New QNAP Attack Emerges in the last 24hrs, the Deadbolt Ransomware
UPDATED 28/01/22 – QNAP has instigated a forced-push firmware update to NAS devices to upgrade their systems to version 5.0.0.1891 (the 23/12/21 update), which will override systems that have their update settings set to ‘Do not automatically update’. This will almost certainly change a number of default settings that in older QTS versions are connected with the means of the deadbolt firmware being instigated on individual NAS systems. Following this, several users have reported that existing iSCSI connections ceased, due to a default setting changing in the update. As per the highlights on the bleepingcomputer update article, this has been resolved by users by seeking out the following setting:
“In “Storage & Snapshots > ISCSI & Fiber Channel” right-click on your Alias (IQN) select “Modify > Network Portal” and select the adapter you utilize for ISCSI.”
Nevertheless, a forced update is quite a big move by the brand in response to this ransomware attack and one that under other circumstances would be something that ideally would have been presented with a “we will be making this forced update on X date, be aware” etc. In the QNAP reddit, a 1st party support team member responded to queries regarding the forced QNAP QTS update with the following;
“We are trying to increase protection against deadbolt. If recommended update is enabled under auto-update, then as soon as we have a security patch, it can be applied right away.
Back in the time of Qlocker, many people got infected after we had patched the vulnerability. In fact, that whole outbreak was after the patch was released. But many people don’t apply a security patch on the same day or even the same week it is released. And that makes it much harder to stop a ransomware campaign. We will work on patches/security enhancements against deadbolt and we hope they get applied right away.
I know there are arguments both ways as to whether or not we should do this. It is a hard decision to make. But it is because of deadbolt and our desire to stop this attack as soon as possible that we did this.”
Additionally, (again, thanks to BeepingComuter for raising this) there are reports that the number of affected devices may have raised significantly since originally projected and several security researchers and internet device monitoring sites raise this number to between 1,160-3,687 as of Jan 28 2022. See tweet below:
🔐 Curated Intel member, @1ZRR4H, observed QNAP ransomware events being reported via IoT search engines, including Shodan and Censys.
🔗 Shodan (1160 events): https://t.co/qpaCTuICAf
🔗 Censys (3687 events): https://t.co/uZKLQprSDE
Tip: use country tags to search by country. pic.twitter.com/2IXpCNpBvV
— Curated Intelligence (@CuratedIntel) January 27, 2022
I will continue to update this article as new information emerges. Please find the original article detailing the Deadbolt ransomware attack on QNA NAS devices below.
Yesterday (25/01) it has been reported on official QNAP forums that several users have been attacked by a new ransomware (actioned with the name Deadbolt) that, if successful in its intrusion, encrypts the content s of your NAS and demands 0.03 bitcoin (about $1000-1100) to provide the decryption key and allow retrieval of your data. QNAP has responded on multiple channels, urging their user base to immediately disable Port Forwarding on their router/modems and the UPnP function of the QNAP NAS within the remote access services. Additionally, they (as you would expect) strongly advise users to update their QTS software to the latest available version to block incoming DeadBolt ransomware attacks. QNAP has since issued this statement, published 26/01/22:
QNAP Systems, Inc. recently discovered that a ransomware called DeadBolt is attempting to attack NAS exposed to the Internet. The ransomware will hijack the NAS login screen and extort bitcoins from the victim. QNAP strongly urges all NAS users to immediately follow the methods below to check whether your NAS is exposed to the Internet, confirm whether the security settings of the router and NAS are complete, and update QTS to the latest version as soon as possible. More information regarding checking the level of access your QNAP NAS has to the internet, as well as how to change key settings to improve security can be found HERE.
