert every time something gets added to this specific article!
Need Advice on Data Storage from an Expert?
Finally, for free advice about your setup, just leave a message in the comments below here at NASCompares.com and we will get back to you.
 Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.
Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.
TRY CHAT
Terms and Conditions


| Where to Buy a Product | |||
|
|
    
|

|
VISIT RETAILER ➤ |
 |
    
|

|
VISIT RETAILER ➤ |
 |
    
|

|
VISIT RETAILER ➤ |
 |
    
|

|
VISIT RETAILER ➤ |
We use affiliate links on the blog allowing NAScompares information and advice service to be free of charge to you. Anything you purchase on the day you click on our links will generate a small commission which is used to run the website. Here is a link for Amazon and B&H. You can also get me a ☕ Ko-fi or old school Paypal. Thanks! To find out more about how to support this advice service check HERE If you need to fix or configure a NAS, check Fiver Have you thought about helping others with your knowledge? Find Instructions Here
Best NAS for under $499
Best NAS for Under $250 (2025)
Minisforum N5 Pro NAS - FIRST IMPRESSIONS
HexOS Q2 Update - What's Changed?
5 Exciting NAS Coming Later in 2025
Beelink ME Mini vs GMKtec G9 vs CWWK P6 NAS Comparison
Access content via Patreon or KO-FI






