How to Install Tailscale on a QNAP NAS Keeping the data as secure as possible is probably one of the most paramount concerns of any NAS owner. Everyone wants to make sure that their data cannot be accessed by unauthorized individuals, but at the same time want to make sure that their hardware can communicate […]
Get an email every time there is a new post added on this page (tag)!
Tag: Tailscale
How to Install and Setup Tailscale on a QNAP NAS
How to Install Tailscale on a QNAP NAS Keeping the data as secure as possible is probably one of the most paramount concerns of any NAS owner. Everyone wants to make sure that their data cannot be accessed by unauthorized individuals, but at the same time want to make sure that their hardware can communicate […]
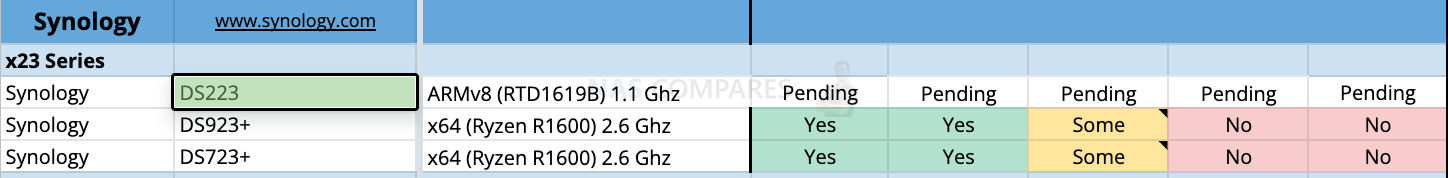
Cannot Install Plex on DS223 or DS423
How to install & set up UNRAID NAS server (SMB, Tailscale VPN and plex)
Synology & QNAP NAS Remote Access Guide – Speed vs Security vs Cost
Accessing Your NAS Remotely – Security vs Speed vs Cost! Network Attached Storage (NAS) devices are an essential part of any home or office network. They provide a central storage location for all your digital files, making it easy to access and share them across multiple devices. However, connecting to a NAS device can be […]
Speed vs Security: Choosing the Right Remote Access Method for Your NAS on Internet
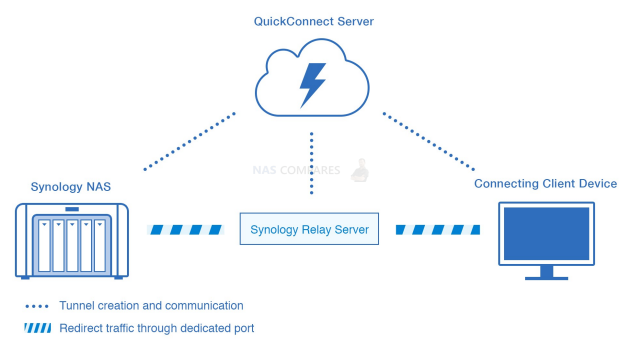
Network Attached Storage (NAS) devices are an essential part of any home or office network. They provide a central storage location for all your digital files, making it easy to access and share them across multiple devices. However, connecting to a NAS device can be complicated, and choosing the right connectivity option can make all […]
How to access your NAS remotely? A Comparison of NKN nConnect and Tailscale

Introduction Brief overview of VPN technology VPN (Virtual Private Network) technology allows users to securely access the internet by encrypting their internet connection and routing it through a remote server. This creates a virtual “tunnel” between the user and the internet, effectively hiding the user’s internet activity and location. VPNs are commonly used by individuals […]