Following the news on this as it has happened over 24hrs, the popular network security site Bleeping Computer reported that DeadBolt ransomware group started attacking QNAP users and encrypting files on compromised NAS devices applying a .deadbolt file extension to affected files
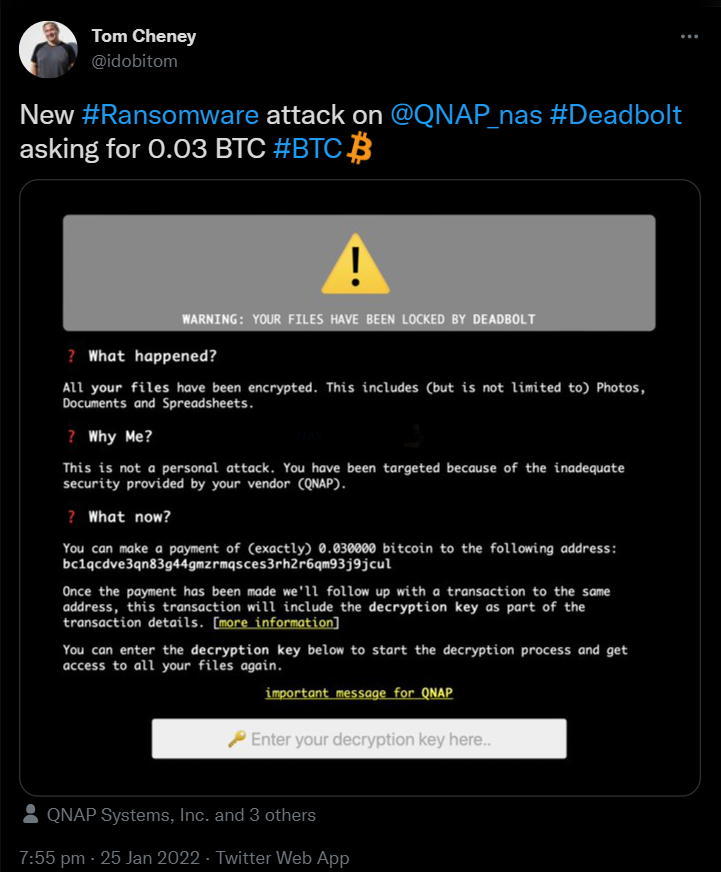
Unlike previous instances involving QNAP NAS being targeted by ransomware, deadbolt are not dropping ransom .txt or docs to the encrypted devices but, this time are replacing the login pages to display warning screens saying “WARNING: Your files have been locked by DeadBolt.” The ransom screen asks the QNAP NAS owner to pay 0.03 bitcoins (roughly $1,100) to a unique Bitcoin address generated for each victim, claiming that the decryption key will be sent to the same blockchain address in the OP_RETURN field once the payment goes through. Sadly, as is always a risk factor with ransomware, currently, there are no confirmations that the threat actors will actually deliver on their promise to send a working decryption key after paying the ransom (as at the time of writing) users who have been affected are not seemingly considering paying (understandably, as this likely facilitates this happening further still in future for others).
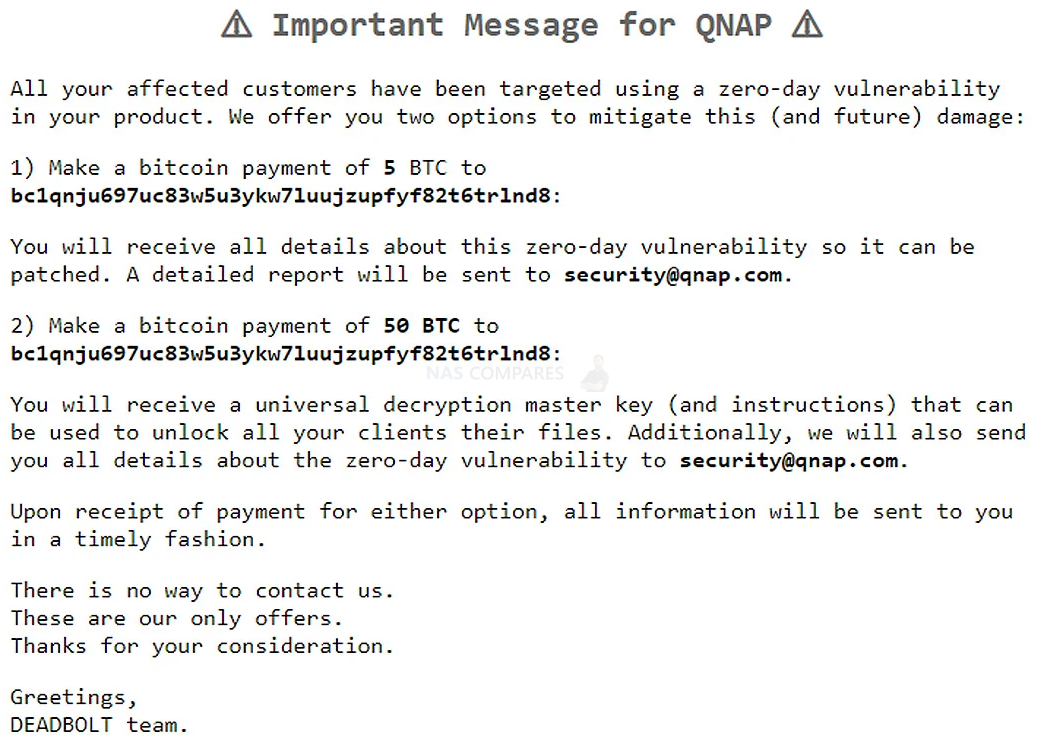
Additional to the main ransom note splash screen on affected QNAP NAS systems, there is also is a link “important message for QNAP,” which then leads to a displayed message from the DeadBolt ransomware group that is specifically for QNAP’s attention. This screen states that the DeadBolt ransomware gang is offering the full details of the alleged zero-day