I remember the same attack done at Synology, ransomware attack demanding 1.2 bitcoin, unfortunately I paid them and they gave the key and I unlocked all of my 10 years worth of files .
since then I unplugged my NAS from internet and don’t use its feature.
what synology did? they sent me $30 headphone… imagine that, I paid 1.2 bitcoin for cheap headphone.
I was considering Qnap until I find this video
REPLY ON YOUTUBE
No.
REPLY ON YOUTUBE
I have secured my QNAP and it has been safe until Saturday when I got hit by Deadbolt, but my most recent snapshot come to the rescue……the thing is that my QNAP was secured as far as I was aware…..????????????????????????????
REPLY ON YOUTUBE
I am IT consultant for 20 years and i loved to had the opportunity to watch this video. To me the thing that QnAP does not have any guilt in their product its at least a bit biased. I know people want to sell NAS and make a good chunk of commissions, its how things works i got that.
But lets face it with a great example, if you have a Tesla, are driving and the car crushes because the system does not allow you to stop, then even if there is a bug there, the brand is responsible, not the end-user for sure.
When we translate the NAS issues, well sure , the end-user needs to have a specific skill set to be able to know how to work with the technologies, but the brand does not say its it can be challenging for some people, who does not understands, a,b,c… etc…. Instead they tell you that you can have everything setup by clicking a simple button, and the more features it has the more people will activate.
I never saw a disclaimer from QNAP or any other NAS brands about what can happen if the users does not have that skillset, and even worst, they market it as a product that is top notch in technology, like having access to the nas content from everywhere. That´s where they have responsibility, i am quite sure some lawsuits will occur sooner then later.
Because they have the responsibility to explain clearly what a basic user should do and should not do…
They also should explain that someone before buying a NAS should have at least a 3-2-1 backup solution , because the NAS is not the backup solution.
I know that for many people, the NAS itself its quite expensive to buy and so many users cant afford to buy external drives for Local backups and also a cloud backup system, that is the bare minimum for whom thinks about having a NAS as home or in a SOHO
And here again i never seen QNAP explaining in a very clear way in their sale pages about their NAS products, when i am talking about QNAP, its not only QNAP , other brands do the same, but are they responsible brands by doing so? in my honest opinion nope.
Probably many small business went out business, some because ethically they don’t want to pay to criminals and others because they cant afford to pay due to the crisis that have impacted so many people worldwide.
Here i believe that QNAP should paid the ransom to solve this issue for their customers, are they obliged to? of course not, but in the other hand they would not have their image burned out and their online reputation is not good to say the least.
I have a QNAP nas devices and i am quite sure that i will never ever buy another from this brand again.
REPLY ON YOUTUBE
I think every brand should add a choice at setup that asks, what is your data classification: very private, private, public. And what is your update tier: beta, innovative, stable and secure. From that the system can make the appropriate choices.
REPLY ON YOUTUBE
Worker with a reliable hacker is what I think is all over the world and I recommend a hacker parfait who works with good heart and sincerity Dee_hack11 is in Seoul☝️☝️☝️.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now.
REPLY ON YOUTUBE
*I was hit, so unplugged, shutdown, external USB backs fine. Plex user, was watching at the time no issues, went to update saver denied, then found the splash screen, no on reboot, water gapped on an independent switch no WiFi etc, it instantly goes to initialization. So save to assume the service themselves have been affected. Did safe shutdown. After some time I turn on everything then I found out I’ve been truly hit by deadbolt. I did as many research as I could and I found out that scott can actually decrypt the encrypted files So I paid some money not upto what deadbolt team are asking, then he decrypted my files*
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you.
REPLY ON YOUTUBE
Let Eddie say something…
REPLY ON YOUTUBE
I wouldn’t touch QNap with a barge pole until they drastically change their approaches to the user base, contempt for the user base isn’t a great strategy.
REPLY ON YOUTUBE
You’re ???? such a genius, I really appreciate your services, fast and safe recovery process..
REPLY ON YOUTUBE
You’re ???? such a genius, I really appreciate your services, fast and safe recovery process..
REPLY ON YOUTUBE
My QNAP NAS used UPnP to open all of the ports needed for bad actors to try brute forcing their way in. I was getting over 1200 login attempts per hour.
REPLY ON YOUTUBE
I think forced updates should be a requirement for utilizing certain features. So, if I enable remote access through a firewall of any sort, forced updates should be enabled. IT enabled organizations wouldn’t be making use if these features anyway and in can absorb the risk of automatic/manual updating.
REPLY ON YOUTUBE
I think they get attacked because they move into Face/Facial/Eye/Mask screening. People don’t like that. This is a threat to privacy. I think that is the root cause of it. I don’t know if Synology is in the same as such.
REPLY ON YOUTUBE
I regret I have missed this video 2 weeks ago. #asustor #deadbolt
REPLY ON YOUTUBE
I’m sorry I purchased a NAS as a means to have a BACKUP of what is/was on my laptop or pc. And it’s even sold as a backup. It started with ‘consumers’ being told to connect an external hard drive to backup their data. They would even supply at times backup software. So you backed up to this external drive. Then they started to sell NAS which was a way to still Backup and be able to access those backed up files from any connected computer.