vulnerability if QNAP pays them 5 Bitcoins in payment, roughly equivalent to $184,000. They are also willing to sell QNAP the master decryption key that can decrypt the files for all affected victims and the zero-day info for 50 bitcoins, roughly $1.85 million based on the current BC valuation. They state that if this payment is made:; “You will receive a universal decryption master key (and instructions) that can be used to unlock all your clients files. Additionally, we will also send you all details about the zero-day vulnerability to security@qnap.com.”
So, fairly brazen stuff!
What Does the DeadBolt Ransomware do to my QNAP NAS?
The DeadBolt ransomware is attempting to encrypt QNAP NAS, units, utilizing what they state is a zero-day vulnerability within QTS (A zero-day vulnerability is a vulnerability in a system or device that has been disclosed but is not yet patched. An exploit that attacks a zero-day vulnerability is called a zero-day exploit). The attack began on January 25th, with numerous QNAP users discovering their data encrypted and file names appended with a .deadbolt file extension, as well as amending the QNAP login web page to show a display screen stating, “WARNING: Your files have been locked by DeadBolt,” (see below:
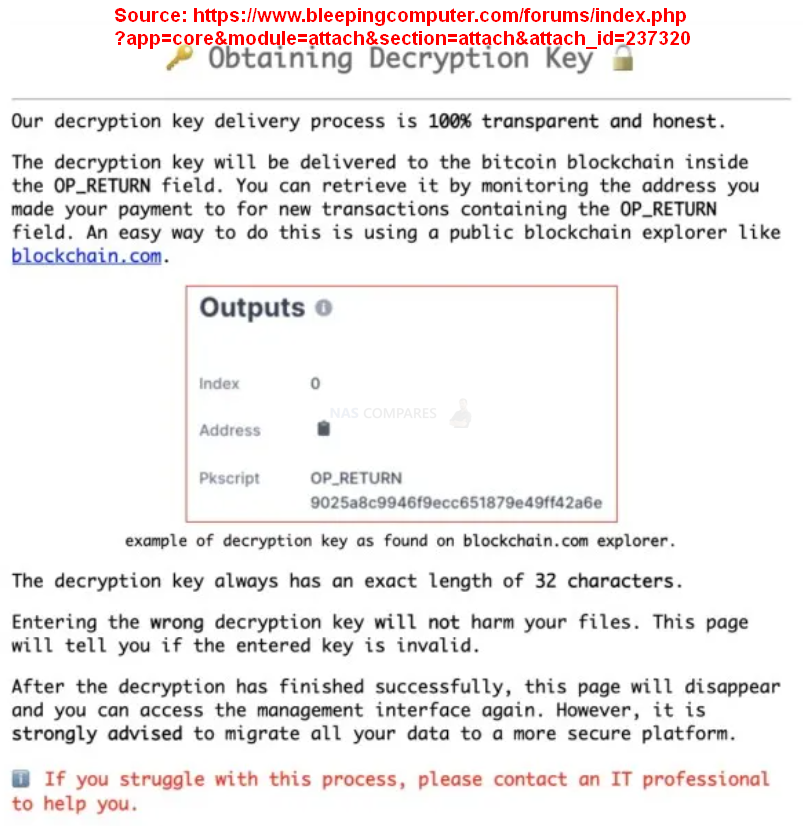
On this occasion, this user was told they need to pay 0.03 bitcoins (roughly $1,100) to an individual Bitcoin link in order to receive the decryption key. The process of receiving the key is detailed follows:
So, if you have not been affected by this ransomware, but have/need your QNAP NAS to be remotely accessible from outside of your local network, what should you do?