So I disagree that you cannot thing of the NAS as a Backup.
Evidence: Why do they supply NetBak. Which can backup or copy your PC to the NAS.
So if you say the NAS is not a Backup tell these companies to stop supplying backup software that works to copy to these systems.
When I was told I needed a Backup I bit the bullet and purchased a second NAS which is used only to receive a Backup Data from the Main NAS! Its stupid but I understand it.
Especially since this last issue I had to erase my partitions to fix my issue. Great!
REPLY ON YOUTUBE
Wow I liked how you pointed out tech support being abrupt.
I reported a problem months and months ago and it was just impossible to arrange for remote support.
Then there was an update which fixed the problem we were trying to work on. So I basically wasted tons of time trying to recreate the problem and pin pointing the actual issue.
So why was I spinning my wheels for months when they knew about the issue.
Just tell me and ask me to be patient while they fix the bug. Why make me waste my important time for this sh*t.
I also had a problem of the NAS running so slow I could not even log in via the web. Thankfully I have a unit that has a hdmi port and was able access it via direct. But still could not use the system.
That was months and months. I was planning on dumping the whole thing. But it meant dumping two QNAP units. The cheaper of the two worked perfectly. I was angry.
Then I read something in a forum and decided to try it. I had to stop running Q’Center. Once I turned it off and removed it my system ran normally.
The same thing happens when you run McAfee. Of all things to slow down your unit so its unusable what is the purpose of having anti-virus. And whomever says its not needed needs their hand examined. You do!
The built-in anti-virus finds things that McAfee does not? And yes they could be false flags but it works.
REPLY ON YOUTUBE
Great video! I just saw lex friedman video and he talks about his devastating qnap ransom attack.
REPLY ON YOUTUBE
your videos could be a bit shorter and more concise. Lots of filler that doesn’t give a lot of information.
REPLY ON YOUTUBE
Not an IT expert but I bought an entry level Qnap NAS, which is now not connected to the internet and I’ve manually updated. What I’d really like to see is a guide to setting the NAS up safely so that the NAS is available to the home users, but protected from the internet outside. Backing up to two USB drives BTW!
REPLY ON YOUTUBE
Great discussion, can an OpenVPN / windows vpn on QNAP do it? and not juse myQNAPcloud? can it not be a good option? between one’s server and user outside of one’s network.
REPLY ON YOUTUBE
QNAP has significant blame in this latest attack. First, it was their operating system that was hacked (no one had to download a corrupt file). Second, they have all their users emails and all they needed to do is send out notifications to us users alerting us to all the attacks this past year not to mention warning us all to “unplug” immediately when this last attack started. Instead, they remain silent by email even to this day. The only reason I figured out I was hacked is after a month of not logging onto my NAS I found all my files encrypted when I went to grab some photos for my wife. I had to figure out for myself (with the help of bleepingcomputer forum) what was going on, how to get the ransom message back because they had quarantined it. No I didnt have a backup and I guess that is my fault for not understanding the hardware and risks better but I bought the NAS because it was supposed to “simple, safe and secure”. I only use my NAS on my LAN and I’ve never downloaded outside files to it but am not savvy enough to not have it connected to the internet thru my router. If Im lucky enough to get my data back after taking out a loan on my credit card and figuring out this whole Bitcoin thing this weekend, Im done with QNAP and their crappy equipment, buggy software and business approach. QNAP’s silence, irresponsibility and incompetence in dealing with these attacks this past year is the real story here that you all should be talking about as well.
REPLY ON YOUTUBE
What is the most concerning for me as a customer, not that hackers exists, they always did. But that Qnap has backdoor account to my own NAS…… they can remotely access to HBS, force update or whatever….. the clear answer to me to your question is : QNAP is not safe at all, period !
REPLY ON YOUTUBE
I don’t understand why so many “intelligent” people finger-point the victims. Do those guys blame their kids who’s got bullied in school? What a pathetic! NOBODY, NOBODY opened the port to the internet! QNAP got the port opened OUT OF THE BOX! I’m not using mycloud, I didn’t open any port. I didn’t enable auto-update because last year I ever lost files after migrating to the latest build!
This is not the first time they messed up everything. As always, QNAP is trying to escape from their own responsibilities. They pretends nothing happened. Custom service is non-existent. Users forum is full of everything but anything helps fix the issue.
Stay away from QNAP like a plague!
REPLY ON YOUTUBE
Infected last month, huge damages to us, and i guess it’s their ex-engneers who made ransom, and i am sure this company will fall.
REPLY ON YOUTUBE
I use my QNAP for Plex, and I share my Plex with two other friends. This is my second ransomware attack (thank goodness I had backups), so should I stop sharing? Can I make my QNAP secure and still share?
REPLY ON YOUTUBE
Thank you for making this enlightening video! I have now checked and switched off UPnP at my router. I was also watching your Plex setup video where you talk about setting remote access for Plex on a Synology NAS (with DSM 7) . How risky is setting up remote access for Plex to access my media remotely and are there ways to mitigate the risk?
REPLY ON YOUTUBE
I have found QNAP TVS-951X about 350£ (450$) used with 30 days free return + 6TB WD RED drives + 32GB RAM, should I buy it ?? it does look in a fair condition I want to use it for 4k streaming + 1080 and some backup + two or three members of my family watching 1080 content with me also to back up my stuff on it, should I buy it ??