How to Check and Amend Your QNAP NAS Internet Access Right Now
Like many ransomware attacks, the full vulnerability that it exploits will become clearer as time goes on, but a high facilitating factor of the deadbolt attack concerns poor remote access security. Remote access to the NAS can be made several ways (some more complex than others) and QNAP in their recent news post on this ransomware attack highlights further recommended network maintenance measures that you should follow/check. Open the Security Counselor program of the QNAP NAS, if you find the warning text “The System Administration service can be directly accessible from an external IP address via the following protocols: HTTP”, it means that your NAS is being exposed to the external network, and the risk is extremely high.
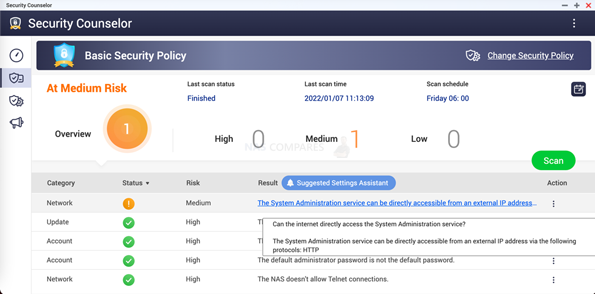
If you are unsure which port numbers on your router are open, then you can use this guide on How to query the port number that has been exposed to the external network HERE. If your NAS is exposed to the Internet, it is recommended that you follow the steps below for NAS security protection:
1: Turn off the Port Forwarding function of the router
Open your router’s system management interface, check the router’s Virtual Server, NAT or Port Forwarding settings, and set the NAS system management ports (8080 and 443 by default) to off.
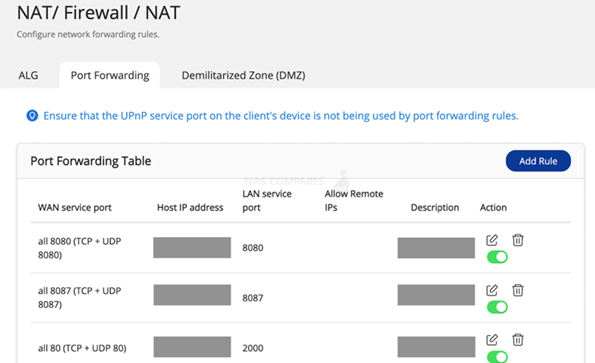
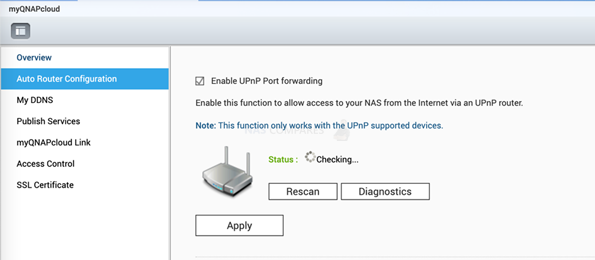
2: Check if the UPnP function of the QNAP NAS remains off
Open the myQNAPcloud app of QTS and check the UPnP Router settings. Uncheck “Enable UPnP Port forwarding”
Connecting with your QNAP NAS remotely may well be a key reason why you purchased the system, but if you are less tech or network protocol savvy, then many users will use the QNAP supplied service. However, I still HIGHLY recommend that you bolster your network security settings as much as possible and ensure you have multiple layers of security (automated or direct authentication required) between the internet and your NAS Drive. If you need a NAS external network connection and want to use the myQNAPcloud Link to connect, please refer to the following link – HERE
Alternatively, QNAP made a whole page on remote access security and a breakdown of the factors HERE. Further details on this are covered in the Data News of the Week Video below from the NASCompares YouTube channel:
We will continue to monitor this and update this article if further information arrives that ranges from changes in the attack methodology to potential fixes and decryption tools emerging.
Additionally, it is worth remembering that exploits can be found in practically any internet-connected appliance, it is just a question of the extent to which a vulnerability can be pushed to execute unique commands. The software makers (not just NAS, but practically ALL internet service linked applications and tools) can only be 1-step ahead of hacks (cat and mouse, 1 step each, etc) and that is why all reputable NAS brands have Security Advisory pages that are regularly updated to list any current vulnerabilities that are found, addressed and patched on their platforms. However, staying on top of these can be difficult, so below is a link to a page here on NASCompares that is updated automatically every day and/when a brand updates its security vulnerability advisory pages. You can add your email address to that page in order to receive updates as soon as the brands publish investigated vulnerabilities. Visit this page by clicking the banner below:
📧 SUBSCRIBE TO OUR NEWSLETTER 🔔
🔒 Join Inner Circle
Get an alert every time something gets added to this specific article!
This description contains links to Amazon. These links will take you to some of the products mentioned in today's content. As an Amazon Associate, I earn from qualifying purchases. Visit the NASCompares Deal Finder to find the best place to buy this device in your region, based on Service, Support and Reputation - Just Search for your NAS Drive in the Box Below
Need Advice on Data Storage from an Expert?
Finally, for free advice about your setup, just leave a message in the comments below here at NASCompares.com and we will get back to you. Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.
Need Help?
Where possible (and where appropriate) please provide as much information about your requirements, as then I can arrange the best answer and solution to your needs. Do not worry about your e-mail address being required, it will NOT be used in a mailing list and will NOT be used in any way other than to respond to your enquiry.

|
 |
Minisforum G7 Pro Review
CAN YOU TRUST UNIFI REVIEWS? Let's Discuss Reviewing UniFi...
WHERE IS SYNOLOGY DSM 8? and DO YOU CARE? (RAID Room)
UniFi Routers vs OpenWRT DIY Routers - Which Should You Choose?
WHY IS PLEX A BIT S#!t NOW? IS 2026 JELLYFIN TIME? (RAID Room)
Synology FS200T NAS is STILL COMING... But... WHY?
Access content via Patreon or KO-FI
Discover more from NAS Compares
Subscribe to get the latest posts sent to your email.






I was hit by deadbolt ransomeware some weeks ago. Finally I got the key and my files have been fully decrypted. Thank you
REPLY ON YOUTUBE
QNAP the most attacked NAS on the planet and worst support. I lost 7tb of data with no way to recover.
REPLY ON YOUTUBE
he did the job for me even when it seemed????????
not possible thank you very much.
Translate to????????????
REPLY ON YOUTUBE
* 4 months August @ I really appreciate you for the professional work you do to get my cell phone back you are the best I recommend it @ ☝️☝️☝️☝️☝️
REPLY ON YOUTUBE
Worker with a reliable hacker is what I think is all over the world and I recommend a hacker parfait who works with good heart and sincerity Dee_hack11 is in Seoul☝️☝️☝️
REPLY ON YOUTUBE
????????????????????Contact this hacker he is honest he helped me recovered my files I’m grateful
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now
REPLY ON YOUTUBE
After trying for some time, I had to contact *SCOTTS_HACK* to help me get the deadbolt off my Nas. I’m free now
REPLY ON YOUTUBE
*I was hit, so unplugged, shutdown, external USB backs fine. Plex user, was watching at the time no issues, went to update saver denied, then found the splash screen, no on reboot, water gapped on an independent switch no WiFi etc, it instantly goes to initialization. So save to assume the service themselves have been affected. Did safe shutdown. After some time I turn on everything then I found out I’ve been truly hit by deadbolt. I did as many research as I could and I found out that scott can actually decrypt the encrypted files. So I paid some money not upto what deadbolt team are asking, then he decrypted my files*
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you
REPLY ON YOUTUBE
Good day all, for DEADBOLT RANSOMWARE REMOVAL, consult *SCOTTS_HACK* Thank you
REPLY ON YOUTUBE
.You can message *SCOTTS_HACK*
REPLY ON YOUTUBE
.You can message *SCOTTS_HACK*
REPLY ON YOUTUBE
Am cool with #GLOCYBER idea. He has much research on the virus and has helped a lot including my self.