thank you
REPLY ON YOUTUBE
Robbie and Eddie, Thank you for this in depth discussion, and guidance. I’m new to this, bought my nas at the end of November, and have been following a steep learning curve since then. I especially liked the advise to NOT TOUCH your network or nas settings if you do not understand the actions and results. I have to remind myself of that each time I mess with the settings, and have to reconstitute my nas.
REPLY ON YOUTUBE
I bought a single, large (16TB) HDD in recent weeks, plugged that into a free bay in my NAS, created a new storage pool & volume, and copied all my existing NAS Data onto it, and when complete, I pulled that Harddrive out. This is my ‘emergency’ back up, should the worst happen.
REPLY ON YOUTUBE
The Bank & Bank card analogy is a good one.
REPLY ON YOUTUBE
I don’t have remote access to either my QNAP or my Synology directly or through their respective relay systems. Instead, I use OneDrive (OD) as a relay point. My NAS is setup to sync with my OD account. When I’m on the road, my laptop syncs files with OD. So, when I edit a file on my laptop, it then syncs to OD which in turn syncs to my NAS. This won’t work for everyone but it can be a very effective way to effectively gain access to your NAS while working remotely. I don’t do this with the entire NAS, just the folders / files that I may need remotely.
REPLY ON YOUTUBE
Just bought a qnap nas yesterday. Really useful conversation. I have to admit i’m a little more concerned after watching this video than i was before.
REPLY ON YOUTUBE
Probably a recommended setting for beginners users from QNAP might works.
REPLY ON YOUTUBE
We are preparing a new video about how to secure your NAS and your local network.
You can send your external IP address to us via NAScompares.com contact form and we will run free vulnerability tests for you.
This will allow you to identify your network vulnerabilities and open ports etc.
REPLY ON YOUTUBE
Thanks again, last year after qlocker Eddie was adamant that myQnapCloud was safe and I believe the issue was upnp allowing access a hard coded back door.
Do you both still feel myQnapCloud is safe ?
REPLY ON YOUTUBE
Really enjoyed this especially since they got me too. Thank you. Small piece of feedback – it’d be great if you gave Edward a bit more of a chance to speak at times. There are sections where it seems he’s just on the receiving end of a long lecture, as opposed to part of the conversation.
REPLY ON YOUTUBE
Rip out the DOM n install unraid on it 😀
REPLY ON YOUTUBE
Thanks Robert. Thanks Edward.
REPLY ON YOUTUBE
Could you do a video on how to secure your nas? Things like what port to put things on. Stuff like that?
REPLY ON YOUTUBE
im using a tricky way to remotely access my NAS files, by hiding them behind a nextcloud single user on a Pi thats not visible. not infallible, but takes breaking that, just to see files, not alter them or upgrade. if i have to upload, i have to remote into a computer and use other methods. rarely do i need to access files , but it can be done if i have to.
REPLY ON YOUTUBE
After using QNAP NAS devices for years – we’ve lost all confidence in the brand and it’s no longer on our supplier list.
REPLY ON YOUTUBE
TL:DW; version – its a security/ease of use trade-off. If you lock things down users find it too hard to use the features the vendor offers and berates them for it. If you open things up you give users the chance to shoot themselves in the foot, and some will.
Case in point being IoT “plug and play” devices. I was struggling to identify a device on my network today and discovered it had a password-protected web server – I guessed the password on the third attempt. You’d have thought vendors would have learned by now but clearly not.
Another interesting point given the mention of TrueNAS – Unraid ships with all security turned off by default. I think they’ve now realised they erred in doing that, but don’t seem to be in any hurry to fix it. I’ll be keeping any NAS behind a VPN. Wish I could do the same thing with Plex but it seems to need an opening to work properly, so I’ll have to isolate it on a VLAN.
REPLY ON YOUTUBE
One of the mistakes that QNAP made on this was that they actually identified and problem and issued a fix before the attack. But they didn’t make the update mandatory (they can override the user desire on when to take an upgrade). Users that had manually done the upgrade like myself or ones that didn’t have their NAS exposed to the Internet were fine. But other users were hijacked.
REPLY ON YOUTUBE
I did enjoy the video. I got a month ago a TVS-H1288X. We wouldn’t be talking about this if everyone had updated their NAS. QNAP needs to have a shout mode that you can’t miss if the patch fixes a vulnerability. The lack of organized information as not only to what to do but why? Example Port 443. It is recommended to change it but what range and why change it. I assume port scanners don’t deviate from assigned ports and look for low honing fruit. So by changing to 478 it is put out of the scanner range? If we do a router port forwarding to use QBelt on the NAS is that a direct open door to get into the NAS? I am guessing no otherwise why do assigned ports exist. At moment because of questions I have port forwarding off therefore I can’t use QBelt VPN which we are told it safe. My point is there needs to be a source that explains all of this that we can read. I am an engineer and programmer. First thing I did was set up QBelt to my android phone. UPnP was off from beginning. I have turned off myQnapCloud as I am unsure of where it stands safety wise. Has it been broken before? I even bought a certificate from Qnap and installed it. I think you should step in detail on each part of these security setting. What to change? Why you do it. And where to get more if on it. Love your videos
REPLY ON YOUTUBE
Data (physical or electronic) is arguably the most important thing you own the protection of it it more important than money.