REPLY ON YOUTUBE
Am cool with #GLOCYBER idea. He has much research on the virus and has helped a lot including my self.
REPLY ON YOUTUBE
????I was so glad when I finally realized and get in touch with Glo Cyber while I used the contact above. He is indeed a genius and his skill are authentic. I rec. everyone to appreciate his efforts.
REPLY ON YOUTUBE
People keep talking about Scott. I think he is good. I will try him.
REPLY ON YOUTUBE
Someone recommended you ????and you also helped me recover mine too. You a genius indeed.
REPLY ON YOUTUBE
just got hit and i was on latest firmware and all apps updated
REPLY ON YOUTUBE
OpenVPN / windows vpn on a QNAP , and not juse myQNAPcloud?
can it not be a good option?
between one’s server and user outside of one’s network.
REPLY ON YOUTUBE
This has just happened to me ???? deadbolt… help
REPLY ON YOUTUBE
Another reason to not enable internet access to your NAS.
REPLY ON YOUTUBE
Rob,
Qnap have several must do’s in light of this Dead Bolt ransomware attack with many branching links. Would you be able to do a video in how to do all these security things please?
REPLY ON YOUTUBE
i really hope qnap will do something about those stuff, lately has been quite a lot, anyway, i do love their nas; and if people use it in the proper way, updating the firmwares and all this, everything should be fine in the end
REPLY ON YOUTUBE
i really hope qnap will do something about those stuff, lately has been quite a lot, anyway, i do love their nas; and if people use it in the proper way, updating the firmwares and all this, everything should be fine in the end
REPLY ON YOUTUBE
This is why god made firewalls and the advice to not expose your NAS to the internet…
REPLY ON YOUTUBE
Question: I’m planning on upgrading from my WD Cloud to a QNAP 453be in the next few days but it will NOT be online. Ever. If it can be avoided. That being said, when I am setting it up for the first time does it “force” me to update the OS or any of the software? Or, can I just set it up completely offline? (I would rather not connect it to the internet specifically for the purpose of never getting any of these bloody attacks. It will be used as a backup device for my family’s laptops and a Plex server for movies we already have on the WD Cloud device (not online).
REPLY ON YOUTUBE
Even though I have Synology (which doesn’t prevent the same from happening), I recommend having an offline backup that is PHYSICALLY unplugged from your NAS After each backup. Even with an offline backup, if it is ejected but not disconnected, all someone has to do is restart the NAS to reconnect and then Infect that backup. You can even take this a step further by initiating backup via USB 3.0 and then disconnecting The router’s internet connection while backing up for peace of mind
then once back up is completed safely eject then physically disconnect offline backup before reconnecting to the internet.
REPLY ON YOUTUBE
2 form authentication helps ?
REPLY ON YOUTUBE
Well bummer, after researching I was on thinking of getting a Qnap instead of a Synology. Now I’m thinking I should get a Synology now.
REPLY ON YOUTUBE
Here we go again. Sigh!
REPLY ON YOUTUBE
I couldn’t even imagine how much those new Gen5 nvme drives are going to cost ????????????????
REPLY ON YOUTUBE
Sea gate drives for the series x are screaming hot. Even when console is off.
REPLY ON YOUTUBE
I have seen a few videos on QNAP re ransomware. Is it more susceptible than synology?
REPLY ON YOUTUBE
04:48 – This video was recorded at 27/01 15:00 GMT. Further information and updates have occurred on this and I have added them at this time marker (regarding forced updates to NAS systems and updates on significantly increased infected systems). If the video looks blurry/360p, then give YouTube 15mins to process or the 720p and 1080p versions (takes them a little time). Cheers for watching.
REPLY ON YOUTUBE