If I loose a $50 note it can be replaced with any other $50 note the thing that makes it unique, the little string of numbers in the corner or any stains or creases are not what gives this value to you.
Conversely if you loose 50mb of data it can’t be replaced with any old 50mb of data as it’s uniqueness IS where the value was held. It is by definition irreplaceable/ priceless.
When average joe numpty buys an external HDD, NAS OR starts doing some form of online cloud storage or backup they have stumbled into the realisation that data holds value.
Often it’s a result of learning the hard way and loosing something.
NAS brands really should be held to account for some things but like you say not all.
From a consumer protection point of view, is it fit for purpose? Does it do everything it was advertised to do? Was it free of defects?
I buy a NAS, follow their instructions for setup while using the drives they recommend.
My expectations are:
– My data will be stored there without risk
– My data will be available using ALL advertised methods without putting it at risk
– I will be prevented from accidentally impacting the above two things.
During the setup process there should be a “most users” option that walks you through a VERY simple wizard (most users are not as smart as they think they are… see Dunning-Kruger effect).
Lock out or at least require a certain level of knowledge to unlock the most advanced features. Maybe a big warning when you select advanced option a big simple warning saying “by clicking this we no longer warrant the safety and security of your data” The stuff a car owner should touch is yellow under the bonnet of most cars now. Oil, wiper fluid, etc…
Also as joe numpty does not understand the difference between redundancy, backup etc etc. prompting them to locally encrypt and purchase a offsite data storage plan, backup to another offsite NAS or set up automatic email reminders for periodic backups.
Updates should always come with a have 3 options:
1. Update instantly on release. Early adopters on the bleeding edge (called that for a reason) “the is an update available and will be installed in x hours unless you hit cancel”
2. Delayed update (default most users). There is a new update available it’s currently being installed on some systems. This update will be automatically installed on this hardware after 30 consecutive days of bug free operation globally”. In this mode critical exploit patches are able to be forced if it impacts the last auto update.
3. Auto update off. Notifications on.
I think it’s absolutely NUTS that people give any nas company any form of slack for not treating your data at least as valuable as a bank treats your money. DONT share your pin, unusual behaviour lockdowns of accounts, etc.
Hard to type all this crap on a mobile phone.
REPLY ON YOUTUBE
Great Discussion! Driver’s license…????????????
REPLY ON YOUTUBE
Absolutely, I bought it for the hardware. Not always as inexpensive as I’d like — TS-873A vs 873-AU come to mind.
Is QNAP safe? Well, when it’s a NAS not an iNAS … mostly. I mean, there’s an IOT vector, but this is an IOT issue — does QNAP need to make its NAS safe against a determined in-network hacker? The IOT threat is just a whole nother topic….
The problem is that they market their internet-connectivity, and they need to stop doing that until they get their house in order, because they don’t have their house in order. Their responsiveness to CVEs has been lackluster at best, bordering on dangerously irresponsible. Security concerns are not as front-and-center as they should be. And magic, hard-coded backdoors in software is so gigantically awful — that stuff never should have been checked in to anything that ships to a customer. Astonishingly terrible.
REPLY ON YOUTUBE
Good discussion! But their privacy policy is what drove me away!
REPLY ON YOUTUBE
Great discussion. I like how you alluded to the “everyday man.” The reason I gravitated from Synology to QNAP was #1) Hardware comparison but most importantly #2) Capability to do more thanks to the software’s ability to have a lot less guardrails allowing me to do more.
I am by no means an IT expert, but I want the most hardware for my money and the software capabilities to do it. I also learned early on YOU HAVE to absolutely!!! know what you are getting yourself into before opening up your network with any NAS.
REPLY ON YOUTUBE
There is only one important rule. Never expose your NAS to the internet…until you know exactly what you are doing! Anyway, and always remember, a NAS is NO backup (RAID is not enough backup, either)!
REPLY ON YOUTUBE
Probably time for everyone to realize that these boxes are not good enough for external access. I have 3 qnap boxes and would never expose them to the outside. You want to go outside, go with the big boys like Azure. Qnap is not up for the job. It is fine for your LAN and leave it there.
REPLY ON YOUTUBE
As regarding the backup, one of the reason’s I am looking at buying a NAS is to allow me to put one in my home and one in my parents home, and allow us to both sync our data to have an off site backup.
But this means both need to be exposed on the internet to allow the sync. In this case it I think it makes sense to have both of these to be using the same platform as this includes software to sync.
However if I chose QNAP it is the process of wanting to get the backup capabilities that is exposing me to the data risk.
I am a software developer, (i.e. the worst person in this case since I know enough to be dangerous), but am no ‘Locksmith’, so would really welcome better hand holding and explanation of what the various features are actually doing behing the scenes and what the risks are.
REPLY ON YOUTUBE
QNAP need to open and honest about what vulnerabilities in what software exist on all of their models. If you fix the vulnerabilities sooner via auto-update (and not all vulnerabilities need reboots) then they wouldn’t be in this situation.
REPLY ON YOUTUBE
How about a step by step guide to secure your qnap nas?
REPLY ON YOUTUBE
No, absolutely, NO
REPLY ON YOUTUBE
Safe to save garbage files I guess.
REPLY ON YOUTUBE